mirror of
https://github.com/MustardChef/WSABuilds.git
synced 2024-11-25 20:56:53 +01:00
Fix Build Process
This commit is contained in:
parent
51ff89f640
commit
7c24d7c711
3
MagiskOnWSA/DLL/README.md
Normal file
3
MagiskOnWSA/DLL/README.md
Normal file
@ -0,0 +1,3 @@
|
|||||||
|
# WSAPatch
|
||||||
|
|
||||||
|
<https://github.com/cinit/WSAPatch/releases>
|
||||||
BIN
MagiskOnWSA/DLL/WsaPatch.dll
Normal file
BIN
MagiskOnWSA/DLL/WsaPatch.dll
Normal file
Binary file not shown.
BIN
MagiskOnWSA/DLL/bin/arm64/lspinit
Normal file
BIN
MagiskOnWSA/DLL/bin/arm64/lspinit
Normal file
Binary file not shown.
BIN
MagiskOnWSA/DLL/bin/x64/lspinit
Normal file
BIN
MagiskOnWSA/DLL/bin/x64/lspinit
Normal file
Binary file not shown.
81
MagiskOnWSA/DLL/cacerts/01ee3bf3.0
Normal file
81
MagiskOnWSA/DLL/cacerts/01ee3bf3.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIDzzCCAregAwIBAgIJAPJgZpghday9MA0GCSqGSIb3DQEBCwUAMH4xCzAJBgNV
|
||||||
|
BAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcMCUplcnVzYWxlbTEQMA4G
|
||||||
|
A1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0ZnJlZS5saW5rMSEwHwYDVQQDDBhO
|
||||||
|
ZXRGcmVlIFNpZ24gLCBIYWRyYW5WcG4wHhcNMTcwMzMwMDEwNDAwWhcNMjcwMjA2
|
||||||
|
MDEwNDAwWjB+MQswCQYDVQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIwEAYDVQQH
|
||||||
|
DAlKZXJ1c2FsZW0xEDAOBgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5ldGZyZWUu
|
||||||
|
bGluazEhMB8GA1UEAwwYTmV0RnJlZSBTaWduICwgSGFkcmFuVnBuMIIBIjANBgkq
|
||||||
|
hkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEApRXoigVenMeP9PGM9zt/TDo60AwOrjAS
|
||||||
|
a2zSgR21Hy9IoJGdR57eZKMKvGirzsgTrzjZl/G92FPppx1hKyZjP1IHES0kzG74
|
||||||
|
yK4JtRGC1T4GYutAHM1ZDv7ZoUnGxsEo5or6CFhR+D/zJ5fiiACFypIICb6qUynk
|
||||||
|
aaSamw1JTKLNUCrs6eArJnThBJP+Czi45uM/mdrB5jnajLvRnFgeqcPp6913zKUy
|
||||||
|
4FsHPm5U26kincnRV/04UB4Xx/f3LHv9L9Ao1aViDbZlHverU0ETCEALHWqnfjX/
|
||||||
|
uSk/zRXZRzDRPCGIdVXuxiYINjCzA4+ZRrdc+qhlpuzn9ct7phi3ewIDAQABo1Aw
|
||||||
|
TjAdBgNVHQ4EFgQU3C1v4yi0aNBn4CzFWEnQl2Lcl94wHwYDVR0jBBgwFoAU3C1v
|
||||||
|
4yi0aNBn4CzFWEnQl2Lcl94wDAYDVR0TBAUwAwEB/zANBgkqhkiG9w0BAQsFAAOC
|
||||||
|
AQEAeHISptZ4rtfTGej48OV5o5q/Z5XmU8G4qnkWX4AfqIl3SOfPc6UzHBE+gYyw
|
||||||
|
zhBfvhW+MMHJaBh0LfswRfbuP3nkOQNvzVSIRyvmYqklZTTSQ1J5AsgB39C1LYWB
|
||||||
|
c79cyYZH3EUU+bdXgBlIxTixpOm+eqoxQlIoAMjmOjQMvOKFsZJcj0XUdULfxC2C
|
||||||
|
PbMkCJ6JB5Dr19NZxsQyEE+GhLiPJDtGcjzfHMZwUDMe1qWKAnPR5P9xZegm50HI
|
||||||
|
ogmnZGL6nfpts5yqeHaQunCKQarUbvY7Sp89wI1J+ntVHVnO9VxubHqWj+1nwlna
|
||||||
|
SBAWwK8ruKyu6mDloyilV6c4+g==
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
f2:60:66:98:21:75:ac:bd
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , HadranVpn"
|
||||||
|
Validity
|
||||||
|
Not Before: Mar 30 01:04:00 2017 GMT
|
||||||
|
Not After : Feb 6 01:04:00 2027 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , HadranVpn"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:a5:15:e8:8a:05:5e:9c:c7:8f:f4:f1:8c:f7:3b:
|
||||||
|
7f:4c:3a:3a:d0:0c:0e:ae:30:12:6b:6c:d2:81:1d:
|
||||||
|
b5:1f:2f:48:a0:91:9d:47:9e:de:64:a3:0a:bc:68:
|
||||||
|
ab:ce:c8:13:af:38:d9:97:f1:bd:d8:53:e9:a7:1d:
|
||||||
|
61:2b:26:63:3f:52:07:11:2d:24:cc:6e:f8:c8:ae:
|
||||||
|
09:b5:11:82:d5:3e:06:62:eb:40:1c:cd:59:0e:fe:
|
||||||
|
d9:a1:49:c6:c6:c1:28:e6:8a:fa:08:58:51:f8:3f:
|
||||||
|
f3:27:97:e2:88:00:85:ca:92:08:09:be:aa:53:29:
|
||||||
|
e4:69:a4:9a:9b:0d:49:4c:a2:cd:50:2a:ec:e9:e0:
|
||||||
|
2b:26:74:e1:04:93:fe:0b:38:b8:e6:e3:3f:99:da:
|
||||||
|
c1:e6:39:da:8c:bb:d1:9c:58:1e:a9:c3:e9:eb:dd:
|
||||||
|
77:cc:a5:32:e0:5b:07:3e:6e:54:db:a9:22:9d:c9:
|
||||||
|
d1:57:fd:38:50:1e:17:c7:f7:f7:2c:7b:fd:2f:d0:
|
||||||
|
28:d5:a5:62:0d:b6:65:1e:f7:ab:53:41:13:08:40:
|
||||||
|
0b:1d:6a:a7:7e:35:ff:b9:29:3f:cd:15:d9:47:30:
|
||||||
|
d1:3c:21:88:75:55:ee:c6:26:08:36:30:b3:03:8f:
|
||||||
|
99:46:b7:5c:fa:a8:65:a6:ec:e7:f5:cb:7b:a6:18:
|
||||||
|
b7:7b
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
DC:2D:6F:E3:28:B4:68:D0:67:E0:2C:C5:58:49:D0:97:62:DC:97:DE
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:DC:2D:6F:E3:28:B4:68:D0:67:E0:2C:C5:58:49:D0:97:62:DC:97:DE
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
78:72:12:a6:d6:78:ae:d7:d3:19:e8:f8:f0:e5:79:a3:9a:bf:
|
||||||
|
67:95:e6:53:c1:b8:aa:79:16:5f:80:1f:a8:89:77:48:e7:cf:
|
||||||
|
73:a5:33:1c:11:3e:81:8c:b0:ce:10:5f:be:15:be:30:c1:c9:
|
||||||
|
68:18:74:2d:fb:30:45:f6:ee:3f:79:e4:39:03:6f:cd:54:88:
|
||||||
|
47:2b:e6:62:a9:25:65:34:d2:43:52:79:02:c8:01:df:d0:b5:
|
||||||
|
2d:85:81:73:bf:5c:c9:86:47:dc:45:14:f9:b7:57:80:19:48:
|
||||||
|
c5:38:b1:a4:e9:be:7a:aa:31:42:52:28:00:c8:e6:3a:34:0c:
|
||||||
|
bc:e2:85:b1:92:5c:8f:45:d4:75:42:df:c4:2d:82:3d:b3:24:
|
||||||
|
08:9e:89:07:90:eb:d7:d3:59:c6:c4:32:10:4f:86:84:b8:8f:
|
||||||
|
24:3b:46:72:3c:df:1c:c6:70:50:33:1e:d6:a5:8a:02:73:d1:
|
||||||
|
e4:ff:71:65:e8:26:e7:41:c8:a2:09:a7:64:62:fa:9d:fa:6d:
|
||||||
|
b3:9c:aa:78:76:90:ba:70:8a:41:aa:d4:6e:f6:3b:4a:9f:3d:
|
||||||
|
c0:8d:49:fa:7b:55:1d:59:ce:f5:5c:6e:6c:7a:96:8f:ed:67:
|
||||||
|
c2:59:da:48:10:16:c0:af:2b:b8:ac:ae:ea:60:e5:a3:28:a5:
|
||||||
|
57:a7:38:fa
|
||||||
81
MagiskOnWSA/DLL/cacerts/024c10e0.0
Normal file
81
MagiskOnWSA/DLL/cacerts/024c10e0.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIID1zCCAr+gAwIBAgIJAIdzf+9gLmi5MA0GCSqGSIb3DQEBCwUAMIGBMQswCQYD
|
||||||
|
VQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIwEAYDVQQHDAlKZXJ1c2FsZW0xEDAO
|
||||||
|
BgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5ldGZyZWUubGluazEkMCIGA1UEAwwb
|
||||||
|
TmV0RnJlZSBTaWduLCBLb3NoZXJTSU0gSVRDMB4XDTE4MDQyMjE2MzMxMloXDTI4
|
||||||
|
MDIyOTE2MzMxMlowgYExCzAJBgNVBAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQ
|
||||||
|
BgNVBAcMCUplcnVzYWxlbTEQMA4GA1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0
|
||||||
|
ZnJlZS5saW5rMSQwIgYDVQQDDBtOZXRGcmVlIFNpZ24sIEtvc2hlclNJTSBJVEMw
|
||||||
|
ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDP4S4XapIOvQv5wWbfBzg2
|
||||||
|
2fY1pWs030zMEOCVvnxMr9Fp1tgs/AVMY+UzkmawwbVDxZQL3goR7RqHPKkvsWXo
|
||||||
|
TEM1DOBajU9l3JRd8djnIMMG0u8wDXzFcVmno/Mh5fCXvhAr9Dd11KokYQKcn5wT
|
||||||
|
uDhJEhyEqB8Ho8BNvTyRts/HrkdJiSFEaSpr2J9BM/v9dIzINfBg/hxy7Em9B0pd
|
||||||
|
wgnKr6Bz0esC10hCYphjzaKpd/23jvfZHZKq4oFSaFzhzC5pbg4cSPCxRUN7kzxs
|
||||||
|
ezRhSoHhzMBXn4ay+VKhBKlKUOxT3STyxPFMYx6s40qlhlmaZ1tN4hLQrwD1jLw7
|
||||||
|
AgMBAAGjUDBOMB0GA1UdDgQWBBSPs38ZeH74K6wWVOIaW6P5ePY71zAfBgNVHSME
|
||||||
|
GDAWgBSPs38ZeH74K6wWVOIaW6P5ePY71zAMBgNVHRMEBTADAQH/MA0GCSqGSIb3
|
||||||
|
DQEBCwUAA4IBAQAcreRYyYYW+7gfAyxfv+AXV2NDlHMuQ6/gS13JgsObnoDcxhT1
|
||||||
|
cSbnAwbhvWXq7uAlD8Kbxp5uNZIt8N5ykqi4qjUXXuBMAZS75Rc9XDmmryBTfC+i
|
||||||
|
fql/2G6Itcj0VaoQK9gbnMumHqdK4wiIJHy4Wx2+b+3CeznwwWz5TWxBJmAqVPCN
|
||||||
|
hiu72Bh+W9wA2xuP65/FcKLpOpROQqUUT0vJd8UT46HMy7X2CXjB/ZWskGYn1V8Z
|
||||||
|
0aEvSW9FQDJllAXnTOLbXqHmY8/bdLraAL7Z7bJYLUxBcVOUe8+B+QN919kJOfk+
|
||||||
|
AYoB1o77qk3kH7jKxxPAH5G7SP2aYtylqb45
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
87:73:7f:ef:60:2e:68:b9
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, KosherSIM ITC"
|
||||||
|
Validity
|
||||||
|
Not Before: Apr 22 16:33:12 2018 GMT
|
||||||
|
Not After : Feb 29 16:33:12 2028 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, KosherSIM ITC"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:cf:e1:2e:17:6a:92:0e:bd:0b:f9:c1:66:df:07:
|
||||||
|
38:36:d9:f6:35:a5:6b:34:df:4c:cc:10:e0:95:be:
|
||||||
|
7c:4c:af:d1:69:d6:d8:2c:fc:05:4c:63:e5:33:92:
|
||||||
|
66:b0:c1:b5:43:c5:94:0b:de:0a:11:ed:1a:87:3c:
|
||||||
|
a9:2f:b1:65:e8:4c:43:35:0c:e0:5a:8d:4f:65:dc:
|
||||||
|
94:5d:f1:d8:e7:20:c3:06:d2:ef:30:0d:7c:c5:71:
|
||||||
|
59:a7:a3:f3:21:e5:f0:97:be:10:2b:f4:37:75:d4:
|
||||||
|
aa:24:61:02:9c:9f:9c:13:b8:38:49:12:1c:84:a8:
|
||||||
|
1f:07:a3:c0:4d:bd:3c:91:b6:cf:c7:ae:47:49:89:
|
||||||
|
21:44:69:2a:6b:d8:9f:41:33:fb:fd:74:8c:c8:35:
|
||||||
|
f0:60:fe:1c:72:ec:49:bd:07:4a:5d:c2:09:ca:af:
|
||||||
|
a0:73:d1:eb:02:d7:48:42:62:98:63:cd:a2:a9:77:
|
||||||
|
fd:b7:8e:f7:d9:1d:92:aa:e2:81:52:68:5c:e1:cc:
|
||||||
|
2e:69:6e:0e:1c:48:f0:b1:45:43:7b:93:3c:6c:7b:
|
||||||
|
34:61:4a:81:e1:cc:c0:57:9f:86:b2:f9:52:a1:04:
|
||||||
|
a9:4a:50:ec:53:dd:24:f2:c4:f1:4c:63:1e:ac:e3:
|
||||||
|
4a:a5:86:59:9a:67:5b:4d:e2:12:d0:af:00:f5:8c:
|
||||||
|
bc:3b
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
8F:B3:7F:19:78:7E:F8:2B:AC:16:54:E2:1A:5B:A3:F9:78:F6:3B:D7
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:8F:B3:7F:19:78:7E:F8:2B:AC:16:54:E2:1A:5B:A3:F9:78:F6:3B:D7
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
1c:ad:e4:58:c9:86:16:fb:b8:1f:03:2c:5f:bf:e0:17:57:63:
|
||||||
|
43:94:73:2e:43:af:e0:4b:5d:c9:82:c3:9b:9e:80:dc:c6:14:
|
||||||
|
f5:71:26:e7:03:06:e1:bd:65:ea:ee:e0:25:0f:c2:9b:c6:9e:
|
||||||
|
6e:35:92:2d:f0:de:72:92:a8:b8:aa:35:17:5e:e0:4c:01:94:
|
||||||
|
bb:e5:17:3d:5c:39:a6:af:20:53:7c:2f:a2:7e:a9:7f:d8:6e:
|
||||||
|
88:b5:c8:f4:55:aa:10:2b:d8:1b:9c:cb:a6:1e:a7:4a:e3:08:
|
||||||
|
88:24:7c:b8:5b:1d:be:6f:ed:c2:7b:39:f0:c1:6c:f9:4d:6c:
|
||||||
|
41:26:60:2a:54:f0:8d:86:2b:bb:d8:18:7e:5b:dc:00:db:1b:
|
||||||
|
8f:eb:9f:c5:70:a2:e9:3a:94:4e:42:a5:14:4f:4b:c9:77:c5:
|
||||||
|
13:e3:a1:cc:cb:b5:f6:09:78:c1:fd:95:ac:90:66:27:d5:5f:
|
||||||
|
19:d1:a1:2f:49:6f:45:40:32:65:94:05:e7:4c:e2:db:5e:a1:
|
||||||
|
e6:63:cf:db:74:ba:da:00:be:d9:ed:b2:58:2d:4c:41:71:53:
|
||||||
|
94:7b:cf:81:f9:03:7d:d7:d9:09:39:f9:3e:01:8a:01:d6:8e:
|
||||||
|
fb:aa:4d:e4:1f:b8:ca:c7:13:c0:1f:91:bb:48:fd:9a:62:dc:
|
||||||
|
a5:a9:be:39
|
||||||
123
MagiskOnWSA/DLL/cacerts/0888e817.0
Normal file
123
MagiskOnWSA/DLL/cacerts/0888e817.0
Normal file
@ -0,0 +1,123 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIF0zCCA7ugAwIBAgIUC+b3kBsjJ33F8+V3PFpQU+h6H0EwDQYJKoZIhvcNAQEL
|
||||||
|
BQAweTELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAGA1UEBwwJSmVy
|
||||||
|
dXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRmcmVlLmxpbmsx
|
||||||
|
HDAaBgNVBAMME05ldEZyZWUgU2lnbiAsWW9zc2kwHhcNMTkwODEyMTkwNDE5WhcN
|
||||||
|
MjkwNjIwMTkwNDE5WjB5MQswCQYDVQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIw
|
||||||
|
EAYDVQQHDAlKZXJ1c2FsZW0xEDAOBgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5l
|
||||||
|
dGZyZWUubGluazEcMBoGA1UEAwwTTmV0RnJlZSBTaWduICxZb3NzaTCCAiIwDQYJ
|
||||||
|
KoZIhvcNAQEBBQADggIPADCCAgoCggIBAN93Sx7QkE3PZVE1NylelP86p1oA2zv9
|
||||||
|
LQBQUiwKkT4Q4gWX8TkyJL/t9AXMxdyxBF31RdNY8DF32ujfowWQdjARB7UhY8Wq
|
||||||
|
A0YlSbD1RwknRrgt+g5Jq6LpeesKQ2PTp9qGDWVqLIZF8/xBlcJKD/pnNesUdGQ+
|
||||||
|
zLx6sro/Tme6LvaFNw4vHmfLGPnsBveqA27Vkz6j2Aay3STMWS7DMb/+aYBGUKvy
|
||||||
|
rZGd4WOXuCY8GkB1apguEFIBRKwWl40bKXgmKqbQSbrfP1Ze5i8kibPUW6cnGkQZ
|
||||||
|
d5o0GJ+1Vjis6rVULNZTFaoPiWTtZDf3atXtTsVI2MkiUPVJ7yh59OiIFENhPM5Q
|
||||||
|
zSjaix4cScMMhCagKMIcU4XfqcimZY4EnMqTq+FCPvmBPdUwbZnbkJOFe8lcueiP
|
||||||
|
k9Wc3xrvskbDILtfq8e0+AGDPa1ZNv+BkXeQG0bEYsvZTSolBXgXwgXJmtlrM0jR
|
||||||
|
3VzBAJTpzXmYel9o2HWpJcpBwPRjtNPXPrj9bXD6hlFdzMIdt8gx1KRZDXQB0ZJM
|
||||||
|
LHlIEg89BgByriuhLMZ6/nUKcK5Adjo7hyI+WvQrSsD8dM9bt3jqXTjjhNspnB14
|
||||||
|
LvpQeJF9AYhXo1YXYnQ3ipveiUt/ib9Y7BbD2zETOnWZZc7+EhUWBN4Q2Ajv5ddn
|
||||||
|
03zJE08oSiPHAgMBAAGjUzBRMB0GA1UdDgQWBBSZDKHvARiHteEbzaAccd8ZpZUL
|
||||||
|
mDAfBgNVHSMEGDAWgBSZDKHvARiHteEbzaAccd8ZpZULmDAPBgNVHRMBAf8EBTAD
|
||||||
|
AQH/MA0GCSqGSIb3DQEBCwUAA4ICAQBiSiaEOJQRzEm8Sa9ig5k8UEuicZRIt0jR
|
||||||
|
h/rlREa9En559XyxwXGXloFbmiUdlXV26BUtbWYn6J178xZ7B0x9istJq20ZeiZF
|
||||||
|
ABvv9DjuATbOLao65mowPL68C8R6ynRplVV7HE+zB3CUt4fyGEs/ud9n8DaqQysc
|
||||||
|
/im40yPqTobBKWJ1RWOrAddyHpQEqdXVxH2EkHTlyvcr9StTN4/pF5iVYeaniXnZ
|
||||||
|
PXqaEnYoqT9c2q8VAWc2a00dSrmHqw2TGKYJ2cSV8olkcdS6nknBsroQMd6Z8eZs
|
||||||
|
lGnwC1L4Nu1WJg8ZIy+Umcf0xAwSU3Zs7AhWIph+sO1Tc8iNFSLLotOKEO0xjBrZ
|
||||||
|
9ierDYZLAVx6XCIiArzgIM0XOwzPKTkwRZ7ip5n4mWx7GxmFJREAvwjRXuWNLZtj
|
||||||
|
s+IfCshjUfBUymYXn544mhou6uv9TeFQcxJ2RUzNr3xrxCuuriaUOGGBAaqrPpec
|
||||||
|
r2wWl/hlpjcw606NHbDlLzRUDO4Rwy1wZ5F6Pr7VXBqZy43tbB9VNbQErXdth0kH
|
||||||
|
UkjRGtv8zTO3MfG8FO1yv+QsWkHAAx73j8jGeSlLrma/KJAaJPpy0b1ud/12yCY4
|
||||||
|
GkFFhltXuc5f9tx+YvBUprWmZ9pd/tcFC+s/7XtpFU3STdfjlhZ6mzcC0IkxuNO9
|
||||||
|
HamDmBP6+A==
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
0b:e6:f7:90:1b:23:27:7d:c5:f3:e5:77:3c:5a:50:53:e8:7a:1f:41
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign ,Yossi"
|
||||||
|
Validity
|
||||||
|
Not Before: Aug 12 19:04:19 2019 GMT
|
||||||
|
Not After : Jun 20 19:04:19 2029 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign ,Yossi"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:df:77:4b:1e:d0:90:4d:cf:65:51:35:37:29:5e:
|
||||||
|
94:ff:3a:a7:5a:00:db:3b:fd:2d:00:50:52:2c:0a:
|
||||||
|
91:3e:10:e2:05:97:f1:39:32:24:bf:ed:f4:05:cc:
|
||||||
|
c5:dc:b1:04:5d:f5:45:d3:58:f0:31:77:da:e8:df:
|
||||||
|
a3:05:90:76:30:11:07:b5:21:63:c5:aa:03:46:25:
|
||||||
|
49:b0:f5:47:09:27:46:b8:2d:fa:0e:49:ab:a2:e9:
|
||||||
|
79:eb:0a:43:63:d3:a7:da:86:0d:65:6a:2c:86:45:
|
||||||
|
f3:fc:41:95:c2:4a:0f:fa:67:35:eb:14:74:64:3e:
|
||||||
|
cc:bc:7a:b2:ba:3f:4e:67:ba:2e:f6:85:37:0e:2f:
|
||||||
|
1e:67:cb:18:f9:ec:06:f7:aa:03:6e:d5:93:3e:a3:
|
||||||
|
d8:06:b2:dd:24:cc:59:2e:c3:31:bf:fe:69:80:46:
|
||||||
|
50:ab:f2:ad:91:9d:e1:63:97:b8:26:3c:1a:40:75:
|
||||||
|
6a:98:2e:10:52:01:44:ac:16:97:8d:1b:29:78:26:
|
||||||
|
2a:a6:d0:49:ba:df:3f:56:5e:e6:2f:24:89:b3:d4:
|
||||||
|
5b:a7:27:1a:44:19:77:9a:34:18:9f:b5:56:38:ac:
|
||||||
|
ea:b5:54:2c:d6:53:15:aa:0f:89:64:ed:64:37:f7:
|
||||||
|
6a:d5:ed:4e:c5:48:d8:c9:22:50:f5:49:ef:28:79:
|
||||||
|
f4:e8:88:14:43:61:3c:ce:50:cd:28:da:8b:1e:1c:
|
||||||
|
49:c3:0c:84:26:a0:28:c2:1c:53:85:df:a9:c8:a6:
|
||||||
|
65:8e:04:9c:ca:93:ab:e1:42:3e:f9:81:3d:d5:30:
|
||||||
|
6d:99:db:90:93:85:7b:c9:5c:b9:e8:8f:93:d5:9c:
|
||||||
|
df:1a:ef:b2:46:c3:20:bb:5f:ab:c7:b4:f8:01:83:
|
||||||
|
3d:ad:59:36:ff:81:91:77:90:1b:46:c4:62:cb:d9:
|
||||||
|
4d:2a:25:05:78:17:c2:05:c9:9a:d9:6b:33:48:d1:
|
||||||
|
dd:5c:c1:00:94:e9:cd:79:98:7a:5f:68:d8:75:a9:
|
||||||
|
25:ca:41:c0:f4:63:b4:d3:d7:3e:b8:fd:6d:70:fa:
|
||||||
|
86:51:5d:cc:c2:1d:b7:c8:31:d4:a4:59:0d:74:01:
|
||||||
|
d1:92:4c:2c:79:48:12:0f:3d:06:00:72:ae:2b:a1:
|
||||||
|
2c:c6:7a:fe:75:0a:70:ae:40:76:3a:3b:87:22:3e:
|
||||||
|
5a:f4:2b:4a:c0:fc:74:cf:5b:b7:78:ea:5d:38:e3:
|
||||||
|
84:db:29:9c:1d:78:2e:fa:50:78:91:7d:01:88:57:
|
||||||
|
a3:56:17:62:74:37:8a:9b:de:89:4b:7f:89:bf:58:
|
||||||
|
ec:16:c3:db:31:13:3a:75:99:65:ce:fe:12:15:16:
|
||||||
|
04:de:10:d8:08:ef:e5:d7:67:d3:7c:c9:13:4f:28:
|
||||||
|
4a:23:c7
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
99:0C:A1:EF:01:18:87:B5:E1:1B:CD:A0:1C:71:DF:19:A5:95:0B:98
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:99:0C:A1:EF:01:18:87:B5:E1:1B:CD:A0:1C:71:DF:19:A5:95:0B:98
|
||||||
|
|
||||||
|
X509v3 Basic Constraints: critical
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
62:4a:26:84:38:94:11:cc:49:bc:49:af:62:83:99:3c:50:4b:
|
||||||
|
a2:71:94:48:b7:48:d1:87:fa:e5:44:46:bd:12:7e:79:f5:7c:
|
||||||
|
b1:c1:71:97:96:81:5b:9a:25:1d:95:75:76:e8:15:2d:6d:66:
|
||||||
|
27:e8:9d:7b:f3:16:7b:07:4c:7d:8a:cb:49:ab:6d:19:7a:26:
|
||||||
|
45:00:1b:ef:f4:38:ee:01:36:ce:2d:aa:3a:e6:6a:30:3c:be:
|
||||||
|
bc:0b:c4:7a:ca:74:69:95:55:7b:1c:4f:b3:07:70:94:b7:87:
|
||||||
|
f2:18:4b:3f:b9:df:67:f0:36:aa:43:2b:1c:fe:29:b8:d3:23:
|
||||||
|
ea:4e:86:c1:29:62:75:45:63:ab:01:d7:72:1e:94:04:a9:d5:
|
||||||
|
d5:c4:7d:84:90:74:e5:ca:f7:2b:f5:2b:53:37:8f:e9:17:98:
|
||||||
|
95:61:e6:a7:89:79:d9:3d:7a:9a:12:76:28:a9:3f:5c:da:af:
|
||||||
|
15:01:67:36:6b:4d:1d:4a:b9:87:ab:0d:93:18:a6:09:d9:c4:
|
||||||
|
95:f2:89:64:71:d4:ba:9e:49:c1:b2:ba:10:31:de:99:f1:e6:
|
||||||
|
6c:94:69:f0:0b:52:f8:36:ed:56:26:0f:19:23:2f:94:99:c7:
|
||||||
|
f4:c4:0c:12:53:76:6c:ec:08:56:22:98:7e:b0:ed:53:73:c8:
|
||||||
|
8d:15:22:cb:a2:d3:8a:10:ed:31:8c:1a:d9:f6:27:ab:0d:86:
|
||||||
|
4b:01:5c:7a:5c:22:22:02:bc:e0:20:cd:17:3b:0c:cf:29:39:
|
||||||
|
30:45:9e:e2:a7:99:f8:99:6c:7b:1b:19:85:25:11:00:bf:08:
|
||||||
|
d1:5e:e5:8d:2d:9b:63:b3:e2:1f:0a:c8:63:51:f0:54:ca:66:
|
||||||
|
17:9f:9e:38:9a:1a:2e:ea:eb:fd:4d:e1:50:73:12:76:45:4c:
|
||||||
|
cd:af:7c:6b:c4:2b:ae:ae:26:94:38:61:81:01:aa:ab:3e:97:
|
||||||
|
9c:af:6c:16:97:f8:65:a6:37:30:eb:4e:8d:1d:b0:e5:2f:34:
|
||||||
|
54:0c:ee:11:c3:2d:70:67:91:7a:3e:be:d5:5c:1a:99:cb:8d:
|
||||||
|
ed:6c:1f:55:35:b4:04:ad:77:6d:87:49:07:52:48:d1:1a:db:
|
||||||
|
fc:cd:33:b7:31:f1:bc:14:ed:72:bf:e4:2c:5a:41:c0:03:1e:
|
||||||
|
f7:8f:c8:c6:79:29:4b:ae:66:bf:28:90:1a:24:fa:72:d1:bd:
|
||||||
|
6e:77:fd:76:c8:26:38:1a:41:45:86:5b:57:b9:ce:5f:f6:dc:
|
||||||
|
7e:62:f0:54:a6:b5:a6:67:da:5d:fe:d7:05:0b:eb:3f:ed:7b:
|
||||||
|
69:15:4d:d2:4d:d7:e3:96:16:7a:9b:37:02:d0:89:31:b8:d3:
|
||||||
|
bd:1d:a9:83:98:13:fa:f8
|
||||||
81
MagiskOnWSA/DLL/cacerts/0b4055f7.0
Normal file
81
MagiskOnWSA/DLL/cacerts/0b4055f7.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIID5TCCAs2gAwIBAgIJALnD1+pTBr26MA0GCSqGSIb3DQEBCwUAMIGIMQswCQYD
|
||||||
|
VQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIwEAYDVQQHDAlKZXJ1c2FsZW0xEDAO
|
||||||
|
BgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5ldGZyZWUubGluazErMCkGA1UEAwwi
|
||||||
|
TmV0RnJlZSBTaWduICwgU2ltS2FzaGVyIC0gVHJpcGxlQzAeFw0xNzA2MjYxNzUx
|
||||||
|
MDlaFw0yNzA1MDUxNzUxMDlaMIGIMQswCQYDVQQGEwJJTDEPMA0GA1UECAwGaXNy
|
||||||
|
YWVsMRIwEAYDVQQHDAlKZXJ1c2FsZW0xEDAOBgNVBAoMB05ldEZyZWUxFTATBgNV
|
||||||
|
BAsMDG5ldGZyZWUubGluazErMCkGA1UEAwwiTmV0RnJlZSBTaWduICwgU2ltS2Fz
|
||||||
|
aGVyIC0gVHJpcGxlQzCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAMM5
|
||||||
|
FtnDwNn6ErV5rZhc9VV1ujRRSDfK6n9TjK0zaHKhwrTgzj6YxzopfspqwoZM6QqS
|
||||||
|
ivNtDLKfQyVFUYGAFQiQgShQNYS8GheXqTI/U7SdWgKFUkdcOPmzNusYwa+G0cLz
|
||||||
|
NiRkKS+yRm+sGf+QLu18KACoc5FbL1+rM8OR0aCG2md/K8Z6xnYm371BGEiZjjhX
|
||||||
|
4tGL7SonHPs35Ga4LI6pJfUUItcliWBW6HnwcRk7Ilq/9q5gUjR5sbIvt0+9hdhj
|
||||||
|
1UQjE4gcsPzN5Fc+RvwDXBqozIk8cPVSNycwY2VZ4FofEAjtanS9R5LrshKK6Oi2
|
||||||
|
n61xzE/vHMVUJKYXqcUCAwEAAaNQME4wHQYDVR0OBBYEFFr8sgox5u0dhxiDDE7A
|
||||||
|
n11wTtBNMB8GA1UdIwQYMBaAFFr8sgox5u0dhxiDDE7An11wTtBNMAwGA1UdEwQF
|
||||||
|
MAMBAf8wDQYJKoZIhvcNAQELBQADggEBAJSPrJ3a3M0m+dHuGevOMKOjP5NexEiT
|
||||||
|
hWUX86/b7u0rKfphqGsl4y+wXRCiMydOwZCMg7MQjYvmT8XoN0rlVu73BxpcxYJg
|
||||||
|
I6Il4erTBSitCiXF39RQ3XW/akAqgAsaPSD4TdSImCVHW3UgJxHtRcM4SodIo+Zh
|
||||||
|
7WuNXCC5ET/C4y2EeMOtkWIcuncjPrL7pJwwiHPYjhK+SiievAzDGhrXbJxAmgy2
|
||||||
|
wsV6qU03j0I3fH1jC23SJRA8GudrZqUoTcfQmERPnyTiTp1Hn271crZ8ai9MPZQm
|
||||||
|
c+wKYHlblPbaj0EA06Dh6uCexhyTxa0wRtTODIfCxoHJMWWWPKb9H3k=
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
b9:c3:d7:ea:53:06:bd:ba
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , SimKasher - TripleC"
|
||||||
|
Validity
|
||||||
|
Not Before: Jun 26 17:51:09 2017 GMT
|
||||||
|
Not After : May 5 17:51:09 2027 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , SimKasher - TripleC"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:c3:39:16:d9:c3:c0:d9:fa:12:b5:79:ad:98:5c:
|
||||||
|
f5:55:75:ba:34:51:48:37:ca:ea:7f:53:8c:ad:33:
|
||||||
|
68:72:a1:c2:b4:e0:ce:3e:98:c7:3a:29:7e:ca:6a:
|
||||||
|
c2:86:4c:e9:0a:92:8a:f3:6d:0c:b2:9f:43:25:45:
|
||||||
|
51:81:80:15:08:90:81:28:50:35:84:bc:1a:17:97:
|
||||||
|
a9:32:3f:53:b4:9d:5a:02:85:52:47:5c:38:f9:b3:
|
||||||
|
36:eb:18:c1:af:86:d1:c2:f3:36:24:64:29:2f:b2:
|
||||||
|
46:6f:ac:19:ff:90:2e:ed:7c:28:00:a8:73:91:5b:
|
||||||
|
2f:5f:ab:33:c3:91:d1:a0:86:da:67:7f:2b:c6:7a:
|
||||||
|
c6:76:26:df:bd:41:18:48:99:8e:38:57:e2:d1:8b:
|
||||||
|
ed:2a:27:1c:fb:37:e4:66:b8:2c:8e:a9:25:f5:14:
|
||||||
|
22:d7:25:89:60:56:e8:79:f0:71:19:3b:22:5a:bf:
|
||||||
|
f6:ae:60:52:34:79:b1:b2:2f:b7:4f:bd:85:d8:63:
|
||||||
|
d5:44:23:13:88:1c:b0:fc:cd:e4:57:3e:46:fc:03:
|
||||||
|
5c:1a:a8:cc:89:3c:70:f5:52:37:27:30:63:65:59:
|
||||||
|
e0:5a:1f:10:08:ed:6a:74:bd:47:92:eb:b2:12:8a:
|
||||||
|
e8:e8:b6:9f:ad:71:cc:4f:ef:1c:c5:54:24:a6:17:
|
||||||
|
a9:c5
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
5A:FC:B2:0A:31:E6:ED:1D:87:18:83:0C:4E:C0:9F:5D:70:4E:D0:4D
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:5A:FC:B2:0A:31:E6:ED:1D:87:18:83:0C:4E:C0:9F:5D:70:4E:D0:4D
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
94:8f:ac:9d:da:dc:cd:26:f9:d1:ee:19:eb:ce:30:a3:a3:3f:
|
||||||
|
93:5e:c4:48:93:85:65:17:f3:af:db:ee:ed:2b:29:fa:61:a8:
|
||||||
|
6b:25:e3:2f:b0:5d:10:a2:33:27:4e:c1:90:8c:83:b3:10:8d:
|
||||||
|
8b:e6:4f:c5:e8:37:4a:e5:56:ee:f7:07:1a:5c:c5:82:60:23:
|
||||||
|
a2:25:e1:ea:d3:05:28:ad:0a:25:c5:df:d4:50:dd:75:bf:6a:
|
||||||
|
40:2a:80:0b:1a:3d:20:f8:4d:d4:88:98:25:47:5b:75:20:27:
|
||||||
|
11:ed:45:c3:38:4a:87:48:a3:e6:61:ed:6b:8d:5c:20:b9:11:
|
||||||
|
3f:c2:e3:2d:84:78:c3:ad:91:62:1c:ba:77:23:3e:b2:fb:a4:
|
||||||
|
9c:30:88:73:d8:8e:12:be:4a:28:9e:bc:0c:c3:1a:1a:d7:6c:
|
||||||
|
9c:40:9a:0c:b6:c2:c5:7a:a9:4d:37:8f:42:37:7c:7d:63:0b:
|
||||||
|
6d:d2:25:10:3c:1a:e7:6b:66:a5:28:4d:c7:d0:98:44:4f:9f:
|
||||||
|
24:e2:4e:9d:47:9f:6e:f5:72:b6:7c:6a:2f:4c:3d:94:26:73:
|
||||||
|
ec:0a:60:79:5b:94:f6:da:8f:41:00:d3:a0:e1:ea:e0:9e:c6:
|
||||||
|
1c:93:c5:ad:30:46:d4:ce:0c:87:c2:c6:81:c9:31:65:96:3c:
|
||||||
|
a6:fd:1f:79
|
||||||
123
MagiskOnWSA/DLL/cacerts/281f8e47.0
Normal file
123
MagiskOnWSA/DLL/cacerts/281f8e47.0
Normal file
@ -0,0 +1,123 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIF1zCCA7+gAwIBAgIUVRcB1uWuaruggL9hYC31+1eO8wEwDQYJKoZIhvcNAQEL
|
||||||
|
BQAwezELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAGA1UEBwwJSmVy
|
||||||
|
dXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRmcmVlLmxpbmsx
|
||||||
|
HjAcBgNVBAMMFU5ldEZyZWUgU2lnbiwgQW1pdE5ldDAeFw0yMDEyMTUxMjQ1MTJa
|
||||||
|
Fw0zMDEyMTMxMjQ1MTJaMHsxCzAJBgNVBAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwx
|
||||||
|
EjAQBgNVBAcMCUplcnVzYWxlbTEQMA4GA1UECgwHTmV0RnJlZTEVMBMGA1UECwwM
|
||||||
|
bmV0ZnJlZS5saW5rMR4wHAYDVQQDDBVOZXRGcmVlIFNpZ24sIEFtaXROZXQwggIi
|
||||||
|
MA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQDNCFBv23NbP80PnYb1j8EQFbUB
|
||||||
|
IUG7ZaR/7acSU5+zFpagTX1HASboUZ6sTVSKYIM/cJ8J6B97PkVb4J1I6+pVa7x3
|
||||||
|
LNJqReP9fCSknshNsc0NlxB4xcCnheov4HYrgW37hznEbiSrR+hDHR0W2A96IEHx
|
||||||
|
x71A3/mQ5Rl2jXv+negYa/xNK8uh+6xGN/zrowPNc8c4EC94hCpuwAzYqoXR+Iph
|
||||||
|
hcdK8WKIge3isEtpYYcswk8U7YIXe6sSAUrVcXaZURTAX00LPptXM92l4C+pBQ4j
|
||||||
|
xgOxXSVJWig7QLJuCPw0BjlLAVwvc4zWib/6tBUcHUZYcZ9+jm7D9sUkD3/Q2WDm
|
||||||
|
BlFMGhGuIGW4FeiX+kSGGYlskds4RYsf6iHVLBAUc3MhtXRPSt3RgTLw823b4dwj
|
||||||
|
OG/0RWjhynRHWmBvW+mWZgGPDZ/VxDR2dltWXGcWyz9hfQNBNhUberBhtLpydHfK
|
||||||
|
4qpYNr7yWBJbXDsXTM6Y5rYVHiWYz/Mf47SEMUhGnqHDlENWNHVAz8LD4xmeywLl
|
||||||
|
1HkcMygyQMKtfTQ8V2Y/7cftfSrTGfG4uTKvewGbsET+ZS0G2aInFijQfnKrhWc+
|
||||||
|
foAVimtJY0KssNDzHpcMMjJAqoIulP4/Mj4ny7XLEIba8o3VI8g20lfZPpo3jl1H
|
||||||
|
KpXNpVOTOR+h/PNUiQIDAQABo1MwUTAdBgNVHQ4EFgQUNtscwInvEKf/FZdrLO1r
|
||||||
|
3yBoFi8wHwYDVR0jBBgwFoAUNtscwInvEKf/FZdrLO1r3yBoFi8wDwYDVR0TAQH/
|
||||||
|
BAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAgEAidKPUdFTIOeiE4CemLVrns6EkNd5
|
||||||
|
zbfi3jeYCvTSzf/ij0Xu7dzZ8valIylgaKQaT3DizHbhtWbmeMbz/0uE08fYIzsY
|
||||||
|
JJBMTf9IoB6bjWcGqWuszM0rVO/wWKhxTG4w+VSScFLT2PHS/8PHpmcQEo8j2QWf
|
||||||
|
+4pAfruFIkoCfApYQE3GaJRZ/vrPGFBfnWEo5K57DivHN/raVu26x83twI6rnYlO
|
||||||
|
htI+p3gV5LZFn66txZAmicA7LFp7wbwTDJwWX+XvOhuHlE11mMkWY3oFei/EZiub
|
||||||
|
n+2Brmt7p9cX2Wkrw5eZdFenGyM8vmzEEExOnuraojfHS/p5G3r4j92Kt/yBZVfK
|
||||||
|
RWqooVQ4J30YL6Z90Rz++wExvsBaYtY+ZjYvso6Mi7N42iemz7fR2h+VBv9BcUKs
|
||||||
|
HET94gNwVsYi7++uqjLyB1NxzpFcPQmfGEJZeQiDeyfY1W2KKiUEsTpi6xu9Bkki
|
||||||
|
dAOiEmiwk2IAv+a0Sd+FalvURx6ldrqCy3ki8offnrPcjedY8kjnyijdOTuj6dTh
|
||||||
|
ybzqxcXItfxrpA+s0bWFh4DK3kP8uUsPBz4q5aHLxtTHMFULXRt4gBifV6InysNx
|
||||||
|
UuqP4yTPCR3QoES4Aba7PR18RnTZXnYWXnsWSspEf1Cf3jTkI9OpB8MHrWh+7v5O
|
||||||
|
AiH5GAGaSCVrseI=
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
55:17:01:d6:e5:ae:6a:bb:a0:80:bf:61:60:2d:f5:fb:57:8e:f3:01
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, AmitNet"
|
||||||
|
Validity
|
||||||
|
Not Before: Dec 15 12:45:12 2020 GMT
|
||||||
|
Not After : Dec 13 12:45:12 2030 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, AmitNet"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:cd:08:50:6f:db:73:5b:3f:cd:0f:9d:86:f5:8f:
|
||||||
|
c1:10:15:b5:01:21:41:bb:65:a4:7f:ed:a7:12:53:
|
||||||
|
9f:b3:16:96:a0:4d:7d:47:01:26:e8:51:9e:ac:4d:
|
||||||
|
54:8a:60:83:3f:70:9f:09:e8:1f:7b:3e:45:5b:e0:
|
||||||
|
9d:48:eb:ea:55:6b:bc:77:2c:d2:6a:45:e3:fd:7c:
|
||||||
|
24:a4:9e:c8:4d:b1:cd:0d:97:10:78:c5:c0:a7:85:
|
||||||
|
ea:2f:e0:76:2b:81:6d:fb:87:39:c4:6e:24:ab:47:
|
||||||
|
e8:43:1d:1d:16:d8:0f:7a:20:41:f1:c7:bd:40:df:
|
||||||
|
f9:90:e5:19:76:8d:7b:fe:9d:e8:18:6b:fc:4d:2b:
|
||||||
|
cb:a1:fb:ac:46:37:fc:eb:a3:03:cd:73:c7:38:10:
|
||||||
|
2f:78:84:2a:6e:c0:0c:d8:aa:85:d1:f8:8a:61:85:
|
||||||
|
c7:4a:f1:62:88:81:ed:e2:b0:4b:69:61:87:2c:c2:
|
||||||
|
4f:14:ed:82:17:7b:ab:12:01:4a:d5:71:76:99:51:
|
||||||
|
14:c0:5f:4d:0b:3e:9b:57:33:dd:a5:e0:2f:a9:05:
|
||||||
|
0e:23:c6:03:b1:5d:25:49:5a:28:3b:40:b2:6e:08:
|
||||||
|
fc:34:06:39:4b:01:5c:2f:73:8c:d6:89:bf:fa:b4:
|
||||||
|
15:1c:1d:46:58:71:9f:7e:8e:6e:c3:f6:c5:24:0f:
|
||||||
|
7f:d0:d9:60:e6:06:51:4c:1a:11:ae:20:65:b8:15:
|
||||||
|
e8:97:fa:44:86:19:89:6c:91:db:38:45:8b:1f:ea:
|
||||||
|
21:d5:2c:10:14:73:73:21:b5:74:4f:4a:dd:d1:81:
|
||||||
|
32:f0:f3:6d:db:e1:dc:23:38:6f:f4:45:68:e1:ca:
|
||||||
|
74:47:5a:60:6f:5b:e9:96:66:01:8f:0d:9f:d5:c4:
|
||||||
|
34:76:76:5b:56:5c:67:16:cb:3f:61:7d:03:41:36:
|
||||||
|
15:1b:7a:b0:61:b4:ba:72:74:77:ca:e2:aa:58:36:
|
||||||
|
be:f2:58:12:5b:5c:3b:17:4c:ce:98:e6:b6:15:1e:
|
||||||
|
25:98:cf:f3:1f:e3:b4:84:31:48:46:9e:a1:c3:94:
|
||||||
|
43:56:34:75:40:cf:c2:c3:e3:19:9e:cb:02:e5:d4:
|
||||||
|
79:1c:33:28:32:40:c2:ad:7d:34:3c:57:66:3f:ed:
|
||||||
|
c7:ed:7d:2a:d3:19:f1:b8:b9:32:af:7b:01:9b:b0:
|
||||||
|
44:fe:65:2d:06:d9:a2:27:16:28:d0:7e:72:ab:85:
|
||||||
|
67:3e:7e:80:15:8a:6b:49:63:42:ac:b0:d0:f3:1e:
|
||||||
|
97:0c:32:32:40:aa:82:2e:94:fe:3f:32:3e:27:cb:
|
||||||
|
b5:cb:10:86:da:f2:8d:d5:23:c8:36:d2:57:d9:3e:
|
||||||
|
9a:37:8e:5d:47:2a:95:cd:a5:53:93:39:1f:a1:fc:
|
||||||
|
f3:54:89
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
36:DB:1C:C0:89:EF:10:A7:FF:15:97:6B:2C:ED:6B:DF:20:68:16:2F
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:36:DB:1C:C0:89:EF:10:A7:FF:15:97:6B:2C:ED:6B:DF:20:68:16:2F
|
||||||
|
|
||||||
|
X509v3 Basic Constraints: critical
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
89:d2:8f:51:d1:53:20:e7:a2:13:80:9e:98:b5:6b:9e:ce:84:
|
||||||
|
90:d7:79:cd:b7:e2:de:37:98:0a:f4:d2:cd:ff:e2:8f:45:ee:
|
||||||
|
ed:dc:d9:f2:f6:a5:23:29:60:68:a4:1a:4f:70:e2:cc:76:e1:
|
||||||
|
b5:66:e6:78:c6:f3:ff:4b:84:d3:c7:d8:23:3b:18:24:90:4c:
|
||||||
|
4d:ff:48:a0:1e:9b:8d:67:06:a9:6b:ac:cc:cd:2b:54:ef:f0:
|
||||||
|
58:a8:71:4c:6e:30:f9:54:92:70:52:d3:d8:f1:d2:ff:c3:c7:
|
||||||
|
a6:67:10:12:8f:23:d9:05:9f:fb:8a:40:7e:bb:85:22:4a:02:
|
||||||
|
7c:0a:58:40:4d:c6:68:94:59:fe:fa:cf:18:50:5f:9d:61:28:
|
||||||
|
e4:ae:7b:0e:2b:c7:37:fa:da:56:ed:ba:c7:cd:ed:c0:8e:ab:
|
||||||
|
9d:89:4e:86:d2:3e:a7:78:15:e4:b6:45:9f:ae:ad:c5:90:26:
|
||||||
|
89:c0:3b:2c:5a:7b:c1:bc:13:0c:9c:16:5f:e5:ef:3a:1b:87:
|
||||||
|
94:4d:75:98:c9:16:63:7a:05:7a:2f:c4:66:2b:9b:9f:ed:81:
|
||||||
|
ae:6b:7b:a7:d7:17:d9:69:2b:c3:97:99:74:57:a7:1b:23:3c:
|
||||||
|
be:6c:c4:10:4c:4e:9e:ea:da:a2:37:c7:4b:fa:79:1b:7a:f8:
|
||||||
|
8f:dd:8a:b7:fc:81:65:57:ca:45:6a:a8:a1:54:38:27:7d:18:
|
||||||
|
2f:a6:7d:d1:1c:fe:fb:01:31:be:c0:5a:62:d6:3e:66:36:2f:
|
||||||
|
b2:8e:8c:8b:b3:78:da:27:a6:cf:b7:d1:da:1f:95:06:ff:41:
|
||||||
|
71:42:ac:1c:44:fd:e2:03:70:56:c6:22:ef:ef:ae:aa:32:f2:
|
||||||
|
07:53:71:ce:91:5c:3d:09:9f:18:42:59:79:08:83:7b:27:d8:
|
||||||
|
d5:6d:8a:2a:25:04:b1:3a:62:eb:1b:bd:06:49:22:74:03:a2:
|
||||||
|
12:68:b0:93:62:00:bf:e6:b4:49:df:85:6a:5b:d4:47:1e:a5:
|
||||||
|
76:ba:82:cb:79:22:f2:87:df:9e:b3:dc:8d:e7:58:f2:48:e7:
|
||||||
|
ca:28:dd:39:3b:a3:e9:d4:e1:c9:bc:ea:c5:c5:c8:b5:fc:6b:
|
||||||
|
a4:0f:ac:d1:b5:85:87:80:ca:de:43:fc:b9:4b:0f:07:3e:2a:
|
||||||
|
e5:a1:cb:c6:d4:c7:30:55:0b:5d:1b:78:80:18:9f:57:a2:27:
|
||||||
|
ca:c3:71:52:ea:8f:e3:24:cf:09:1d:d0:a0:44:b8:01:b6:bb:
|
||||||
|
3d:1d:7c:46:74:d9:5e:76:16:5e:7b:16:4a:ca:44:7f:50:9f:
|
||||||
|
de:34:e4:23:d3:a9:07:c3:07:ad:68:7e:ee:fe:4e:02:21:f9:
|
||||||
|
18:01:9a:48:25:6b:b1:e2
|
||||||
123
MagiskOnWSA/DLL/cacerts/2ef957f0.0
Normal file
123
MagiskOnWSA/DLL/cacerts/2ef957f0.0
Normal file
@ -0,0 +1,123 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIF4zCCA8ugAwIBAgIUAkc9yNk/4jz9hPra/7vONeYwrtIwDQYJKoZIhvcNAQEL
|
||||||
|
BQAwgYAxCzAJBgNVBAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcMCUpl
|
||||||
|
cnVzYWxlbTEQMA4GA1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0ZnJlZS5saW5r
|
||||||
|
MSMwIQYDVQQDDBpOZXRGcmVlIFNpZ24sIElCIC0gc3BvdG5ldDAeFw0yMDA1MTMw
|
||||||
|
ODIzMjJaFw0zMDA1MTEwODIzMjJaMIGAMQswCQYDVQQGEwJJTDEPMA0GA1UECAwG
|
||||||
|
aXNyYWVsMRIwEAYDVQQHDAlKZXJ1c2FsZW0xEDAOBgNVBAoMB05ldEZyZWUxFTAT
|
||||||
|
BgNVBAsMDG5ldGZyZWUubGluazEjMCEGA1UEAwwaTmV0RnJlZSBTaWduLCBJQiAt
|
||||||
|
IHNwb3RuZXQwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQDNgVcx94Ap
|
||||||
|
985mKOzFx4/lExkRuI8f9hdAUY9XqE94X7fT8hmCP6pxy/7+JzMjfn/YMmECea51
|
||||||
|
cuV4ZH+xUZ5WxoQajx/ICJtfaOSV/YIkB40o6JcN95EhKuickdiWnGFjsOZwc1Wj
|
||||||
|
sqHzjNZJWvV3KnoUGJQfc0F7/Th7HvQoNRqAkUBcXS521m7GqndlmE5zAo7WCD/N
|
||||||
|
7ggWeO2g8xPOW5YldHZ9mMSZXVYLRn95wrEtBX4SVXqSWdlPAE+m1jbHU2Gu2eM5
|
||||||
|
LxichbN1FQRL63aeZJjSgOEDaWnASLlqq+rnIWiecoYOGe7qoNl+jGaNAQmg3bq0
|
||||||
|
nOYouRu7nUGQbOn/eX3BwHEVx9WKiUPHop24NPW70wXXfEU0UNM3FjuU/V/uFA89
|
||||||
|
RQZRcg28O3SrzLybBGwCo+Kp5Sp54a59/Uw5FvX9OSsHX/QqdMxtFWlXvwqeuV8p
|
||||||
|
DOlYrAU8WrttR4ruZ3OJ5Rd5w8eu0U2s+dQLrMVgJo2ji2Ji9tBoHId50KVSBDgq
|
||||||
|
TGs40TB3cnWeO0kf3luz8CgH/+ls08ruDSXpA88FL6adFLfMhfDgBjq9OM0twL31
|
||||||
|
dVeZvxplqSvLQqiO7uc6s2qzGN/KaMP41eZaWuuiwZtwnFbArg8H2zQDpcLM72Ha
|
||||||
|
yeqQUAHHIjDx4pmww9yeSk8a1a0Pt71SLwIDAQABo1MwUTAdBgNVHQ4EFgQUU0dF
|
||||||
|
eW32zoZaL/BW2H++Jj5tyK8wHwYDVR0jBBgwFoAUU0dFeW32zoZaL/BW2H++Jj5t
|
||||||
|
yK8wDwYDVR0TAQH/BAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAgEAlwsfMiO4Bg0E
|
||||||
|
ciN+dAs0+i9grg0CzD2qUpVl6rDN6Vq12DoLgIL/qAH9wiKDPfl9LniwLQfkK/HE
|
||||||
|
U868x90OOaopBhrO+SPfQX0grz2xYDxnMJXuBKDGr8jHy+QeRq2JN4Sq9BW8Ayfo
|
||||||
|
9Z3xFpGAf0pohvT5ipeR45u9BZsGBH49iur+snf+t4PL7we7Q4rZ5Z1ZFO0ctlGh
|
||||||
|
hkS6cGpsmkrH/ysQpD07JmN/Iwklz8xKyiRdRc1qL5BBbLOedawpPNA6PuVBNDg2
|
||||||
|
jLDZyiirC9zBUTIUohruHQ6lWyHxvx5+BcwmU2LEZMfIVFddQ/KOZ5FcsscDUxvg
|
||||||
|
YvFdB7iIZNOMBASowXcp7qq6gySkA0qoD+O55nvDocKkqsImuacmOAHmgXfd6zAV
|
||||||
|
QPo/l/qaMDldpYoKL3WI3GlViTKhBFBKqgb9iR8oKgzMdi+A95XzbHaFFrvG0NaU
|
||||||
|
Qdiuvp7e09Ja44RAbz2Q4JyDhoo1xxgvfCluUMWWT0AdE9UdV88lpaaD3iPHPOao
|
||||||
|
E1QFv5hb04gCSU5V+F8a/SULWUitu7NdiBZQRwYbk8xS7Ta8Qcn1/ICJHsx3FKbJ
|
||||||
|
Z2vhVxCoT22IAdbcd4AL2pJS3EqNZlydfcUg42vCDovKheTWNYQzBW5c0IKPKAq9
|
||||||
|
Z52Mpo8iek5gwCa8k8r1ZTiyODgDO7Y=
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
02:47:3d:c8:d9:3f:e2:3c:fd:84:fa:da:ff:bb:ce:35:e6:30:ae:d2
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, IB - spotnet"
|
||||||
|
Validity
|
||||||
|
Not Before: May 13 08:23:22 2020 GMT
|
||||||
|
Not After : May 11 08:23:22 2030 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, IB - spotnet"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:cd:81:57:31:f7:80:29:f7:ce:66:28:ec:c5:c7:
|
||||||
|
8f:e5:13:19:11:b8:8f:1f:f6:17:40:51:8f:57:a8:
|
||||||
|
4f:78:5f:b7:d3:f2:19:82:3f:aa:71:cb:fe:fe:27:
|
||||||
|
33:23:7e:7f:d8:32:61:02:79:ae:75:72:e5:78:64:
|
||||||
|
7f:b1:51:9e:56:c6:84:1a:8f:1f:c8:08:9b:5f:68:
|
||||||
|
e4:95:fd:82:24:07:8d:28:e8:97:0d:f7:91:21:2a:
|
||||||
|
e8:9c:91:d8:96:9c:61:63:b0:e6:70:73:55:a3:b2:
|
||||||
|
a1:f3:8c:d6:49:5a:f5:77:2a:7a:14:18:94:1f:73:
|
||||||
|
41:7b:fd:38:7b:1e:f4:28:35:1a:80:91:40:5c:5d:
|
||||||
|
2e:76:d6:6e:c6:aa:77:65:98:4e:73:02:8e:d6:08:
|
||||||
|
3f:cd:ee:08:16:78:ed:a0:f3:13:ce:5b:96:25:74:
|
||||||
|
76:7d:98:c4:99:5d:56:0b:46:7f:79:c2:b1:2d:05:
|
||||||
|
7e:12:55:7a:92:59:d9:4f:00:4f:a6:d6:36:c7:53:
|
||||||
|
61:ae:d9:e3:39:2f:18:9c:85:b3:75:15:04:4b:eb:
|
||||||
|
76:9e:64:98:d2:80:e1:03:69:69:c0:48:b9:6a:ab:
|
||||||
|
ea:e7:21:68:9e:72:86:0e:19:ee:ea:a0:d9:7e:8c:
|
||||||
|
66:8d:01:09:a0:dd:ba:b4:9c:e6:28:b9:1b:bb:9d:
|
||||||
|
41:90:6c:e9:ff:79:7d:c1:c0:71:15:c7:d5:8a:89:
|
||||||
|
43:c7:a2:9d:b8:34:f5:bb:d3:05:d7:7c:45:34:50:
|
||||||
|
d3:37:16:3b:94:fd:5f:ee:14:0f:3d:45:06:51:72:
|
||||||
|
0d:bc:3b:74:ab:cc:bc:9b:04:6c:02:a3:e2:a9:e5:
|
||||||
|
2a:79:e1:ae:7d:fd:4c:39:16:f5:fd:39:2b:07:5f:
|
||||||
|
f4:2a:74:cc:6d:15:69:57:bf:0a:9e:b9:5f:29:0c:
|
||||||
|
e9:58:ac:05:3c:5a:bb:6d:47:8a:ee:67:73:89:e5:
|
||||||
|
17:79:c3:c7:ae:d1:4d:ac:f9:d4:0b:ac:c5:60:26:
|
||||||
|
8d:a3:8b:62:62:f6:d0:68:1c:87:79:d0:a5:52:04:
|
||||||
|
38:2a:4c:6b:38:d1:30:77:72:75:9e:3b:49:1f:de:
|
||||||
|
5b:b3:f0:28:07:ff:e9:6c:d3:ca:ee:0d:25:e9:03:
|
||||||
|
cf:05:2f:a6:9d:14:b7:cc:85:f0:e0:06:3a:bd:38:
|
||||||
|
cd:2d:c0:bd:f5:75:57:99:bf:1a:65:a9:2b:cb:42:
|
||||||
|
a8:8e:ee:e7:3a:b3:6a:b3:18:df:ca:68:c3:f8:d5:
|
||||||
|
e6:5a:5a:eb:a2:c1:9b:70:9c:56:c0:ae:0f:07:db:
|
||||||
|
34:03:a5:c2:cc:ef:61:da:c9:ea:90:50:01:c7:22:
|
||||||
|
30:f1:e2:99:b0:c3:dc:9e:4a:4f:1a:d5:ad:0f:b7:
|
||||||
|
bd:52:2f
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
53:47:45:79:6D:F6:CE:86:5A:2F:F0:56:D8:7F:BE:26:3E:6D:C8:AF
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:53:47:45:79:6D:F6:CE:86:5A:2F:F0:56:D8:7F:BE:26:3E:6D:C8:AF
|
||||||
|
|
||||||
|
X509v3 Basic Constraints: critical
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
97:0b:1f:32:23:b8:06:0d:04:72:23:7e:74:0b:34:fa:2f:60:
|
||||||
|
ae:0d:02:cc:3d:aa:52:95:65:ea:b0:cd:e9:5a:b5:d8:3a:0b:
|
||||||
|
80:82:ff:a8:01:fd:c2:22:83:3d:f9:7d:2e:78:b0:2d:07:e4:
|
||||||
|
2b:f1:c4:53:ce:bc:c7:dd:0e:39:aa:29:06:1a:ce:f9:23:df:
|
||||||
|
41:7d:20:af:3d:b1:60:3c:67:30:95:ee:04:a0:c6:af:c8:c7:
|
||||||
|
cb:e4:1e:46:ad:89:37:84:aa:f4:15:bc:03:27:e8:f5:9d:f1:
|
||||||
|
16:91:80:7f:4a:68:86:f4:f9:8a:97:91:e3:9b:bd:05:9b:06:
|
||||||
|
04:7e:3d:8a:ea:fe:b2:77:fe:b7:83:cb:ef:07:bb:43:8a:d9:
|
||||||
|
e5:9d:59:14:ed:1c:b6:51:a1:86:44:ba:70:6a:6c:9a:4a:c7:
|
||||||
|
ff:2b:10:a4:3d:3b:26:63:7f:23:09:25:cf:cc:4a:ca:24:5d:
|
||||||
|
45:cd:6a:2f:90:41:6c:b3:9e:75:ac:29:3c:d0:3a:3e:e5:41:
|
||||||
|
34:38:36:8c:b0:d9:ca:28:ab:0b:dc:c1:51:32:14:a2:1a:ee:
|
||||||
|
1d:0e:a5:5b:21:f1:bf:1e:7e:05:cc:26:53:62:c4:64:c7:c8:
|
||||||
|
54:57:5d:43:f2:8e:67:91:5c:b2:c7:03:53:1b:e0:62:f1:5d:
|
||||||
|
07:b8:88:64:d3:8c:04:04:a8:c1:77:29:ee:aa:ba:83:24:a4:
|
||||||
|
03:4a:a8:0f:e3:b9:e6:7b:c3:a1:c2:a4:aa:c2:26:b9:a7:26:
|
||||||
|
38:01:e6:81:77:dd:eb:30:15:40:fa:3f:97:fa:9a:30:39:5d:
|
||||||
|
a5:8a:0a:2f:75:88:dc:69:55:89:32:a1:04:50:4a:aa:06:fd:
|
||||||
|
89:1f:28:2a:0c:cc:76:2f:80:f7:95:f3:6c:76:85:16:bb:c6:
|
||||||
|
d0:d6:94:41:d8:ae:be:9e:de:d3:d2:5a:e3:84:40:6f:3d:90:
|
||||||
|
e0:9c:83:86:8a:35:c7:18:2f:7c:29:6e:50:c5:96:4f:40:1d:
|
||||||
|
13:d5:1d:57:cf:25:a5:a6:83:de:23:c7:3c:e6:a8:13:54:05:
|
||||||
|
bf:98:5b:d3:88:02:49:4e:55:f8:5f:1a:fd:25:0b:59:48:ad:
|
||||||
|
bb:b3:5d:88:16:50:47:06:1b:93:cc:52:ed:36:bc:41:c9:f5:
|
||||||
|
fc:80:89:1e:cc:77:14:a6:c9:67:6b:e1:57:10:a8:4f:6d:88:
|
||||||
|
01:d6:dc:77:80:0b:da:92:52:dc:4a:8d:66:5c:9d:7d:c5:20:
|
||||||
|
e3:6b:c2:0e:8b:ca:85:e4:d6:35:84:33:05:6e:5c:d0:82:8f:
|
||||||
|
28:0a:bd:67:9d:8c:a6:8f:22:7a:4e:60:c0:26:bc:93:ca:f5:
|
||||||
|
65:38:b2:38:38:03:3b:b6
|
||||||
81
MagiskOnWSA/DLL/cacerts/39698488.0
Normal file
81
MagiskOnWSA/DLL/cacerts/39698488.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIID2TCCAsGgAwIBAgIJANyOw2Zo67cgMA0GCSqGSIb3DQEBCwUAMIGCMQswCQYD
|
||||||
|
VQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIwEAYDVQQHDAlKZXJ1c2FsZW0xEDAO
|
||||||
|
BgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5ldGZyZWUubGluazElMCMGA1UEAwwc
|
||||||
|
TmV0RnJlZSBTaWduLCBLU0lNIC0gUGFydG5lcjAeFw0xODA0MjYwODIwNTlaFw0y
|
||||||
|
ODAzMDQwODIwNTlaMIGCMQswCQYDVQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIw
|
||||||
|
EAYDVQQHDAlKZXJ1c2FsZW0xEDAOBgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5l
|
||||||
|
dGZyZWUubGluazElMCMGA1UEAwwcTmV0RnJlZSBTaWduLCBLU0lNIC0gUGFydG5l
|
||||||
|
cjCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAPHMntK9YDmWRrtYegwY
|
||||||
|
K4wXPFegP0yyh+ULK2E2aDQkm3Qf8esdYLB032f6BtjSP9OkBALCYa2hgBhxLN/B
|
||||||
|
ozQeSSaZrol8Jw9eB/D8H0j4uGxvqQWCo1jqczIzWcIMOYz7DVbtWcf9Bnh6nAm4
|
||||||
|
fumR6rkR9lgJb6PRcEzgcAp7T/dMm5C70X8jmS42Q1LNBtah2LDx4tPP/PLNDJMA
|
||||||
|
usTJMvub9ttTdSUViHFtryoPpi9Xf8v0UXnHCLN1SouWQfuzwARwcMxMtKlewOiB
|
||||||
|
rHTlFGEDtgMk4iXs3gw47J5HYI0s7GrKA0OQ8i3/kozFdvdl1Fb5pqA+GOGHw0JH
|
||||||
|
x7UCAwEAAaNQME4wHQYDVR0OBBYEFEWCRa1+fLj2mN6Z1YDbIscBUIWrMB8GA1Ud
|
||||||
|
IwQYMBaAFEWCRa1+fLj2mN6Z1YDbIscBUIWrMAwGA1UdEwQFMAMBAf8wDQYJKoZI
|
||||||
|
hvcNAQELBQADggEBALLit1Nn8DsZhzVvp3LaWkM6B/cwj/J4PRieAnlXOieblANa
|
||||||
|
Zk2IHgICyVhau6m9OJVPzja83EthGUkB2Mu0hPYQSbL29n8vMYpz5UmoqYpn78Cb
|
||||||
|
lH0RLGSNTcMiz/5vDyRllbFZQM1FIikO9Pyjp4WjAGeHzgpZqNY1YDjBlQnGcJiC
|
||||||
|
pdMCO/KJCXNHDSpZMI0oFNpanURQdNIB30QmWwOdCodAiXK8NBZ6HXrvxo8VkOKg
|
||||||
|
7P9T6IHq3vpRZ9wpDXYCqDvfdQRurfeTSFl/7U3NB8IxkcTCncQvV+Ry8PY23rZ9
|
||||||
|
wpypjLV/3V23/aanygRRmeyGVHbSh9eSfiMBIHc=
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
dc:8e:c3:66:68:eb:b7:20
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, KSIM - Partner"
|
||||||
|
Validity
|
||||||
|
Not Before: Apr 26 08:20:59 2018 GMT
|
||||||
|
Not After : Mar 4 08:20:59 2028 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, KSIM - Partner"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:f1:cc:9e:d2:bd:60:39:96:46:bb:58:7a:0c:18:
|
||||||
|
2b:8c:17:3c:57:a0:3f:4c:b2:87:e5:0b:2b:61:36:
|
||||||
|
68:34:24:9b:74:1f:f1:eb:1d:60:b0:74:df:67:fa:
|
||||||
|
06:d8:d2:3f:d3:a4:04:02:c2:61:ad:a1:80:18:71:
|
||||||
|
2c:df:c1:a3:34:1e:49:26:99:ae:89:7c:27:0f:5e:
|
||||||
|
07:f0:fc:1f:48:f8:b8:6c:6f:a9:05:82:a3:58:ea:
|
||||||
|
73:32:33:59:c2:0c:39:8c:fb:0d:56:ed:59:c7:fd:
|
||||||
|
06:78:7a:9c:09:b8:7e:e9:91:ea:b9:11:f6:58:09:
|
||||||
|
6f:a3:d1:70:4c:e0:70:0a:7b:4f:f7:4c:9b:90:bb:
|
||||||
|
d1:7f:23:99:2e:36:43:52:cd:06:d6:a1:d8:b0:f1:
|
||||||
|
e2:d3:cf:fc:f2:cd:0c:93:00:ba:c4:c9:32:fb:9b:
|
||||||
|
f6:db:53:75:25:15:88:71:6d:af:2a:0f:a6:2f:57:
|
||||||
|
7f:cb:f4:51:79:c7:08:b3:75:4a:8b:96:41:fb:b3:
|
||||||
|
c0:04:70:70:cc:4c:b4:a9:5e:c0:e8:81:ac:74:e5:
|
||||||
|
14:61:03:b6:03:24:e2:25:ec:de:0c:38:ec:9e:47:
|
||||||
|
60:8d:2c:ec:6a:ca:03:43:90:f2:2d:ff:92:8c:c5:
|
||||||
|
76:f7:65:d4:56:f9:a6:a0:3e:18:e1:87:c3:42:47:
|
||||||
|
c7:b5
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
45:82:45:AD:7E:7C:B8:F6:98:DE:99:D5:80:DB:22:C7:01:50:85:AB
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:45:82:45:AD:7E:7C:B8:F6:98:DE:99:D5:80:DB:22:C7:01:50:85:AB
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
b2:e2:b7:53:67:f0:3b:19:87:35:6f:a7:72:da:5a:43:3a:07:
|
||||||
|
f7:30:8f:f2:78:3d:18:9e:02:79:57:3a:27:9b:94:03:5a:66:
|
||||||
|
4d:88:1e:02:02:c9:58:5a:bb:a9:bd:38:95:4f:ce:36:bc:dc:
|
||||||
|
4b:61:19:49:01:d8:cb:b4:84:f6:10:49:b2:f6:f6:7f:2f:31:
|
||||||
|
8a:73:e5:49:a8:a9:8a:67:ef:c0:9b:94:7d:11:2c:64:8d:4d:
|
||||||
|
c3:22:cf:fe:6f:0f:24:65:95:b1:59:40:cd:45:22:29:0e:f4:
|
||||||
|
fc:a3:a7:85:a3:00:67:87:ce:0a:59:a8:d6:35:60:38:c1:95:
|
||||||
|
09:c6:70:98:82:a5:d3:02:3b:f2:89:09:73:47:0d:2a:59:30:
|
||||||
|
8d:28:14:da:5a:9d:44:50:74:d2:01:df:44:26:5b:03:9d:0a:
|
||||||
|
87:40:89:72:bc:34:16:7a:1d:7a:ef:c6:8f:15:90:e2:a0:ec:
|
||||||
|
ff:53:e8:81:ea:de:fa:51:67:dc:29:0d:76:02:a8:3b:df:75:
|
||||||
|
04:6e:ad:f7:93:48:59:7f:ed:4d:cd:07:c2:31:91:c4:c2:9d:
|
||||||
|
c4:2f:57:e4:72:f0:f6:36:de:b6:7d:c2:9c:a9:8c:b5:7f:dd:
|
||||||
|
5d:b7:fd:a6:a7:ca:04:51:99:ec:86:54:76:d2:87:d7:92:7e:
|
||||||
|
23:01:20:77
|
||||||
123
MagiskOnWSA/DLL/cacerts/3f66ddee.0
Normal file
123
MagiskOnWSA/DLL/cacerts/3f66ddee.0
Normal file
@ -0,0 +1,123 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIFzzCCA7egAwIBAgIUEwVOrPcQ9DVIGMi4qkZrs70iQnowDQYJKoZIhvcNAQEL
|
||||||
|
BQAwdzELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAGA1UEBwwJSmVy
|
||||||
|
dXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRmcmVlLmxpbmsx
|
||||||
|
GjAYBgNVBAMMEU5ldEZyZWUgU2lnbiwgSVRDMB4XDTIxMDQxNDE3NTE1M1oXDTMx
|
||||||
|
MDQxMjE3NTE1M1owdzELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAG
|
||||||
|
A1UEBwwJSmVydXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRm
|
||||||
|
cmVlLmxpbmsxGjAYBgNVBAMMEU5ldEZyZWUgU2lnbiwgSVRDMIICIjANBgkqhkiG
|
||||||
|
9w0BAQEFAAOCAg8AMIICCgKCAgEAwncsxkaH7L3LnDC3P6gVbqwWc5ieLHnKtgk8
|
||||||
|
AHsHQVuzFbKJikfA5FFdZQoCslPBR83pwzTi2wrnFKzApDdLBrB8NgbAzhimQ0gd
|
||||||
|
miRe4GdC8/W5WDu97+JnI+AGFGrbJxCzBfxc7hYC/0gTp9y8jWO9241OxuhYjlUf
|
||||||
|
7fXHqIlXKlz+h/0PPhop82yv5AeMolyGaQ5LnyuDCGZsS1VG+KiMhxQO9rB5pUAr
|
||||||
|
qHwAJ3UzGqXoMphSyoBYpvNG4R6MGOTvDgSVOZ8CJRbI4Y4/2XRpmXKC4EsKObR5
|
||||||
|
OVqm+iCSxX23DCWg/RBEClB6CAadkEFWXtOATtiCP/pPEGywOxFU82ENV/2MEm/w
|
||||||
|
/HMTLoBiKA8lnq8z1KcPzZ1w8oZk/N+Y/wibuPz+qQJPIW5OiXvNcq2QiVck843v
|
||||||
|
nZjEEd5GEx5FHAiPe71QBKq55Teb4G2/PeO5v26tUc9z1Nl7AQS7equ/XW3Xe5IT
|
||||||
|
+HP+VIq/x0hN9fpAbOwL7vnIZO4oMWR5wVXqo8B2vCd+XtHQXeYldzaggTtc026Q
|
||||||
|
cm/YHaIrexShAWKmfU5MfrGTOrfEgi11aJQTNDZzlR3eodMCkRJmV1wm8LjuJSyz
|
||||||
|
CVas2kLCAQ0LoT4c1Vp8SC2/5FGZNQ9SHhiqzDESNt9efqr4CF7/1MgTGXASunoH
|
||||||
|
UBp3KccCAwEAAaNTMFEwHQYDVR0OBBYEFN7AZUcFTTIew+Sve7rVPacztLA/MB8G
|
||||||
|
A1UdIwQYMBaAFN7AZUcFTTIew+Sve7rVPacztLA/MA8GA1UdEwEB/wQFMAMBAf8w
|
||||||
|
DQYJKoZIhvcNAQELBQADggIBAKf+3/4Adi0mslhs8N/JONbRaord4GBpqRtQ9OXV
|
||||||
|
pgyF7f7S/rBFnTcBbyqCSu0EitrDIAZ81rmJ8Cx0ae827v0fkRKwmtIl/G0QgUzd
|
||||||
|
4uVPe3UuALBjqedhVrfnNGZQvb1jbeTJ9R1u7V95au32fZk+1gHc69eA2NZgQ2kk
|
||||||
|
sazKnC8Urca3CgmVuuE8EeYcChRCWQ8qiCVKicm9g0tfwdLGIJMsQJPi7lXBmdlI
|
||||||
|
Gex5ADiNk3G5dIKVt3BqG9KYXBN9mw6RK7LIMGPJR20ydRy5vxPazKQXHaVWnvfU
|
||||||
|
4Gg7xgjNygMFYuflt6kPfek3HdIo5CASLwzz86dhwqdp0Wun8KMx3wfXu9IArL2p
|
||||||
|
AkT7z1d3zZWiaaXZ+JSUNcmC8560PVUE3Ygdkpi5AKBkLizmKt7ZuSU4LZvlcl7x
|
||||||
|
kvu2ZoAFyXh6LOL+UduLCzXVpCKh9rz1cnRkcqbkfdk3pSs+Z6HXT4aZriRqRNR4
|
||||||
|
0zaIjLLR93s7rlohRmXUu7uxG0wk6K88H4f8n6IHgZHZCeizY2s7rW6ZMsjuHM4T
|
||||||
|
8PrEdYR68VKJ4kSpBRyTxlUT4CZzfRaaViEhN52JSSxXUcfpOphO1tDavyeUAR8r
|
||||||
|
1+Prire6Y6/A0U5mr9gssB2HtBw69FUC6O//foeoc9JLO08dCuDznHs+UtH06hws
|
||||||
|
NA54
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
13:05:4e:ac:f7:10:f4:35:48:18:c8:b8:aa:46:6b:b3:bd:22:42:7a
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, ITC"
|
||||||
|
Validity
|
||||||
|
Not Before: Apr 14 17:51:53 2021 GMT
|
||||||
|
Not After : Apr 12 17:51:53 2031 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, ITC"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:c2:77:2c:c6:46:87:ec:bd:cb:9c:30:b7:3f:a8:
|
||||||
|
15:6e:ac:16:73:98:9e:2c:79:ca:b6:09:3c:00:7b:
|
||||||
|
07:41:5b:b3:15:b2:89:8a:47:c0:e4:51:5d:65:0a:
|
||||||
|
02:b2:53:c1:47:cd:e9:c3:34:e2:db:0a:e7:14:ac:
|
||||||
|
c0:a4:37:4b:06:b0:7c:36:06:c0:ce:18:a6:43:48:
|
||||||
|
1d:9a:24:5e:e0:67:42:f3:f5:b9:58:3b:bd:ef:e2:
|
||||||
|
67:23:e0:06:14:6a:db:27:10:b3:05:fc:5c:ee:16:
|
||||||
|
02:ff:48:13:a7:dc:bc:8d:63:bd:db:8d:4e:c6:e8:
|
||||||
|
58:8e:55:1f:ed:f5:c7:a8:89:57:2a:5c:fe:87:fd:
|
||||||
|
0f:3e:1a:29:f3:6c:af:e4:07:8c:a2:5c:86:69:0e:
|
||||||
|
4b:9f:2b:83:08:66:6c:4b:55:46:f8:a8:8c:87:14:
|
||||||
|
0e:f6:b0:79:a5:40:2b:a8:7c:00:27:75:33:1a:a5:
|
||||||
|
e8:32:98:52:ca:80:58:a6:f3:46:e1:1e:8c:18:e4:
|
||||||
|
ef:0e:04:95:39:9f:02:25:16:c8:e1:8e:3f:d9:74:
|
||||||
|
69:99:72:82:e0:4b:0a:39:b4:79:39:5a:a6:fa:20:
|
||||||
|
92:c5:7d:b7:0c:25:a0:fd:10:44:0a:50:7a:08:06:
|
||||||
|
9d:90:41:56:5e:d3:80:4e:d8:82:3f:fa:4f:10:6c:
|
||||||
|
b0:3b:11:54:f3:61:0d:57:fd:8c:12:6f:f0:fc:73:
|
||||||
|
13:2e:80:62:28:0f:25:9e:af:33:d4:a7:0f:cd:9d:
|
||||||
|
70:f2:86:64:fc:df:98:ff:08:9b:b8:fc:fe:a9:02:
|
||||||
|
4f:21:6e:4e:89:7b:cd:72:ad:90:89:57:24:f3:8d:
|
||||||
|
ef:9d:98:c4:11:de:46:13:1e:45:1c:08:8f:7b:bd:
|
||||||
|
50:04:aa:b9:e5:37:9b:e0:6d:bf:3d:e3:b9:bf:6e:
|
||||||
|
ad:51:cf:73:d4:d9:7b:01:04:bb:7a:ab:bf:5d:6d:
|
||||||
|
d7:7b:92:13:f8:73:fe:54:8a:bf:c7:48:4d:f5:fa:
|
||||||
|
40:6c:ec:0b:ee:f9:c8:64:ee:28:31:64:79:c1:55:
|
||||||
|
ea:a3:c0:76:bc:27:7e:5e:d1:d0:5d:e6:25:77:36:
|
||||||
|
a0:81:3b:5c:d3:6e:90:72:6f:d8:1d:a2:2b:7b:14:
|
||||||
|
a1:01:62:a6:7d:4e:4c:7e:b1:93:3a:b7:c4:82:2d:
|
||||||
|
75:68:94:13:34:36:73:95:1d:de:a1:d3:02:91:12:
|
||||||
|
66:57:5c:26:f0:b8:ee:25:2c:b3:09:56:ac:da:42:
|
||||||
|
c2:01:0d:0b:a1:3e:1c:d5:5a:7c:48:2d:bf:e4:51:
|
||||||
|
99:35:0f:52:1e:18:aa:cc:31:12:36:df:5e:7e:aa:
|
||||||
|
f8:08:5e:ff:d4:c8:13:19:70:12:ba:7a:07:50:1a:
|
||||||
|
77:29:c7
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
DE:C0:65:47:05:4D:32:1E:C3:E4:AF:7B:BA:D5:3D:A7:33:B4:B0:3F
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:DE:C0:65:47:05:4D:32:1E:C3:E4:AF:7B:BA:D5:3D:A7:33:B4:B0:3F
|
||||||
|
|
||||||
|
X509v3 Basic Constraints: critical
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
a7:fe:df:fe:00:76:2d:26:b2:58:6c:f0:df:c9:38:d6:d1:6a:
|
||||||
|
8a:dd:e0:60:69:a9:1b:50:f4:e5:d5:a6:0c:85:ed:fe:d2:fe:
|
||||||
|
b0:45:9d:37:01:6f:2a:82:4a:ed:04:8a:da:c3:20:06:7c:d6:
|
||||||
|
b9:89:f0:2c:74:69:ef:36:ee:fd:1f:91:12:b0:9a:d2:25:fc:
|
||||||
|
6d:10:81:4c:dd:e2:e5:4f:7b:75:2e:00:b0:63:a9:e7:61:56:
|
||||||
|
b7:e7:34:66:50:bd:bd:63:6d:e4:c9:f5:1d:6e:ed:5f:79:6a:
|
||||||
|
ed:f6:7d:99:3e:d6:01:dc:eb:d7:80:d8:d6:60:43:69:24:b1:
|
||||||
|
ac:ca:9c:2f:14:ad:c6:b7:0a:09:95:ba:e1:3c:11:e6:1c:0a:
|
||||||
|
14:42:59:0f:2a:88:25:4a:89:c9:bd:83:4b:5f:c1:d2:c6:20:
|
||||||
|
93:2c:40:93:e2:ee:55:c1:99:d9:48:19:ec:79:00:38:8d:93:
|
||||||
|
71:b9:74:82:95:b7:70:6a:1b:d2:98:5c:13:7d:9b:0e:91:2b:
|
||||||
|
b2:c8:30:63:c9:47:6d:32:75:1c:b9:bf:13:da:cc:a4:17:1d:
|
||||||
|
a5:56:9e:f7:d4:e0:68:3b:c6:08:cd:ca:03:05:62:e7:e5:b7:
|
||||||
|
a9:0f:7d:e9:37:1d:d2:28:e4:20:12:2f:0c:f3:f3:a7:61:c2:
|
||||||
|
a7:69:d1:6b:a7:f0:a3:31:df:07:d7:bb:d2:00:ac:bd:a9:02:
|
||||||
|
44:fb:cf:57:77:cd:95:a2:69:a5:d9:f8:94:94:35:c9:82:f3:
|
||||||
|
9e:b4:3d:55:04:dd:88:1d:92:98:b9:00:a0:64:2e:2c:e6:2a:
|
||||||
|
de:d9:b9:25:38:2d:9b:e5:72:5e:f1:92:fb:b6:66:80:05:c9:
|
||||||
|
78:7a:2c:e2:fe:51:db:8b:0b:35:d5:a4:22:a1:f6:bc:f5:72:
|
||||||
|
74:64:72:a6:e4:7d:d9:37:a5:2b:3e:67:a1:d7:4f:86:99:ae:
|
||||||
|
24:6a:44:d4:78:d3:36:88:8c:b2:d1:f7:7b:3b:ae:5a:21:46:
|
||||||
|
65:d4:bb:bb:b1:1b:4c:24:e8:af:3c:1f:87:fc:9f:a2:07:81:
|
||||||
|
91:d9:09:e8:b3:63:6b:3b:ad:6e:99:32:c8:ee:1c:ce:13:f0:
|
||||||
|
fa:c4:75:84:7a:f1:52:89:e2:44:a9:05:1c:93:c6:55:13:e0:
|
||||||
|
26:73:7d:16:9a:56:21:21:37:9d:89:49:2c:57:51:c7:e9:3a:
|
||||||
|
98:4e:d6:d0:da:bf:27:94:01:1f:2b:d7:e3:eb:8a:b7:ba:63:
|
||||||
|
af:c0:d1:4e:66:af:d8:2c:b0:1d:87:b4:1c:3a:f4:55:02:e8:
|
||||||
|
ef:ff:7e:87:a8:73:d2:4b:3b:4f:1d:0a:e0:f3:9c:7b:3e:52:
|
||||||
|
d1:f4:ea:1c:2c:34:0e:78
|
||||||
122
MagiskOnWSA/DLL/cacerts/42afec87.0
Normal file
122
MagiskOnWSA/DLL/cacerts/42afec87.0
Normal file
@ -0,0 +1,122 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIFxzCCA6+gAwIBAgIJAMOfeHNsvnuxMA0GCSqGSIb3DQEBCwUAMHoxCzAJBgNV
|
||||||
|
BAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcMCUplcnVzYWxlbTEQMA4G
|
||||||
|
A1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0ZnJlZS5saW5rMR0wGwYDVQQDDBRO
|
||||||
|
ZXRGcmVlIFNpZ24gLElCLUlUQzAeFw0xOTEwMjYxOTEwMjNaFw0yOTA5MDMxOTEw
|
||||||
|
MjNaMHoxCzAJBgNVBAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcMCUpl
|
||||||
|
cnVzYWxlbTEQMA4GA1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0ZnJlZS5saW5r
|
||||||
|
MR0wGwYDVQQDDBROZXRGcmVlIFNpZ24gLElCLUlUQzCCAiIwDQYJKoZIhvcNAQEB
|
||||||
|
BQADggIPADCCAgoCggIBAPistDj0oOuF1Mtu2VyYOK+O/fhMHQIYg3ZG7HMxIPBp
|
||||||
|
dSpCeH+3Z6Qi1YSlDkd0sW7C3KqUt1gsJyf2HZLBrCEBBlFtCN/zCdIjo/pelR7q
|
||||||
|
+qXYr67y980GzZqnlYgGbS3PbthsXfayAQi1LsSR1UXdUg91WgJLFdMgIVsnSq5K
|
||||||
|
w8re1D+V9KfX1SnmH/WDfzb/ickxryyiieMQV+lNegDhsTqSaHuOowsFNgZkwsoo
|
||||||
|
c+DAuHfBFn+jWwZMFPDsiWSROsh4rcft172+I4ReR1Cr2JdHzueJQNx8mTcr5COM
|
||||||
|
e6Hl72K4Kot4G6ohL74GATs6fSP3kcy8UafDSnODAffixZt7S59K9hSqsMVJvTzS
|
||||||
|
T/pmhrQFS7xACj4TJa/f1t+5LYRe6FdwEcXeHNcfSVVRfPgLdiKFAD5ok3TFBXfO
|
||||||
|
fsAkpdhdfSSUOBWLuE/l+Ko56enic59JeewwbC322Ihvn+1PaloVINHQTlXJhCFD
|
||||||
|
CkoizPrm9AFlM2IK+qPN0GSckj2X6Eo/bxFmt6GXsZW8kzoDc4TlclLxoMJB+jJn
|
||||||
|
H1EH9+h1wWNR9kybBnrnKSGdlapD0OK42H/Ul44uLtNLKN3zpMvYWabSdThYTUqZ
|
||||||
|
pCg8tXyQj1z/3l12Ka7QIEqkqTHF35MTe0YrDLbKo4N8s1vlkfevcwHeerSI5ts1
|
||||||
|
AgMBAAGjUDBOMB0GA1UdDgQWBBSnCGbym3/xoGKcYFbwvP2yTjBbADAfBgNVHSME
|
||||||
|
GDAWgBSnCGbym3/xoGKcYFbwvP2yTjBbADAMBgNVHRMEBTADAQH/MA0GCSqGSIb3
|
||||||
|
DQEBCwUAA4ICAQCspY/ayI3Mwvp6nAWpBaLSw/YDWChYAG99prvgCSRYVgwRQGw5
|
||||||
|
oZnhYFSZM+Suh0cHKh3tU1nZDpgn/vvqOmf1IPHCI+ZOEY73YZmPlYD3JE2ZJDzO
|
||||||
|
QdJPwW/07W7XAjCIoLw27C/xJDRpBRCXpqfAfmw8qTrNEsozhX9pzJkCVr6UtYX5
|
||||||
|
X5LWY0oX9Y/OY8dGQeGqQNeAMwVyW0pmUs5lmVTzPP4mhWLmqF8MCPf8ULswBfr+
|
||||||
|
uWHNGG1u7RAwm8MP4hi1IgT8bVLQJjaLFRV/dUVHDs5dnF0ZnpNnvfoJxCbyMjcR
|
||||||
|
JWb4yR+31ZNrC+SZobtTcEOnzuaaL5AHGb6gZt0qGOVoykPM4dtlFH3jVrCdvOAA
|
||||||
|
0QCzjfu6o8Eb2HzdWKKm4Kxl9mlwznQrOCa3jmj6L9g/Y1tetYAnJwrgzZVvrNMV
|
||||||
|
5bLW1beBvb/Y99z3TNhjqgjv5gBeeN0cJ63k8P/ZuikuNuhCub2Lo8diYhaw2C6o
|
||||||
|
5hMg+q5U9FML//mXWsD6bHN68XPQEUf43O8BCOeIOyW1fDIX3y9RcwJf2lP4frkH
|
||||||
|
Eo9RaDUsLWdPVxPvgdVSZUiOxkKJ3CxSJaffrsccNTMcFx/ACzQqn6gxRHPuqK0Y
|
||||||
|
0Ka6pV5b03zWCT+G6qzidxHjKnwOhKV5r+5nYFzcvPpZijK/RmnSDjWuTQ==
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
c3:9f:78:73:6c:be:7b:b1
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign ,IB-ITC"
|
||||||
|
Validity
|
||||||
|
Not Before: Oct 26 19:10:23 2019 GMT
|
||||||
|
Not After : Sep 3 19:10:23 2029 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign ,IB-ITC"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:f8:ac:b4:38:f4:a0:eb:85:d4:cb:6e:d9:5c:98:
|
||||||
|
38:af:8e:fd:f8:4c:1d:02:18:83:76:46:ec:73:31:
|
||||||
|
20:f0:69:75:2a:42:78:7f:b7:67:a4:22:d5:84:a5:
|
||||||
|
0e:47:74:b1:6e:c2:dc:aa:94:b7:58:2c:27:27:f6:
|
||||||
|
1d:92:c1:ac:21:01:06:51:6d:08:df:f3:09:d2:23:
|
||||||
|
a3:fa:5e:95:1e:ea:fa:a5:d8:af:ae:f2:f7:cd:06:
|
||||||
|
cd:9a:a7:95:88:06:6d:2d:cf:6e:d8:6c:5d:f6:b2:
|
||||||
|
01:08:b5:2e:c4:91:d5:45:dd:52:0f:75:5a:02:4b:
|
||||||
|
15:d3:20:21:5b:27:4a:ae:4a:c3:ca:de:d4:3f:95:
|
||||||
|
f4:a7:d7:d5:29:e6:1f:f5:83:7f:36:ff:89:c9:31:
|
||||||
|
af:2c:a2:89:e3:10:57:e9:4d:7a:00:e1:b1:3a:92:
|
||||||
|
68:7b:8e:a3:0b:05:36:06:64:c2:ca:28:73:e0:c0:
|
||||||
|
b8:77:c1:16:7f:a3:5b:06:4c:14:f0:ec:89:64:91:
|
||||||
|
3a:c8:78:ad:c7:ed:d7:bd:be:23:84:5e:47:50:ab:
|
||||||
|
d8:97:47:ce:e7:89:40:dc:7c:99:37:2b:e4:23:8c:
|
||||||
|
7b:a1:e5:ef:62:b8:2a:8b:78:1b:aa:21:2f:be:06:
|
||||||
|
01:3b:3a:7d:23:f7:91:cc:bc:51:a7:c3:4a:73:83:
|
||||||
|
01:f7:e2:c5:9b:7b:4b:9f:4a:f6:14:aa:b0:c5:49:
|
||||||
|
bd:3c:d2:4f:fa:66:86:b4:05:4b:bc:40:0a:3e:13:
|
||||||
|
25:af:df:d6:df:b9:2d:84:5e:e8:57:70:11:c5:de:
|
||||||
|
1c:d7:1f:49:55:51:7c:f8:0b:76:22:85:00:3e:68:
|
||||||
|
93:74:c5:05:77:ce:7e:c0:24:a5:d8:5d:7d:24:94:
|
||||||
|
38:15:8b:b8:4f:e5:f8:aa:39:e9:e9:e2:73:9f:49:
|
||||||
|
79:ec:30:6c:2d:f6:d8:88:6f:9f:ed:4f:6a:5a:15:
|
||||||
|
20:d1:d0:4e:55:c9:84:21:43:0a:4a:22:cc:fa:e6:
|
||||||
|
f4:01:65:33:62:0a:fa:a3:cd:d0:64:9c:92:3d:97:
|
||||||
|
e8:4a:3f:6f:11:66:b7:a1:97:b1:95:bc:93:3a:03:
|
||||||
|
73:84:e5:72:52:f1:a0:c2:41:fa:32:67:1f:51:07:
|
||||||
|
f7:e8:75:c1:63:51:f6:4c:9b:06:7a:e7:29:21:9d:
|
||||||
|
95:aa:43:d0:e2:b8:d8:7f:d4:97:8e:2e:2e:d3:4b:
|
||||||
|
28:dd:f3:a4:cb:d8:59:a6:d2:75:38:58:4d:4a:99:
|
||||||
|
a4:28:3c:b5:7c:90:8f:5c:ff:de:5d:76:29:ae:d0:
|
||||||
|
20:4a:a4:a9:31:c5:df:93:13:7b:46:2b:0c:b6:ca:
|
||||||
|
a3:83:7c:b3:5b:e5:91:f7:af:73:01:de:7a:b4:88:
|
||||||
|
e6:db:35
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
A7:08:66:F2:9B:7F:F1:A0:62:9C:60:56:F0:BC:FD:B2:4E:30:5B:00
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:A7:08:66:F2:9B:7F:F1:A0:62:9C:60:56:F0:BC:FD:B2:4E:30:5B:00
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
ac:a5:8f:da:c8:8d:cc:c2:fa:7a:9c:05:a9:05:a2:d2:c3:f6:
|
||||||
|
03:58:28:58:00:6f:7d:a6:bb:e0:09:24:58:56:0c:11:40:6c:
|
||||||
|
39:a1:99:e1:60:54:99:33:e4:ae:87:47:07:2a:1d:ed:53:59:
|
||||||
|
d9:0e:98:27:fe:fb:ea:3a:67:f5:20:f1:c2:23:e6:4e:11:8e:
|
||||||
|
f7:61:99:8f:95:80:f7:24:4d:99:24:3c:ce:41:d2:4f:c1:6f:
|
||||||
|
f4:ed:6e:d7:02:30:88:a0:bc:36:ec:2f:f1:24:34:69:05:10:
|
||||||
|
97:a6:a7:c0:7e:6c:3c:a9:3a:cd:12:ca:33:85:7f:69:cc:99:
|
||||||
|
02:56:be:94:b5:85:f9:5f:92:d6:63:4a:17:f5:8f:ce:63:c7:
|
||||||
|
46:41:e1:aa:40:d7:80:33:05:72:5b:4a:66:52:ce:65:99:54:
|
||||||
|
f3:3c:fe:26:85:62:e6:a8:5f:0c:08:f7:fc:50:bb:30:05:fa:
|
||||||
|
fe:b9:61:cd:18:6d:6e:ed:10:30:9b:c3:0f:e2:18:b5:22:04:
|
||||||
|
fc:6d:52:d0:26:36:8b:15:15:7f:75:45:47:0e:ce:5d:9c:5d:
|
||||||
|
19:9e:93:67:bd:fa:09:c4:26:f2:32:37:11:25:66:f8:c9:1f:
|
||||||
|
b7:d5:93:6b:0b:e4:99:a1:bb:53:70:43:a7:ce:e6:9a:2f:90:
|
||||||
|
07:19:be:a0:66:dd:2a:18:e5:68:ca:43:cc:e1:db:65:14:7d:
|
||||||
|
e3:56:b0:9d:bc:e0:00:d1:00:b3:8d:fb:ba:a3:c1:1b:d8:7c:
|
||||||
|
dd:58:a2:a6:e0:ac:65:f6:69:70:ce:74:2b:38:26:b7:8e:68:
|
||||||
|
fa:2f:d8:3f:63:5b:5e:b5:80:27:27:0a:e0:cd:95:6f:ac:d3:
|
||||||
|
15:e5:b2:d6:d5:b7:81:bd:bf:d8:f7:dc:f7:4c:d8:63:aa:08:
|
||||||
|
ef:e6:00:5e:78:dd:1c:27:ad:e4:f0:ff:d9:ba:29:2e:36:e8:
|
||||||
|
42:b9:bd:8b:a3:c7:62:62:16:b0:d8:2e:a8:e6:13:20:fa:ae:
|
||||||
|
54:f4:53:0b:ff:f9:97:5a:c0:fa:6c:73:7a:f1:73:d0:11:47:
|
||||||
|
f8:dc:ef:01:08:e7:88:3b:25:b5:7c:32:17:df:2f:51:73:02:
|
||||||
|
5f:da:53:f8:7e:b9:07:12:8f:51:68:35:2c:2d:67:4f:57:13:
|
||||||
|
ef:81:d5:52:65:48:8e:c6:42:89:dc:2c:52:25:a7:df:ae:c7:
|
||||||
|
1c:35:33:1c:17:1f:c0:0b:34:2a:9f:a8:31:44:73:ee:a8:ad:
|
||||||
|
18:d0:a6:ba:a5:5e:5b:d3:7c:d6:09:3f:86:ea:ac:e2:77:11:
|
||||||
|
e3:2a:7c:0e:84:a5:79:af:ee:67:60:5c:dc:bc:fa:59:8a:32:
|
||||||
|
bf:46:69:d2:0e:35:ae:4d
|
||||||
81
MagiskOnWSA/DLL/cacerts/482e0622.0
Normal file
81
MagiskOnWSA/DLL/cacerts/482e0622.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIDwzCCAqugAwIBAgIJAJvSq+oh8F6+MA0GCSqGSIb3DQEBCwUAMHgxCzAJBgNV
|
||||||
|
BAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcMCUplcnVzYWxlbTEQMA4G
|
||||||
|
A1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0ZnJlZS5saW5rMRswGQYDVQQDDBJO
|
||||||
|
ZXRGcmVlIFNpZ24gLCAwMTkwHhcNMTYwNDIxMTAyNzA1WhcNMjYwMjI4MTAyNzA1
|
||||||
|
WjB4MQswCQYDVQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIwEAYDVQQHDAlKZXJ1
|
||||||
|
c2FsZW0xEDAOBgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5ldGZyZWUubGluazEb
|
||||||
|
MBkGA1UEAwwSTmV0RnJlZSBTaWduICwgMDE5MIIBIjANBgkqhkiG9w0BAQEFAAOC
|
||||||
|
AQ8AMIIBCgKCAQEA5Wq8zAqW7KGANXfbg9Ck8rx4nPjSkerlSPS/yNEVa/L8HulD
|
||||||
|
q/GVMRaPaL+RqI4GQt6LeQAmj1FZS01rQQITNRsg6MhNrPhENhg48rjFNIxuEnMv
|
||||||
|
IfydKGGU2mFXcMtQ9IoRSe4OYE3CKDG0pYzfXhh+TW0H4KKqjO6mjPmMcNjbstpK
|
||||||
|
vOPFg6Xu5em6hvtQCKC0V551WKWmNQiHOpwRdVIdbWBv3S5xiO5tZVigGpEJ1gLe
|
||||||
|
8W+Zn2ozcpvh+m38QSZ0A1DVP5Te/7q9L3+BPub8kz3C6GnNK547ucM5HBmOzNwN
|
||||||
|
luZHVUsehCLc0I965Wd4ZRUXXeeo7BibjRI6mQIDAQABo1AwTjAdBgNVHQ4EFgQU
|
||||||
|
tLpJD3JS6YPg7VQl2gKrPJByEycwHwYDVR0jBBgwFoAUtLpJD3JS6YPg7VQl2gKr
|
||||||
|
PJByEycwDAYDVR0TBAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAQEAThhIvkN/HsFG
|
||||||
|
7jaHl8yyH3IyvHX+LrItJyhRaQ4xALzGllGCLWvN15e2SWITdXncd4nMU7VRVG1k
|
||||||
|
CiX6H55Jh1U/DmZHmUI2HBhf/2liFNKXKDOeHg4u+FIzgzuIc0z+RvwPpw9IVLio
|
||||||
|
Pe6lbaIc5+80kO/mwJwQZoEaqTyL1Ujn69cosiZpiYF3xtxkfBWEWe7XkLunLqqV
|
||||||
|
DoMEGMq+MUxO+Jngv0j/7dSi1/1eovNnrV4YeF2Flvq2xY1aCKO/cocv5v7w5wEm
|
||||||
|
8fMFQwKcT7QcCx+/nkx3r0tDHxO7og7xr8petCK+ULqwL28ha4U0l+kLF0ZRiG5H
|
||||||
|
Ni6Hj6Oi9A==
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
9b:d2:ab:ea:21:f0:5e:be
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , 019"
|
||||||
|
Validity
|
||||||
|
Not Before: Apr 21 10:27:05 2016 GMT
|
||||||
|
Not After : Feb 28 10:27:05 2026 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , 019"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:e5:6a:bc:cc:0a:96:ec:a1:80:35:77:db:83:d0:
|
||||||
|
a4:f2:bc:78:9c:f8:d2:91:ea:e5:48:f4:bf:c8:d1:
|
||||||
|
15:6b:f2:fc:1e:e9:43:ab:f1:95:31:16:8f:68:bf:
|
||||||
|
91:a8:8e:06:42:de:8b:79:00:26:8f:51:59:4b:4d:
|
||||||
|
6b:41:02:13:35:1b:20:e8:c8:4d:ac:f8:44:36:18:
|
||||||
|
38:f2:b8:c5:34:8c:6e:12:73:2f:21:fc:9d:28:61:
|
||||||
|
94:da:61:57:70:cb:50:f4:8a:11:49:ee:0e:60:4d:
|
||||||
|
c2:28:31:b4:a5:8c:df:5e:18:7e:4d:6d:07:e0:a2:
|
||||||
|
aa:8c:ee:a6:8c:f9:8c:70:d8:db:b2:da:4a:bc:e3:
|
||||||
|
c5:83:a5:ee:e5:e9:ba:86:fb:50:08:a0:b4:57:9e:
|
||||||
|
75:58:a5:a6:35:08:87:3a:9c:11:75:52:1d:6d:60:
|
||||||
|
6f:dd:2e:71:88:ee:6d:65:58:a0:1a:91:09:d6:02:
|
||||||
|
de:f1:6f:99:9f:6a:33:72:9b:e1:fa:6d:fc:41:26:
|
||||||
|
74:03:50:d5:3f:94:de:ff:ba:bd:2f:7f:81:3e:e6:
|
||||||
|
fc:93:3d:c2:e8:69:cd:2b:9e:3b:b9:c3:39:1c:19:
|
||||||
|
8e:cc:dc:0d:96:e6:47:55:4b:1e:84:22:dc:d0:8f:
|
||||||
|
7a:e5:67:78:65:15:17:5d:e7:a8:ec:18:9b:8d:12:
|
||||||
|
3a:99
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
B4:BA:49:0F:72:52:E9:83:E0:ED:54:25:DA:02:AB:3C:90:72:13:27
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:B4:BA:49:0F:72:52:E9:83:E0:ED:54:25:DA:02:AB:3C:90:72:13:27
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
4e:18:48:be:43:7f:1e:c1:46:ee:36:87:97:cc:b2:1f:72:32:
|
||||||
|
bc:75:fe:2e:b2:2d:27:28:51:69:0e:31:00:bc:c6:96:51:82:
|
||||||
|
2d:6b:cd:d7:97:b6:49:62:13:75:79:dc:77:89:cc:53:b5:51:
|
||||||
|
54:6d:64:0a:25:fa:1f:9e:49:87:55:3f:0e:66:47:99:42:36:
|
||||||
|
1c:18:5f:ff:69:62:14:d2:97:28:33:9e:1e:0e:2e:f8:52:33:
|
||||||
|
83:3b:88:73:4c:fe:46:fc:0f:a7:0f:48:54:b8:a8:3d:ee:a5:
|
||||||
|
6d:a2:1c:e7:ef:34:90:ef:e6:c0:9c:10:66:81:1a:a9:3c:8b:
|
||||||
|
d5:48:e7:eb:d7:28:b2:26:69:89:81:77:c6:dc:64:7c:15:84:
|
||||||
|
59:ee:d7:90:bb:a7:2e:aa:95:0e:83:04:18:ca:be:31:4c:4e:
|
||||||
|
f8:99:e0:bf:48:ff:ed:d4:a2:d7:fd:5e:a2:f3:67:ad:5e:18:
|
||||||
|
78:5d:85:96:fa:b6:c5:8d:5a:08:a3:bf:72:87:2f:e6:fe:f0:
|
||||||
|
e7:01:26:f1:f3:05:43:02:9c:4f:b4:1c:0b:1f:bf:9e:4c:77:
|
||||||
|
af:4b:43:1f:13:bb:a2:0e:f1:af:ca:5e:b4:22:be:50:ba:b0:
|
||||||
|
2f:6f:21:6b:85:34:97:e9:0b:17:46:51:88:6e:47:36:2e:87:
|
||||||
|
8f:a3:a2:f4
|
||||||
123
MagiskOnWSA/DLL/cacerts/4a3b190e.0
Normal file
123
MagiskOnWSA/DLL/cacerts/4a3b190e.0
Normal file
@ -0,0 +1,123 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIFzzCCA7egAwIBAgIUWVzvad617aEkkFZ5UDDiq93NTVkwDQYJKoZIhvcNAQEL
|
||||||
|
BQAwdzELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAGA1UEBwwJSmVy
|
||||||
|
dXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRmcmVlLmxpbmsx
|
||||||
|
GjAYBgNVBAMMEU5ldEZyZWUgU2lnbiwgMDk5MB4XDTIxMDQwNzIyMTQ0NFoXDTMx
|
||||||
|
MDQwNTIyMTQ0NFowdzELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAG
|
||||||
|
A1UEBwwJSmVydXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRm
|
||||||
|
cmVlLmxpbmsxGjAYBgNVBAMMEU5ldEZyZWUgU2lnbiwgMDk5MIICIjANBgkqhkiG
|
||||||
|
9w0BAQEFAAOCAg8AMIICCgKCAgEAsnHF+C8rBiEzeZJ88nKVAZEh6SwSrNwoRNLV
|
||||||
|
gr69fj9mU7Tpgu8dRP+1q4MaZDTdXw+pqbvo/R9Jzc/YCN1BvrvL5ULCfNOwoCFa
|
||||||
|
MyLhNQ/zXMwfWiCeWr5qJ0rdpyWrGvXrurYIcbwzgAxpQA5krBUyZI/QJIjWi6PG
|
||||||
|
FZya7YrvzcvEG3Mbzl+E/G12FDuT5NVuNQIBE+mR9ZOFPrZsEDJb7SoZoIic7p1k
|
||||||
|
mrHwPMv3w07QIHOwFq9e8t/c7cFMEqOUC2/+Uw73J2MdYLX5vyTDtChAM0h5M00F
|
||||||
|
14tO7t46ofZ+GHj8w0kNoFk5Z1eNIXMasbs77fCN6LYHN1seuKvDh0p4ZdDLdObo
|
||||||
|
Y2XT8n+I7O2tY5PIaNoWDuQpKwUplY0WQFca7iKyy8ajojJPOMt40SaR7NtBvwl3
|
||||||
|
fYRPHvX57tQB55vpcTq7uVdaeEq3/G19wRVgDLs/MIFaPTV31RyOsrUzIc944aN8
|
||||||
|
YDBG4Mw6uUyVG3wxq9/QgZliW+wNj77gSMFZsj7aA0FqaDpQ4hdoGoehKP+B6y10
|
||||||
|
ZVOqe/sgPnZBW/KW+3uwOP/Bq809Q+G/JUQR23bhqCYht7zbi+f5pOmKXijAjnMh
|
||||||
|
Bs7fnxzc0YMNHYQ3RF9VNiteC8/+8rMgXIjq94cF8vAkm/kHT4qyNIzLVu/oUkrp
|
||||||
|
UYFd0YMCAwEAAaNTMFEwHQYDVR0OBBYEFHpftzbYdX1vM6czqDzA2ABKkMMzMB8G
|
||||||
|
A1UdIwQYMBaAFHpftzbYdX1vM6czqDzA2ABKkMMzMA8GA1UdEwEB/wQFMAMBAf8w
|
||||||
|
DQYJKoZIhvcNAQELBQADggIBACntHyKEjJaGqezp/SYdmvC6Gw0HVEahudZJTlM8
|
||||||
|
uWDCINdJFSSRMnAHC57qeKU+4AuN2ZO0BnRyVSK1XY0rlS0ZeNidRg2g1PgplJ3I
|
||||||
|
4KPKiq0LxllnPtSJiuNp81LazUj5iyqsHCPDE0pZVu1729kTfL2a2Ah3yaB5LxiX
|
||||||
|
6xMuZurI3LscOcfrN3oUH0lvlvt4hjmpi90UJ/Wtd+fllyw1sqInQfv87MOkoFzy
|
||||||
|
u9Rif2ZiBwMw32K9X7q/w7/iw77G1F9u/gbogP7CgDkKCxeyl5rLwkJKgV0g93xg
|
||||||
|
bonHdOmKlHYLMBuEx1CYdvAZcEwPdeiNuKbj1l8iJ4+PeYD2hRo+NmL/8Kjj3XTr
|
||||||
|
Xymah0bNsJFYda7W4plL6DzjvrMjwkLq1IeLDZLvL0iNk0wfe3GY7ojvqcY55XEo
|
||||||
|
TdEHiKqck8uTxzH/U5AGh26nbOxAe6AYNmbgmiJxWZXqYeqEmTx9B6Zk61RdFTem
|
||||||
|
gml5hqvUjM97JmSi/ORF31uP6+Jv35oQEo4YjeDD6ACDiDBjfyjPVMGVAxf6IRSt
|
||||||
|
s9O6OoYKZO09gaRuHXLSY9kfXSGsrV5mqbFr0r2C8n+u8kGjkILaCabil7cMBUfz
|
||||||
|
x95VUUI9AUunwF2ERMuTgfR1CE4gDJcUTU7Wf1o3xEpvCgQ6ffYzBXkHjeOTaZkI
|
||||||
|
zlA/
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
59:5c:ef:69:de:b5:ed:a1:24:90:56:79:50:30:e2:ab:dd:cd:4d:59
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, 099"
|
||||||
|
Validity
|
||||||
|
Not Before: Apr 7 22:14:44 2021 GMT
|
||||||
|
Not After : Apr 5 22:14:44 2031 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, 099"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:b2:71:c5:f8:2f:2b:06:21:33:79:92:7c:f2:72:
|
||||||
|
95:01:91:21:e9:2c:12:ac:dc:28:44:d2:d5:82:be:
|
||||||
|
bd:7e:3f:66:53:b4:e9:82:ef:1d:44:ff:b5:ab:83:
|
||||||
|
1a:64:34:dd:5f:0f:a9:a9:bb:e8:fd:1f:49:cd:cf:
|
||||||
|
d8:08:dd:41:be:bb:cb:e5:42:c2:7c:d3:b0:a0:21:
|
||||||
|
5a:33:22:e1:35:0f:f3:5c:cc:1f:5a:20:9e:5a:be:
|
||||||
|
6a:27:4a:dd:a7:25:ab:1a:f5:eb:ba:b6:08:71:bc:
|
||||||
|
33:80:0c:69:40:0e:64:ac:15:32:64:8f:d0:24:88:
|
||||||
|
d6:8b:a3:c6:15:9c:9a:ed:8a:ef:cd:cb:c4:1b:73:
|
||||||
|
1b:ce:5f:84:fc:6d:76:14:3b:93:e4:d5:6e:35:02:
|
||||||
|
01:13:e9:91:f5:93:85:3e:b6:6c:10:32:5b:ed:2a:
|
||||||
|
19:a0:88:9c:ee:9d:64:9a:b1:f0:3c:cb:f7:c3:4e:
|
||||||
|
d0:20:73:b0:16:af:5e:f2:df:dc:ed:c1:4c:12:a3:
|
||||||
|
94:0b:6f:fe:53:0e:f7:27:63:1d:60:b5:f9:bf:24:
|
||||||
|
c3:b4:28:40:33:48:79:33:4d:05:d7:8b:4e:ee:de:
|
||||||
|
3a:a1:f6:7e:18:78:fc:c3:49:0d:a0:59:39:67:57:
|
||||||
|
8d:21:73:1a:b1:bb:3b:ed:f0:8d:e8:b6:07:37:5b:
|
||||||
|
1e:b8:ab:c3:87:4a:78:65:d0:cb:74:e6:e8:63:65:
|
||||||
|
d3:f2:7f:88:ec:ed:ad:63:93:c8:68:da:16:0e:e4:
|
||||||
|
29:2b:05:29:95:8d:16:40:57:1a:ee:22:b2:cb:c6:
|
||||||
|
a3:a2:32:4f:38:cb:78:d1:26:91:ec:db:41:bf:09:
|
||||||
|
77:7d:84:4f:1e:f5:f9:ee:d4:01:e7:9b:e9:71:3a:
|
||||||
|
bb:b9:57:5a:78:4a:b7:fc:6d:7d:c1:15:60:0c:bb:
|
||||||
|
3f:30:81:5a:3d:35:77:d5:1c:8e:b2:b5:33:21:cf:
|
||||||
|
78:e1:a3:7c:60:30:46:e0:cc:3a:b9:4c:95:1b:7c:
|
||||||
|
31:ab:df:d0:81:99:62:5b:ec:0d:8f:be:e0:48:c1:
|
||||||
|
59:b2:3e:da:03:41:6a:68:3a:50:e2:17:68:1a:87:
|
||||||
|
a1:28:ff:81:eb:2d:74:65:53:aa:7b:fb:20:3e:76:
|
||||||
|
41:5b:f2:96:fb:7b:b0:38:ff:c1:ab:cd:3d:43:e1:
|
||||||
|
bf:25:44:11:db:76:e1:a8:26:21:b7:bc:db:8b:e7:
|
||||||
|
f9:a4:e9:8a:5e:28:c0:8e:73:21:06:ce:df:9f:1c:
|
||||||
|
dc:d1:83:0d:1d:84:37:44:5f:55:36:2b:5e:0b:cf:
|
||||||
|
fe:f2:b3:20:5c:88:ea:f7:87:05:f2:f0:24:9b:f9:
|
||||||
|
07:4f:8a:b2:34:8c:cb:56:ef:e8:52:4a:e9:51:81:
|
||||||
|
5d:d1:83
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
7A:5F:B7:36:D8:75:7D:6F:33:A7:33:A8:3C:C0:D8:00:4A:90:C3:33
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:7A:5F:B7:36:D8:75:7D:6F:33:A7:33:A8:3C:C0:D8:00:4A:90:C3:33
|
||||||
|
|
||||||
|
X509v3 Basic Constraints: critical
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
29:ed:1f:22:84:8c:96:86:a9:ec:e9:fd:26:1d:9a:f0:ba:1b:
|
||||||
|
0d:07:54:46:a1:b9:d6:49:4e:53:3c:b9:60:c2:20:d7:49:15:
|
||||||
|
24:91:32:70:07:0b:9e:ea:78:a5:3e:e0:0b:8d:d9:93:b4:06:
|
||||||
|
74:72:55:22:b5:5d:8d:2b:95:2d:19:78:d8:9d:46:0d:a0:d4:
|
||||||
|
f8:29:94:9d:c8:e0:a3:ca:8a:ad:0b:c6:59:67:3e:d4:89:8a:
|
||||||
|
e3:69:f3:52:da:cd:48:f9:8b:2a:ac:1c:23:c3:13:4a:59:56:
|
||||||
|
ed:7b:db:d9:13:7c:bd:9a:d8:08:77:c9:a0:79:2f:18:97:eb:
|
||||||
|
13:2e:66:ea:c8:dc:bb:1c:39:c7:eb:37:7a:14:1f:49:6f:96:
|
||||||
|
fb:78:86:39:a9:8b:dd:14:27:f5:ad:77:e7:e5:97:2c:35:b2:
|
||||||
|
a2:27:41:fb:fc:ec:c3:a4:a0:5c:f2:bb:d4:62:7f:66:62:07:
|
||||||
|
03:30:df:62:bd:5f:ba:bf:c3:bf:e2:c3:be:c6:d4:5f:6e:fe:
|
||||||
|
06:e8:80:fe:c2:80:39:0a:0b:17:b2:97:9a:cb:c2:42:4a:81:
|
||||||
|
5d:20:f7:7c:60:6e:89:c7:74:e9:8a:94:76:0b:30:1b:84:c7:
|
||||||
|
50:98:76:f0:19:70:4c:0f:75:e8:8d:b8:a6:e3:d6:5f:22:27:
|
||||||
|
8f:8f:79:80:f6:85:1a:3e:36:62:ff:f0:a8:e3:dd:74:eb:5f:
|
||||||
|
29:9a:87:46:cd:b0:91:58:75:ae:d6:e2:99:4b:e8:3c:e3:be:
|
||||||
|
b3:23:c2:42:ea:d4:87:8b:0d:92:ef:2f:48:8d:93:4c:1f:7b:
|
||||||
|
71:98:ee:88:ef:a9:c6:39:e5:71:28:4d:d1:07:88:aa:9c:93:
|
||||||
|
cb:93:c7:31:ff:53:90:06:87:6e:a7:6c:ec:40:7b:a0:18:36:
|
||||||
|
66:e0:9a:22:71:59:95:ea:61:ea:84:99:3c:7d:07:a6:64:eb:
|
||||||
|
54:5d:15:37:a6:82:69:79:86:ab:d4:8c:cf:7b:26:64:a2:fc:
|
||||||
|
e4:45:df:5b:8f:eb:e2:6f:df:9a:10:12:8e:18:8d:e0:c3:e8:
|
||||||
|
00:83:88:30:63:7f:28:cf:54:c1:95:03:17:fa:21:14:ad:b3:
|
||||||
|
d3:ba:3a:86:0a:64:ed:3d:81:a4:6e:1d:72:d2:63:d9:1f:5d:
|
||||||
|
21:ac:ad:5e:66:a9:b1:6b:d2:bd:82:f2:7f:ae:f2:41:a3:90:
|
||||||
|
82:da:09:a6:e2:97:b7:0c:05:47:f3:c7:de:55:51:42:3d:01:
|
||||||
|
4b:a7:c0:5d:84:44:cb:93:81:f4:75:08:4e:20:0c:97:14:4d:
|
||||||
|
4e:d6:7f:5a:37:c4:4a:6f:0a:04:3a:7d:f6:33:05:79:07:8d:
|
||||||
|
e3:93:69:99:08:ce:50:3f
|
||||||
123
MagiskOnWSA/DLL/cacerts/4eba579e.0
Normal file
123
MagiskOnWSA/DLL/cacerts/4eba579e.0
Normal file
@ -0,0 +1,123 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIFzzCCA7egAwIBAgIUERKcb5NZIK+7kIzZeeqoTynDxo8wDQYJKoZIhvcNAQEL
|
||||||
|
BQAwdzELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAGA1UEBwwJSmVy
|
||||||
|
dXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRmcmVlLmxpbmsx
|
||||||
|
GjAYBgNVBAMMEU5ldEZyZWUgU2lnbiwgSE9UMB4XDTIyMDkxNDE1MjE0MVoXDTMy
|
||||||
|
MDkxMTE1MjE0MVowdzELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAG
|
||||||
|
A1UEBwwJSmVydXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRm
|
||||||
|
cmVlLmxpbmsxGjAYBgNVBAMMEU5ldEZyZWUgU2lnbiwgSE9UMIICIjANBgkqhkiG
|
||||||
|
9w0BAQEFAAOCAg8AMIICCgKCAgEAtAAmmLun08jzoWMLyC/fzCu9aES7fLWCU2Ur
|
||||||
|
u3sntuHLDJabIvU0p16hCMC3MVOTKFAKOJ9A+REyOyewQLJ+0Oi0rOPA6jk/+Srj
|
||||||
|
l69AwzkJYFli7ORClC/N1E2aKWj9evZHHdXeRMs2pklM9eRR+wYQUTQ5bkd0/Lsj
|
||||||
|
81QDUSzmgX/qkq3Dc4AiSt0gR+rd+c70y8IjVnBSwmHspyGv8Ve9DdRR3U01H8pM
|
||||||
|
gYpQVrN8BVfRNVpQgpjlKQZKQM1CcLFqUq++fG/QnhgcVuygGnqWAjNCkfbWi7Hq
|
||||||
|
IMYK5cyA3oLYiBH8gE0Js4ypf/jtFNBTeE7aiNbF6YgD6kPvlBIQ3nWHcvYz83mc
|
||||||
|
/yI8kDPHPBmNnCTxa46AYRBt3ungIKchSoIP2pfUDcwPI8C2o79ninvYxtwg2FH6
|
||||||
|
Mbc/hJqaGrTsFgw9rGitniZ4GHVPftW89O3xBENP9QAHimwbG8BCiwuweDu2xPsR
|
||||||
|
AJJ+a9bFRucDIaacOzrCjuzbXFJIy3KOgghe8V5mYypLHq8/pcDWczL59iWZit+l
|
||||||
|
2gt+wYIU3HxzC2AqzlBFadI10IlLFolaGyH9hJd5U0kYEXVp2IQV/6PGVhvmJI9y
|
||||||
|
9n+MqReibwUQVfuEg+l0gblqC2eTGnab5AVoCK/4cK+zxE0+wBpK70X4NtYLf0BO
|
||||||
|
WItUFK8CAwEAAaNTMFEwHQYDVR0OBBYEFG+/JFFhEinGuN7gWnOZxSMerGmZMB8G
|
||||||
|
A1UdIwQYMBaAFG+/JFFhEinGuN7gWnOZxSMerGmZMA8GA1UdEwEB/wQFMAMBAf8w
|
||||||
|
DQYJKoZIhvcNAQELBQADggIBAEVxrI5JmqQi5DhRAVIet41hFWrEIiJwYMbRYhRK
|
||||||
|
NpW1U4X7OiOm+/8v68oMkh3KHwbpIo48/egUDgv+F7Dzz5NhRgjXQbIW7ixO5+i+
|
||||||
|
7rW+177oJVvKtpD2NAp4o0Nty826AntDzyulSs7KvoE+Ifwq7iUTNwPmeOBpd7N2
|
||||||
|
WCZzpjOhhbuG4yYE+K76nZ34C8+7w3488iL8e5RwJQeuvXnEy4NiFzZmsoYqPUBd
|
||||||
|
HaZIQePxXI3jYi1YdckED3GZwo9VBZkarA5GekBvF9B2z/eKoHfnRrHDuQmBSAY3
|
||||||
|
+GBfqG6WNpDisKSj4YgeNXkTOZjOCyl/a3nwpLUawxAJyPjtgzc2vRDg3eVHUJNN
|
||||||
|
HIp60XVRQwwCTH6dHJiHsDCb2/6DgZzcUW20a4u8+zgDN+M+V8DYGjeTN/2X18br
|
||||||
|
kGN67L+n2krGQmVM4vu+42uOx0SJR/x10D8io7Vl9khWG3pB3GBoQSHivenzNPAW
|
||||||
|
BfJJG4keyG3EAVPHmyHpjP36NXe8rmimOgVVGDujEz+je+w9L4YQgQg5VfVp3+Pu
|
||||||
|
Wd7BbSsig+Vqgw1EDksMScLh34ZwniR1w2QL86XT5ExYNXQdo18fVYV0/OyzXKZx
|
||||||
|
8qnaParnjvguOl0YG4aXh0+72lEeIHXpPMmy6TDDqAOgNlrVbjviBw/J4Nzlty9s
|
||||||
|
bXLk
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
11:12:9c:6f:93:59:20:af:bb:90:8c:d9:79:ea:a8:4f:29:c3:c6:8f
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, HOT"
|
||||||
|
Validity
|
||||||
|
Not Before: Sep 14 15:21:41 2022 GMT
|
||||||
|
Not After : Sep 11 15:21:41 2032 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, HOT"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:b4:00:26:98:bb:a7:d3:c8:f3:a1:63:0b:c8:2f:
|
||||||
|
df:cc:2b:bd:68:44:bb:7c:b5:82:53:65:2b:bb:7b:
|
||||||
|
27:b6:e1:cb:0c:96:9b:22:f5:34:a7:5e:a1:08:c0:
|
||||||
|
b7:31:53:93:28:50:0a:38:9f:40:f9:11:32:3b:27:
|
||||||
|
b0:40:b2:7e:d0:e8:b4:ac:e3:c0:ea:39:3f:f9:2a:
|
||||||
|
e3:97:af:40:c3:39:09:60:59:62:ec:e4:42:94:2f:
|
||||||
|
cd:d4:4d:9a:29:68:fd:7a:f6:47:1d:d5:de:44:cb:
|
||||||
|
36:a6:49:4c:f5:e4:51:fb:06:10:51:34:39:6e:47:
|
||||||
|
74:fc:bb:23:f3:54:03:51:2c:e6:81:7f:ea:92:ad:
|
||||||
|
c3:73:80:22:4a:dd:20:47:ea:dd:f9:ce:f4:cb:c2:
|
||||||
|
23:56:70:52:c2:61:ec:a7:21:af:f1:57:bd:0d:d4:
|
||||||
|
51:dd:4d:35:1f:ca:4c:81:8a:50:56:b3:7c:05:57:
|
||||||
|
d1:35:5a:50:82:98:e5:29:06:4a:40:cd:42:70:b1:
|
||||||
|
6a:52:af:be:7c:6f:d0:9e:18:1c:56:ec:a0:1a:7a:
|
||||||
|
96:02:33:42:91:f6:d6:8b:b1:ea:20:c6:0a:e5:cc:
|
||||||
|
80:de:82:d8:88:11:fc:80:4d:09:b3:8c:a9:7f:f8:
|
||||||
|
ed:14:d0:53:78:4e:da:88:d6:c5:e9:88:03:ea:43:
|
||||||
|
ef:94:12:10:de:75:87:72:f6:33:f3:79:9c:ff:22:
|
||||||
|
3c:90:33:c7:3c:19:8d:9c:24:f1:6b:8e:80:61:10:
|
||||||
|
6d:de:e9:e0:20:a7:21:4a:82:0f:da:97:d4:0d:cc:
|
||||||
|
0f:23:c0:b6:a3:bf:67:8a:7b:d8:c6:dc:20:d8:51:
|
||||||
|
fa:31:b7:3f:84:9a:9a:1a:b4:ec:16:0c:3d:ac:68:
|
||||||
|
ad:9e:26:78:18:75:4f:7e:d5:bc:f4:ed:f1:04:43:
|
||||||
|
4f:f5:00:07:8a:6c:1b:1b:c0:42:8b:0b:b0:78:3b:
|
||||||
|
b6:c4:fb:11:00:92:7e:6b:d6:c5:46:e7:03:21:a6:
|
||||||
|
9c:3b:3a:c2:8e:ec:db:5c:52:48:cb:72:8e:82:08:
|
||||||
|
5e:f1:5e:66:63:2a:4b:1e:af:3f:a5:c0:d6:73:32:
|
||||||
|
f9:f6:25:99:8a:df:a5:da:0b:7e:c1:82:14:dc:7c:
|
||||||
|
73:0b:60:2a:ce:50:45:69:d2:35:d0:89:4b:16:89:
|
||||||
|
5a:1b:21:fd:84:97:79:53:49:18:11:75:69:d8:84:
|
||||||
|
15:ff:a3:c6:56:1b:e6:24:8f:72:f6:7f:8c:a9:17:
|
||||||
|
a2:6f:05:10:55:fb:84:83:e9:74:81:b9:6a:0b:67:
|
||||||
|
93:1a:76:9b:e4:05:68:08:af:f8:70:af:b3:c4:4d:
|
||||||
|
3e:c0:1a:4a:ef:45:f8:36:d6:0b:7f:40:4e:58:8b:
|
||||||
|
54:14:af
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
6F:BF:24:51:61:12:29:C6:B8:DE:E0:5A:73:99:C5:23:1E:AC:69:99
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:6F:BF:24:51:61:12:29:C6:B8:DE:E0:5A:73:99:C5:23:1E:AC:69:99
|
||||||
|
|
||||||
|
X509v3 Basic Constraints: critical
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
45:71:ac:8e:49:9a:a4:22:e4:38:51:01:52:1e:b7:8d:61:15:
|
||||||
|
6a:c4:22:22:70:60:c6:d1:62:14:4a:36:95:b5:53:85:fb:3a:
|
||||||
|
23:a6:fb:ff:2f:eb:ca:0c:92:1d:ca:1f:06:e9:22:8e:3c:fd:
|
||||||
|
e8:14:0e:0b:fe:17:b0:f3:cf:93:61:46:08:d7:41:b2:16:ee:
|
||||||
|
2c:4e:e7:e8:be:ee:b5:be:d7:be:e8:25:5b:ca:b6:90:f6:34:
|
||||||
|
0a:78:a3:43:6d:cb:cd:ba:02:7b:43:cf:2b:a5:4a:ce:ca:be:
|
||||||
|
81:3e:21:fc:2a:ee:25:13:37:03:e6:78:e0:69:77:b3:76:58:
|
||||||
|
26:73:a6:33:a1:85:bb:86:e3:26:04:f8:ae:fa:9d:9d:f8:0b:
|
||||||
|
cf:bb:c3:7e:3c:f2:22:fc:7b:94:70:25:07:ae:bd:79:c4:cb:
|
||||||
|
83:62:17:36:66:b2:86:2a:3d:40:5d:1d:a6:48:41:e3:f1:5c:
|
||||||
|
8d:e3:62:2d:58:75:c9:04:0f:71:99:c2:8f:55:05:99:1a:ac:
|
||||||
|
0e:46:7a:40:6f:17:d0:76:cf:f7:8a:a0:77:e7:46:b1:c3:b9:
|
||||||
|
09:81:48:06:37:f8:60:5f:a8:6e:96:36:90:e2:b0:a4:a3:e1:
|
||||||
|
88:1e:35:79:13:39:98:ce:0b:29:7f:6b:79:f0:a4:b5:1a:c3:
|
||||||
|
10:09:c8:f8:ed:83:37:36:bd:10:e0:dd:e5:47:50:93:4d:1c:
|
||||||
|
8a:7a:d1:75:51:43:0c:02:4c:7e:9d:1c:98:87:b0:30:9b:db:
|
||||||
|
fe:83:81:9c:dc:51:6d:b4:6b:8b:bc:fb:38:03:37:e3:3e:57:
|
||||||
|
c0:d8:1a:37:93:37:fd:97:d7:c6:eb:90:63:7a:ec:bf:a7:da:
|
||||||
|
4a:c6:42:65:4c:e2:fb:be:e3:6b:8e:c7:44:89:47:fc:75:d0:
|
||||||
|
3f:22:a3:b5:65:f6:48:56:1b:7a:41:dc:60:68:41:21:e2:bd:
|
||||||
|
e9:f3:34:f0:16:05:f2:49:1b:89:1e:c8:6d:c4:01:53:c7:9b:
|
||||||
|
21:e9:8c:fd:fa:35:77:bc:ae:68:a6:3a:05:55:18:3b:a3:13:
|
||||||
|
3f:a3:7b:ec:3d:2f:86:10:81:08:39:55:f5:69:df:e3:ee:59:
|
||||||
|
de:c1:6d:2b:22:83:e5:6a:83:0d:44:0e:4b:0c:49:c2:e1:df:
|
||||||
|
86:70:9e:24:75:c3:64:0b:f3:a5:d3:e4:4c:58:35:74:1d:a3:
|
||||||
|
5f:1f:55:85:74:fc:ec:b3:5c:a6:71:f2:a9:da:3d:aa:e7:8e:
|
||||||
|
f8:2e:3a:5d:18:1b:86:97:87:4f:bb:da:51:1e:20:75:e9:3c:
|
||||||
|
c9:b2:e9:30:c3:a8:03:a0:36:5a:d5:6e:3b:e2:07:0f:c9:e0:
|
||||||
|
dc:e5:b7:2f:6c:6d:72:e4
|
||||||
123
MagiskOnWSA/DLL/cacerts/6207c6f5.0
Normal file
123
MagiskOnWSA/DLL/cacerts/6207c6f5.0
Normal file
@ -0,0 +1,123 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIF0zCCA7ugAwIBAgIUaH5U+ogY8MmdlevWZGKqnge9GKQwDQYJKoZIhvcNAQEL
|
||||||
|
BQAweTELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAGA1UEBwwJSmVy
|
||||||
|
dXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRmcmVlLmxpbmsx
|
||||||
|
HDAaBgNVBAMME05ldEZyZWUgU2lnbiwgQmV6ZXEwHhcNMjIwNjAxMTk1NTIxWhcN
|
||||||
|
MzIwNTI5MTk1NTIxWjB5MQswCQYDVQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIw
|
||||||
|
EAYDVQQHDAlKZXJ1c2FsZW0xEDAOBgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5l
|
||||||
|
dGZyZWUubGluazEcMBoGA1UEAwwTTmV0RnJlZSBTaWduLCBCZXplcTCCAiIwDQYJ
|
||||||
|
KoZIhvcNAQEBBQADggIPADCCAgoCggIBANipYPeTK3GJ9BpwEpEGE/hzB8MlD+Rs
|
||||||
|
hw4tTWWRtZC0ok9kY/jmWJSzRMP4jKbOPtKkiUNNd3l2SvgvrHPuMz/R9B728wK2
|
||||||
|
ZYS295KTRDSgM51e+gCfziUXR36mCCvjuLmRdVbsXrAJjAtlPN1SD9eFDtMx6Pm8
|
||||||
|
LfSK6HyVF4Igafq8el6x9lSdfGqWWxWjuBaO6ooNUoIORYOLOQezMHRG1vfabx58
|
||||||
|
aEKZSN+bvEPmf4m1RXu4ynevE8aEQBHsr/4X7sU7hRXXrxLkS5qJSeqbfS+tp36a
|
||||||
|
HaVA8APRradFLvZa9ejAli8WAwwdw2r6AATQ3mmuIcaZUeC954HPgUwaz97wE2zo
|
||||||
|
GMbsX7bE9oEyLRT8sDV+dvN8MEXvt2XWx4icHLuycqxOGzZKkjmP73qMdeZw+mxW
|
||||||
|
xBk8H7pCWBQsJ5z0xxtir5kBVUqPSdmAOsz3FLhRyW8JB09JurZc3czxaCrVT7oS
|
||||||
|
MGIj+koFIYlbQqudwBTPF3hUBlgvS3PA339YHD6H8Fncj20tb2MxQ6jb5IDnFvY/
|
||||||
|
dc36sSauiUCzwPJM1FHDmaJDQcj7r2EArWDxZrWL1Zt99xf3yQQFUWh8+BMOba9M
|
||||||
|
x1E6XWfhVGlhS9yks0DwOKktO+rZwO3fVTVprWvnzFOWmpHAzvLxfiS5blseebAM
|
||||||
|
3+S4PGQiCHJBAgMBAAGjUzBRMB0GA1UdDgQWBBSFbv9UhQwCMY5hdYElGT2uCS2g
|
||||||
|
PTAfBgNVHSMEGDAWgBSFbv9UhQwCMY5hdYElGT2uCS2gPTAPBgNVHRMBAf8EBTAD
|
||||||
|
AQH/MA0GCSqGSIb3DQEBCwUAA4ICAQB5FmjWgu11dysbxacJO5uLYQ/UVipSFAsl
|
||||||
|
s/x04NRHona1UpOLGt6y70Q4XjkLnabeYc+x5g1UUr6BzDjXb4CG/FLjGhNP4zPE
|
||||||
|
xL9bUXpVThFHyO1LrsnbSLfIJZZ4CRvPmx0vbK0G9p23PTNCv7RFqDfqfA1P0z/g
|
||||||
|
X1n8SatOauOefsM94AihODwoOWLFsl14YnYp99V1f7ChrqZ4GKzgb0M+COJLOAIV
|
||||||
|
Ur6qaa5eqKf8jIw08xbZy19K4jgOEGIDifmoAtYEpCwIzH9VPeDqdcaBGuc+uZUp
|
||||||
|
9mxgIbJk0qgaPmu25TM12x66YeZZvPgeOycl2dzMTIwPvw3TfNzrio7tPRk5GEcT
|
||||||
|
3KzngfFpvQyros/kYQMKMPYL5hssRae4aDGr9sS1D4LR31hhopQ0+w4y/+kQJDbB
|
||||||
|
JCkUP87ae6mtNW4sCXaStWaZZzomonEAxNkh4sfBMT5wVsglU236k/yN5n7Ib/mL
|
||||||
|
yGUBs6lzMdcScG+Ath4cwtxNnC3m2g8w8/MYAf/+wBL/A8r2GAPTqLvfjtEzH621
|
||||||
|
b1Yw4//rSJg5ZpO1IGBFIVBFImBHOpHrjigPEJECiUS3y0jKUNyymo66QqRHwl1Y
|
||||||
|
71gRskGUK6tyfO45ZiLH8r8m7NR1wXBmAAmtOtdzi5H2ahVRNrW/zrfS7ttASJB5
|
||||||
|
20p8M55zUw==
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
68:7e:54:fa:88:18:f0:c9:9d:95:eb:d6:64:62:aa:9e:07:bd:18:a4
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, Bezeq"
|
||||||
|
Validity
|
||||||
|
Not Before: Jun 1 19:55:21 2022 GMT
|
||||||
|
Not After : May 29 19:55:21 2032 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, Bezeq"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:d8:a9:60:f7:93:2b:71:89:f4:1a:70:12:91:06:
|
||||||
|
13:f8:73:07:c3:25:0f:e4:6c:87:0e:2d:4d:65:91:
|
||||||
|
b5:90:b4:a2:4f:64:63:f8:e6:58:94:b3:44:c3:f8:
|
||||||
|
8c:a6:ce:3e:d2:a4:89:43:4d:77:79:76:4a:f8:2f:
|
||||||
|
ac:73:ee:33:3f:d1:f4:1e:f6:f3:02:b6:65:84:b6:
|
||||||
|
f7:92:93:44:34:a0:33:9d:5e:fa:00:9f:ce:25:17:
|
||||||
|
47:7e:a6:08:2b:e3:b8:b9:91:75:56:ec:5e:b0:09:
|
||||||
|
8c:0b:65:3c:dd:52:0f:d7:85:0e:d3:31:e8:f9:bc:
|
||||||
|
2d:f4:8a:e8:7c:95:17:82:20:69:fa:bc:7a:5e:b1:
|
||||||
|
f6:54:9d:7c:6a:96:5b:15:a3:b8:16:8e:ea:8a:0d:
|
||||||
|
52:82:0e:45:83:8b:39:07:b3:30:74:46:d6:f7:da:
|
||||||
|
6f:1e:7c:68:42:99:48:df:9b:bc:43:e6:7f:89:b5:
|
||||||
|
45:7b:b8:ca:77:af:13:c6:84:40:11:ec:af:fe:17:
|
||||||
|
ee:c5:3b:85:15:d7:af:12:e4:4b:9a:89:49:ea:9b:
|
||||||
|
7d:2f:ad:a7:7e:9a:1d:a5:40:f0:03:d1:ad:a7:45:
|
||||||
|
2e:f6:5a:f5:e8:c0:96:2f:16:03:0c:1d:c3:6a:fa:
|
||||||
|
00:04:d0:de:69:ae:21:c6:99:51:e0:bd:e7:81:cf:
|
||||||
|
81:4c:1a:cf:de:f0:13:6c:e8:18:c6:ec:5f:b6:c4:
|
||||||
|
f6:81:32:2d:14:fc:b0:35:7e:76:f3:7c:30:45:ef:
|
||||||
|
b7:65:d6:c7:88:9c:1c:bb:b2:72:ac:4e:1b:36:4a:
|
||||||
|
92:39:8f:ef:7a:8c:75:e6:70:fa:6c:56:c4:19:3c:
|
||||||
|
1f:ba:42:58:14:2c:27:9c:f4:c7:1b:62:af:99:01:
|
||||||
|
55:4a:8f:49:d9:80:3a:cc:f7:14:b8:51:c9:6f:09:
|
||||||
|
07:4f:49:ba:b6:5c:dd:cc:f1:68:2a:d5:4f:ba:12:
|
||||||
|
30:62:23:fa:4a:05:21:89:5b:42:ab:9d:c0:14:cf:
|
||||||
|
17:78:54:06:58:2f:4b:73:c0:df:7f:58:1c:3e:87:
|
||||||
|
f0:59:dc:8f:6d:2d:6f:63:31:43:a8:db:e4:80:e7:
|
||||||
|
16:f6:3f:75:cd:fa:b1:26:ae:89:40:b3:c0:f2:4c:
|
||||||
|
d4:51:c3:99:a2:43:41:c8:fb:af:61:00:ad:60:f1:
|
||||||
|
66:b5:8b:d5:9b:7d:f7:17:f7:c9:04:05:51:68:7c:
|
||||||
|
f8:13:0e:6d:af:4c:c7:51:3a:5d:67:e1:54:69:61:
|
||||||
|
4b:dc:a4:b3:40:f0:38:a9:2d:3b:ea:d9:c0:ed:df:
|
||||||
|
55:35:69:ad:6b:e7:cc:53:96:9a:91:c0:ce:f2:f1:
|
||||||
|
7e:24:b9:6e:5b:1e:79:b0:0c:df:e4:b8:3c:64:22:
|
||||||
|
08:72:41
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
85:6E:FF:54:85:0C:02:31:8E:61:75:81:25:19:3D:AE:09:2D:A0:3D
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:85:6E:FF:54:85:0C:02:31:8E:61:75:81:25:19:3D:AE:09:2D:A0:3D
|
||||||
|
|
||||||
|
X509v3 Basic Constraints: critical
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
79:16:68:d6:82:ed:75:77:2b:1b:c5:a7:09:3b:9b:8b:61:0f:
|
||||||
|
d4:56:2a:52:14:0b:25:b3:fc:74:e0:d4:47:a2:76:b5:52:93:
|
||||||
|
8b:1a:de:b2:ef:44:38:5e:39:0b:9d:a6:de:61:cf:b1:e6:0d:
|
||||||
|
54:52:be:81:cc:38:d7:6f:80:86:fc:52:e3:1a:13:4f:e3:33:
|
||||||
|
c4:c4:bf:5b:51:7a:55:4e:11:47:c8:ed:4b:ae:c9:db:48:b7:
|
||||||
|
c8:25:96:78:09:1b:cf:9b:1d:2f:6c:ad:06:f6:9d:b7:3d:33:
|
||||||
|
42:bf:b4:45:a8:37:ea:7c:0d:4f:d3:3f:e0:5f:59:fc:49:ab:
|
||||||
|
4e:6a:e3:9e:7e:c3:3d:e0:08:a1:38:3c:28:39:62:c5:b2:5d:
|
||||||
|
78:62:76:29:f7:d5:75:7f:b0:a1:ae:a6:78:18:ac:e0:6f:43:
|
||||||
|
3e:08:e2:4b:38:02:15:52:be:aa:69:ae:5e:a8:a7:fc:8c:8c:
|
||||||
|
34:f3:16:d9:cb:5f:4a:e2:38:0e:10:62:03:89:f9:a8:02:d6:
|
||||||
|
04:a4:2c:08:cc:7f:55:3d:e0:ea:75:c6:81:1a:e7:3e:b9:95:
|
||||||
|
29:f6:6c:60:21:b2:64:d2:a8:1a:3e:6b:b6:e5:33:35:db:1e:
|
||||||
|
ba:61:e6:59:bc:f8:1e:3b:27:25:d9:dc:cc:4c:8c:0f:bf:0d:
|
||||||
|
d3:7c:dc:eb:8a:8e:ed:3d:19:39:18:47:13:dc:ac:e7:81:f1:
|
||||||
|
69:bd:0c:ab:a2:cf:e4:61:03:0a:30:f6:0b:e6:1b:2c:45:a7:
|
||||||
|
b8:68:31:ab:f6:c4:b5:0f:82:d1:df:58:61:a2:94:34:fb:0e:
|
||||||
|
32:ff:e9:10:24:36:c1:24:29:14:3f:ce:da:7b:a9:ad:35:6e:
|
||||||
|
2c:09:76:92:b5:66:99:67:3a:26:a2:71:00:c4:d9:21:e2:c7:
|
||||||
|
c1:31:3e:70:56:c8:25:53:6d:fa:93:fc:8d:e6:7e:c8:6f:f9:
|
||||||
|
8b:c8:65:01:b3:a9:73:31:d7:12:70:6f:80:b6:1e:1c:c2:dc:
|
||||||
|
4d:9c:2d:e6:da:0f:30:f3:f3:18:01:ff:fe:c0:12:ff:03:ca:
|
||||||
|
f6:18:03:d3:a8:bb:df:8e:d1:33:1f:ad:b5:6f:56:30:e3:ff:
|
||||||
|
eb:48:98:39:66:93:b5:20:60:45:21:50:45:22:60:47:3a:91:
|
||||||
|
eb:8e:28:0f:10:91:02:89:44:b7:cb:48:ca:50:dc:b2:9a:8e:
|
||||||
|
ba:42:a4:47:c2:5d:58:ef:58:11:b2:41:94:2b:ab:72:7c:ee:
|
||||||
|
39:66:22:c7:f2:bf:26:ec:d4:75:c1:70:66:00:09:ad:3a:d7:
|
||||||
|
73:8b:91:f6:6a:15:51:36:b5:bf:ce:b7:d2:ee:db:40:48:90:
|
||||||
|
79:db:4a:7c:33:9e:73:53
|
||||||
81
MagiskOnWSA/DLL/cacerts/66bbb532.0
Normal file
81
MagiskOnWSA/DLL/cacerts/66bbb532.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIID4TCCAsmgAwIBAgIJAIsaro78xwDlMA0GCSqGSIb3DQEBCwUAMIGGMQswCQYD
|
||||||
|
VQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIwEAYDVQQHDAlKZXJ1c2FsZW0xEDAO
|
||||||
|
BgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5ldGZyZWUubGluazEpMCcGA1UEAwwg
|
||||||
|
TmV0RnJlZSBTaWduICwgS29zaGVyU2ltIENlbGxjb20wHhcNMTcwMjA5MTYzNzIz
|
||||||
|
WhcNMjYxMjE5MTYzNzIzWjCBhjELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFl
|
||||||
|
bDESMBAGA1UEBwwJSmVydXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQL
|
||||||
|
DAxuZXRmcmVlLmxpbmsxKTAnBgNVBAMMIE5ldEZyZWUgU2lnbiAsIEtvc2hlclNp
|
||||||
|
bSBDZWxsY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAsGzn8/an
|
||||||
|
SokAGXPd8XvBEyNCEby+4MQNa/osraC7ORKNk3C42b0cfPhf8pUpj66L69EcgmhS
|
||||||
|
veZyrZYlDGnUh7/2faF0EwtxffN1UK5qzEFfd2YICHXl81pVvifbmZgB3/c64KFm
|
||||||
|
+2CsyWZ2XTGPzD9zIrJdHFGgHdVu/UDDj0oLU2G0v0npse7au/gKNSxx1StzP3N6
|
||||||
|
uOo6Ih3KB74FCF0hc2aiJpfE9ECinSeHHF39TMzEJNvC4+fuTOb1odYsNP83otp7
|
||||||
|
KbLjCQsCMomxQlQTy3vfTvCA8f2BSILo4U6j/BHyhZriyjvhnPTlonWBrLHU5bd+
|
||||||
|
HNeiIeucPgRz+QIDAQABo1AwTjAdBgNVHQ4EFgQUf3PgrlRBo19oBK4M47swRdXg
|
||||||
|
pAQwHwYDVR0jBBgwFoAUf3PgrlRBo19oBK4M47swRdXgpAQwDAYDVR0TBAUwAwEB
|
||||||
|
/zANBgkqhkiG9w0BAQsFAAOCAQEAUIdlD+x9CFJXvKgmW6FAuAV3w6JG8zz4MwQO
|
||||||
|
5aXbs3g8ioIJ6KUBmtzcQhM/NLVr/oXIXPZxXWI7tP3f5N3iLVwrh6krKOU+jSna
|
||||||
|
HXK0BYXPivp8rRJX56gUQqLUlS94l3iAHX8N+qY2D0hSj4H044R5mWsuYxrtdAr2
|
||||||
|
glaz6luXOo+NMH2uRnWYX/uAAEpbQLPlztVsoV4LsZ2C54dK7neQ+A6qRL/IZwJE
|
||||||
|
bYeRwWYoK7OY/BNLj/Vx25IzZYlU/lP8qa6UcUWmPeyIPJqPvjdO95zEodX2iuWE
|
||||||
|
cuc5pUqSu5/xxosDx3vWpFhPaU5gq9WEN5uPgFd96yHoFKWvtg==
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
8b:1a:ae:8e:fc:c7:00:e5
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , KosherSim Cellcom"
|
||||||
|
Validity
|
||||||
|
Not Before: Feb 9 16:37:23 2017 GMT
|
||||||
|
Not After : Dec 19 16:37:23 2026 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , KosherSim Cellcom"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:b0:6c:e7:f3:f6:a7:4a:89:00:19:73:dd:f1:7b:
|
||||||
|
c1:13:23:42:11:bc:be:e0:c4:0d:6b:fa:2c:ad:a0:
|
||||||
|
bb:39:12:8d:93:70:b8:d9:bd:1c:7c:f8:5f:f2:95:
|
||||||
|
29:8f:ae:8b:eb:d1:1c:82:68:52:bd:e6:72:ad:96:
|
||||||
|
25:0c:69:d4:87:bf:f6:7d:a1:74:13:0b:71:7d:f3:
|
||||||
|
75:50:ae:6a:cc:41:5f:77:66:08:08:75:e5:f3:5a:
|
||||||
|
55:be:27:db:99:98:01:df:f7:3a:e0:a1:66:fb:60:
|
||||||
|
ac:c9:66:76:5d:31:8f:cc:3f:73:22:b2:5d:1c:51:
|
||||||
|
a0:1d:d5:6e:fd:40:c3:8f:4a:0b:53:61:b4:bf:49:
|
||||||
|
e9:b1:ee:da:bb:f8:0a:35:2c:71:d5:2b:73:3f:73:
|
||||||
|
7a:b8:ea:3a:22:1d:ca:07:be:05:08:5d:21:73:66:
|
||||||
|
a2:26:97:c4:f4:40:a2:9d:27:87:1c:5d:fd:4c:cc:
|
||||||
|
c4:24:db:c2:e3:e7:ee:4c:e6:f5:a1:d6:2c:34:ff:
|
||||||
|
37:a2:da:7b:29:b2:e3:09:0b:02:32:89:b1:42:54:
|
||||||
|
13:cb:7b:df:4e:f0:80:f1:fd:81:48:82:e8:e1:4e:
|
||||||
|
a3:fc:11:f2:85:9a:e2:ca:3b:e1:9c:f4:e5:a2:75:
|
||||||
|
81:ac:b1:d4:e5:b7:7e:1c:d7:a2:21:eb:9c:3e:04:
|
||||||
|
73:f9
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
7F:73:E0:AE:54:41:A3:5F:68:04:AE:0C:E3:BB:30:45:D5:E0:A4:04
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:7F:73:E0:AE:54:41:A3:5F:68:04:AE:0C:E3:BB:30:45:D5:E0:A4:04
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
50:87:65:0f:ec:7d:08:52:57:bc:a8:26:5b:a1:40:b8:05:77:
|
||||||
|
c3:a2:46:f3:3c:f8:33:04:0e:e5:a5:db:b3:78:3c:8a:82:09:
|
||||||
|
e8:a5:01:9a:dc:dc:42:13:3f:34:b5:6b:fe:85:c8:5c:f6:71:
|
||||||
|
5d:62:3b:b4:fd:df:e4:dd:e2:2d:5c:2b:87:a9:2b:28:e5:3e:
|
||||||
|
8d:29:da:1d:72:b4:05:85:cf:8a:fa:7c:ad:12:57:e7:a8:14:
|
||||||
|
42:a2:d4:95:2f:78:97:78:80:1d:7f:0d:fa:a6:36:0f:48:52:
|
||||||
|
8f:81:f4:e3:84:79:99:6b:2e:63:1a:ed:74:0a:f6:82:56:b3:
|
||||||
|
ea:5b:97:3a:8f:8d:30:7d:ae:46:75:98:5f:fb:80:00:4a:5b:
|
||||||
|
40:b3:e5:ce:d5:6c:a1:5e:0b:b1:9d:82:e7:87:4a:ee:77:90:
|
||||||
|
f8:0e:aa:44:bf:c8:67:02:44:6d:87:91:c1:66:28:2b:b3:98:
|
||||||
|
fc:13:4b:8f:f5:71:db:92:33:65:89:54:fe:53:fc:a9:ae:94:
|
||||||
|
71:45:a6:3d:ec:88:3c:9a:8f:be:37:4e:f7:9c:c4:a1:d5:f6:
|
||||||
|
8a:e5:84:72:e7:39:a5:4a:92:bb:9f:f1:c6:8b:03:c7:7b:d6:
|
||||||
|
a4:58:4f:69:4e:60:ab:d5:84:37:9b:8f:80:57:7d:eb:21:e8:
|
||||||
|
14:a5:af:b6
|
||||||
81
MagiskOnWSA/DLL/cacerts/820d5f23.0
Normal file
81
MagiskOnWSA/DLL/cacerts/820d5f23.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIDzTCCArWgAwIBAgIJAM/zhl8GVAzYMA0GCSqGSIb3DQEBCwUAMH0xCzAJBgNV
|
||||||
|
BAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcMCUplcnVzYWxlbTEQMA4G
|
||||||
|
A1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0ZnJlZS5saW5rMSAwHgYDVQQDDBdO
|
||||||
|
ZXRGcmVlIFNpZ24sIEhvdE1vYmlsZTAeFw0xNjA3MTMxMTM5MzZaFw0yNjA1MjIx
|
||||||
|
MTM5MzZaMH0xCzAJBgNVBAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcM
|
||||||
|
CUplcnVzYWxlbTEQMA4GA1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0ZnJlZS5s
|
||||||
|
aW5rMSAwHgYDVQQDDBdOZXRGcmVlIFNpZ24sIEhvdE1vYmlsZTCCASIwDQYJKoZI
|
||||||
|
hvcNAQEBBQADggEPADCCAQoCggEBAK36bGJixwgMX5twmmteI3j+8JfR5XdOSN6N
|
||||||
|
MLLsQuR7/LUXMbCBB5WNDGoF823rDbiIZwuqoH4JVN3I4BNitl0QzB2wlTLzEkMr
|
||||||
|
Db9sA6owahQwhh+m1yNovM3luSlt7eJS8yWUMNgp8gPxWV1j3RBGASHRKuzU2btg
|
||||||
|
I7WZoD5vNX2VrdrN+TxbRsrRHbMZhmv2Q8v4vNf1bwma64VyT+VDALx0V6HSjSnP
|
||||||
|
XMBvY0qtsqQILt53nTrtbTyat1oJaAcaeF/oSi+ibcRqRD0RQjPokD7ZBEIzx7b4
|
||||||
|
5YD4bsdr9WbSMjaa6DMDC0Zr/1MavLJu5DqO9hMljKfxb5HMcB8CAwEAAaNQME4w
|
||||||
|
HQYDVR0OBBYEFLRpqEWnXat8cUzbZ2r+LdeBMj+mMB8GA1UdIwQYMBaAFLRpqEWn
|
||||||
|
Xat8cUzbZ2r+LdeBMj+mMAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQELBQADggEB
|
||||||
|
ADXTOVrk1BbXQiCbPUX0eWOskyu+Nq4uJONFhrhBiKwG/leMd+fKjtbj5avVh81B
|
||||||
|
1NmHojzlls/kWcI4bjfqkKpv1eXKlrRA334BoLxGj7u4dbzgNfCNhE96lA6qIW+6
|
||||||
|
m6BkpYESXc06RX41RVWzYyOJX6foSv8aqdo1aICy+LvBtXewKQixDbGFNqSmSLB5
|
||||||
|
UHcrwjgOK8aWXvaJe2mJAV91HKhfgSFkFsokrVveaP985ej3s59si4htKbI9Qqx0
|
||||||
|
ZBMJdfklpqI1fDdL4cDNssX6kNus+gnJzP0tQW00DMH6V6OIqYrL/CJRJx4634yT
|
||||||
|
ddo6lzNM9hZhrtlM/czjLn8=
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
cf:f3:86:5f:06:54:0c:d8
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, HotMobile"
|
||||||
|
Validity
|
||||||
|
Not Before: Jul 13 11:39:36 2016 GMT
|
||||||
|
Not After : May 22 11:39:36 2026 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, HotMobile"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:ad:fa:6c:62:62:c7:08:0c:5f:9b:70:9a:6b:5e:
|
||||||
|
23:78:fe:f0:97:d1:e5:77:4e:48:de:8d:30:b2:ec:
|
||||||
|
42:e4:7b:fc:b5:17:31:b0:81:07:95:8d:0c:6a:05:
|
||||||
|
f3:6d:eb:0d:b8:88:67:0b:aa:a0:7e:09:54:dd:c8:
|
||||||
|
e0:13:62:b6:5d:10:cc:1d:b0:95:32:f3:12:43:2b:
|
||||||
|
0d:bf:6c:03:aa:30:6a:14:30:86:1f:a6:d7:23:68:
|
||||||
|
bc:cd:e5:b9:29:6d:ed:e2:52:f3:25:94:30:d8:29:
|
||||||
|
f2:03:f1:59:5d:63:dd:10:46:01:21:d1:2a:ec:d4:
|
||||||
|
d9:bb:60:23:b5:99:a0:3e:6f:35:7d:95:ad:da:cd:
|
||||||
|
f9:3c:5b:46:ca:d1:1d:b3:19:86:6b:f6:43:cb:f8:
|
||||||
|
bc:d7:f5:6f:09:9a:eb:85:72:4f:e5:43:00:bc:74:
|
||||||
|
57:a1:d2:8d:29:cf:5c:c0:6f:63:4a:ad:b2:a4:08:
|
||||||
|
2e:de:77:9d:3a:ed:6d:3c:9a:b7:5a:09:68:07:1a:
|
||||||
|
78:5f:e8:4a:2f:a2:6d:c4:6a:44:3d:11:42:33:e8:
|
||||||
|
90:3e:d9:04:42:33:c7:b6:f8:e5:80:f8:6e:c7:6b:
|
||||||
|
f5:66:d2:32:36:9a:e8:33:03:0b:46:6b:ff:53:1a:
|
||||||
|
bc:b2:6e:e4:3a:8e:f6:13:25:8c:a7:f1:6f:91:cc:
|
||||||
|
70:1f
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
B4:69:A8:45:A7:5D:AB:7C:71:4C:DB:67:6A:FE:2D:D7:81:32:3F:A6
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:B4:69:A8:45:A7:5D:AB:7C:71:4C:DB:67:6A:FE:2D:D7:81:32:3F:A6
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
35:d3:39:5a:e4:d4:16:d7:42:20:9b:3d:45:f4:79:63:ac:93:
|
||||||
|
2b:be:36:ae:2e:24:e3:45:86:b8:41:88:ac:06:fe:57:8c:77:
|
||||||
|
e7:ca:8e:d6:e3:e5:ab:d5:87:cd:41:d4:d9:87:a2:3c:e5:96:
|
||||||
|
cf:e4:59:c2:38:6e:37:ea:90:aa:6f:d5:e5:ca:96:b4:40:df:
|
||||||
|
7e:01:a0:bc:46:8f:bb:b8:75:bc:e0:35:f0:8d:84:4f:7a:94:
|
||||||
|
0e:aa:21:6f:ba:9b:a0:64:a5:81:12:5d:cd:3a:45:7e:35:45:
|
||||||
|
55:b3:63:23:89:5f:a7:e8:4a:ff:1a:a9:da:35:68:80:b2:f8:
|
||||||
|
bb:c1:b5:77:b0:29:08:b1:0d:b1:85:36:a4:a6:48:b0:79:50:
|
||||||
|
77:2b:c2:38:0e:2b:c6:96:5e:f6:89:7b:69:89:01:5f:75:1c:
|
||||||
|
a8:5f:81:21:64:16:ca:24:ad:5b:de:68:ff:7c:e5:e8:f7:b3:
|
||||||
|
9f:6c:8b:88:6d:29:b2:3d:42:ac:74:64:13:09:75:f9:25:a6:
|
||||||
|
a2:35:7c:37:4b:e1:c0:cd:b2:c5:fa:90:db:ac:fa:09:c9:cc:
|
||||||
|
fd:2d:41:6d:34:0c:c1:fa:57:a3:88:a9:8a:cb:fc:22:51:27:
|
||||||
|
1e:3a:df:8c:93:75:da:3a:97:33:4c:f6:16:61:ae:d9:4c:fd:
|
||||||
|
cc:e3:2e:7f
|
||||||
123
MagiskOnWSA/DLL/cacerts/85c0c4be.0
Normal file
123
MagiskOnWSA/DLL/cacerts/85c0c4be.0
Normal file
@ -0,0 +1,123 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIF3TCCA8WgAwIBAgIUGSL6iZ8Kz/CT3Q1kiYoKK75gxfwwDQYJKoZIhvcNAQEL
|
||||||
|
BQAwfjELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAGA1UEBwwJSmVy
|
||||||
|
dXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRmcmVlLmxpbmsx
|
||||||
|
ITAfBgNVBAMMGE5ldEZyZWUgU2lnbiwgSUIgUGFydG5lcjAeFw0yMDA0MjYxNDAz
|
||||||
|
MzlaFw0zMDA0MjQxNDAzMzlaMH4xCzAJBgNVBAYTAklMMQ8wDQYDVQQIDAZpc3Jh
|
||||||
|
ZWwxEjAQBgNVBAcMCUplcnVzYWxlbTEQMA4GA1UECgwHTmV0RnJlZTEVMBMGA1UE
|
||||||
|
CwwMbmV0ZnJlZS5saW5rMSEwHwYDVQQDDBhOZXRGcmVlIFNpZ24sIElCIFBhcnRu
|
||||||
|
ZXIwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCtj4vt55TGvmidDKVj
|
||||||
|
ktTyTHDKIJShq72REaYGfQhweEEBzMRJzprw8spOtL7LsayfyV7On/9NY7X6p79a
|
||||||
|
QFJUM/lGMwj5E5gWWDJt5yEe/LEJTHpeZUXIBu78cJR9pZsUP+iWvqj2TgJ2GwoD
|
||||||
|
WDdSmDWTxY93AP+4BL2421hA/NPjY8xkP+hofupC02WgKIODrC/72FrScQnxnMkD
|
||||||
|
1Hu9Yw4W4kX8FAhWR3YeXRE0gWV93JTWdBOEzM+7DKn9pdpNZdYXBu2UysNTwrsH
|
||||||
|
2c31R86et7o2NRhRup5GDBIgaVAi+RjmnTi7GIj5Js3IhIe9hOW5hoSwhNTZiCT+
|
||||||
|
Ks4zVvdvebA/1XMiQI2HQMQTtLrysYIYjM28YsEWob2JqYQ4eACcmEq2ZZJNMDj4
|
||||||
|
yGSdJVqZBwnwbK6PmmzQc9n7y+hSUHgg/6x7lPGRfG2XsIhrDrK8nuEU4mRSRlGG
|
||||||
|
OEL0dC7GY8ywAI30E5nLPtk6vcToaWAz12rC1waI5xyYKgcP8SdOg70SwQj/2/lO
|
||||||
|
QC5Bzl7581/XKbbLdrsQBXiJ7CN83z046Bs4TqBEqlTzKV257CwLXIW2Kd4nydx+
|
||||||
|
UuGEqeoNDIIxZCapRQ83mKGJmtGraLN73TLAfZJ2xq3xhMlXejR5JB4JGFmAhGBt
|
||||||
|
/Qr3MBAM9Lrn2vD0buihAn5D/QIDAQABo1MwUTAdBgNVHQ4EFgQUxgogJN2fOSCA
|
||||||
|
+Q1tBXEiLQz1clcwHwYDVR0jBBgwFoAUxgogJN2fOSCA+Q1tBXEiLQz1clcwDwYD
|
||||||
|
VR0TAQH/BAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAgEAFslaPHqfvOxKDjLHgbNB
|
||||||
|
Vu+m9/uLfMCMAxo85z8hayEIt7/HEzf03CQji/U3OMJPeah7POKlFkDE9tHxgPmD
|
||||||
|
Xmw7/gKPolJaPHS9hv484Fd7yu47lKuskYxW3FP9b1s7woO5YmCE8hVSWMLHRz1h
|
||||||
|
Sr7Mx8zj9/4nT1TF+ZI85TySCjhq+toQCFVmS/1gv2fqz2UoTJVebdJOwNgyiyjB
|
||||||
|
+y3ekjcXWIVZEsVqNDjM/6C+Uz1LJm+qzAoNOdVc7EIgheUTsNr3te/Zgv0Cg8Eo
|
||||||
|
d4V+EyaQkElbXKqcafZngxjQqyvEVoHocGDTvf+B3DLaqCIldEyWyusGsC1tyoJR
|
||||||
|
vQrkwco1VDWl89o3cPOgalI8M7W1nCougNt7PCNO/RjsdOncJE9UUphLHXO1nIgn
|
||||||
|
mGTVq3ZurDFaIodUNVV4YB+mmJ87ZjIbs8uQUvzEcQnoCmDBg4ABk+e4CJJhzLNP
|
||||||
|
XW+0L8W37ZyHl5Fx2JPWnZuGhZ214ODQJZ1T164G9dfkULHmd3xxc1hGEfvdybHd
|
||||||
|
sDIISA+7z1CJXtZYLJ5noOQG7VbrG0KUvO7U897/miXmF6C1rYwpTVlKhEQ8cChU
|
||||||
|
JnZrCImXL32d8iOzSU4EbLy8Nq89T3fcnWKstGbKpzJdzJ8bJUnveoEEGbo3rP72
|
||||||
|
86H7Aq+q7qWFjZT/vp9J2Is=
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
19:22:fa:89:9f:0a:cf:f0:93:dd:0d:64:89:8a:0a:2b:be:60:c5:fc
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, IB Partner"
|
||||||
|
Validity
|
||||||
|
Not Before: Apr 26 14:03:39 2020 GMT
|
||||||
|
Not After : Apr 24 14:03:39 2030 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, IB Partner"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:ad:8f:8b:ed:e7:94:c6:be:68:9d:0c:a5:63:92:
|
||||||
|
d4:f2:4c:70:ca:20:94:a1:ab:bd:91:11:a6:06:7d:
|
||||||
|
08:70:78:41:01:cc:c4:49:ce:9a:f0:f2:ca:4e:b4:
|
||||||
|
be:cb:b1:ac:9f:c9:5e:ce:9f:ff:4d:63:b5:fa:a7:
|
||||||
|
bf:5a:40:52:54:33:f9:46:33:08:f9:13:98:16:58:
|
||||||
|
32:6d:e7:21:1e:fc:b1:09:4c:7a:5e:65:45:c8:06:
|
||||||
|
ee:fc:70:94:7d:a5:9b:14:3f:e8:96:be:a8:f6:4e:
|
||||||
|
02:76:1b:0a:03:58:37:52:98:35:93:c5:8f:77:00:
|
||||||
|
ff:b8:04:bd:b8:db:58:40:fc:d3:e3:63:cc:64:3f:
|
||||||
|
e8:68:7e:ea:42:d3:65:a0:28:83:83:ac:2f:fb:d8:
|
||||||
|
5a:d2:71:09:f1:9c:c9:03:d4:7b:bd:63:0e:16:e2:
|
||||||
|
45:fc:14:08:56:47:76:1e:5d:11:34:81:65:7d:dc:
|
||||||
|
94:d6:74:13:84:cc:cf:bb:0c:a9:fd:a5:da:4d:65:
|
||||||
|
d6:17:06:ed:94:ca:c3:53:c2:bb:07:d9:cd:f5:47:
|
||||||
|
ce:9e:b7:ba:36:35:18:51:ba:9e:46:0c:12:20:69:
|
||||||
|
50:22:f9:18:e6:9d:38:bb:18:88:f9:26:cd:c8:84:
|
||||||
|
87:bd:84:e5:b9:86:84:b0:84:d4:d9:88:24:fe:2a:
|
||||||
|
ce:33:56:f7:6f:79:b0:3f:d5:73:22:40:8d:87:40:
|
||||||
|
c4:13:b4:ba:f2:b1:82:18:8c:cd:bc:62:c1:16:a1:
|
||||||
|
bd:89:a9:84:38:78:00:9c:98:4a:b6:65:92:4d:30:
|
||||||
|
38:f8:c8:64:9d:25:5a:99:07:09:f0:6c:ae:8f:9a:
|
||||||
|
6c:d0:73:d9:fb:cb:e8:52:50:78:20:ff:ac:7b:94:
|
||||||
|
f1:91:7c:6d:97:b0:88:6b:0e:b2:bc:9e:e1:14:e2:
|
||||||
|
64:52:46:51:86:38:42:f4:74:2e:c6:63:cc:b0:00:
|
||||||
|
8d:f4:13:99:cb:3e:d9:3a:bd:c4:e8:69:60:33:d7:
|
||||||
|
6a:c2:d7:06:88:e7:1c:98:2a:07:0f:f1:27:4e:83:
|
||||||
|
bd:12:c1:08:ff:db:f9:4e:40:2e:41:ce:5e:f9:f3:
|
||||||
|
5f:d7:29:b6:cb:76:bb:10:05:78:89:ec:23:7c:df:
|
||||||
|
3d:38:e8:1b:38:4e:a0:44:aa:54:f3:29:5d:b9:ec:
|
||||||
|
2c:0b:5c:85:b6:29:de:27:c9:dc:7e:52:e1:84:a9:
|
||||||
|
ea:0d:0c:82:31:64:26:a9:45:0f:37:98:a1:89:9a:
|
||||||
|
d1:ab:68:b3:7b:dd:32:c0:7d:92:76:c6:ad:f1:84:
|
||||||
|
c9:57:7a:34:79:24:1e:09:18:59:80:84:60:6d:fd:
|
||||||
|
0a:f7:30:10:0c:f4:ba:e7:da:f0:f4:6e:e8:a1:02:
|
||||||
|
7e:43:fd
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
C6:0A:20:24:DD:9F:39:20:80:F9:0D:6D:05:71:22:2D:0C:F5:72:57
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:C6:0A:20:24:DD:9F:39:20:80:F9:0D:6D:05:71:22:2D:0C:F5:72:57
|
||||||
|
|
||||||
|
X509v3 Basic Constraints: critical
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
16:c9:5a:3c:7a:9f:bc:ec:4a:0e:32:c7:81:b3:41:56:ef:a6:
|
||||||
|
f7:fb:8b:7c:c0:8c:03:1a:3c:e7:3f:21:6b:21:08:b7:bf:c7:
|
||||||
|
13:37:f4:dc:24:23:8b:f5:37:38:c2:4f:79:a8:7b:3c:e2:a5:
|
||||||
|
16:40:c4:f6:d1:f1:80:f9:83:5e:6c:3b:fe:02:8f:a2:52:5a:
|
||||||
|
3c:74:bd:86:fe:3c:e0:57:7b:ca:ee:3b:94:ab:ac:91:8c:56:
|
||||||
|
dc:53:fd:6f:5b:3b:c2:83:b9:62:60:84:f2:15:52:58:c2:c7:
|
||||||
|
47:3d:61:4a:be:cc:c7:cc:e3:f7:fe:27:4f:54:c5:f9:92:3c:
|
||||||
|
e5:3c:92:0a:38:6a:fa:da:10:08:55:66:4b:fd:60:bf:67:ea:
|
||||||
|
cf:65:28:4c:95:5e:6d:d2:4e:c0:d8:32:8b:28:c1:fb:2d:de:
|
||||||
|
92:37:17:58:85:59:12:c5:6a:34:38:cc:ff:a0:be:53:3d:4b:
|
||||||
|
26:6f:aa:cc:0a:0d:39:d5:5c:ec:42:20:85:e5:13:b0:da:f7:
|
||||||
|
b5:ef:d9:82:fd:02:83:c1:28:77:85:7e:13:26:90:90:49:5b:
|
||||||
|
5c:aa:9c:69:f6:67:83:18:d0:ab:2b:c4:56:81:e8:70:60:d3:
|
||||||
|
bd:ff:81:dc:32:da:a8:22:25:74:4c:96:ca:eb:06:b0:2d:6d:
|
||||||
|
ca:82:51:bd:0a:e4:c1:ca:35:54:35:a5:f3:da:37:70:f3:a0:
|
||||||
|
6a:52:3c:33:b5:b5:9c:2a:2e:80:db:7b:3c:23:4e:fd:18:ec:
|
||||||
|
74:e9:dc:24:4f:54:52:98:4b:1d:73:b5:9c:88:27:98:64:d5:
|
||||||
|
ab:76:6e:ac:31:5a:22:87:54:35:55:78:60:1f:a6:98:9f:3b:
|
||||||
|
66:32:1b:b3:cb:90:52:fc:c4:71:09:e8:0a:60:c1:83:80:01:
|
||||||
|
93:e7:b8:08:92:61:cc:b3:4f:5d:6f:b4:2f:c5:b7:ed:9c:87:
|
||||||
|
97:91:71:d8:93:d6:9d:9b:86:85:9d:b5:e0:e0:d0:25:9d:53:
|
||||||
|
d7:ae:06:f5:d7:e4:50:b1:e6:77:7c:71:73:58:46:11:fb:dd:
|
||||||
|
c9:b1:dd:b0:32:08:48:0f:bb:cf:50:89:5e:d6:58:2c:9e:67:
|
||||||
|
a0:e4:06:ed:56:eb:1b:42:94:bc:ee:d4:f3:de:ff:9a:25:e6:
|
||||||
|
17:a0:b5:ad:8c:29:4d:59:4a:84:44:3c:70:28:54:26:76:6b:
|
||||||
|
08:89:97:2f:7d:9d:f2:23:b3:49:4e:04:6c:bc:bc:36:af:3d:
|
||||||
|
4f:77:dc:9d:62:ac:b4:66:ca:a7:32:5d:cc:9f:1b:25:49:ef:
|
||||||
|
7a:81:04:19:ba:37:ac:fe:f6:f3:a1:fb:02:af:aa:ee:a5:85:
|
||||||
|
8d:94:ff:be:9f:49:d8:8b
|
||||||
123
MagiskOnWSA/DLL/cacerts/a4f6f3c0.0
Normal file
123
MagiskOnWSA/DLL/cacerts/a4f6f3c0.0
Normal file
@ -0,0 +1,123 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIFzzCCA7egAwIBAgIUJd8EwuvF4INK2P9FOVcNOxdqsSgwDQYJKoZIhvcNAQEL
|
||||||
|
BQAwdzELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAGA1UEBwwJSmVy
|
||||||
|
dXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRmcmVlLmxpbmsx
|
||||||
|
GjAYBgNVBAMMEU5ldEZyZWUgU2lnbiwgMDE4MB4XDTIxMDUwNDIwNTMxMFoXDTMx
|
||||||
|
MDUwMjIwNTMxMFowdzELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAG
|
||||||
|
A1UEBwwJSmVydXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRm
|
||||||
|
cmVlLmxpbmsxGjAYBgNVBAMMEU5ldEZyZWUgU2lnbiwgMDE4MIICIjANBgkqhkiG
|
||||||
|
9w0BAQEFAAOCAg8AMIICCgKCAgEA1kkqmmuy9XZw0PVC6wwg0BJFs0zWn3IgUYmd
|
||||||
|
8UXeqfT5Uii/PM4as/Wf3EG7ByRE03njCVTFussYEE3lbHEsjzvcCiDxOkG2HoYf
|
||||||
|
G69Bt+jxKPPNFIjom3SB3l6S57UyiSHk5TaS/x7NpjUhVeMde/McBqW7FU/eEYgx
|
||||||
|
PBaqkQNNG0Wqtl6XybwSdsh0vGJ92wzlTwrKhVpAbesu4L9OYVleZtdW7/xtoB1J
|
||||||
|
aMygZmSEV7v6mW7dMzJdRk8zHCssLJJOgGno/5R/i6/ezGeKu31/FtcpGOw6o8Jc
|
||||||
|
yBvAOV4oV/S992Y+Uxll33dYNTg7ABYNtYYd864K51T03HJi/pedNd2ALu0Oqb/I
|
||||||
|
04dYt8ZRVK1I+K1b7LsYzVIM/5YWRS3uCNAfQMsfy/4ECD/IgbXVGI+Z0kHrElgV
|
||||||
|
uYrOglYrAuFrtG1kV4hoPaGsFjzxM/wrdXaJii0EvbLASeX6TDWOP+5xTZhBesTs
|
||||||
|
6/gAR/DzOQpdqEIn5v/+foKgaCtBHdFPbayFoywg/Dq9rjbq+7pOiS9XzywHgOZU
|
||||||
|
Ussq+F0TB0nJ7NkN2Jx5DiAaehOZJpZNWADVheoUehfLGQDA3ffhwi+tdANkgOMc
|
||||||
|
w6igzwbo1PIrZNcoXDpG+3Dpo8J1+X+nXe4HOKh8K5TbdR9xmUAag3sKZZ5wPjyt
|
||||||
|
bAq/II0CAwEAAaNTMFEwHQYDVR0OBBYEFK0REcJzkVprhzsKvxjI9w+vlYTiMB8G
|
||||||
|
A1UdIwQYMBaAFK0REcJzkVprhzsKvxjI9w+vlYTiMA8GA1UdEwEB/wQFMAMBAf8w
|
||||||
|
DQYJKoZIhvcNAQELBQADggIBALe8h93x+yAkpIeVRcOoNpSnpNiDc7/bY2fJxxWy
|
||||||
|
Yo4TaT9J+dhlbdedvzgbm0NUcWCKKA0vmR+/PsKYwdJcko1e3kdKTmWGwEBPDRJC
|
||||||
|
kCGn2ZuXeJokRzyAVKceU7DPHAq7n/C5IJ9ivTMEKYc5SS6WxdxBYePf+tXmPGGi
|
||||||
|
vYrL1hEgZ+oUx1rXRz7Spr8lUFc7PPvjfPLD9uRoO5K6rdkeHiChuY45Sky/A012
|
||||||
|
FRhyKR7liZZPtl6QzuLiIDVNcAoJL3SYeaQMmNt6kupQmMcey1RnOwzq56UGOxMr
|
||||||
|
RSUwgiz56PtQwx6q8R6wqpfJgFipoOzRME6+WgoHPyvIZV9AzNnH4Pv+vfVun8TC
|
||||||
|
AEvbcyjPyJUL89TqJIgpmlyLRmNETurrGWVgOS4/0rJy5q35I4rDMdrbM8S0AJZy
|
||||||
|
rSfwwRZXfmxoxYSkx+W6pyIJoj9dtidp1PsKcDoT7CrapmhOKqJzxKdCX3yNQBd0
|
||||||
|
wWoemiLvBRsCJ1dTZePe470aGmpkL8eLSx68neujrbK9lvDC/GIm97Wx103izZw0
|
||||||
|
TkkSyB/JtXcqERWYVfAnmhaxIPS1Gwvk+ytBs9kYbNx1cHvPR+JUbax8jmmamKHN
|
||||||
|
k20mVi+ExBJcyBCs+1gCkKXSlMUpvOSc+tG+nS390JD5pyui1dPp1dlogIX95ad0
|
||||||
|
H5kG
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
25:df:04:c2:eb:c5:e0:83:4a:d8:ff:45:39:57:0d:3b:17:6a:b1:28
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, 018"
|
||||||
|
Validity
|
||||||
|
Not Before: May 4 20:53:10 2021 GMT
|
||||||
|
Not After : May 2 20:53:10 2031 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, 018"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:d6:49:2a:9a:6b:b2:f5:76:70:d0:f5:42:eb:0c:
|
||||||
|
20:d0:12:45:b3:4c:d6:9f:72:20:51:89:9d:f1:45:
|
||||||
|
de:a9:f4:f9:52:28:bf:3c:ce:1a:b3:f5:9f:dc:41:
|
||||||
|
bb:07:24:44:d3:79:e3:09:54:c5:ba:cb:18:10:4d:
|
||||||
|
e5:6c:71:2c:8f:3b:dc:0a:20:f1:3a:41:b6:1e:86:
|
||||||
|
1f:1b:af:41:b7:e8:f1:28:f3:cd:14:88:e8:9b:74:
|
||||||
|
81:de:5e:92:e7:b5:32:89:21:e4:e5:36:92:ff:1e:
|
||||||
|
cd:a6:35:21:55:e3:1d:7b:f3:1c:06:a5:bb:15:4f:
|
||||||
|
de:11:88:31:3c:16:aa:91:03:4d:1b:45:aa:b6:5e:
|
||||||
|
97:c9:bc:12:76:c8:74:bc:62:7d:db:0c:e5:4f:0a:
|
||||||
|
ca:85:5a:40:6d:eb:2e:e0:bf:4e:61:59:5e:66:d7:
|
||||||
|
56:ef:fc:6d:a0:1d:49:68:cc:a0:66:64:84:57:bb:
|
||||||
|
fa:99:6e:dd:33:32:5d:46:4f:33:1c:2b:2c:2c:92:
|
||||||
|
4e:80:69:e8:ff:94:7f:8b:af:de:cc:67:8a:bb:7d:
|
||||||
|
7f:16:d7:29:18:ec:3a:a3:c2:5c:c8:1b:c0:39:5e:
|
||||||
|
28:57:f4:bd:f7:66:3e:53:19:65:df:77:58:35:38:
|
||||||
|
3b:00:16:0d:b5:86:1d:f3:ae:0a:e7:54:f4:dc:72:
|
||||||
|
62:fe:97:9d:35:dd:80:2e:ed:0e:a9:bf:c8:d3:87:
|
||||||
|
58:b7:c6:51:54:ad:48:f8:ad:5b:ec:bb:18:cd:52:
|
||||||
|
0c:ff:96:16:45:2d:ee:08:d0:1f:40:cb:1f:cb:fe:
|
||||||
|
04:08:3f:c8:81:b5:d5:18:8f:99:d2:41:eb:12:58:
|
||||||
|
15:b9:8a:ce:82:56:2b:02:e1:6b:b4:6d:64:57:88:
|
||||||
|
68:3d:a1:ac:16:3c:f1:33:fc:2b:75:76:89:8a:2d:
|
||||||
|
04:bd:b2:c0:49:e5:fa:4c:35:8e:3f:ee:71:4d:98:
|
||||||
|
41:7a:c4:ec:eb:f8:00:47:f0:f3:39:0a:5d:a8:42:
|
||||||
|
27:e6:ff:fe:7e:82:a0:68:2b:41:1d:d1:4f:6d:ac:
|
||||||
|
85:a3:2c:20:fc:3a:bd:ae:36:ea:fb:ba:4e:89:2f:
|
||||||
|
57:cf:2c:07:80:e6:54:52:cb:2a:f8:5d:13:07:49:
|
||||||
|
c9:ec:d9:0d:d8:9c:79:0e:20:1a:7a:13:99:26:96:
|
||||||
|
4d:58:00:d5:85:ea:14:7a:17:cb:19:00:c0:dd:f7:
|
||||||
|
e1:c2:2f:ad:74:03:64:80:e3:1c:c3:a8:a0:cf:06:
|
||||||
|
e8:d4:f2:2b:64:d7:28:5c:3a:46:fb:70:e9:a3:c2:
|
||||||
|
75:f9:7f:a7:5d:ee:07:38:a8:7c:2b:94:db:75:1f:
|
||||||
|
71:99:40:1a:83:7b:0a:65:9e:70:3e:3c:ad:6c:0a:
|
||||||
|
bf:20:8d
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
AD:11:11:C2:73:91:5A:6B:87:3B:0A:BF:18:C8:F7:0F:AF:95:84:E2
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:AD:11:11:C2:73:91:5A:6B:87:3B:0A:BF:18:C8:F7:0F:AF:95:84:E2
|
||||||
|
|
||||||
|
X509v3 Basic Constraints: critical
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
b7:bc:87:dd:f1:fb:20:24:a4:87:95:45:c3:a8:36:94:a7:a4:
|
||||||
|
d8:83:73:bf:db:63:67:c9:c7:15:b2:62:8e:13:69:3f:49:f9:
|
||||||
|
d8:65:6d:d7:9d:bf:38:1b:9b:43:54:71:60:8a:28:0d:2f:99:
|
||||||
|
1f:bf:3e:c2:98:c1:d2:5c:92:8d:5e:de:47:4a:4e:65:86:c0:
|
||||||
|
40:4f:0d:12:42:90:21:a7:d9:9b:97:78:9a:24:47:3c:80:54:
|
||||||
|
a7:1e:53:b0:cf:1c:0a:bb:9f:f0:b9:20:9f:62:bd:33:04:29:
|
||||||
|
87:39:49:2e:96:c5:dc:41:61:e3:df:fa:d5:e6:3c:61:a2:bd:
|
||||||
|
8a:cb:d6:11:20:67:ea:14:c7:5a:d7:47:3e:d2:a6:bf:25:50:
|
||||||
|
57:3b:3c:fb:e3:7c:f2:c3:f6:e4:68:3b:92:ba:ad:d9:1e:1e:
|
||||||
|
20:a1:b9:8e:39:4a:4c:bf:03:4d:76:15:18:72:29:1e:e5:89:
|
||||||
|
96:4f:b6:5e:90:ce:e2:e2:20:35:4d:70:0a:09:2f:74:98:79:
|
||||||
|
a4:0c:98:db:7a:92:ea:50:98:c7:1e:cb:54:67:3b:0c:ea:e7:
|
||||||
|
a5:06:3b:13:2b:45:25:30:82:2c:f9:e8:fb:50:c3:1e:aa:f1:
|
||||||
|
1e:b0:aa:97:c9:80:58:a9:a0:ec:d1:30:4e:be:5a:0a:07:3f:
|
||||||
|
2b:c8:65:5f:40:cc:d9:c7:e0:fb:fe:bd:f5:6e:9f:c4:c2:00:
|
||||||
|
4b:db:73:28:cf:c8:95:0b:f3:d4:ea:24:88:29:9a:5c:8b:46:
|
||||||
|
63:44:4e:ea:eb:19:65:60:39:2e:3f:d2:b2:72:e6:ad:f9:23:
|
||||||
|
8a:c3:31:da:db:33:c4:b4:00:96:72:ad:27:f0:c1:16:57:7e:
|
||||||
|
6c:68:c5:84:a4:c7:e5:ba:a7:22:09:a2:3f:5d:b6:27:69:d4:
|
||||||
|
fb:0a:70:3a:13:ec:2a:da:a6:68:4e:2a:a2:73:c4:a7:42:5f:
|
||||||
|
7c:8d:40:17:74:c1:6a:1e:9a:22:ef:05:1b:02:27:57:53:65:
|
||||||
|
e3:de:e3:bd:1a:1a:6a:64:2f:c7:8b:4b:1e:bc:9d:eb:a3:ad:
|
||||||
|
b2:bd:96:f0:c2:fc:62:26:f7:b5:b1:d7:4d:e2:cd:9c:34:4e:
|
||||||
|
49:12:c8:1f:c9:b5:77:2a:11:15:98:55:f0:27:9a:16:b1:20:
|
||||||
|
f4:b5:1b:0b:e4:fb:2b:41:b3:d9:18:6c:dc:75:70:7b:cf:47:
|
||||||
|
e2:54:6d:ac:7c:8e:69:9a:98:a1:cd:93:6d:26:56:2f:84:c4:
|
||||||
|
12:5c:c8:10:ac:fb:58:02:90:a5:d2:94:c5:29:bc:e4:9c:fa:
|
||||||
|
d1:be:9d:2d:fd:d0:90:f9:a7:2b:a2:d5:d3:e9:d5:d9:68:80:
|
||||||
|
85:fd:e5:a7:74:1f:99:06
|
||||||
BIN
MagiskOnWSA/DLL/cacerts/b0396035.0
Normal file
BIN
MagiskOnWSA/DLL/cacerts/b0396035.0
Normal file
Binary file not shown.
81
MagiskOnWSA/DLL/cacerts/ea335731.0
Normal file
81
MagiskOnWSA/DLL/cacerts/ea335731.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIDzzCCAregAwIBAgIJANJjV3HuLlVqMA0GCSqGSIb3DQEBCwUAMH4xCzAJBgNV
|
||||||
|
BAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcMCWplcnVzYWxlbTEQMA4G
|
||||||
|
A1UECgwHTmV0RnJlZTEZMBcGA1UECwwQbmV0ZnJlZS42MTNtLm9yZzEdMBsGA1UE
|
||||||
|
AwwUTmV0RnJlZSBTaWduICxSTCBJU1AwHhcNMTQxMTE1MjMxNjU0WhcNMjQwOTIz
|
||||||
|
MjMxNjU0WjB+MQswCQYDVQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIwEAYDVQQH
|
||||||
|
DAlqZXJ1c2FsZW0xEDAOBgNVBAoMB05ldEZyZWUxGTAXBgNVBAsMEG5ldGZyZWUu
|
||||||
|
NjEzbS5vcmcxHTAbBgNVBAMMFE5ldEZyZWUgU2lnbiAsUkwgSVNQMIIBIjANBgkq
|
||||||
|
hkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA2gEv5S0YJFYrWSNJJNhtBRN9IfyFhh/l
|
||||||
|
NCo2K8DKkq3CFCthHADZu1v9gRAa9NxC7wrsmK/wBTwoVwcHKrxrmxt/vs6bwZZ7
|
||||||
|
9/TwKDA9Ar3SY6bvsDvij0/53frRoAhUJwdFkwlkIN0DNJWv8n3xAoIRBI3pOxcE
|
||||||
|
890Q2RDw+ydc4OIgETIel3vDqe7aTXTjb7BJjqIYTf9Wad3gmTGpRToNhC0kyQuk
|
||||||
|
MN2XxYHhK/+jjoL/O9vcd3ZLaYlYbQbT/Ud63CfIyvB+ASkqnRGFBIQttkzVrPHP
|
||||||
|
fRkhM+C6BlRfv0njt9Hl5jJjreWXSryd5iSwVVU6VtHo6TZFtUwA/wIDAQABo1Aw
|
||||||
|
TjAdBgNVHQ4EFgQUG9R/R+XGIIaXGs74B2+JNqoka7kwHwYDVR0jBBgwFoAUG9R/
|
||||||
|
R+XGIIaXGs74B2+JNqoka7kwDAYDVR0TBAUwAwEB/zANBgkqhkiG9w0BAQsFAAOC
|
||||||
|
AQEAQh9Id5A0LvTu4yCqM8rrP1mpEBKv4XjMWihR9gZ6fBY8NkyWBfyQkylc6Jlm
|
||||||
|
vrtFH4etuQkElN7tL1ZAyXAmOVnXB19asft/swA+UGEpdqmdIJiz+Q9KSP4c64Xw
|
||||||
|
L9svsOqBouiBYPWpURO0AJVk42lmXVGopGcet8hzMmmBejlCbDWi7mu+RJEMIMkp
|
||||||
|
g6cITc6m/Hrawt3oRxfyERKdoXUpTtTV5Cu4oHLwgcdMbp7IvHJO1SS5fP8OhObN
|
||||||
|
9aVsHN+TzDsXZqkvYn/Tn4fO4YtUdokCSzc39caq9ZiwqUpD0dSOYDotlIIXmzxE
|
||||||
|
OmymXu+SCGzKmR72vZouU0NuTw==
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
d2:63:57:71:ee:2e:55:6a
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = jerusalem, O = NetFree, OU = netfree.613m.org, CN = "NetFree Sign ,RL ISP"
|
||||||
|
Validity
|
||||||
|
Not Before: Nov 15 23:16:54 2014 GMT
|
||||||
|
Not After : Sep 23 23:16:54 2024 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = jerusalem, O = NetFree, OU = netfree.613m.org, CN = "NetFree Sign ,RL ISP"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:da:01:2f:e5:2d:18:24:56:2b:59:23:49:24:d8:
|
||||||
|
6d:05:13:7d:21:fc:85:86:1f:e5:34:2a:36:2b:c0:
|
||||||
|
ca:92:ad:c2:14:2b:61:1c:00:d9:bb:5b:fd:81:10:
|
||||||
|
1a:f4:dc:42:ef:0a:ec:98:af:f0:05:3c:28:57:07:
|
||||||
|
07:2a:bc:6b:9b:1b:7f:be:ce:9b:c1:96:7b:f7:f4:
|
||||||
|
f0:28:30:3d:02:bd:d2:63:a6:ef:b0:3b:e2:8f:4f:
|
||||||
|
f9:dd:fa:d1:a0:08:54:27:07:45:93:09:64:20:dd:
|
||||||
|
03:34:95:af:f2:7d:f1:02:82:11:04:8d:e9:3b:17:
|
||||||
|
04:f3:dd:10:d9:10:f0:fb:27:5c:e0:e2:20:11:32:
|
||||||
|
1e:97:7b:c3:a9:ee:da:4d:74:e3:6f:b0:49:8e:a2:
|
||||||
|
18:4d:ff:56:69:dd:e0:99:31:a9:45:3a:0d:84:2d:
|
||||||
|
24:c9:0b:a4:30:dd:97:c5:81:e1:2b:ff:a3:8e:82:
|
||||||
|
ff:3b:db:dc:77:76:4b:69:89:58:6d:06:d3:fd:47:
|
||||||
|
7a:dc:27:c8:ca:f0:7e:01:29:2a:9d:11:85:04:84:
|
||||||
|
2d:b6:4c:d5:ac:f1:cf:7d:19:21:33:e0:ba:06:54:
|
||||||
|
5f:bf:49:e3:b7:d1:e5:e6:32:63:ad:e5:97:4a:bc:
|
||||||
|
9d:e6:24:b0:55:55:3a:56:d1:e8:e9:36:45:b5:4c:
|
||||||
|
00:ff
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
1B:D4:7F:47:E5:C6:20:86:97:1A:CE:F8:07:6F:89:36:AA:24:6B:B9
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:1B:D4:7F:47:E5:C6:20:86:97:1A:CE:F8:07:6F:89:36:AA:24:6B:B9
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
42:1f:48:77:90:34:2e:f4:ee:e3:20:aa:33:ca:eb:3f:59:a9:
|
||||||
|
10:12:af:e1:78:cc:5a:28:51:f6:06:7a:7c:16:3c:36:4c:96:
|
||||||
|
05:fc:90:93:29:5c:e8:99:66:be:bb:45:1f:87:ad:b9:09:04:
|
||||||
|
94:de:ed:2f:56:40:c9:70:26:39:59:d7:07:5f:5a:b1:fb:7f:
|
||||||
|
b3:00:3e:50:61:29:76:a9:9d:20:98:b3:f9:0f:4a:48:fe:1c:
|
||||||
|
eb:85:f0:2f:db:2f:b0:ea:81:a2:e8:81:60:f5:a9:51:13:b4:
|
||||||
|
00:95:64:e3:69:66:5d:51:a8:a4:67:1e:b7:c8:73:32:69:81:
|
||||||
|
7a:39:42:6c:35:a2:ee:6b:be:44:91:0c:20:c9:29:83:a7:08:
|
||||||
|
4d:ce:a6:fc:7a:da:c2:dd:e8:47:17:f2:11:12:9d:a1:75:29:
|
||||||
|
4e:d4:d5:e4:2b:b8:a0:72:f0:81:c7:4c:6e:9e:c8:bc:72:4e:
|
||||||
|
d5:24:b9:7c:ff:0e:84:e6:cd:f5:a5:6c:1c:df:93:cc:3b:17:
|
||||||
|
66:a9:2f:62:7f:d3:9f:87:ce:e1:8b:54:76:89:02:4b:37:37:
|
||||||
|
f5:c6:aa:f5:98:b0:a9:4a:43:d1:d4:8e:60:3a:2d:94:82:17:
|
||||||
|
9b:3c:44:3a:6c:a6:5e:ef:92:08:6c:ca:99:1e:f6:bd:9a:2e:
|
||||||
|
53:43:6e:4f
|
||||||
81
MagiskOnWSA/DLL/cacerts/f9b4d31c.0
Normal file
81
MagiskOnWSA/DLL/cacerts/f9b4d31c.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIID3TCCAsWgAwIBAgIJALT9ZoUCwnlMMA0GCSqGSIb3DQEBCwUAMIGEMQswCQYD
|
||||||
|
VQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIwEAYDVQQHDAlKZXJ1c2FsZW0xEDAO
|
||||||
|
BgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5ldGZyZWUubGluazEnMCUGA1UEAwwe
|
||||||
|
TmV0RnJlZSBTaWduICwgTmV0RnJlZUFueXdoZXJlMB4XDTE2MDQwNTE1MTc0MVoX
|
||||||
|
DTI2MDIxMjE1MTc0MVowgYQxCzAJBgNVBAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwx
|
||||||
|
EjAQBgNVBAcMCUplcnVzYWxlbTEQMA4GA1UECgwHTmV0RnJlZTEVMBMGA1UECwwM
|
||||||
|
bmV0ZnJlZS5saW5rMScwJQYDVQQDDB5OZXRGcmVlIFNpZ24gLCBOZXRGcmVlQW55
|
||||||
|
d2hlcmUwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC19KPegpnTrYAJ
|
||||||
|
m3ZWQ/vEL3rAXBE89jFcDU7xYmRgeEI+CKD+U5exLTmD7w0pQVM45HghlufWL0uy
|
||||||
|
pPYBR0YL6PbvFzskTnlaQuZBbwBsqf7hrAh7gA3nWintID50L8xtHKiRiLfK+NnM
|
||||||
|
//iQ03uwkwLT2xaUMvw7IbZcrHlwTfN6fxvvfhnCIE/Tnjz2p3aQI6ZmrD6rwZLm
|
||||||
|
oX2TGXQGCteOpM0gpn3gi/q30qzMsgCQ6YfeATzjGFe2rMM6Gy66HjNEzO5w6i7W
|
||||||
|
mG57upSNCTIgKjjwtGlZMg53jVqlfuMuZbZO7OwyatpcuV3KgtER5H8HuQboaZ4v
|
||||||
|
IYAA+0IZAgMBAAGjUDBOMB0GA1UdDgQWBBQR8hgc1nsIVVnUyF3uhivwht7AzDAf
|
||||||
|
BgNVHSMEGDAWgBQR8hgc1nsIVVnUyF3uhivwht7AzDAMBgNVHRMEBTADAQH/MA0G
|
||||||
|
CSqGSIb3DQEBCwUAA4IBAQCOBLgAhZGzGCKvXLbITDrZIC4Oh4sBD4geGnlcO8Rt
|
||||||
|
10JLn9lgW0SnYfMoX2ZOayiwlEltF7PB2dYiGk9+7vDjzpChp5HBDLSTJpCdJ5lc
|
||||||
|
AWEyTjGw9z7cfUUnGJtCaNDPvaLjcvi4KELyAyn3HejwPMcG+F1wyCjwWKoo0MX7
|
||||||
|
ac+/qnp50nUcPYGnPS2hKoMp8tVkC56q9h7KU9AfY001b11lnVfeJynDuMKWivgw
|
||||||
|
6KOH0YSvWt8/d6DM6MtxMyAxdS5sP7htj8pdBTMcHHfw44663xdsd+9nvlaSXDNR
|
||||||
|
aq71pK24e7eEg0zZQEJ8L6finDIQAx8jt6kse1uVZW50
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
b4:fd:66:85:02:c2:79:4c
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , NetFreeAnywhere"
|
||||||
|
Validity
|
||||||
|
Not Before: Apr 5 15:17:41 2016 GMT
|
||||||
|
Not After : Feb 12 15:17:41 2026 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , NetFreeAnywhere"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:b5:f4:a3:de:82:99:d3:ad:80:09:9b:76:56:43:
|
||||||
|
fb:c4:2f:7a:c0:5c:11:3c:f6:31:5c:0d:4e:f1:62:
|
||||||
|
64:60:78:42:3e:08:a0:fe:53:97:b1:2d:39:83:ef:
|
||||||
|
0d:29:41:53:38:e4:78:21:96:e7:d6:2f:4b:b2:a4:
|
||||||
|
f6:01:47:46:0b:e8:f6:ef:17:3b:24:4e:79:5a:42:
|
||||||
|
e6:41:6f:00:6c:a9:fe:e1:ac:08:7b:80:0d:e7:5a:
|
||||||
|
29:ed:20:3e:74:2f:cc:6d:1c:a8:91:88:b7:ca:f8:
|
||||||
|
d9:cc:ff:f8:90:d3:7b:b0:93:02:d3:db:16:94:32:
|
||||||
|
fc:3b:21:b6:5c:ac:79:70:4d:f3:7a:7f:1b:ef:7e:
|
||||||
|
19:c2:20:4f:d3:9e:3c:f6:a7:76:90:23:a6:66:ac:
|
||||||
|
3e:ab:c1:92:e6:a1:7d:93:19:74:06:0a:d7:8e:a4:
|
||||||
|
cd:20:a6:7d:e0:8b:fa:b7:d2:ac:cc:b2:00:90:e9:
|
||||||
|
87:de:01:3c:e3:18:57:b6:ac:c3:3a:1b:2e:ba:1e:
|
||||||
|
33:44:cc:ee:70:ea:2e:d6:98:6e:7b:ba:94:8d:09:
|
||||||
|
32:20:2a:38:f0:b4:69:59:32:0e:77:8d:5a:a5:7e:
|
||||||
|
e3:2e:65:b6:4e:ec:ec:32:6a:da:5c:b9:5d:ca:82:
|
||||||
|
d1:11:e4:7f:07:b9:06:e8:69:9e:2f:21:80:00:fb:
|
||||||
|
42:19
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
11:F2:18:1C:D6:7B:08:55:59:D4:C8:5D:EE:86:2B:F0:86:DE:C0:CC
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:11:F2:18:1C:D6:7B:08:55:59:D4:C8:5D:EE:86:2B:F0:86:DE:C0:CC
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
8e:04:b8:00:85:91:b3:18:22:af:5c:b6:c8:4c:3a:d9:20:2e:
|
||||||
|
0e:87:8b:01:0f:88:1e:1a:79:5c:3b:c4:6d:d7:42:4b:9f:d9:
|
||||||
|
60:5b:44:a7:61:f3:28:5f:66:4e:6b:28:b0:94:49:6d:17:b3:
|
||||||
|
c1:d9:d6:22:1a:4f:7e:ee:f0:e3:ce:90:a1:a7:91:c1:0c:b4:
|
||||||
|
93:26:90:9d:27:99:5c:01:61:32:4e:31:b0:f7:3e:dc:7d:45:
|
||||||
|
27:18:9b:42:68:d0:cf:bd:a2:e3:72:f8:b8:28:42:f2:03:29:
|
||||||
|
f7:1d:e8:f0:3c:c7:06:f8:5d:70:c8:28:f0:58:aa:28:d0:c5:
|
||||||
|
fb:69:cf:bf:aa:7a:79:d2:75:1c:3d:81:a7:3d:2d:a1:2a:83:
|
||||||
|
29:f2:d5:64:0b:9e:aa:f6:1e:ca:53:d0:1f:63:4d:35:6f:5d:
|
||||||
|
65:9d:57:de:27:29:c3:b8:c2:96:8a:f8:30:e8:a3:87:d1:84:
|
||||||
|
af:5a:df:3f:77:a0:cc:e8:cb:71:33:20:31:75:2e:6c:3f:b8:
|
||||||
|
6d:8f:ca:5d:05:33:1c:1c:77:f0:e3:8e:ba:df:17:6c:77:ef:
|
||||||
|
67:be:56:92:5c:33:51:6a:ae:f5:a4:ad:b8:7b:b7:84:83:4c:
|
||||||
|
d9:40:42:7c:2f:a7:e2:9c:32:10:03:1f:23:b7:a9:2c:7b:5b:
|
||||||
|
95:65:6e:74
|
||||||
81
MagiskOnWSA/DLL/cacerts/fbb5e364.0
Normal file
81
MagiskOnWSA/DLL/cacerts/fbb5e364.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIDxzCCAq+gAwIBAgIJAI2ViHiNxvW8MA0GCSqGSIb3DQEBCwUAMHoxCzAJBgNV
|
||||||
|
BAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcMCUplcnVzYWxlbTEQMA4G
|
||||||
|
A1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0ZnJlZS5saW5rMR0wGwYDVQQDDBRO
|
||||||
|
ZXRGcmVlIFNpZ24gLCB4Mm9uZTAeFw0xNjAzMTMxNjM1MjFaFw0yNjAxMjAxNjM1
|
||||||
|
MjFaMHoxCzAJBgNVBAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcMCUpl
|
||||||
|
cnVzYWxlbTEQMA4GA1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0ZnJlZS5saW5r
|
||||||
|
MR0wGwYDVQQDDBROZXRGcmVlIFNpZ24gLCB4Mm9uZTCCASIwDQYJKoZIhvcNAQEB
|
||||||
|
BQADggEPADCCAQoCggEBALCFuiEa8k1KjSdvAUUXywlvxFUKP4hD2BrY0dvWK0xe
|
||||||
|
WnKO7jHpDK88Dv3+2aa15c09ULKLqw6NDg3zPo1Tzb6hJs2nuI5dXbmoKA8QRQr1
|
||||||
|
ny6JNi4LxAle6LTNqcAw+jsONmyx62vDXpRAHTNsguBdqbKZZp/8jLm9aNg0uvbn
|
||||||
|
g/E6gvUrwCylidcL3fQ3GiZsjj2RgzUITtLG2gCtHdAv87c5OJOw1tONv4Yfayxk
|
||||||
|
uG1n+4Z3eKzsDIbO7wbnWypcI/lod9xGub0st3YWjdxp10N2x5EYLgfwThG03RBk
|
||||||
|
vdWY1kfrzaL1e1jn0x5yqbdOEwzgZeQQZDmNNpybhlECAwEAAaNQME4wHQYDVR0O
|
||||||
|
BBYEFCimmwvFnAJ3VrIam6IzW70HpeNHMB8GA1UdIwQYMBaAFCimmwvFnAJ3VrIa
|
||||||
|
m6IzW70HpeNHMAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQELBQADggEBAKhoWpR6
|
||||||
|
G4atxcAdzQhA3e9LcyRNBdLvtNeZSSPHBPuxRqXDxRT6QhwdYR/mK9WjcOxdA6mj
|
||||||
|
m/wwLvOy3sbDFQySUs0Yu+aWn9GsFBBgdJoTwSgnwjY60wQ+/yyWCXIFabVHz7Nw
|
||||||
|
wepexJVQfz2yfnwfGHo3FCI4526NMwxEzy1Xt17wY4fxFmEusVEKqYKnYsHg2s8K
|
||||||
|
/4GKabaBpcv7iy3vIsks7mGe5NrgNS4MLACC8+5d3XVoqJeXsbX8usaRFDZrseE4
|
||||||
|
O3d27X+0kjPAKx8Ztn70VWDbS7Cuic6kKrBXjjEN5OTD60GJ1CCiZp6miyjkTHBq
|
||||||
|
mRkn51xTIRBX6S0=
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
8d:95:88:78:8d:c6:f5:bc
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , x2one"
|
||||||
|
Validity
|
||||||
|
Not Before: Mar 13 16:35:21 2016 GMT
|
||||||
|
Not After : Jan 20 16:35:21 2026 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , x2one"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:b0:85:ba:21:1a:f2:4d:4a:8d:27:6f:01:45:17:
|
||||||
|
cb:09:6f:c4:55:0a:3f:88:43:d8:1a:d8:d1:db:d6:
|
||||||
|
2b:4c:5e:5a:72:8e:ee:31:e9:0c:af:3c:0e:fd:fe:
|
||||||
|
d9:a6:b5:e5:cd:3d:50:b2:8b:ab:0e:8d:0e:0d:f3:
|
||||||
|
3e:8d:53:cd:be:a1:26:cd:a7:b8:8e:5d:5d:b9:a8:
|
||||||
|
28:0f:10:45:0a:f5:9f:2e:89:36:2e:0b:c4:09:5e:
|
||||||
|
e8:b4:cd:a9:c0:30:fa:3b:0e:36:6c:b1:eb:6b:c3:
|
||||||
|
5e:94:40:1d:33:6c:82:e0:5d:a9:b2:99:66:9f:fc:
|
||||||
|
8c:b9:bd:68:d8:34:ba:f6:e7:83:f1:3a:82:f5:2b:
|
||||||
|
c0:2c:a5:89:d7:0b:dd:f4:37:1a:26:6c:8e:3d:91:
|
||||||
|
83:35:08:4e:d2:c6:da:00:ad:1d:d0:2f:f3:b7:39:
|
||||||
|
38:93:b0:d6:d3:8d:bf:86:1f:6b:2c:64:b8:6d:67:
|
||||||
|
fb:86:77:78:ac:ec:0c:86:ce:ef:06:e7:5b:2a:5c:
|
||||||
|
23:f9:68:77:dc:46:b9:bd:2c:b7:76:16:8d:dc:69:
|
||||||
|
d7:43:76:c7:91:18:2e:07:f0:4e:11:b4:dd:10:64:
|
||||||
|
bd:d5:98:d6:47:eb:cd:a2:f5:7b:58:e7:d3:1e:72:
|
||||||
|
a9:b7:4e:13:0c:e0:65:e4:10:64:39:8d:36:9c:9b:
|
||||||
|
86:51
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
28:A6:9B:0B:C5:9C:02:77:56:B2:1A:9B:A2:33:5B:BD:07:A5:E3:47
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:28:A6:9B:0B:C5:9C:02:77:56:B2:1A:9B:A2:33:5B:BD:07:A5:E3:47
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
a8:68:5a:94:7a:1b:86:ad:c5:c0:1d:cd:08:40:dd:ef:4b:73:
|
||||||
|
24:4d:05:d2:ef:b4:d7:99:49:23:c7:04:fb:b1:46:a5:c3:c5:
|
||||||
|
14:fa:42:1c:1d:61:1f:e6:2b:d5:a3:70:ec:5d:03:a9:a3:9b:
|
||||||
|
fc:30:2e:f3:b2:de:c6:c3:15:0c:92:52:cd:18:bb:e6:96:9f:
|
||||||
|
d1:ac:14:10:60:74:9a:13:c1:28:27:c2:36:3a:d3:04:3e:ff:
|
||||||
|
2c:96:09:72:05:69:b5:47:cf:b3:70:c1:ea:5e:c4:95:50:7f:
|
||||||
|
3d:b2:7e:7c:1f:18:7a:37:14:22:38:e7:6e:8d:33:0c:44:cf:
|
||||||
|
2d:57:b7:5e:f0:63:87:f1:16:61:2e:b1:51:0a:a9:82:a7:62:
|
||||||
|
c1:e0:da:cf:0a:ff:81:8a:69:b6:81:a5:cb:fb:8b:2d:ef:22:
|
||||||
|
c9:2c:ee:61:9e:e4:da:e0:35:2e:0c:2c:00:82:f3:ee:5d:dd:
|
||||||
|
75:68:a8:97:97:b1:b5:fc:ba:c6:91:14:36:6b:b1:e1:38:3b:
|
||||||
|
77:76:ed:7f:b4:92:33:c0:2b:1f:19:b6:7e:f4:55:60:db:4b:
|
||||||
|
b0:ae:89:ce:a4:2a:b0:57:8e:31:0d:e4:e4:c3:eb:41:89:d4:
|
||||||
|
20:a2:66:9e:a6:8b:28:e4:4c:70:6a:99:19:27:e7:5c:53:21:
|
||||||
|
10:57:e9:2d
|
||||||
38
MagiskOnWSA/DLL/docs/Fixes/Fix Error 0x80073CF0.md
Normal file
38
MagiskOnWSA/DLL/docs/Fixes/Fix Error 0x80073CF0.md
Normal file
@ -0,0 +1,38 @@
|
|||||||
|
## Issue: </br> Error 0x80073CF0 when "Run.bat" is executed to install Windows Subystem for Android (WSA)
|
||||||
|
### Preface:
|
||||||
|
##### This issue can arise due to many factors such as corruption of files when downloading the .zip/.7z files or extracting from the .zip/.7z files. This can be also caused if the folder name is too long (This is the case as MagiskOnWSA tends to generate a long string for the .zip/.7z file and the folder within the archive.)
|
||||||
|
|
||||||
|
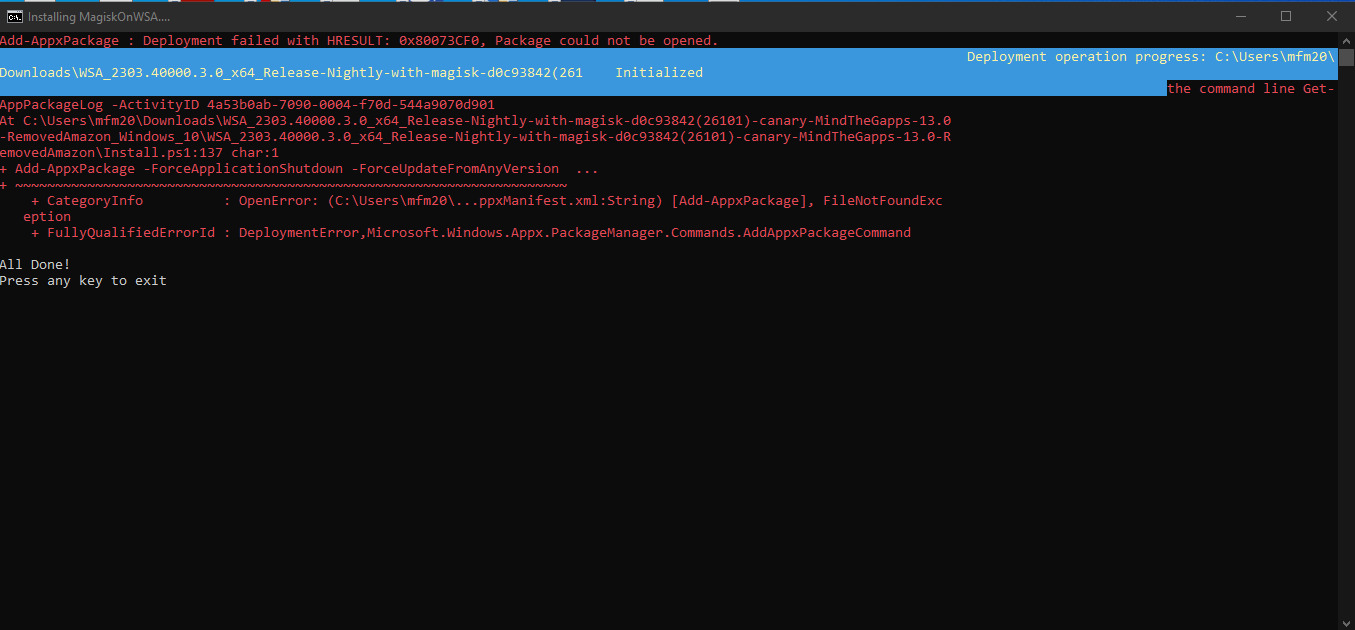
|
||||||
|
|
||||||
|
|
||||||
|
---
|
||||||
|
## Solution
|
||||||
|
|
||||||
|
**1. Ensure the partition/drive you are installing from is NTFS**
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
**2. Redownload WSA Build .zip/.7z file from the [Releases page](https://github.com/MustardChef/WSABuilds/releases) (sometime the files can be corrupted during download and extraction)**
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
**3. Rename the .zip/.7z file to a shorter name, which can be anything to your choosing </br> (For example: WSA_2XXX.XXXXX.X.X_XXXX_Release-Nightly-with-magisk-XXXXXXX-XXXXXX-MindTheGapps-XX.X-RemovedAmazon ----> WSAArchive2XXX)**
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
**4. Extract the .zip or .7z archive (depends on the release) using 7-zip or a proper archive tool and not the built in Windows archive extractor**
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
**5. Rename the extracted folder(s) to a shorter name, which can be anything to your choosing**
|
||||||
|
|
||||||
|
#### For example:
|
||||||
|
- **Before:** WSA_2XXX.XXXXX.X.X_XXXX_Release-Nightly-with-magisk-XXXXXXX-XXXXXX-MindTheGapps-XX.X-RemovedAmazon
|
||||||
|
- **After:** WSAExtracted2XXX
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
**6. Ensure that 'Run.bat' is run as Administrator**
|
||||||
|
|
||||||
|
**Hope this works for you!**
|
||||||
|
|
||||||
108
MagiskOnWSA/DLL/docs/Fixes/Fix Error 0x80073CF6.md
Normal file
108
MagiskOnWSA/DLL/docs/Fixes/Fix Error 0x80073CF6.md
Normal file
@ -0,0 +1,108 @@
|
|||||||
|
## Issue: </br> Error 0x80073CF6 when "Run.bat" is executed to install Windows Subystem for Android (WSA)
|
||||||
|
### Preface:
|
||||||
|
##### This issue can arise due to many factors that is preventing the app from being registered. Although there is no definite solution, we can try these steps to try to fix the problem
|
||||||
|
##### This installation issue may also arise in systems that are using Modified Windows OSes such as ReviOS, Tiny10/11, etc. This is due to the fact that these OSes have been modified to remove certain features that are deemed unnecessary. This may cause issues with the installation of WSA.
|
||||||
|
</br>
|
||||||
|
|
||||||
|
```Powershell
|
||||||
|
Add-AppxPackage : Deployment failed with HRESULT: 0x80073CF6, Package could not be registered
|
||||||
|
In E:\WSA\Install.ps1:102 Character:1
|
||||||
|
+ Add-AppxPackage -ForceApplicationShutdown -ForceUpdateFromAnyVersion
|
||||||
|
|
||||||
|
+ CategoryInfo : WriteError: (E:\WSA\AppxManifest.xml:String) [Add-AppxPackage], IOException
|
||||||
|
+ FullyQualifiedErrorId : DeploymentError,Microsoft.Windows.Appx.PackageManager.Commands.AddAppxPackageCommand
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
</br>
|
||||||
|
|
||||||
|
---
|
||||||
|
## Prequisite Steps:
|
||||||
|
|
||||||
|
**1. Ensure the partition/drive you are installing from is NTFS**
|
||||||
|
|
||||||
|
**2. Redownload WSA Build .zip (sometime the files can be corrupted during download and extraction)**
|
||||||
|
|
||||||
|
**3. If you have installed WSA prior, make sure that it has been uninstalled and delete all folders containing "WindowsSubsystemForAndroid" from the following directories/paths and the subdirectories within:**
|
||||||
|
|
||||||
|
- *C:\ProgramData\Microsoft\Windows\AppRepository*
|
||||||
|
|
||||||
|
- *C:\ProgramData\Microsoft\Windows\WindowsApps*
|
||||||
|
|
||||||
|
- *%localappdata\ProgramData\Packages*
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
**4. Restart your Computer**
|
||||||
|
|
||||||
|
If the issue has been fixed, then there is no need to follow through the rest of the guide.
|
||||||
|
However, if you have the same issue, it is vital that you obtain the logs and try to decipher what is causing the error
|
||||||
|
|
||||||
|
To obtain the logs (admin privilege required):
|
||||||
|
|
||||||
|
1. Open a PowerShell window and change working directory to your Windows Subsystem For Android™ directory.
|
||||||
|
|
||||||
|
2. Run the command below in PowerShell. This should fail with an ActivityID, which is a UUID required for the next step.
|
||||||
|
```Powershell
|
||||||
|
Add-AppxPackage -ForceApplicationShutdown -ForceUpdateFromAnyVersion -Register .\AppxManifest.xml
|
||||||
|
```
|
||||||
|
3. Run the command below in PowerShell. This should print the log of the failed operation.
|
||||||
|
|
||||||
|
```Powershell
|
||||||
|
Get-AppPackageLog -ActivityID <UUID>
|
||||||
|
```
|
||||||
|
|
||||||
|
</br>
|
||||||
|
|
||||||
|
|
||||||
|
---
|
||||||
|
|
||||||
|
### There are various causes that lead to error 0x80073CF6 </br> Find the fix that matches the error presented in the logs obtained from the instructions above
|
||||||
|
|
||||||
|
---
|
||||||
|
## Issue 1: 0x800706D9 "There are no more endpoints avaliable from endpoint mapper"
|
||||||
|
|
||||||
|
<img src="https://user-images.githubusercontent.com/68516357/227363632-7270ee01-9a98-44c2-9ccc-1fb2ef24897c.jpg" style="width: 900px;"/>
|
||||||
|
|
||||||
|
### **Windows Firewall**
|
||||||
|
|
||||||
|
**1. Ensure that Windows Firewall is on and is working with "Recommended Settings" being enabled**
|
||||||
|
|
||||||
|
**2. Ensure that Windows Firewall service is running. If not, enable it.**
|
||||||
|
|
||||||
|
**3. Restart your PC**
|
||||||
|
|
||||||
|
### Other Firewalls
|
||||||
|
|
||||||
|
**1. Ensure that your Firewall is on and is working with "Recommended Settings" being enabled**
|
||||||
|
|
||||||
|
**2. Ensure that your Firewall is not blocking or preventing new entries**
|
||||||
|
|
||||||
|
**3. Restart your PC**
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
---
|
||||||
|
## Issue 2: 0x80073B06 "Initial screen image for the current application context cannot be recognized"
|
||||||
|
|
||||||
|
```powershell
|
||||||
|
Installing MagiskOnWSA...
|
||||||
|
Add AppxPackage: Deployment failed due to HRESULT: 0x80073CF6, unable to register the package.
|
||||||
|
AppxManifest.xml (24,27): Error 0x80073B06: Unable to install or update package MicrosoftCorporateII.WindowsSubsystemForAndroid_ 8wekyb 3d8bbwe because the initial screen image for the current application context cannot be recognized. The application context may include specific language, DPI, contrast, or other special conditions. If you cannot recognize a context specific splash screen image, add a splash screen image to use as the default setting. Note: For additional information, look for [ActivityId] 94c065bb-5a2a-0004-129b-c1942a5ad901 in the event log, or use the command line Get AppPackageLo g - ActivityID 94c065bb-5a2a-0004-129b-c1942a5ad901 in the location D: WSA WSA Install.ps1:106 Character: 1
|
||||||
|
+ Add-AppxPackage -ForceApplicationShutdown -ForceUpdateFromAnyVersion ...
|
||||||
|
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
|
||||||
|
+ CategoryInfo : WriteError: (D:\WSA\WSA\AppxManifest.xml:String) [Add-AppxPackage], IOException
|
||||||
|
+ FullyQualifiedErrorId : DeploymentError,Microsoft.Windows.Appx.PackageManager.Commands.AddAppxPackageCommand
|
||||||
|
```
|
||||||
|
### Solution:
|
||||||
|
|
||||||
|
**1.** If you encounter this problem when installing from a build built using [MagiskOnWSALocal](https://github.com/LSPosed/MagiskOnWSALocal) or [WSA-Script](https://github.com/YT-Advanced/WSA-Script), try deleting the previously built builds and rebuild. Make sure to delete and reclone the git repo if you are building using MagiskOnWSALocal.
|
||||||
|
|
||||||
|
***Or***
|
||||||
|
|
||||||
|
**2.** If you encounter this problem when installing using prebuilt builds from [Releases](https://github.com/YT-Advanced/WSA-Script/releases/latest) from this repo, try redownloading the latest build. If the issue persists, report to the [Issues](https://github.com/YT-Advanced/WSA-Script/issues) and I will be happy to assist you
|
||||||
|
|
||||||
|
|
||||||
|
---
|
||||||
|
|
||||||
|
**Hope these fixes work for you!**
|
||||||
26
MagiskOnWSA/DLL/docs/Fixes/Fix Error 0x80073CF9.md
Normal file
26
MagiskOnWSA/DLL/docs/Fixes/Fix Error 0x80073CF9.md
Normal file
@ -0,0 +1,26 @@
|
|||||||
|
## Issue: </br> Error 0x80073CF9 when "Run.bat" is executed to install Windows Subystem for Android (WSA)
|
||||||
|
### Preface:
|
||||||
|
##### This issue can arise due to many factors such as corruption of files when downloading the .zip files or extracting from the .zip files. This can be also caused if the folder name is too long (This is the case as MagiskOnWSA tends to generate a long string for the .zip file and the folder within the archive.)
|
||||||
|
|
||||||
|
<img src="https://user-images.githubusercontent.com/68516357/219852713-fde4520d-9fa8-4c8b-80e6-ac2adecbeae9.png" style="width: 600px;"/>
|
||||||
|
|
||||||
|
---
|
||||||
|
## Solution
|
||||||
|
|
||||||
|
**1. Ensure the partition/drive you are installing from is NTFS**
|
||||||
|
|
||||||
|
**2. Redownload WSA .zip file on [Release page](https://github.com/YT-Advanced/WSA-Script/releases/latest) (sometime the files can be corrupted during download and extraction)**
|
||||||
|
|
||||||
|
**3. Rename the .zip folder to a shorter name, which can be anything to your choosing </br> (WSA_2xxx.xxxxx.xx.x_x64_Release-Nightly-with-magisk-xxxxxxx-MindTheGapps-13.0-as-Pixel-5-RemovedAmazon ----> WSAArchive2XXX)**
|
||||||
|
|
||||||
|
**4. Extract the .zip using WinRAR or a proper archive tool and not the built in Windows .zip extractor**
|
||||||
|
|
||||||
|
**5. Rename the extracted folder(s) to a shorter name, which can be anything to your choosing**
|
||||||
|
|
||||||
|
#### For example:
|
||||||
|
- **Before:** WSA_2XXX.XXXXX.X.X_XXXX_Release-Nightly-with-magisk-XXXXXXX-XXXXXX-MindTheGapps-XX.X-RemovedAmazon
|
||||||
|
- **After:** WSAExtracted2XXX
|
||||||
|
|
||||||
|
**6. Ensure that 'Run.bat' is run as Administrator**
|
||||||
|
|
||||||
|
**Hope this works for you!**
|
||||||
33
MagiskOnWSA/DLL/docs/Fixes/Fix Error 0x80073CFB.md
Normal file
33
MagiskOnWSA/DLL/docs/Fixes/Fix Error 0x80073CFB.md
Normal file
@ -0,0 +1,33 @@
|
|||||||
|
## Issue: </br> Error 0x80073CFB when "Run.bat" is executed to install Windows Subystem for Android (WSA)
|
||||||
|
### Preface:
|
||||||
|
##### This issue can arise due to the fact that "the provided package is already installed, and reinstallation of the package was blocked. Check the AppXDeployment-Server event log for details."
|
||||||
|
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
|
||||||
|
---
|
||||||
|
## Solution
|
||||||
|
|
||||||
|
**1. Go to ``%LOCALAPPDATA%/Packages/``, and make sure that the folder ``MicrosoftCorporationII.WindowsSubsystemForAndroid_8wekyb3d8bbwe`` is deleted. (If it does not exist, move on to Step **2**.)**
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
**2. Open Powershell (as Admin) and run the following command:**
|
||||||
|
|
||||||
|
```powershell
|
||||||
|
Get-AppxPackage -Name "MicrosoftCorporationII.WindowsSubsystemForAndroid" -AllUsers | Remove-AppxPackage -AllUsers
|
||||||
|
```
|
||||||
|
<br>
|
||||||
|
|
||||||
|
**3. Delete all folders related to WSA (expect the .zip files for WSA Builds), which include folders extracted for WSA installation.**
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
**4. Re-extract and re-run ``Run.bat``**
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
***The issue should now be fixed***
|
||||||
|
|
||||||
|
---
|
||||||
29
MagiskOnWSA/DLL/docs/Fixes/Fix Error 0x80073CFD.md
Normal file
29
MagiskOnWSA/DLL/docs/Fixes/Fix Error 0x80073CFD.md
Normal file
@ -0,0 +1,29 @@
|
|||||||
|
## Issue: </br> Error 0x80073CFD when "Run.bat" is executed to install Windows Subystem for Android (WSA)
|
||||||
|
### Preface:
|
||||||
|
##### This issue is caused by having a Windows 10 Build that is too old to run WSA and hence the installer halts and presents the error, as shown below
|
||||||
|
|
||||||
|
</br>
|
||||||
|
|
||||||
|
```Powershell
|
||||||
|
Registering AppxManifest.xml...
|
||||||
|
Add-AppxPackage : Deployment failed with HRESULT: 0x80073CFD,
|
||||||
|
Prerequisite for an install could not be satisfied. Windows cannot install package MicrosoftCorporationII.WindowsSubsystemForAndroid_2301.40000.7.0_x64__8wekyb3d8bbwe because this package is not compatible with the device.
|
||||||
|
The package requires OS version 10.0.19044.2604 or higher on the Windows.Desktop device family.
|
||||||
|
The device is currently running OS version 10.0.19043.2364.
|
||||||
|
NOTE: For additional information, look for [ActivityId] 8b8599fb-55c1-0002-338b-868bc155d901 in the Event Log or use the command line
|
||||||
|
Get-AppPackageLog -ActivityID 8b8599fb-55c1-0002-338b-868bc155d901
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
</br>
|
||||||
|
|
||||||
|
---
|
||||||
|
## Solution:
|
||||||
|
|
||||||
|
### The Solution is simple:
|
||||||
|
|
||||||
|
Using the [Microsoft Guide](https://support.microsoft.com/en-gb/windows/update-windows-3c5ae7fc-9fb6-9af1-1984-b5e0412c556a#WindowsVersion=Windows_10), update Windows 10 to the latest version
|
||||||
|
|
||||||
|
***Or***
|
||||||
|
|
||||||
|
Using the [Windows 10 Update Assistant](https://support.microsoft.com/en-us/topic/windows-10-update-assistant-3550dfb2-a015-7765-12ea-fba2ac36fb3f), update Windows 10 to the latest version
|
||||||
15
MagiskOnWSA/DLL/docs/Fixes/Fix Error 0x80073D10.md
Normal file
15
MagiskOnWSA/DLL/docs/Fixes/Fix Error 0x80073D10.md
Normal file
@ -0,0 +1,15 @@
|
|||||||
|
## Issue: </br> Error 0x80073D10 when "Run.bat" is executed to install Windows Subystem for Android (WSA)
|
||||||
|
### Preface:
|
||||||
|
##### This issue is caused when your are trying to install the incorrect WSA package for your CPU Archetecture. For example, you are mistakenly trying to install the arm64 package on your x64 system.
|
||||||
|
|
||||||
|
<img src="https://user-images.githubusercontent.com/68516357/222832801-66c0b96a-363d-4f6e-a654-6bfb618c32e2.png" style="width: 500px;"/>
|
||||||
|
|
||||||
|
---
|
||||||
|
|
||||||
|
## Solution
|
||||||
|
|
||||||
|
**1. To ensure that you download the correct package for your CPU archtecture, go to the [Release](https://github.com/YT-Advanced/WSA-Script/releases/latest) of this repository then check again**
|
||||||
|
|
||||||
|
**2. Click on the package matching your Operating System (OS) and CPU Archetecture**
|
||||||
|
|
||||||
|
**3. Download then install the package by follow the [Installation guide](https://github.com/YT-Advanced/WSA-Script#--installation) in README.md file**
|
||||||
47
MagiskOnWSA/DLL/docs/Fixes/FixInstallps1.md
Normal file
47
MagiskOnWSA/DLL/docs/Fixes/FixInstallps1.md
Normal file
@ -0,0 +1,47 @@
|
|||||||
|
<summary><h2>Issue:<h2><h3> Install.ps1 is not recognized/missing<h3></summary>
|
||||||
|
|
||||||
|
<img src="https://media.discordapp.net/attachments/1044322950725259274/1068243571544690719/9Qf3veK.png" />
|
||||||
|
<img src="https://user-images.githubusercontent.com/68516357/215262023-89e0e0fa-3dd7-4d6d-b93a-224169f61971.png" />
|
||||||
|
|
||||||
|
## Solution
|
||||||
|
|
||||||
|
If the popup windows disappear without asking administrative permission and Windows Subsystem For Android™ is not installed successfully, you should manually run Install.ps1 as administrator:
|
||||||
|
|
||||||
|
|
||||||
|
**1. Redownload the WSA Build and rename the extracted folder to a shorter name, which can be anything to your choosing** </br>
|
||||||
|
|
||||||
|
- For example:
|
||||||
|
|
||||||
|
- **Before:** WSA_2XXX.XXXXXXX_XXXX_Release-Nightly-with-magisk-XXXXXXX-XXXXXX-MindTheGapps-XX.X-RemovedAmazon
|
||||||
|
|
||||||
|
- **After:** WSAArchive2XXX
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
**2. Copy the path of the folder by right clicking on the folder and select "Show More Options" and click on "Copy as path"**
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
**3. Press Win + X on your keyboard and select Windows™ Terminal (Admin) or Powershell (Admin) depending on the version of Windows™ you are running**
|
||||||
|
|
||||||
|
|||
|
||||||
|
|--------|------|
|
||||||
|
|<img src="https://upload.wikimedia.org/wikipedia/commons/e/e6/Windows_11_logo.svg" style="width: 200px;"/> |<img src="https://upload.wikimedia.org/wikipedia/commons/0/05/Windows_10_Logo.svg" style="width: 200px;"/> |
|
||||||
|
|||
|
||||||
|
|
||||||
|
|
||||||
|
**4. Input the command below and press enter, replacing {X:\path\to\your\extracted\folder} including the {} with the path of the extracted folder**
|
||||||
|
|
||||||
|
```Powershell
|
||||||
|
cd "{X:\path\to\your\extracted\folder}"
|
||||||
|
```
|
||||||
|
|
||||||
|
**5. Input the command below and press Enter**
|
||||||
|
|
||||||
|
```Powershell
|
||||||
|
PowerShell.exe -ExecutionPolicy Bypass -File .\Install.ps1
|
||||||
|
```
|
||||||
|
|
||||||
|
**6. The script will run and Windows Subsystem For Android™ will be installed**
|
||||||
|
|
||||||
|
</details>
|
||||||
144
MagiskOnWSA/DLL/docs/Fixes/FixInternet.md
Normal file
144
MagiskOnWSA/DLL/docs/Fixes/FixInternet.md
Normal file
@ -0,0 +1,144 @@
|
|||||||
|
## Issues:
|
||||||
|
### No Internet
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## Solution:
|
||||||
|
These will be split into multiple solutions due to the different causes of the problem of no internet on Windows Subsystem for Android (WSA) and Windows Subsytem for Linux (WSL)
|
||||||
|
|
||||||
|
---
|
||||||
|
|
||||||
|
<details>
|
||||||
|
<summary><h3>Fix #1: Uninstalling Hyper-V Network Adapters<h3></summary>
|
||||||
|
|
||||||
|
**Some Hyper-V Network Drivers may be interferring with WSA or WSL**
|
||||||
|
|
||||||
|
**⚠️ Carry these instructions out with caution. ⚠️**
|
||||||
|
|
||||||
|
**⚠️ I do not take responsibility for any damage caused ⚠️**
|
||||||
|
|
||||||
|
#### **Step 1: Open Device Manager**
|
||||||
|
1. Using Search or Win + X, open Device manager
|
||||||
|
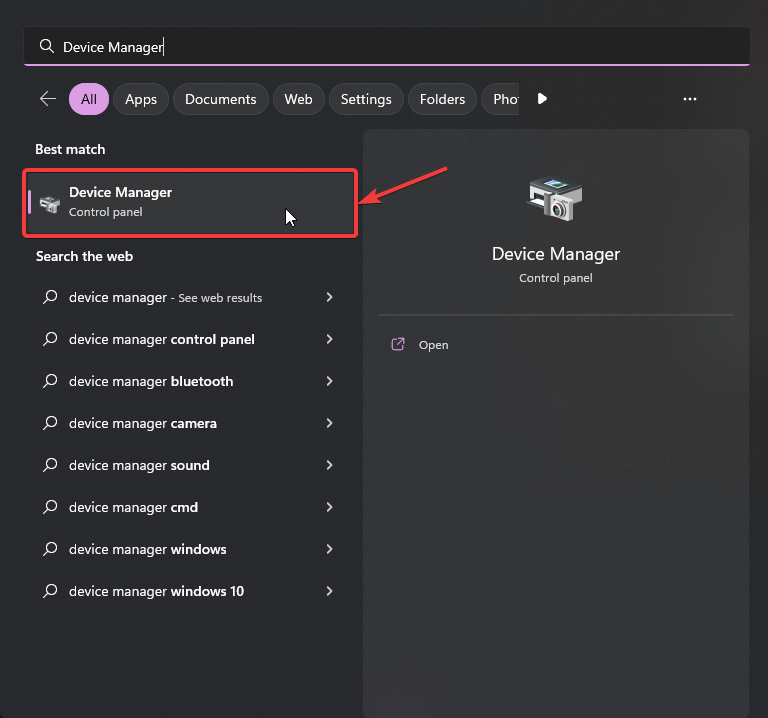
|
||||||
|
|
||||||
|
#### **Step 2: Show Hidden Device**
|
||||||
|
3. Press on "View"
|
||||||
|
4. Select "Show hidden devices"
|
||||||
|
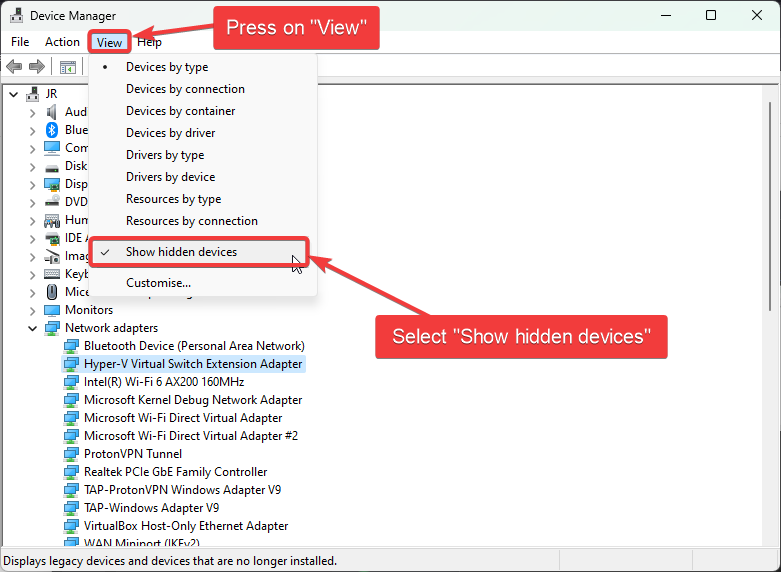
|
||||||
|
|
||||||
|
#### **Step 3: Uninstalling All Hyper-V Network Adapter**
|
||||||
|
5. Select each driver that has "Hyper-V" in its name
|
||||||
|
6. Right-Click and select "Uninstall Driver" for each of these drivers
|
||||||
|
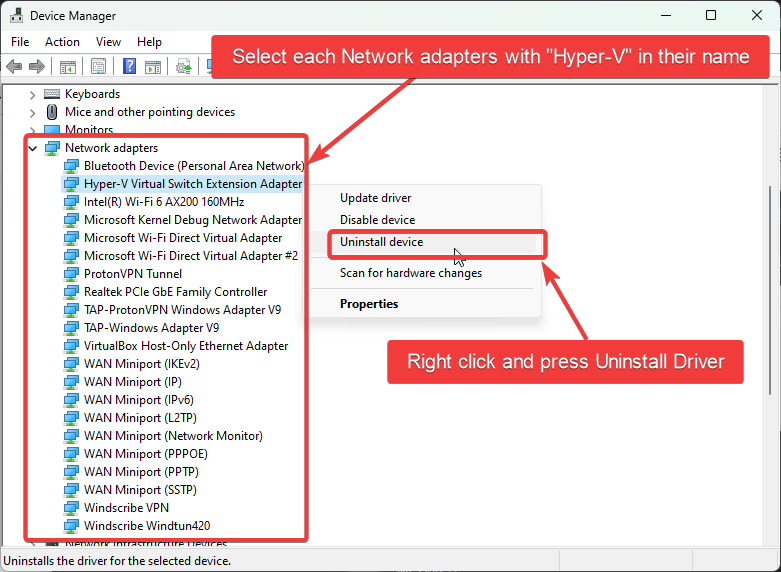
|
||||||
|
#### **Step 4: Restart Windows**
|
||||||
|

|
||||||
|
</details>
|
||||||
|
|
||||||
|
---
|
||||||
|
<details>
|
||||||
|
<summary><h3>Fix #2: Checking Firewall Settings<h3></summary>
|
||||||
|
|
||||||
|
Sometimes Windows Firewall and other Firewall tools and software may be the cause of internet issues. It is therefore important that we check them if we are facing issues with internet on WSA.
|
||||||
|
|
||||||
|
|
||||||
|
<summary><h4>Users with Windows Firewall<h4></summary>
|
||||||
|
|
||||||
|
****1. Open Windows Firewall by pressing the Windows Key and "R" key, Open Run****
|
||||||
|
|
||||||
|
****2. Type WF.msc, and then select OK. See also [Open Windows Firewall](https://learn.microsoft.com/en-us/windows/security/operating-system-security/network-security/windows-firewall/best-practices-configuring)****
|
||||||
|
|
||||||
|
****3. Go to the "Inbound Connection" tab****
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
****4. Find the entries in the list that state: "Windows Subsystem for Android™"****
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
|
||||||
|
****5. Confirm that these entries are Enabled and "Action" is set to "Allow" for both UDP and TCP for all entries (as shown above)****
|
||||||
|
|
||||||
|
****6. Now, go to the "Outbound Connection" tab****
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
****7. Find the entries in the list that state: "Windows Subsystem for Android™"****
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
****5. Confirm that these entries are Enabled and "Action" is set to "Allow" for both UDP and TCP for all entries (as shown above)****
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
> <picture>
|
||||||
|
> <source media="(prefers-color-scheme: light)" srcset="https://raw.githubusercontent.com/Mqxx/GitHub-Markdown/main/blockquotes/badge/light-theme/tip.svg">
|
||||||
|
> <img alt="Tip" src="https://raw.githubusercontent.com/Mqxx/GitHub-Markdown/main/blockquotes/badge/dark-theme/tip.svg">
|
||||||
|
> </picture><br>
|
||||||
|
>
|
||||||
|
> You may not have as many entries for "Windows Subsystem for Android™", as shown in the screenshots provded. These are just for illustration purposes and Firewall entries may look different on your device.
|
||||||
|
|
||||||
|
|
||||||
|
<summary><h4>Antivirus Users<h4></summary>
|
||||||
|
|
||||||
|
It is a known issue that some antivirus firewall such as those built-in to ESET, Bitdefender, AVG and many others, can prevent the internet for Windows Susbsystem for Android (WSA) from working.
|
||||||
|
It is highly recommended to disable the firewall provided by these Antivirus/Antimalware tools and fallback to Windows Firewall, to see if the internet starts working.
|
||||||
|
|
||||||
|
Source: From [this](https://community.bitdefender.com/en/discussion/91237/bitdefender-blocking-wsl2-traffic-solution-to-a-thread-that-was-left-unresolved)
|
||||||
|
|
||||||
|
|
||||||
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
---
|
||||||
|
|
||||||
|
<details>
|
||||||
|
<summary><h3>Fix #3: Changing Android DNS Settings<h3></summary>
|
||||||
|
|
||||||
|
****1. Open Windows Firewall by pressing the Windows Key and "R" key, Open Run****
|
||||||
|
|
||||||
|
****2. Type wsa://com.android.settings, and then select OK.****
|
||||||
|
|
||||||
|
****3. Wait for Android Settings to load and open.****
|
||||||
|
|
||||||
|
****4. In Android Settings, click on the "Network and Internet" Section.****
|
||||||
|
|
||||||
|
****5. In the "Network and Internet" Section, select "Private DNS" .****
|
||||||
|
|
||||||
|
****6. In the "Select Private DNS mode", click on "Private DNS provider hostname".****
|
||||||
|
|
||||||
|
****7. In the entry box below, type "dns.google" and click save.****
|
||||||
|
|
||||||
|
****8. Now click on the "Internet" section and click on VirtWifi.****
|
||||||
|
|
||||||
|
****9. Click on "Disconnect".****
|
||||||
|
|
||||||
|
****10. Then click on "Connect".****
|
||||||
|
|
||||||
|
Your Internet should now be fixed!
|
||||||
|
|
||||||
|
|
||||||
|
</details>
|
||||||
|
|
||||||
|
---
|
||||||
|
|
||||||
|
<details>
|
||||||
|
<summary><h3>Fix #4: Enabling and Disabling Advanced Networking from WSA Settings<h3></summary>
|
||||||
|
|
||||||
|
1. Go to the Start Menu and search for Windows Subsystem for Android™
|
||||||
|
2. Depending on your WSA version, the Advanced Networking setting is located in different places witin the WSA Settings app
|
||||||
|
|
||||||
|
- For 2305 and newer builds, you must go to "Advanced settings" and then to "Experimental features"
|
||||||
|
- For 2304 and older builds, this setting is located in the "System" tab/ main screen when you open the Settings app
|
||||||
|
|
||||||
|
3. Make sure that if Advanced Networking is enabled, you disable it as this may be causing issues with the internet
|
||||||
|
|
||||||
|
This should fix the internet if Advanced Networking was on and the internet was not working due to this
|
||||||
|
|
||||||
|
</details>
|
||||||
26
MagiskOnWSA/DLL/docs/Fixes/FixPathTooLong.md
Normal file
26
MagiskOnWSA/DLL/docs/Fixes/FixPathTooLong.md
Normal file
@ -0,0 +1,26 @@
|
|||||||
|
## Issue: </br> Error stating that "Path is too long" when extracting files from .zip archive, needed to install Windows Subystem for Android (WSA)
|
||||||
|
### Preface:
|
||||||
|
##### This issue is caused if the folder name is too long. This is the typically the case as MagiskOnWSALocal script tends to generate a long string for the .zip file and the folder within the archive.
|
||||||
|
|
||||||
|
<img src="https://user-images.githubusercontent.com/68516357/219853616-154615b8-125c-4b68-b2f7-43fc2f7b1f74.png" style="width: 600px;"/>
|
||||||
|
|
||||||
|
---
|
||||||
|
## Solution
|
||||||
|
|
||||||
|
The solution is simple, all you have to do is:
|
||||||
|
|
||||||
|
**1. Rename the .zip/.7z file to a shorter name, which can be anything to your choosing** </br>
|
||||||
|
|
||||||
|
- For example:
|
||||||
|
|
||||||
|
- **Before:** WSA_2XXX.XXXXX.X.X_XXXX_Release-Nightly-with-magisk-XXXXXXX-XXXXXX-MindTheGapps-XX.X-RemovedAmazon
|
||||||
|
|
||||||
|
- **After:** WSAArchive2XXX
|
||||||
|
|
||||||
|
**2. Rename the extracted folder to a shorter name, which can be anything to your choosing** </br>
|
||||||
|
|
||||||
|
- For example:
|
||||||
|
|
||||||
|
- **Before:** WSA_2XXX.XXXXXXX_XXXX_Release-Nightly-with-magisk-XXXXXXX-XXXXXX-MindTheGapps-XX.X-RemovedAmazon
|
||||||
|
|
||||||
|
- **After:** WSAArchive2XXX
|
||||||
51
MagiskOnWSA/DLL/docs/Fixes/FixVirtError.md
Normal file
51
MagiskOnWSA/DLL/docs/Fixes/FixVirtError.md
Normal file
@ -0,0 +1,51 @@
|
|||||||
|
## Issues:
|
||||||
|
|
||||||
|
<img src="https://user-images.githubusercontent.com/68629435/213985345-a6fc6e97-63f3-4741-8965-8d62a0d6b824.png"/>
|
||||||
|
|
||||||
|
## Solution:
|
||||||
|
|
||||||
|
You may encounter this problem, even if Virtualization is enabled on your PC (in the BIOS) and shows up as enabled in Task Manager (as seen below) and Virtual Machine Platform + Windows Hypervisor Platform is Enabled. The solution is:
|
||||||
|
|
||||||
|
1. ***Remove WSA***: Right clicking on "Windows Subsystem for Android™ Settings" and pressing uninstall + Deleting the extracted WSA (MagiskOnWSA/WSABuilds) folder that you extracted and installed from.
|
||||||
|
|
||||||
|
2. ***Go to "Turn Windows features on and off" and if any of these features below are enabled, DISABLE THEM.***
|
||||||
|
|
||||||
|
- Hyper-V
|
||||||
|
- Virtual Machine Platform
|
||||||
|
- Windows Hypervisor Platform
|
||||||
|
- Windows Subsystem for Linux
|
||||||
|
|
||||||
|
3. ***Restart your PC***
|
||||||
|
|
||||||
|
4. ***Boot into your BIOS, and DISABLE Virtualization.***
|
||||||
|
|
||||||
|
- ***[Click here for a guide for Windows 11](https://support.microsoft.com/en-us/windows/enable-virtualization-on-windows-11-pcs-c5578302-6e43-4b4b-a449-8ced115f58e1)***
|
||||||
|
- ***[Click here for a guide for Windows 10](https://support.microsoft.com/en-us/windows/enable-virtualization-on-windows-10-pcs-c5578302-6e43-4b4b-a449-8ced115f58e1)***
|
||||||
|
|
||||||
|
5. ***Ensure that you have Control Flow Guard enabled in Windows Security > Apps & browser control > Exploit protection.*** This is a known issue that can prevent WSA from starting
|
||||||
|
|
||||||
|
6. ***In registry editor (regedit), go to “\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\FsDepends"***
|
||||||
|
|
||||||
|
Change the value of “Start” from “3” to “0”
|
||||||
|
|
||||||
|
> **Note**
|
||||||
|
> You can change it back to 3, if it makes no difference
|
||||||
|
|
||||||
|
7. ***Then in CMD (Run as Adminstrator), paste:***
|
||||||
|
|
||||||
|
```cmd
|
||||||
|
bcdedit /set hypervisorlaunchtype auto
|
||||||
|
```
|
||||||
|
|
||||||
|
8. ***ENABLE the features that you disabled in ``Step 2`` and restart a second time.***
|
||||||
|
|
||||||
|
9. ***Boot into your BIOS, and ENABLE Virtualization.***
|
||||||
|
|
||||||
|
- ***[Click here for a guide for Windows 11](https://support.microsoft.com/en-us/windows/enable-virtualization-on-windows-11-pcs-c5578302-6e43-4b4b-a449-8ced115f58e1)***
|
||||||
|
- ***[Click here for a guide for Windows 10](https://support.microsoft.com/en-us/windows/enable-virtualization-on-windows-10-pcs-c5578302-6e43-4b4b-a449-8ced115f58e1)***
|
||||||
|
|
||||||
|
10. ***Restart the Computer***
|
||||||
|
|
||||||
|
11. ***Reinstall WSA by running `Run.bat`***
|
||||||
|
|
||||||
|
**Hope this works for you!**
|
||||||
58
MagiskOnWSA/DLL/docs/Fixes/Google Play Issues.md
Normal file
58
MagiskOnWSA/DLL/docs/Fixes/Google Play Issues.md
Normal file
@ -0,0 +1,58 @@
|
|||||||
|
|
||||||
|
## Issue 1: After signing in to your Google Account from the Play Store App, Play Store keeps crashing
|
||||||
|
|
||||||
|
### Preface:
|
||||||
|
##### This issue will prevent you from opening Play Store and effectively prevent the function of MindTheGapps/OpenGapps. This issue may usually occur after signing in. Known cases indicate that this issue is pretty common on newer hardware (12th or 13th Gen Intel Processors, for example)
|
||||||
|
|
||||||
|
---
|
||||||
|
|
||||||
|
## Solution:
|
||||||
|
|
||||||
|
###### Step 1.
|
||||||
|
|
||||||
|
**Open Android Settings by pressing the Windows Key and "R" key, Open Run**
|
||||||
|
|
||||||
|
###### Step 2.
|
||||||
|
|
||||||
|
**Type wsa://com.android.settings, and then select OK.**
|
||||||
|
|
||||||
|
###### Step 3.
|
||||||
|
|
||||||
|
**Wait for Android Settings to load and open.**
|
||||||
|
|
||||||
|
###### Step 4.
|
||||||
|
|
||||||
|
**In Android Settings, click on the "Apps" Section and then click on "All Apps".**
|
||||||
|
|
||||||
|
###### Step 5.
|
||||||
|
|
||||||
|
**In the "All Apps" Section, find the "Google Play Services" app .**
|
||||||
|
|
||||||
|
###### Step 6.
|
||||||
|
|
||||||
|
**Click on the "Google Play Services" app, which should open a page with various different options for the app ("Permissions", "Notification", "Storage and Cache" etc.)**
|
||||||
|
|
||||||
|
###### Step 7.
|
||||||
|
|
||||||
|
**Click on "Storage and Cache"**
|
||||||
|
|
||||||
|
###### Step 8.
|
||||||
|
|
||||||
|
**Find the "Manage Space" button and click on it, which should popup a window reading "Google Play services storage"**
|
||||||
|
|
||||||
|
###### Step 9.
|
||||||
|
|
||||||
|
**Click on "Clear All Data" and done**
|
||||||
|
|
||||||
|
</br>
|
||||||
|
|
||||||
|
## Issue 2: Could not sign-in. There was a problem connecting to play.google.com
|
||||||
|
|
||||||
|
### Preface:
|
||||||
|
##### This issue will prevent you from signing into Play Store and effectively prevent the function of MindTheGapps/OpenGapps. This issue may usually occur after updating. Known cases have occured after updating from a non Google Apps WSA build to a Google Apps build
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
---
|
||||||
|
|
||||||
|
## Solution: If you are using VPN, please disconnect it because VPN may make WSA fail to connect to VirtWifi.
|
||||||
13
MagiskOnWSA/DLL/docs/Fixes/InstallPs1FailedToUpdate.md
Normal file
13
MagiskOnWSA/DLL/docs/Fixes/InstallPs1FailedToUpdate.md
Normal file
@ -0,0 +1,13 @@
|
|||||||
|
## Issues: Install.ps1 Failed To Update
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
<img src="https://github.com/MustardChef/WSABuilds/assets/68516357/7dff07f2-fde7-40b8-946c-d63ea18b2f99"/>
|
||||||
|
|
||||||
|
## Solution:
|
||||||
|
|
||||||
|
1. Run Powershell with this command:
|
||||||
|
```powershell
|
||||||
|
PowerShell.exe -ExecutionPolicy Bypass -File .\Install.ps1
|
||||||
|
```
|
||||||
|
|
||||||
29
MagiskOnWSA/DLL/docs/Fixes/InternetSecuritySettingsBlock.md
Normal file
29
MagiskOnWSA/DLL/docs/Fixes/InternetSecuritySettingsBlock.md
Normal file
@ -0,0 +1,29 @@
|
|||||||
|
## Issue: </br> Error stating that "Your Internet security settings prevented one or more files from opening" when trying to run `Install.ps1` or `Run.bat` to install Windows Subystem for Android (WSA)
|
||||||
|
|
||||||
|
### Preface:
|
||||||
|
##### This issue is caused if the folder name is too long. This is the typically the case as MagiskOnWSALocal script tends to generate a long string for the .zip file and the folder within the archive.
|
||||||
|
|
||||||
|
<img src="https://github.com/MustardChef/WSABuilds/assets/68516357/b17308cb-6b99-419d-ba79-3119bdbacd9d" style="width: 400px;"/>
|
||||||
|
|
||||||
|
---
|
||||||
|
## Solution
|
||||||
|
|
||||||
|
The solution is simple, all you have to do is:
|
||||||
|
|
||||||
|
**1. Rename the .zip/.7z file to a shorter name, which can be anything to your choosing** </br>
|
||||||
|
|
||||||
|
- For example:
|
||||||
|
|
||||||
|
- **Before:** WSA_2XXX.XXXXX.X.X_XXXX_Release-Nightly-with-magisk-XXXXXXX-XXXXXX-MindTheGapps-XX.X-RemovedAmazon
|
||||||
|
|
||||||
|
- **After:** WSAArchive2XXX
|
||||||
|
|
||||||
|
**2. Rename the extracted folder to a shorter name, which can be anything to your choosing** </br>
|
||||||
|
|
||||||
|
- For example:
|
||||||
|
|
||||||
|
- **Before:** WSA_2XXX.XXXXXXX_XXXX_Release-Nightly-with-magisk-XXXXXXX-XXXXXX-MindTheGapps-XX.X-RemovedAmazon
|
||||||
|
|
||||||
|
- **After:** WSAArchive2XXX
|
||||||
|
|
||||||
|
---
|
||||||
30
MagiskOnWSA/DLL/docs/Fixes/Keyboard Is Not Working.md
Normal file
30
MagiskOnWSA/DLL/docs/Fixes/Keyboard Is Not Working.md
Normal file
@ -0,0 +1,30 @@
|
|||||||
|
## Issue: Keyboard Does Not Work
|
||||||
|
|
||||||
|
### Preface:
|
||||||
|
##### This issue will prevent you from using your keyboard on WSA
|
||||||
|
|
||||||
|
|
||||||
|
## Solution:
|
||||||
|
|
||||||
|
#### 1. ***Open Run by pressing the Windows Key and R***
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
#### 2. ***Type in services.msc in the box and then select OK***
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
#### 3. ***Search for Touch Keyboard and Handwriting Panel***
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
#### 4. ***Enable it by switching startup type to automatic***
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
#### 5. ***Click apply***
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
#### 6. ***Restart your computer.***
|
||||||
|
|
||||||
33
MagiskOnWSA/DLL/docs/Fixes/MissingIcons.md
Normal file
33
MagiskOnWSA/DLL/docs/Fixes/MissingIcons.md
Normal file
@ -0,0 +1,33 @@
|
|||||||
|
## Issue: Icons have disappeared or have turned white after updating WSA or after restarting your computer
|
||||||
|
|
||||||
|
### Preface:
|
||||||
|
##### This looks like a bug in the WSA itself and the icons can be restored by the following steps.
|
||||||
|
|
||||||
|
## Solution
|
||||||
|
|
||||||
|
**1.** Backup `userdata.vhdx` from `%LOCALAPPDATA%\Packages\MicrosoftCorporationII.WindowsSubsystemForAndroid_8wekyb3d8bbwe\LocalCache\userdata.vhdx`
|
||||||
|
|
||||||
|
**2.** Uninstall WSA by [Following this guide](https://github.com/YT-Advanced/WSA-Script#--uninstallation)
|
||||||
|
|
||||||
|
**3.** Remove the two lines in `Install.ps1` that automatically launches Magisk and Play Store after the installation is finished
|
||||||
|
|
||||||
|
```powershell
|
||||||
|
function Finish {
|
||||||
|
Clear-Host
|
||||||
|
Start-Process "wsa://com.topjohnwu.magisk"
|
||||||
|
Start-Process "wsa://com.android.vending"
|
||||||
|
}
|
||||||
|
```
|
||||||
|
|
||||||
|
**4.** Install WSA
|
||||||
|
|
||||||
|
**5.** Restore `userdata.vhdx` to `%LOCALAPPDATA%\Packages\MicrosoftCorporationII.WindowsSubsystemForAndroid_8wekyb3d8bbwe\LocalCache\userdata.vhdx`
|
||||||
|
|
||||||
|
**6.** Start WSA
|
||||||
|
|
||||||
|
</br>
|
||||||
|
|
||||||
|
> **Warning**
|
||||||
|
>**Do not start WSA before restoring user data.**
|
||||||
|
|
||||||
|
</br>
|
||||||
@ -0,0 +1,33 @@
|
|||||||
|
## Issue: </br> Error: No connection could be made because the target machine actively refused it (10061)
|
||||||
|
### Preface:
|
||||||
|
##### This issue occurs when you are either using a sideloading application such as [WSA-Sideloader](https://github.com/infinitepower18/WSA-Sideloader) or [WSAPacman](https://github.com/alesimula/wsa_pacman), or when you try to connect to a device using ``adb.exe`` via [Android SDK Platform Tools](https://developer.android.com/tools/releases/platform-tools). This issue arises due to an issue with the inability of Hyper V to reserve port 58526 causing the issue, as seen below.
|
||||||
|
|
||||||
|
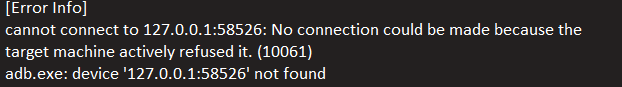
|
||||||
|
|
||||||
|
```
|
||||||
|
cannot connect to ||127.0.0.1:58526:|| No connection could be made because the target machine actively refused it. (10061)
|
||||||
|
```
|
||||||
|
---
|
||||||
|
|
||||||
|
## Solution
|
||||||
|
|
||||||
|
This is a [bug](https://github.com/microsoft/WSA/issues/136) with the subsystem itself, restarting the PC will usually fix it. But, if you still get this error, try these steps:
|
||||||
|
|
||||||
|
- ##### _**1. Make sure WSA is turned off and disable WSA autostart in Task Manager ---> Startup Apps before proceeding**_
|
||||||
|
|
||||||
|
- ##### _**2. Disable Hyper-V (if it is enabled) using the command**_
|
||||||
|
|
||||||
|
```powershell
|
||||||
|
dism.exe /Online /Disable-Feature:Microsoft-Hyper-V
|
||||||
|
```
|
||||||
|
|
||||||
|
- ##### **3. Reboot your PC**
|
||||||
|
|
||||||
|
- ##### _**4. Reserve port 58526 so Hyper-V doesn't reserve it back using the command**_
|
||||||
|
```cmd
|
||||||
|
netsh int ipv4 add excludedportrange protocol=tcp startport=58526 numberofports=1
|
||||||
|
```
|
||||||
|
|
||||||
|
- ##### _**5. Re-enable Hyper-V (if it was previously enabled) using the command `dism.exe /Online /Enable-Feature:Microsoft-Hyper-V /All` and reboot your PC**_
|
||||||
|
|
||||||
|
**Hope this works for you!**
|
||||||
@ -0,0 +1,21 @@
|
|||||||
|
## Issue: </br> Windows Subystem for Android (WSA) is unable to run any apps and there is no splashscreen (when opening the Files app from the settings) and no icons for Android apps.
|
||||||
|
### Preface:
|
||||||
|
##### Why this occurs is unknown. However, after multiple attempts trying to fix this issue, a solution was found.
|
||||||
|
|
||||||
|
|
||||||
|
https://github.com/MustardChef/WSABuilds/assets/68516357/a9690842-5159-470a-b472-5990faabeac8
|
||||||
|
|
||||||
|
|
||||||
|
---
|
||||||
|
## Solution
|
||||||
|
|
||||||
|
**Rename the extracted folder to a shorter name, which can be anything to your choosing.**
|
||||||
|
|
||||||
|
- **Before:** WSA_2XXX.XXXXXXX_XXXX_Release-Nightly-with-magisk-XXXXXXX-XXXXXX-MindTheGapps-XX.X-RemovedAmazon
|
||||||
|
|
||||||
|
- **After:** WSAArchive2XXX
|
||||||
|
|
||||||
|
https://github.com/MustardChef/WSABuilds/assets/68516357/626ec699-6f74-40ff-94fb-26fbe1c4f182
|
||||||
|
|
||||||
|
**Hope this works for you!**
|
||||||
|
---
|
||||||
@ -0,0 +1,21 @@
|
|||||||
|
## Issue: </br> Windows Subystem for Android (WSA) Settings app crashes after installation, when opened, and you are unable to run any apps.
|
||||||
|
### Preface:
|
||||||
|
##### Why this occurs is unknown. However, after multiple attempts trying to fix this issue, a solution was found.
|
||||||
|
|
||||||
|
https://github.com/MustardChef/WSABuilds/assets/68516357/7333e8b4-7c09-4032-b816-47fc0d83767b
|
||||||
|
|
||||||
|
|
||||||
|
---
|
||||||
|
## Solution
|
||||||
|
|
||||||
|
**Rename the extracted folder to a shorter name, which can be anything to your choosing.**
|
||||||
|
|
||||||
|
- **Before:** WSA_2XXX.XXXXXXX_XXXX_Release-Nightly-with-magisk-XXXXXXX-XXXXXX-MindTheGapps-XX.X-RemovedAmazon
|
||||||
|
|
||||||
|
- **After:** WSAArchive2XXX
|
||||||
|
|
||||||
|
https://github.com/MustardChef/WSABuilds/assets/68516357/7a33df5b-e68b-43b1-9365-9c4d7ff5c2db
|
||||||
|
|
||||||
|
|
||||||
|
**Hope this works for you!**
|
||||||
|
---
|
||||||
51
MagiskOnWSA/DLL/docs/Fixes/WSA Stopped Working.md
Normal file
51
MagiskOnWSA/DLL/docs/Fixes/WSA Stopped Working.md
Normal file
@ -0,0 +1,51 @@
|
|||||||
|
## Issues: WSA Stopped Working!
|
||||||
|
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
##### ***You may encounter this problem. WSA has been working fine for you, but all of a sudden, it breaks/ stops working. You are distraught. What do you do, when WSA beloved had been borked.***
|
||||||
|
|
||||||
|
## Solution:
|
||||||
|
|
||||||
|
1. ***Go to "Turn Windows features on and off" and if any of these features below are enabled, DISABLE THEM.***
|
||||||
|
|
||||||
|
- Hyper-V
|
||||||
|
- Virtual Machine Platform
|
||||||
|
- Windows Hypervisor Platform
|
||||||
|
- Windows Subsystem for Linux
|
||||||
|
|
||||||
|
2. ***Restart your PC***
|
||||||
|
|
||||||
|
3. ***Boot into your BIOS, and DISABLE Virtualization.***
|
||||||
|
|
||||||
|
- ***[Click here for a guide for Windows 11](https://support.microsoft.com/en-us/windows/enable-virtualization-on-windows-11-pcs-c5578302-6e43-4b4b-a449-8ced115f58e1)***
|
||||||
|
- ***[Click here for a guide for Windows 10](https://support.microsoft.com/en-us/windows/enable-virtualization-on-windows-10-pcs-c5578302-6e43-4b4b-a449-8ced115f58e1)***
|
||||||
|
|
||||||
|
4. ***Ensure that you have Control Flow Guard enabled in Windows Security > Apps & browser control > Exploit protection.*** This is a known issue that can prevent WSA from starting
|
||||||
|
|
||||||
|
5. ***In registry editor (regedit), go to “\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\FsDepends"***
|
||||||
|
|
||||||
|
Change the value of “Start” from “3” to “0”
|
||||||
|
|
||||||
|
> **Note**
|
||||||
|
> You can change it back to 3, if it makes no difference
|
||||||
|
|
||||||
|
|
||||||
|
6. ***Then in CMD (Run as Adminstrator), paste:***
|
||||||
|
|
||||||
|
```cmd
|
||||||
|
bcdedit /set hypervisorlaunchtype auto
|
||||||
|
```
|
||||||
|
|
||||||
|
7. ***ENABLE the features that you disabled in ``Step 1`` and restart a second time.***
|
||||||
|
|
||||||
|
8. ***Boot into your BIOS, and ENABLE Virtualization.***
|
||||||
|
|
||||||
|
- ***[Click here for a guide for Windows 11](https://support.microsoft.com/en-us/windows/enable-virtualization-on-windows-11-pcs-c5578302-6e43-4b4b-a449-8ced115f58e1)***
|
||||||
|
- ***[Click here for a guide for Windows 10](https://support.microsoft.com/en-us/windows/enable-virtualization-on-windows-10-pcs-c5578302-6e43-4b4b-a449-8ced115f58e1)***
|
||||||
|
|
||||||
|
9. ***Restart the Computer***
|
||||||
|
|
||||||
|
10. ***Try re-running WSA by running `Run.bat` or via the Windows Subsystem for Android Settings app***
|
||||||
|
|
||||||
|
**Hope this works for you!**
|
||||||
33
MagiskOnWSA/DLL/docs/Guides/ADB-Sideloading.md
Normal file
33
MagiskOnWSA/DLL/docs/Guides/ADB-Sideloading.md
Normal file
@ -0,0 +1,33 @@
|
|||||||
|
# Sideloading APKs in to Windows Subsystem for Android
|
||||||
|
-------------
|
||||||
|
|
||||||
|
## Setting up ADB to work with WSA
|
||||||
|
- Launch **Windows Subsystem for Android**.
|
||||||
|
- Here, click on **Advanced Settings** and then enable **Developer mode** by clicking on the toggle button.
|
||||||
|
- Take note of **IP address and port** shown in the Developer mode section.
|
||||||
|
- Launch Windows Terminal and make sure ADB is installed ([install ADB](https://www.xda-developers.com/install-adb-windows-macos-linux/#adbsetupwindows)).
|
||||||
|
- Use command ``adb pair 127.0.0.1:58526`` to pair ADB with WSA.
|
||||||
|
- In Wireless debugging window, see **Device name** and under it **IP address and port**.
|
||||||
|
- Use command ``adb connect 127.0.0.1:58526`` to connect WSA with ADB.
|
||||||
|
|
||||||
|
Once this is done, use command ``adb devices`` to make sure that WSA is connected.
|
||||||
|
|
||||||
|
|
||||||
|
## Installing APKs using ADB
|
||||||
|
Now you can install any app you want, but I personally suggest installing a web browser and a file manager first.
|
||||||
|
- Download the APK.
|
||||||
|
- Open File Explorer, right click on downloaded APK and tap on Copy as path.
|
||||||
|
- Launch Windows Terminal.
|
||||||
|
- Use ``adb install <file path>`` to install the APK.
|
||||||
|
[**P.S.** You can right click to paste in Terminal]
|
||||||
|
|
||||||
|
## After installation using ADB
|
||||||
|
You can now open the web browser you installed in Android, and download and install Aurora Store like you do on any Android device - normally sideloading APK without using ADB.
|
||||||
|
***
|
||||||
|
|
||||||
|
|
||||||
|
### A list of suggested apps to install on WSA:
|
||||||
|
- [microG](https://microg.org/): A free-as-in-freedom re-implementation of Google’s proprietary Android user space apps and libraries.
|
||||||
|
- [Aurora Store](https://files.auroraoss.com/AuroraStore/Stable/): an app store that lets you download apps from Google Play without a Google account.
|
||||||
|
- [MiX](https://forum.xda-developers.com/t/app-2-2-mixplorer-v6-x-released-fully-featured-file-manager.1523691/): MiXplorer mix of explorers (SD, FTP, Lan, Cloud and other storage explorers) is a fast, smooth, beautiful, reliable and full-featured file manager with a simple and intuitive user interface.
|
||||||
|
- [Bromite](https://github.com/bromite/bromite): A Chromium fork with support for ad blocking and enhanced privacy.
|
||||||
24
MagiskOnWSA/DLL/docs/Guides/BusyBox.md
Normal file
24
MagiskOnWSA/DLL/docs/Guides/BusyBox.md
Normal file
@ -0,0 +1,24 @@
|
|||||||
|
## Guide: How to install BusyBox
|
||||||
|
|
||||||
|
### Preface:
|
||||||
|
##### Since Magisk has BusyBox built-in already, this proceedure is very simple
|
||||||
|
|
||||||
|
## Process
|
||||||
|
|
||||||
|
### Step 1:
|
||||||
|
Using an Android browser downloaded though the Play Store/sideloaded into WSA, download the following [Magisk Module](https://github.com/Magisk-Modules-Alt-Repo/BuiltIn-BusyBox) to install and symlink BusyBox with its applets to the Magisk built-in busybox binary. No need to do it manually or to get a Custom Build.
|
||||||
|
|
||||||
|
### Step 2:
|
||||||
|
Through Magisk Manager, install the Magisk module .zip file
|
||||||
|
|
||||||
|
### Step 3 (Optional):
|
||||||
|
You can then test if BusyBox is working by either using a Root Checker:
|
||||||
|
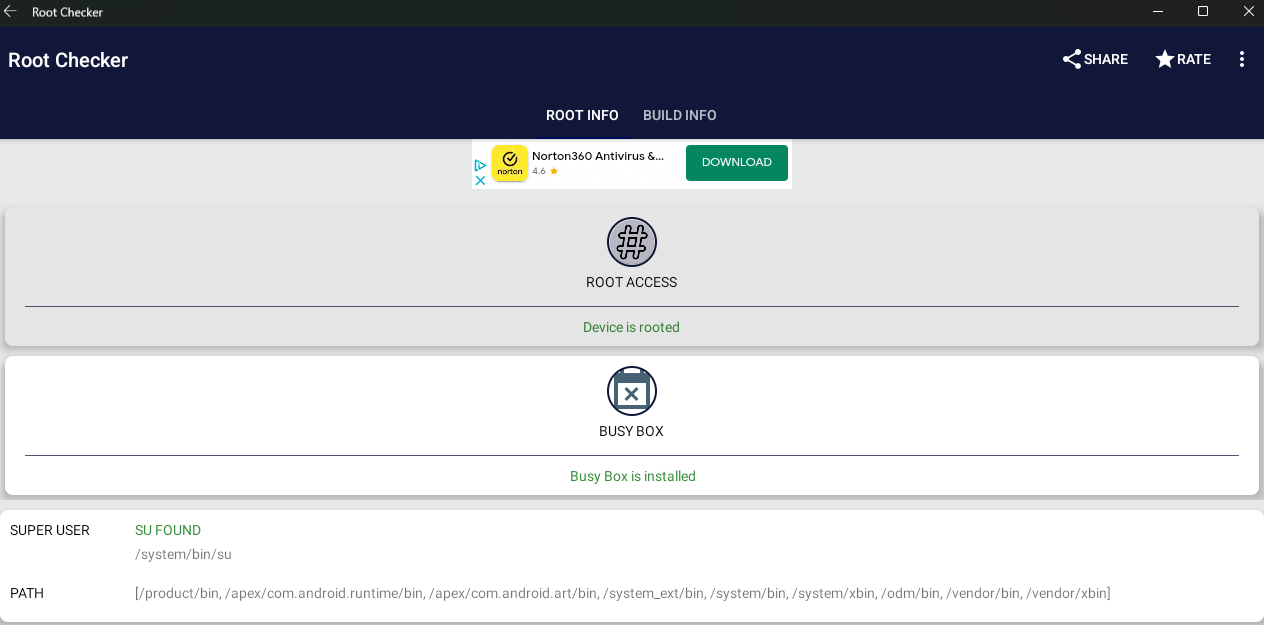
|
||||||
|
|
||||||
|
or by using ADB Shell and:
|
||||||
|
|
||||||
|
`` adb shell ``
|
||||||
|
``su``
|
||||||
|
``busybox | head -1``
|
||||||
|
|
||||||
|
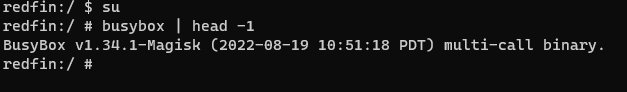
|
||||||
20
MagiskOnWSA/DLL/docs/Guides/ChangingGPU.md
Normal file
20
MagiskOnWSA/DLL/docs/Guides/ChangingGPU.md
Normal file
@ -0,0 +1,20 @@
|
|||||||
|
### Guide: Changing the GPU used by Windows Subsystem For Android™
|
||||||
|
|
||||||
|
1. Open up Windows Subsystem For Android™ Settings --> Either by going to the Start Menu and searching for it or by using the Search feature
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
2. Make sure to turn off Windows Subsystem For Android™ by pressing ``Turn off`` in the ``Turn off Windows Subsystem For Android™`` tab
|
||||||
|
|
||||||
|
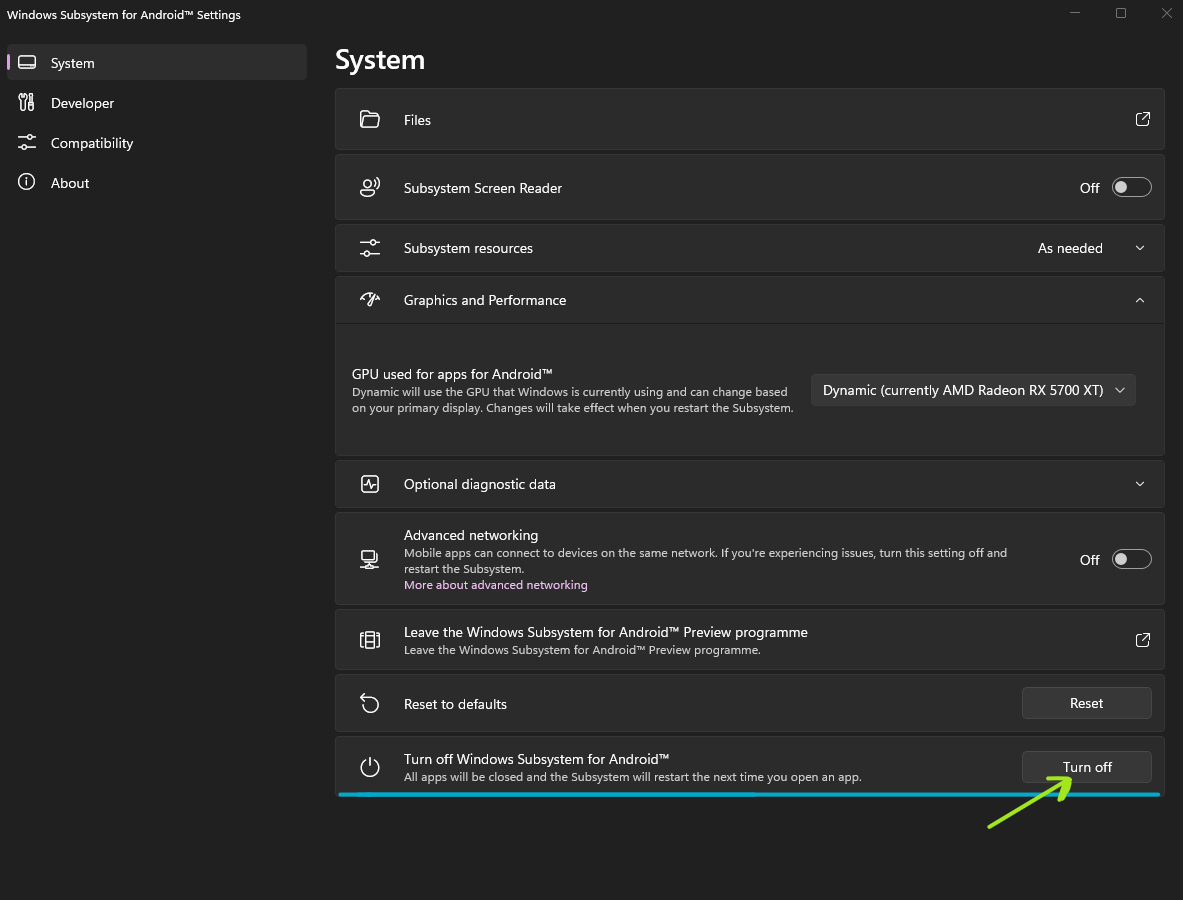
|
||||||
|
|
||||||
|
|
||||||
|
3. In Windows Subsystem For Android™ Settings select the ``Graphics and Performance`` Tab
|
||||||
|
|
||||||
|
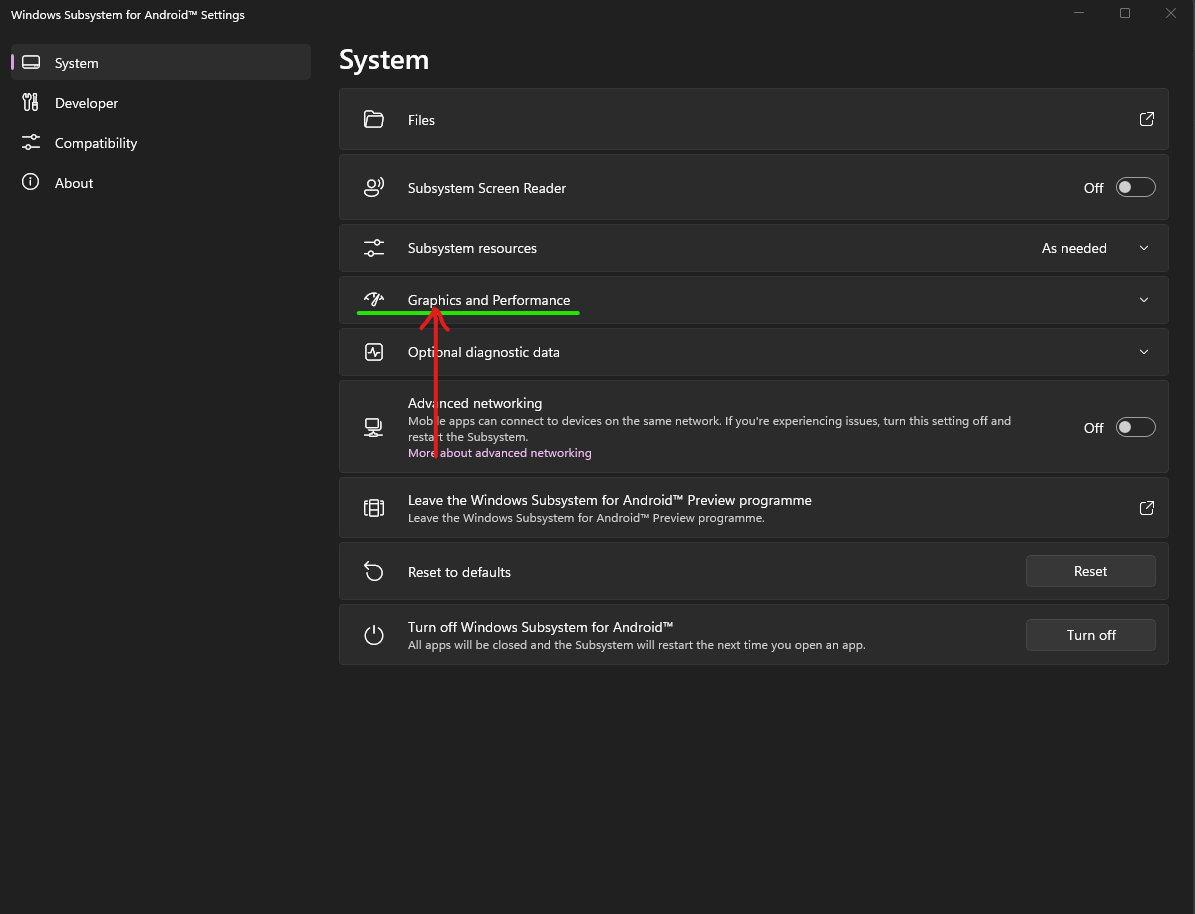
|
||||||
|
|
||||||
|
4. Click on the selection for ``GPU used for apps for Android™`` and select the GPU that you would like Windows Subsystem For Android™ to use.
|
||||||
|
|
||||||
|
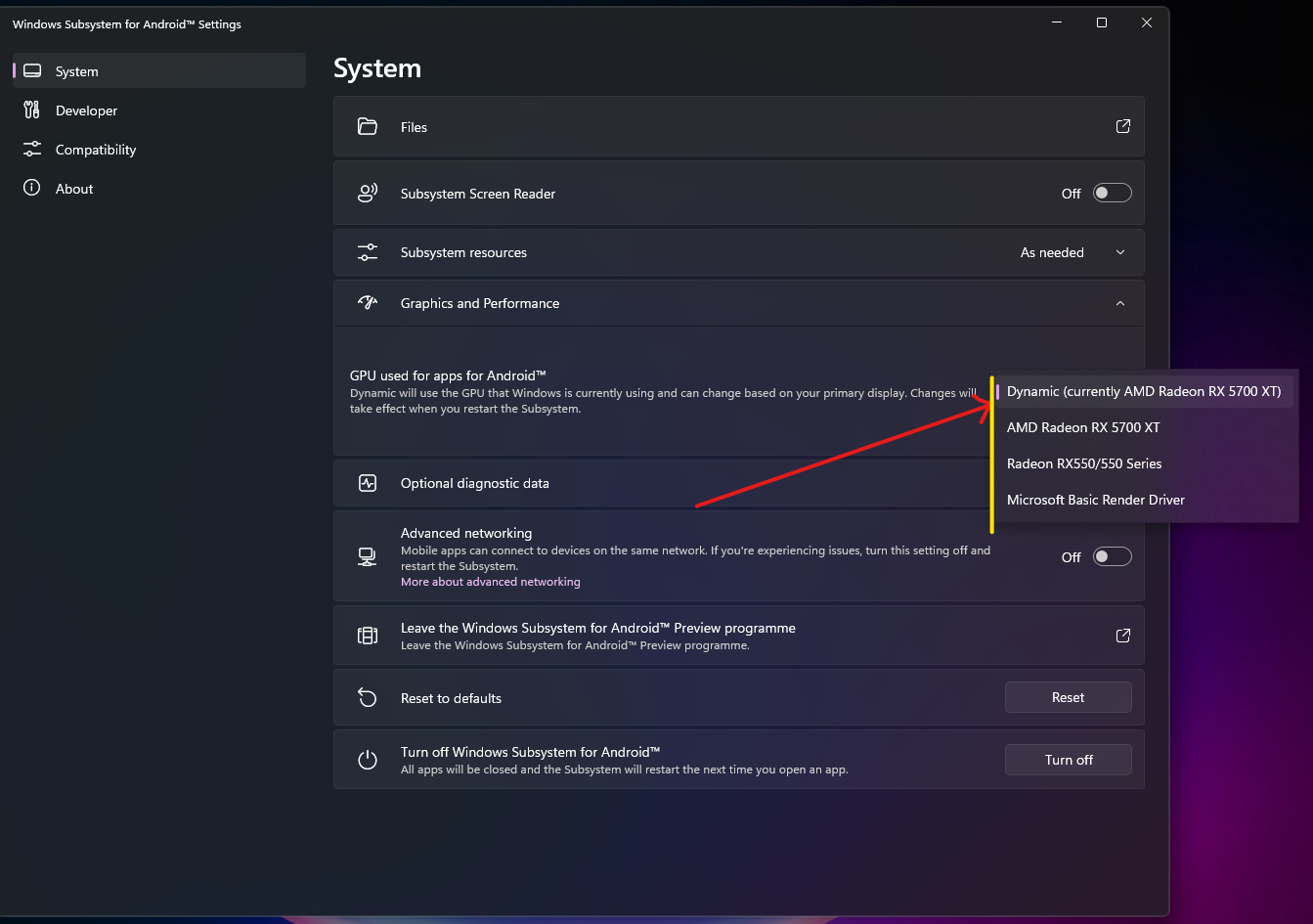
|
||||||
|
|
||||||
|
|
||||||
31
MagiskOnWSA/DLL/docs/Guides/Checksum.md
Normal file
31
MagiskOnWSA/DLL/docs/Guides/Checksum.md
Normal file
@ -0,0 +1,31 @@
|
|||||||
|
# Check integrity of downloaded file
|
||||||
|
|
||||||
|
|
||||||
|
### **1. Press Win + X on your keyboard and select Windows™ Terminal (Admin) or Powershell (Admin) depending on the version of Windows™ you are running**
|
||||||
|
|
||||||
|
|||
|
||||||
|
|--------|------|
|
||||||
|
|<img src="https://upload.wikimedia.org/wikipedia/commons/e/e6/Windows_11_logo.svg" style="width: 200px;"/> |<img src="https://upload.wikimedia.org/wikipedia/commons/0/05/Windows_10_Logo.svg" style="width: 200px;"/> |
|
||||||
|
|||
|
||||||
|
|
||||||
|
|
||||||
|
### **2. Input the command below and press enter, replacing {X:\path\to\your\downloaded\archive\package} including the {} with the path of the downloaded archive package**
|
||||||
|
|
||||||
|
```Powershell
|
||||||
|
cd "{X:\path\to\your\downloaded\archive\package}"
|
||||||
|
```
|
||||||
|
|
||||||
|
### **3. Input the command below and press enter, replacing WSA_2XXX.XXXXX.X.X_XXXX_Release-Nightly-with-magisk-XXXXXXX-XXXXXX-MindTheGapps-XX.X-RemovedAmazon with the name of the archive package**
|
||||||
|
|
||||||
|
```Powershell
|
||||||
|
certutil -hashfile "WSA_2XXX.XXXXX.X.X_XXXX_Release-Nightly-with-magisk-XXXXXXX-XXXXXX-MindTheGapps-XX.X-RemovedAmazon" SHA256
|
||||||
|
```
|
||||||
|
For PowerShell:
|
||||||
|
```PowerShell
|
||||||
|
(Get-FileHash -Path "WSA_2XXX.XXXXX.X.X_XXXX_Release-Nightly-with-magisk-XXXXXXX-XXXXXX-MindTheGapps-XX.X-RemovedAmazon" -Algorithm SHA256).Hash
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
### **4. Compare the SHA256 output with ones at [Release](https://github.com/YT-Advanced/WSA-Script/releases/latest) or in the `sha256-checksum.txt` (if you download artifact from the Custom Build task).**
|
||||||
|
- If package don't have the same SHA-256 Hash, please download then check again.
|
||||||
|
- If package have the same SHA-256, install it by [Following this guide](https://github.com/YT-Advanced/WSA-Script#--installation)
|
||||||
15
MagiskOnWSA/DLL/docs/Guides/KernelSU.md
Normal file
15
MagiskOnWSA/DLL/docs/Guides/KernelSU.md
Normal file
@ -0,0 +1,15 @@
|
|||||||
|
# Install KernelSU Manager
|
||||||
|
|
||||||
|
## Text Guide
|
||||||
|
|
||||||
|
1. [Connect to WSA with ADB](ADB-Sideloading.md#setting-up-adb-to-work-with-wsa)
|
||||||
|
2. Run the following command:
|
||||||
|
```
|
||||||
|
adb shell ksuinstall
|
||||||
|
```
|
||||||
|
|
||||||
|
If the installation completes successfully, the KernelSU Manager will launching.
|
||||||
|
|
||||||
|
<!--
|
||||||
|
## Video Guide
|
||||||
|
-->
|
||||||
21
MagiskOnWSA/DLL/docs/Guides/LocalHostLoopback.md
Normal file
21
MagiskOnWSA/DLL/docs/Guides/LocalHostLoopback.md
Normal file
@ -0,0 +1,21 @@
|
|||||||
|
## Guide: LocalHost Loopback
|
||||||
|
#### Preface: You want to connect WSA to the localhost (Windows 11 hosting machine) or to a development server I run on Windows 11 or any such scenario where you would want to connect to the Windows 11 localhost, but are unable to
|
||||||
|
|
||||||
|
### Note: Localhost Loopback has now been officially added to the update 2308 of WSA, and so this guide is probably outdated now.
|
||||||
|
|
||||||
|
---
|
||||||
|
|
||||||
|
## Process:
|
||||||
|
|
||||||
|
**1.** Run PowerShell as administrator
|
||||||
|
|
||||||
|
**2.** Execute
|
||||||
|
```powershell
|
||||||
|
Set-NetFirewallHyperVVMSetting -VMCreatorId '{9E288F02-CE00-4D9E-BE2B-14CE463B0298}' -LoopbackEnabled True
|
||||||
|
```
|
||||||
|
|
||||||
|
3.Execute
|
||||||
|
```powershell
|
||||||
|
New-NetFirewallHyperVRule -DisplayName LoopbackAllow -VMCreatorId '{9E288F02-CE00-4D9E-BE2B-14CE463B0298}' -Direction Inbound -Action Allow -LocalPorts [PORT]
|
||||||
|
```
|
||||||
|
(replacing [PORT] with the port you're trying to expose)
|
||||||
54
MagiskOnWSA/DLL/docs/Guides/MoveToExtDrive.md
Normal file
54
MagiskOnWSA/DLL/docs/Guides/MoveToExtDrive.md
Normal file
@ -0,0 +1,54 @@
|
|||||||
|
## Guide: Moving/Installing Windows Subsystem For Android™ (WSA) to another partition or disk
|
||||||
|
|
||||||
|
### Preface:
|
||||||
|
##### WSA can take up a lot of storage space, hence you want to move it to another partition or disk with more space. <br> This guide goes through a method by which you can install WSA from another disk and to store the data in that drive (instead of `%LOCALAPPDATA%\Packages\MicrosoftCorporationII.WindowsSubsystemForAndroid_8wekyb3d8bbwe`).
|
||||||
|
|
||||||
|
### Prerequisites:
|
||||||
|
- The partition/ disk that you want to move/install Windows Subsystem For Android™ to, ****MUST**** be **NTFS**
|
||||||
|
- Recommended that both disks, C:/ and the disk/partition that you want to install (move) WSA on (to), are SSDs
|
||||||
|
- HDDs may work, but performance issues may arise
|
||||||
|
- Basic knowledge on Command Prompt (CMD) usage
|
||||||
|
- There must be enough space on the disk/partiton that you are installing/moving WSA to (recommended 20GB, as the VHDX can become very large in size)
|
||||||
|
|
||||||
|
> **Note**
|
||||||
|
>
|
||||||
|
> If you want to preseve your data, make a backup of the `%LOCALAPPDATA%\Packages\MicrosoftCorporationII.WindowsSubsystemForAndroid_8wekyb3d8bbwe\LocalCache\userdata.vhdx` file. After uninstalling, copy the VHDX file back to the `%LOCALAPPDATA%\Packages\MicrosoftCorporationII.WindowsSubsystemForAndroid_8wekyb3d8bbwe\LocalCache` folder.
|
||||||
|
|
||||||
|
|
||||||
|
## Process:
|
||||||
|
|
||||||
|
|
||||||
|
- ### Step 1: Remove all previous installations from WSABuilds or official WSA Releases
|
||||||
|
- To remove WSA installed through WSABuild:
|
||||||
|
|
||||||
|
- **1.)** Make sure that Windows Subsystem For Android™ is not running
|
||||||
|
- **2.)** Search for ``Windows Subsystem For Android™ Settings`` using the built-in Windows Search, or through Add and Remove Programs and press uninstall
|
||||||
|
- **3.)** Delete the WSA folder that you extracted and Run.bat was run from to install WSA (MagiskOnWSA folder)
|
||||||
|
- **4.)** Go to ``%LOCALAPPDATA%/Packages/`` and delete the folder named ``MicrosoftCorporationII.WindowsSubsystemForAndroid_8wekyb3d8bbwe``
|
||||||
|
|
||||||
|
- If you get an error that states that the file(s) could not be deleted, make sure that WSA is turned off
|
||||||
|
|
||||||
|
- To remove WSA installed from the Microsoft Store:
|
||||||
|
|
||||||
|
- **1.)** Search for ``Windows Subsystem For Android™ Settings`` using the built-in Windows Search, or through Add and Remove Programs and press uninstall
|
||||||
|
|
||||||
|
|
||||||
|
- ### Step 2: Install WSA from the desired partition
|
||||||
|
- **1.)** Download the latest WSA Build according to Windows Version and CPU Archtecture from [Release](https://github.com/YT-Advanced/WSA-Script/releases/latest).
|
||||||
|
- **2.)** Extract to the desired partition or drive
|
||||||
|
- Using the same process as detailed in [Installation](https://github.com/YT-Advanced/WSA-Script#--installation)
|
||||||
|
- **3.)** Open the extracted folder and run ``Run.bat``
|
||||||
|
|
||||||
|
|
||||||
|
- ### Step 3: Moving the AppData (VHDX + data) from your Windows drive (C:\) to the desired partition/drive
|
||||||
|
- **1.)** Go to ``%LOCALAPPDATA%\Packages\`` and copy the folder named ``MicrosoftCorporationII.WindowsSubsystemForAndroid_8wekyb3d8bbwe`` to the desired drive/partition, making sure to delete the folder from ``%LOCALAPPDATA%\Packages\`` after copying
|
||||||
|
|
||||||
|
- **2.)** Open Command Prompt (Admin) through Windows Terminal (Admin) or directly and run the command:
|
||||||
|
```shell
|
||||||
|
mklink /J "%LOCALAPPDATA%\Packages\MicrosoftCorporationII.WindowsSubsystemForAndroid_8wekyb3d8bbwe" "Location_Of_Folder_In_Other_Drive"
|
||||||
|
```
|
||||||
|
Replacing Location_Of_Folder_In_Other_Drive with the location of the folder named ``MicrosoftCorporationII.WindowsSubsystemForAndroid_8wekyb3d8bbwe``, copied to the desired to the drive/partition in 1st point of Step 3
|
||||||
|
|
||||||
|
- ### Step 4: Testing if everything is working
|
||||||
|
- Run Windows Subsystem For Android™ Settings
|
||||||
|
- If it crashes, you have made a mistake whilst following the guide. Try following it again.
|
||||||
11
MagiskOnWSA/DLL/docs/Guides/Sideloading.md
Normal file
11
MagiskOnWSA/DLL/docs/Guides/Sideloading.md
Normal file
@ -0,0 +1,11 @@
|
|||||||
|
## Guide: Sideloading APKs
|
||||||
|
|
||||||
|
### This guide covers the four different methods of sideloading and installing APKs (from Windows) into Windows Subsystem For Android™
|
||||||
|
|
||||||
|
|Application|
|
||||||
|
|-----------|
|
||||||
|
|[<img src="https://github-production-user-asset-6210df.s3.amazonaws.com/44692189/243088634-38def9fd-e9e0-48da-90d2-85988bb79c6a.png" style="width: 350px;" style="float: left;"/>](WSAFiles.md)|
|
||||||
|
|[<img src="https://user-images.githubusercontent.com/68516357/226143645-0a0ff0df-00f4-4d69-a257-1ffbee039f36.png" style="width: 350px;" style="float: left;"/>](WSA-Sideloader.md)|
|
||||||
|
|[<img src="https://user-images.githubusercontent.com/68516357/226144462-25e8ba07-9f5b-424b-9ecf-b973e8f396b2.png" style="width: 350px;" style="float: left;"/>](WSAPacman.md)|
|
||||||
|
|[<img src="https://user-images.githubusercontent.com/68516357/226143960-70ba58b6-7339-48c8-9f25-602e7236eaf5.png" style="width: 346px;" style="float: left;"/>](ADB-Sideloading.md)|
|
||||||
|
|[<img src="https://user-images.githubusercontent.com/68516357/228315858-1f76e13f-be5a-49c9-8e72-1417b9d6796b.png" style="width: 346px;" style="float: left;"/>](https://github.com/Paving-Base/APK-Installer/blob/main/README.en-US.md#how-to-install-the-apk-installer)|
|
||||||
73
MagiskOnWSA/DLL/docs/Guides/WSA-Sideloader.md
Normal file
73
MagiskOnWSA/DLL/docs/Guides/WSA-Sideloader.md
Normal file
@ -0,0 +1,73 @@
|
|||||||
|
# WSA Sideloader Usage Guide
|
||||||
|
#### With WSA Sideloader, you can install any APK file onto WSA, as well as XAPK, APKM and APKS files.
|
||||||
|
#### This guide will show you how to use it.
|
||||||
|
|
||||||
|
</br>
|
||||||
|
|
||||||
|
</br>
|
||||||
|
|
||||||
|
## How to Download and Install WSA-Sideloader
|
||||||
|
|
||||||
|
#### You can download WSA Sideloader in 3 different ways:
|
||||||
|
Operating System|Downloads
|
||||||
|
|---------|---------|
|
||||||
|
|<img src="https://upload.wikimedia.org/wikipedia/commons/e/e6/Windows_11_logo.svg" style="width: 150px;"/></br><img src="https://upload.wikimedia.org/wikipedia/commons/0/05/Windows_10_Logo.svg" style="width: 150px;"/> |[<img src="https://user-images.githubusercontent.com/49786146/159123331-729ae9f2-4cf9-439b-8515-16a4ef991089.png" style="width: 200px;"/>](https://winstall.app/apps/infinitepower18.WSASideloader)|
|
||||||
|
|<img src="https://upload.wikimedia.org/wikipedia/commons/e/e6/Windows_11_logo.svg" style="width: 150px;"/></br><img src="https://upload.wikimedia.org/wikipedia/commons/0/05/Windows_10_Logo.svg" style="width: 150px;"/> |[<img src="https://user-images.githubusercontent.com/68516357/226141505-c93328f9-d6ae-4838-b080-85b073bfa1e0.png" style="width: 200px;"/>](https://github.com/infinitepower18/WSA-Sideloader/releases/latest)|
|
||||||
|
|<img src="https://upload.wikimedia.org/wikipedia/commons/e/e6/Windows_11_logo.svg" style="width: 150px;"/>|[<img src="https://get.microsoft.com/images/en-us%20dark.svg" style="width: 200px;"/>](https://apps.microsoft.com/store/detail/9NMFSJB25QJR?launch=true&cid=wsabuilds&mode=mini)|
|
||||||
|
|
||||||
|
## Setup
|
||||||
|
|
||||||
|
***Step 1. Once installed, you should see this screen:***
|
||||||
|
|
||||||
|
<img width="311" alt="image" src="https://github.com/infinitepower18/WSA-Sideloader/assets/44692189/ede49229-4667-47b1-ac2d-84f2d71b954f">
|
||||||
|
|
||||||
|
>**Note** :
|
||||||
|
> If you get a message that says WSA is not installed, check that you have downloaded and installed WSA correctly as per the WSABuilds instructions.
|
||||||
|
|
||||||
|
</br>
|
||||||
|
|
||||||
|
***Step 2. Next, open WSA Settings from the start menu or by typing wsa-settings:// in your browser's address bar, select Developer and enable Developer mode.***
|
||||||
|
|
||||||
|
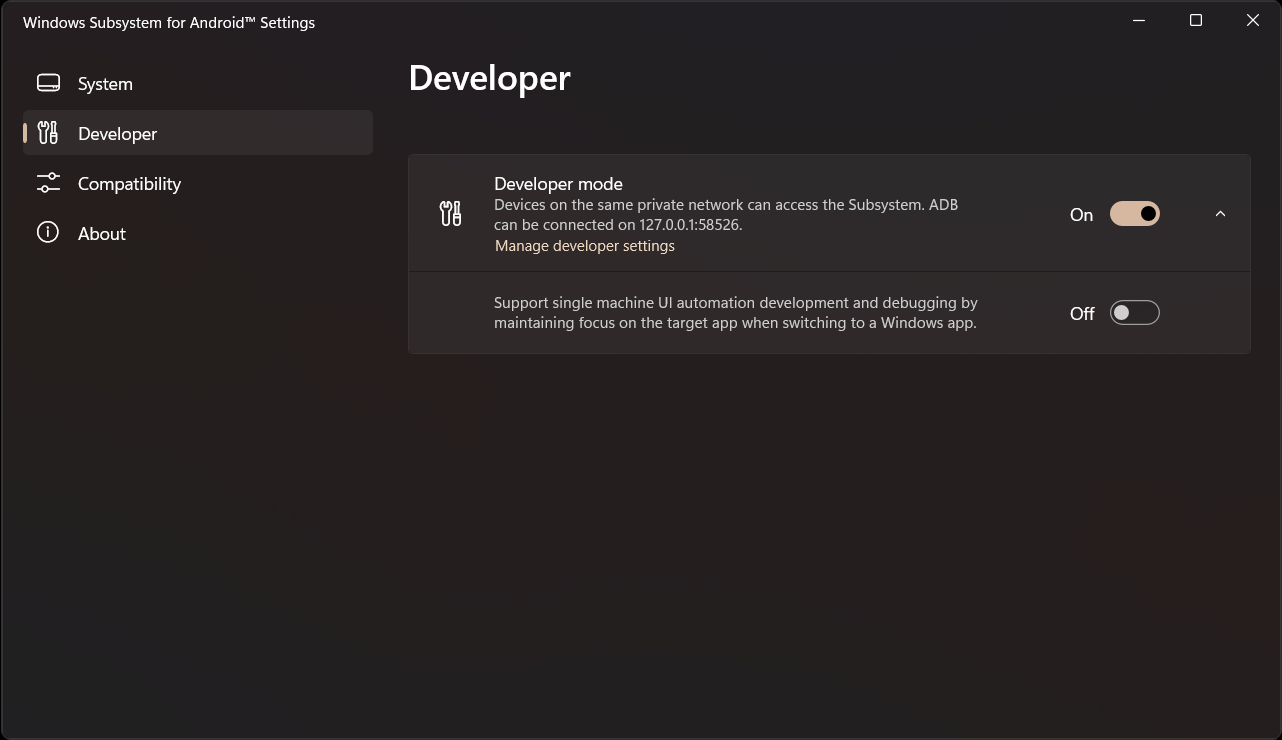
|
||||||
|
|
||||||
|
</br>
|
||||||
|
|
||||||
|
***Step 3. Now, you can click the Browse button to select your APK file. You can also double click a file in File Explorer to automatically open WSA Sideloader with the APK file already selected.***
|
||||||
|
|
||||||
|
<img width="1144" alt="image" src="https://github.com/MustardChef/WSABuilds/assets/44692189/a66efe96-8f0c-4a2c-930d-a9c60c7f1945">
|
||||||
|
|
||||||
|
</br>
|
||||||
|
|
||||||
|
***Step 4. The first time you install an APK, it will ask to allow ADB debugging. Allow it and attempt the installation again. Check the always allow box if you don't want to manually accept the permission every time you install an app.***
|
||||||
|
|
||||||
|
<img width="485" alt="image" src="https://user-images.githubusercontent.com/44692189/226060674-233a60b5-56d7-4dcf-a626-295d21a4c464.png">
|
||||||
|
|
||||||
|
</br>
|
||||||
|
|
||||||
|
***Step 5. It should take a few seconds to install the APK. Once it says `The application has been successfully installed`, you can click Open app. Bundle files may take longer depending on the file size.***
|
||||||
|
|
||||||
|
>**Note** :
|
||||||
|
> If WSA is off, WSA Sideloader will start it for you. After 30 seconds, the installation will automatically continue.
|
||||||
|
|
||||||
|
<img width="314" alt="image" src="https://user-images.githubusercontent.com/44692189/226061387-f0126c32-3a2f-49c4-8ecf-83ad5809ab38.png">
|
||||||
|
|
||||||
|
</br>
|
||||||
|
|
||||||
|
***You can find all your installed WSA apps on the start menu, as well as via the "Installed apps" button in WSA Sideloader:***
|
||||||
|
|
||||||
|
<img width="962" alt="image" src="https://user-images.githubusercontent.com/44692189/226061500-c210ded3-5342-483d-b4b8-c4b683b138a7.png">
|
||||||
|
|
||||||
|
## Updating WSA Sideloader
|
||||||
|
From time to time, there may be updates that improve the reliability of the app, as well as ensuring it works properly with future releases of WSA.
|
||||||
|
|
||||||
|
Therefore, it's highly recommended you keep it up to date.
|
||||||
|
|
||||||
|
- If you installed WSA Sideloader using MS Store, you can update the app via the store.
|
||||||
|
- If you installed through other methods, the sideloader will notify you of an update the next time you launch it.
|
||||||
|
|
||||||
|
## Troubleshooting
|
||||||
|
If you get an error like the one below, check that you have allowed the ADB authorization and enabled Developer Mode. Also try disabling and enabling USB debugging under manage developer settings as that can sometimes fix issues with the ADB connection.
|
||||||
|
|
||||||
|
<img width="446" alt="image" src="https://user-images.githubusercontent.com/44692189/226061768-61743f6c-2ed3-401a-a561-8754c297ad74.png">
|
||||||
|
|
||||||
|
If you get a message saying `No connection could be made because the target machine actively refused it`, follow [this guide](https://github.com/YT-Advanced/WSA-Script/blob/main/docs/Fixes/TargetMachineActivelyRefusedConnection.md)
|
||||||
52
MagiskOnWSA/DLL/docs/Guides/WSAFiles.md
Normal file
52
MagiskOnWSA/DLL/docs/Guides/WSAFiles.md
Normal file
@ -0,0 +1,52 @@
|
|||||||
|
# Sideloading using the Files app
|
||||||
|
|
||||||
|
#### Starting with WSA version 2305, you can sideload APK files using the Files app. This guide will show you how.
|
||||||
|
|
||||||
|
> **NOTE:**
|
||||||
|
> This guide is only applicable for WSA versions 2305 and above. If you're using an older version, you will need to use [ADB](ADB-Sideloading.md) or one of the [listed APK installers](Sideloading.md).
|
||||||
|
|
||||||
|
## Setup
|
||||||
|
|
||||||
|
***1. Open the Windows Subsystem for Android app, go to Advanced Settings and enable share user folders found under experimental features. Then select the folder that you would like to share by clicking on "Change folder".***
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
***2. Go to the "System" section and open the Files app.***
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
***3. Click on Subsystem for Android, followed by Windows to browse through your Windows files.***
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
<img width="962" alt="image" src="https://github.com/MustardChef/WSABuilds/assets/44692189/95885809-deb2-4ac4-b468-7447fb84dde0">
|
||||||
|
|
||||||
|
<br>
|
||||||
|
<br>
|
||||||
|
|
||||||
|
***4. Click the APK you want to install and choose package installer if it asks. Agree to the warnings and then click install.***
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
<img width="443" alt="image" src="https://github.com/MustardChef/WSABuilds/assets/44692189/9e0698de-e47e-45c9-83a0-8c8ea1297cd4">
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
> **NOTE:**
|
||||||
|
> If you're facing problems, try disabling `Block installation of malicious apps` in the WSA app.
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
## After installation
|
||||||
|
|
||||||
|
#### Once installed, you can launch the sideloaded app from the Start Menu.
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
#### If you want to install bundle files, such as .apkm or .xapk, you can install [SAI](https://apkpure.com/split-apks-installer-sai/com.aefyr.sai) and use that to install bundle files, as well as regular APKs.
|
||||||
30
MagiskOnWSA/DLL/docs/Guides/WSAPacman.md
Normal file
30
MagiskOnWSA/DLL/docs/Guides/WSAPacman.md
Normal file
@ -0,0 +1,30 @@
|
|||||||
|
# WSAPacman
|
||||||
|
|
||||||
|
**Step 1:** Download and install [**WSA Pacman**](https://github.com/alesimula/wsa_pacman/releases)
|
||||||
|
|
||||||
|
**Step 2:** Go to `Windows Subsystem for Android` → `Developer` and turn on **Developer mode**.
|
||||||
|
|
||||||
|
> **Warning**:
|
||||||
|
> #### You have to give WSAPacman, ADB Debugging permission.
|
||||||
|
>
|
||||||
|
> 
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## Issues and Solutions
|
||||||
|
|
||||||
|
#### If the "Install" button is greyed out while installing apk
|
||||||
|
|
||||||
|
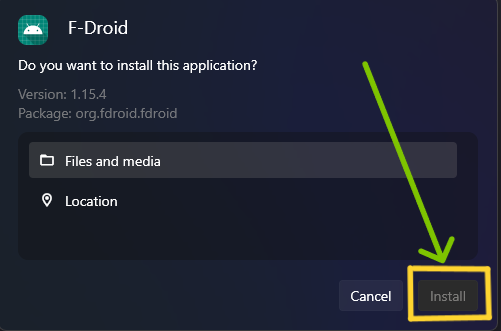
|
||||||
|
|
||||||
|
#### Solution: Open WSAPacman and turn on WSA from there.
|
||||||
|
>
|
||||||
|
|
||||||
|
</br>
|
||||||
|
|
||||||
|
#### If WSAPacman states that the "Installation timed out":
|
||||||
|
|
||||||
|
<img src="https://user-images.githubusercontent.com/68516357/222983664-cf41ac0b-194b-4c11-9b40-2975eea6c176.png" style="width: 350px;"/>
|
||||||
|
|
||||||
|
#### Solution: Wait for a few minutes, and see if the app is installed and shows in the Start Menu. If not retry the installation </br> In the case that nothing works, report this to the [WSAPacman Github](https://github.com/alesimula/wsa_pacman)
|
||||||
419
MagiskOnWSA/DLL/docs/Issues.html
Normal file
419
MagiskOnWSA/DLL/docs/Issues.html
Normal file
@ -0,0 +1,419 @@
|
|||||||
|
<!DOCTYPE html>
|
||||||
|
<html
|
||||||
|
lang="en"
|
||||||
|
data-color-mode="auto"
|
||||||
|
data-light-theme="light"
|
||||||
|
data-dark-theme="dark"
|
||||||
|
data-a11y-animated-images="system"
|
||||||
|
>
|
||||||
|
<head>
|
||||||
|
<meta charset="utf-8" />
|
||||||
|
<link rel="dns-prefetch" href="https://github.githubassets.com" />
|
||||||
|
<link rel="dns-prefetch" href="https://avatars.githubusercontent.com" />
|
||||||
|
<link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com" />
|
||||||
|
<link
|
||||||
|
rel="dns-prefetch"
|
||||||
|
href="https://user-images.githubusercontent.com/"
|
||||||
|
/>
|
||||||
|
<link rel="preconnect" href="https://github.githubassets.com" crossorigin />
|
||||||
|
<link rel="preconnect" href="https://avatars.githubusercontent.com" />
|
||||||
|
|
||||||
|
<link
|
||||||
|
crossorigin="anonymous"
|
||||||
|
media="all"
|
||||||
|
rel="stylesheet"
|
||||||
|
href="https://github.githubassets.com/assets/light-0eace2597ca3.css"
|
||||||
|
/>
|
||||||
|
<link
|
||||||
|
crossorigin="anonymous"
|
||||||
|
media="all"
|
||||||
|
rel="stylesheet"
|
||||||
|
href="https://github.githubassets.com/assets/dark-a167e256da9c.css"
|
||||||
|
/>
|
||||||
|
|
||||||
|
<link
|
||||||
|
crossorigin="anonymous"
|
||||||
|
media="all"
|
||||||
|
rel="stylesheet"
|
||||||
|
href="https://github.githubassets.com/assets/primer-711f412bb361.css"
|
||||||
|
/>
|
||||||
|
<link
|
||||||
|
crossorigin="anonymous"
|
||||||
|
media="all"
|
||||||
|
rel="stylesheet"
|
||||||
|
href="https://github.githubassets.com/assets/global-8215aa0ce496.css"
|
||||||
|
/>
|
||||||
|
|
||||||
|
<script src="https://code.jquery.com/jquery-3.3.1.min.js"></script>
|
||||||
|
<script src="https://cdn.polyfill.io/v3/polyfill.min.js"></script>
|
||||||
|
<!-- <script src="https://fastly.jsdelivr.net/npm/marked/marked.min.js"></script> -->
|
||||||
|
<script type="application/javascript">
|
||||||
|
|
||||||
|
var repo = "YT-Advanced/WSA-Script";
|
||||||
|
|
||||||
|
var cdn = "";
|
||||||
|
|
||||||
|
repo = getRepo(repo);
|
||||||
|
|
||||||
|
cdn = `https://raw.githubusercontent.com/${repo}/main/`;
|
||||||
|
cdn = `https://ghproxy.com/https://raw.githubusercontent.com/${repo}/main/`;
|
||||||
|
//cdn = `https://fastly.jsdelivr.net/gh/${repo}@main/`;
|
||||||
|
//cdn = `https://gcore.jsdelivr.net/gh/${repo}@main/`;
|
||||||
|
//cdn = `https://cdn.statically.io/gh/${repo}/main/`;
|
||||||
|
//cdn = `https://cdn.staticaly.com/gh/${repo}/main/`;
|
||||||
|
|
||||||
|
|
||||||
|
parameter = {
|
||||||
|
"--arch": {
|
||||||
|
"name": "--arch",
|
||||||
|
"description": "Target CPU architecture of WSA.",
|
||||||
|
"detailedinfo": "",
|
||||||
|
"required": true,
|
||||||
|
"default": "x64",
|
||||||
|
"type": "choice",
|
||||||
|
"options": [
|
||||||
|
"x64",
|
||||||
|
"arm64"
|
||||||
|
]
|
||||||
|
},
|
||||||
|
"--release-type": {
|
||||||
|
"name": "--release-type",
|
||||||
|
"description": "WSA Release Channel.",
|
||||||
|
"detailedinfo": "",
|
||||||
|
"required": true,
|
||||||
|
"default": "retail",
|
||||||
|
"type": "choice",
|
||||||
|
"options": [
|
||||||
|
"retail",
|
||||||
|
"latest",
|
||||||
|
"RP",
|
||||||
|
"WIS",
|
||||||
|
"WIF"
|
||||||
|
]
|
||||||
|
},
|
||||||
|
"--root-sol": {
|
||||||
|
"name": "--root-sol",
|
||||||
|
"description": "Root solution.",
|
||||||
|
"detailedinfo": "None for no integration of root.",
|
||||||
|
"required": true,
|
||||||
|
"default": "magisk",
|
||||||
|
"type": "choice",
|
||||||
|
"options": [
|
||||||
|
"magisk",
|
||||||
|
"kernelsu",
|
||||||
|
"none"
|
||||||
|
]
|
||||||
|
},
|
||||||
|
"--magisk-branch": {
|
||||||
|
"name": "--magisk-branch",
|
||||||
|
"description": "Magisk branch.",
|
||||||
|
"detailedinfo": "",
|
||||||
|
"required": true,
|
||||||
|
"default": "magisk",
|
||||||
|
"type": "choice",
|
||||||
|
"options": [
|
||||||
|
"topjohnwu",
|
||||||
|
"HuskyDG",
|
||||||
|
"vvb2060"
|
||||||
|
]
|
||||||
|
},
|
||||||
|
"--magisk-ver": {
|
||||||
|
"name": "--magisk-ver",
|
||||||
|
"description": "Magisk version.",
|
||||||
|
"detailedinfo": "",
|
||||||
|
"required": true,
|
||||||
|
"default": "stable",
|
||||||
|
"type": "choice",
|
||||||
|
"options": [
|
||||||
|
"stable",
|
||||||
|
"beta",
|
||||||
|
"canary",
|
||||||
|
"debug"
|
||||||
|
]
|
||||||
|
},
|
||||||
|
"--compress-format": {
|
||||||
|
"name": "--compress-format",
|
||||||
|
"description": "Compression algorithms",
|
||||||
|
"detailedinfo": "Compress format of output file.",
|
||||||
|
"required": true,
|
||||||
|
"default": "7z",
|
||||||
|
"type": "choice",
|
||||||
|
"options": [
|
||||||
|
"7z",
|
||||||
|
"zip"
|
||||||
|
]
|
||||||
|
},
|
||||||
|
"--install-gapps": {
|
||||||
|
"name": "--install-gapps",
|
||||||
|
"description": "Install MindTheGapps into the system.",
|
||||||
|
"detailedinfo": "",
|
||||||
|
"required": false,
|
||||||
|
"default": true,
|
||||||
|
"type": "boolean"
|
||||||
|
},
|
||||||
|
"--remove-amazon": {
|
||||||
|
"name": "--remove-amazon",
|
||||||
|
"description": "Remove Amazon Appstore from the system.",
|
||||||
|
"detailedinfo": "",
|
||||||
|
"required": false,
|
||||||
|
"default": true,
|
||||||
|
"type": "boolean"
|
||||||
|
}
|
||||||
|
};
|
||||||
|
|
||||||
|
function getRepo(repo) {
|
||||||
|
var url = document.location.toString();
|
||||||
|
var arr = url.split("?")[0].split("/");
|
||||||
|
if (arr.length > 1) {
|
||||||
|
for (var i = 0; i < arr.length; i++) {
|
||||||
|
if (
|
||||||
|
arr[i].indexOf(".github.io") >= 0 &&
|
||||||
|
i + 1 < arr.length &&
|
||||||
|
arr[i + 1].length > 0
|
||||||
|
) {
|
||||||
|
return arr[i].replace(".github.io", "") + "/" + arr[i + 1];
|
||||||
|
}
|
||||||
|
}
|
||||||
|
}
|
||||||
|
return repo;
|
||||||
|
}
|
||||||
|
|
||||||
|
function getUrlParam(paraName) {
|
||||||
|
var url = document.location.toString();
|
||||||
|
var arrObj = url.split("?");
|
||||||
|
if (arrObj.length > 1) {
|
||||||
|
var arrPara = arrObj[1].split("&");
|
||||||
|
var arr;
|
||||||
|
for (var i = 0; i < arrPara.length; i++) {
|
||||||
|
arr = arrPara[i].split("=");
|
||||||
|
if (arr != null && arr[0] == paraName) {
|
||||||
|
return arr[1];
|
||||||
|
}
|
||||||
|
}
|
||||||
|
}
|
||||||
|
return "";
|
||||||
|
}
|
||||||
|
|
||||||
|
function httpGetAsync(theUrl, callback) {
|
||||||
|
let xmlHttpReq = new XMLHttpRequest();
|
||||||
|
xmlHttpReq.onreadystatechange = function () {
|
||||||
|
if (xmlHttpReq.readyState == 4 && xmlHttpReq.status == 200)
|
||||||
|
callback(xmlHttpReq.responseText);
|
||||||
|
};
|
||||||
|
xmlHttpReq.open("GET", theUrl, true); // true for asynchronous
|
||||||
|
xmlHttpReq.send(null);
|
||||||
|
}
|
||||||
|
|
||||||
|
window.onload = function () {
|
||||||
|
setTitle();
|
||||||
|
|
||||||
|
$("#inputs").find("div").remove(); //html('');
|
||||||
|
var html = "";
|
||||||
|
for (var key in parameter) {
|
||||||
|
//console.log(key, result[key]);
|
||||||
|
html += createInput(parameter[key]);
|
||||||
|
}
|
||||||
|
$("#inputs").prepend(html);
|
||||||
|
|
||||||
|
};
|
||||||
|
|
||||||
|
function setTitle() {
|
||||||
|
document.title = repo;
|
||||||
|
$("#titleA")[0].href = `https://github.com/${repo}`;
|
||||||
|
$("#titleA")[0].innerText = repo.substring(repo.indexOf("/") + 1);
|
||||||
|
}
|
||||||
|
|
||||||
|
function createInput(data) {
|
||||||
|
var html = "";
|
||||||
|
|
||||||
|
var name = "";
|
||||||
|
var desc = "";
|
||||||
|
var type = "";
|
||||||
|
var dft = "";
|
||||||
|
var req = "";
|
||||||
|
var info = "";
|
||||||
|
if (data.hasOwnProperty("name")) name = data.name;
|
||||||
|
if (data.hasOwnProperty("description")) desc = data.description;
|
||||||
|
if (data.hasOwnProperty("type")) type = data.type;
|
||||||
|
if (data.hasOwnProperty("default")) dft = data.default;
|
||||||
|
if (data.hasOwnProperty("required")) req = data.required;
|
||||||
|
if (data.hasOwnProperty("detailedinfo")) info = data.detailedinfo;
|
||||||
|
|
||||||
|
if (type == "choice") {
|
||||||
|
var par = "";
|
||||||
|
var valname = {"none":"None","x64":"x64","arm64":"ARM64","retail":"Retail","RP":"Release Preview","WIS":"Insider Slow (Beta)","WIF":"Insider Fast (Dev)","latest":"WSA Insider","stable":"Magisk Stable","beta":"Magisk Beta","canary":"Magisk Canary","debug":"Magisk Debug","topjohnwu":"Magisk Official","HuskyDG":"Magisk Delta (HuskyDG)","vvb2060":"Magisk Alpha (vvb2060)","magisk":"Magisk","kernelsu":"KernelSU","zip":".zip","7z":".7z"};
|
||||||
|
if (req) par = "required";
|
||||||
|
html += `<div class="form-group mt-1 mb-2 ${par}"><div class="form-group-header"><label class="color-fg-default text-mono f6" for="${name}">${name}</label></div><div class="form-group-body">`;
|
||||||
|
html += `<select class="form-select form-control select-sm input-contrast" id="${name}" required="" name="inputs[${name}]" value="'${dft}'">`;
|
||||||
|
var opts = [];
|
||||||
|
if (data.hasOwnProperty("options")) opts = data.options;
|
||||||
|
for (var v in opts) {
|
||||||
|
var addpar = "";
|
||||||
|
if (opts[v] == dft) addpar = 'selected="selected"';
|
||||||
|
html += `<option ${addpar} value="${opts[v]}">${valname[opts[v]]}</option>`;
|
||||||
|
}
|
||||||
|
html += `</select>`;
|
||||||
|
html += `<label class="js-navigation-open Link--primary" title="${info}" data-pjax="#repo-content-pjax-container" data-turbo-frame="repo-content-turbo-frame" href="#">: ${desc}</label>`;
|
||||||
|
html += `</div></div>`;
|
||||||
|
} else if (type == "boolean") {
|
||||||
|
var par = "";
|
||||||
|
var addpar = "";
|
||||||
|
if (dft) addpar += ' checked="checked"';
|
||||||
|
html += `<div class="form-group mt-1 mb-2"><div class="form-group-header"><label class="color-fg-default text-mono f6" for="${name}">${name}${par}</label></div><div class="form-group-body">`;
|
||||||
|
html += `<div class="form-checkbox my-0"><label class="color-fg-default text-mono f6 sm"><input type="checkbox" id="${name}" name="inputs[${name}]" value="${name}" ${addpar}/></label>`;
|
||||||
|
html += `<label class="js-navigation-open Link--primary" title="${info}" data-pjax="#repo-content-pjax-container" data-turbo-frame="repo-content-turbo-frame" href="#">: ${desc}</label>`;
|
||||||
|
html += `</label></div></div>`;
|
||||||
|
} else {
|
||||||
|
}
|
||||||
|
return html;
|
||||||
|
}
|
||||||
|
|
||||||
|
function processext(ext) {
|
||||||
|
var obj = $("#ext_btn_" + ext.replace(/\./g, "·"));
|
||||||
|
var exts = $("#ext").val().split(",");
|
||||||
|
if (obj.hasClass("btn-danger")) {
|
||||||
|
//要删除掉已经输入的内容
|
||||||
|
exts.map((val, i) => {
|
||||||
|
if (val === ext) {
|
||||||
|
exts.splice(i, 1);
|
||||||
|
}
|
||||||
|
});
|
||||||
|
obj.removeClass("btn-danger");
|
||||||
|
} else {
|
||||||
|
obj.addClass("btn-danger");
|
||||||
|
exts.push(ext);
|
||||||
|
}
|
||||||
|
exts.map((val, i) => {
|
||||||
|
if (val === "") {
|
||||||
|
exts.splice(i, 1);
|
||||||
|
}
|
||||||
|
});
|
||||||
|
$("#ext").val(exts.join(","));
|
||||||
|
}
|
||||||
|
|
||||||
|
function createIssues() {
|
||||||
|
var form = document.getElementById("inputs");
|
||||||
|
let formData = new FormData(form);
|
||||||
|
var title = "Custom WSA Build Do not edit this";
|
||||||
|
var body = "";
|
||||||
|
|
||||||
|
for (var key in parameter) {
|
||||||
|
var name = parameter[key]["name"];
|
||||||
|
var type = parameter[key]["type"];
|
||||||
|
if (name == "title") {
|
||||||
|
if (formData.get(`inputs[${name}]`)) {
|
||||||
|
title += " " + formData.get(`inputs[${name}]`);
|
||||||
|
} else {
|
||||||
|
title += " " + new Date().toISOString().substr(0, 10);
|
||||||
|
}
|
||||||
|
continue;
|
||||||
|
}
|
||||||
|
if (formData.get(`inputs[${name}]`)) {
|
||||||
|
if (type == "choice") {
|
||||||
|
body += " " + name + " " + formData.get(`inputs[${name}]`);
|
||||||
|
} else if (type == "boolean") {
|
||||||
|
body += " " + name;
|
||||||
|
} else {
|
||||||
|
|
||||||
|
}
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
window.location.href = `https://github.com/${repo}/issues/new?title=${title}&body=${body}`;
|
||||||
|
}
|
||||||
|
</script>
|
||||||
|
|
||||||
|
<title></title>
|
||||||
|
</head>
|
||||||
|
|
||||||
|
<body
|
||||||
|
class="logged-in env-production page-responsive"
|
||||||
|
style="word-wrap: break-word"
|
||||||
|
>
|
||||||
|
<div
|
||||||
|
class="application-main left-0 text-left p-3 mx-auto container-xl px-3 px-md-4 px-lg-5 mt-4"
|
||||||
|
>
|
||||||
|
<pre
|
||||||
|
id="logoP"
|
||||||
|
style="
|
||||||
|
display: block;
|
||||||
|
font-family: ui-monospace, SFMono-Regular, SF Mono, Menlo, Consolas,
|
||||||
|
Liberation Mono, monospace !important;
|
||||||
|
font-size: 12px !important;
|
||||||
|
line-height: 12px !important;
|
||||||
|
margin: 15px 10px;
|
||||||
|
color: red;
|
||||||
|
"
|
||||||
|
>
|
||||||
|
██╗ ██╗███████╗ █████╗ ██████╗ ██╗ ██╗██╗██╗ ██████╗
|
||||||
|
██║ ██║██╔════╝██╔══██╗ ██╔══██╗██║ ██║██║██║ ██╔══██╗
|
||||||
|
██║ █╗ ██║███████╗███████║ ██████╔╝██║ ██║██║██║ ██║ ██║
|
||||||
|
██║███╗██║╚════██║██╔══██║ ██╔══██╗██║ ██║██║██║ ██║ ██║
|
||||||
|
╚███╔███╔╝███████║██║ ██║ ██████╔╝╚██████╔╝██║███████╗██████╔╝
|
||||||
|
╚══╝╚══╝ ╚══════╝╚═╝ ╚═╝ ╚═════╝ ╚═════╝ ╚═╝╚══════╝╚═════╝
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
</pre>
|
||||||
|
<div class="flex-auto min-width-0 width-fit mr-3">
|
||||||
|
<div
|
||||||
|
class="d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"
|
||||||
|
>
|
||||||
|
<svg
|
||||||
|
aria-hidden="true"
|
||||||
|
height="16"
|
||||||
|
viewBox="0 0 16 16"
|
||||||
|
version="1.1"
|
||||||
|
width="16"
|
||||||
|
data-view-component="true"
|
||||||
|
class="octicon octicon-repo color-fg-muted mr-2"
|
||||||
|
>
|
||||||
|
<path
|
||||||
|
fill-rule="evenodd"
|
||||||
|
d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"
|
||||||
|
></path>
|
||||||
|
</svg>
|
||||||
|
<strong itemprop="name" class="mr-2 flex-self-stretch">
|
||||||
|
<a
|
||||||
|
id="titleA"
|
||||||
|
data-pjax="#repo-content-pjax-container"
|
||||||
|
data-turbo-frame="repo-content-turbo-frame"
|
||||||
|
href="#"
|
||||||
|
></a>
|
||||||
|
</strong>
|
||||||
|
</div>
|
||||||
|
</div>
|
||||||
|
<div data-replace-remote-form-target="" class="workflow-dispatch">
|
||||||
|
<form id="inputs">
|
||||||
|
<button
|
||||||
|
type="button"
|
||||||
|
class="btn State--merged"
|
||||||
|
onclick="return createIssues()"
|
||||||
|
autofocus=""
|
||||||
|
>
|
||||||
|
Create Issue
|
||||||
|
</button>
|
||||||
|
</form>
|
||||||
|
</div>
|
||||||
|
</div>
|
||||||
|
<footer
|
||||||
|
class="footer width-full container-xl mt-3 text-center color-fg-muted"
|
||||||
|
>
|
||||||
|
<a
|
||||||
|
aria-label="Homepage"
|
||||||
|
title="GitHub"
|
||||||
|
class="footer-octicon mr-2"
|
||||||
|
href="https://github.com/YT-Advanced"
|
||||||
|
>
|
||||||
|
<img
|
||||||
|
class="avatar rounded-2 avatar-user"
|
||||||
|
src="https://avatars.githubusercontent.com/u/70064328?v=4"
|
||||||
|
width="40"
|
||||||
|
height="40"
|
||||||
|
alt="@wjz304"
|
||||||
|
/>
|
||||||
|
</a>
|
||||||
|
<span> Copyright © 2023 YT-Advanced</span>
|
||||||
|
</footer>
|
||||||
|
</body>
|
||||||
|
</html>
|
||||||
461
MagiskOnWSA/DLL/docs/README.md
Normal file
461
MagiskOnWSA/DLL/docs/README.md
Normal file
@ -0,0 +1,461 @@
|
|||||||
|
# WSA-Script
|
||||||
|
## MagiskOnWSA (For Windows™ 10 and 11) by [@YT-Advanced](https://github.com/YT-Advanced/)
|
||||||
|
### Windows Subsystem For Android™ (WSA) with Google Play Services and Magisk
|
||||||
|
|
||||||
|
<details>
|
||||||
|
<summary><h3> ❓Want to build your custom build❓ <h3></summary>
|
||||||
|
|
||||||
|
|
||||||
|
| :exclamation: **Important:** `⚠️DO NOT FORK⚠️` |
|
||||||
|
|------------------------------------------------------------------------|
|
||||||
|
|**This repository is designed specifically not to be forked. MagiskOnWSA and some of the various forks and clones that have sprung up on the platform (***potentially***) violate GitHub's Terms of Service due to abuse of GitHub Actions and have been ultimately warned, disabled or banned.**|
|
||||||
|
|**Therefore, don't fork this repository unless you're a developer and want to modify the code itself and/or want to contribute to this Github repository.**|
|
||||||
|
|**If you want to create your Custom Build, please follow the instructions set out clearly, to avoid the repo from being taken down as a result of a misuse of Github Actions due to the large number of forks. AND ALSO if you want to build with Latest Insider version, please skip the first 7 steps**|
|
||||||
|
|
||||||
|
#### **1. Star this repos (I will happy if you do that)**
|
||||||
|
|
||||||
|
#### **2. Check the version from [Releases](https://github.com/YT-Advanced/WSA-Script/releases/) first. If it does not have the version you want, continue to follow this guide. If it does, then feel free to use those prebuild WSA builds**
|
||||||
|
|
||||||
|
#### **3. Open [this page directly](https://YT-Advanced.github.io/WSA-Script) then choose the option that you want to build**
|
||||||
|
|
||||||
|
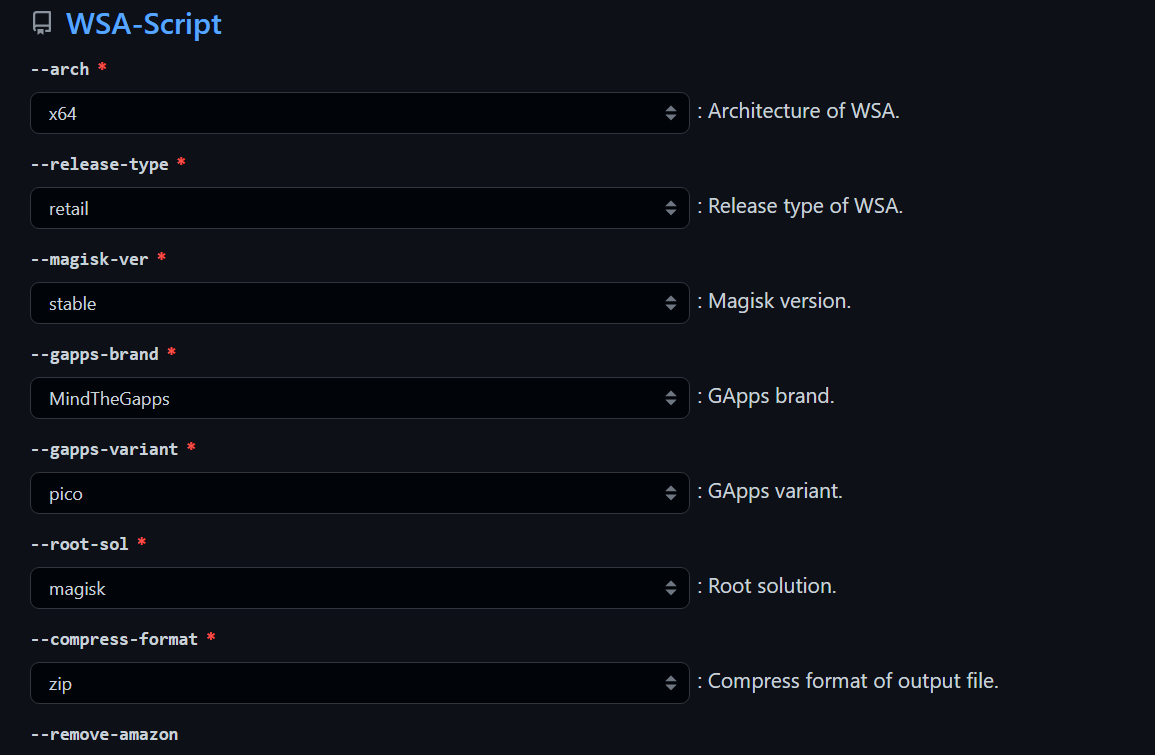
|
||||||
|
|
||||||
|
#### **4. Click "Create Issues" Button, the issues page will be generated and open. Then you click "Submit New Issues" (green button) and wait.**
|
||||||
|
|
||||||
|
|
||||||
|
#### **5. After about 10 minutes, the bot will reply that the workflow have built successfully (like the picture below), OPEN THE LINK BELOW THE BOT COMMENT**
|
||||||
|
|
||||||
|
|
||||||
|
#### **6. Download the package as artifact**
|
||||||
|
**DO NOT download it via multithread downloaders like IDM**
|
||||||
|
|
||||||
|
|
||||||
|
#### **7. Install like normal using [the instructions](https://github.com/YT-Advanced/WSA-Script#--installation) in this repository** and most important of all....
|
||||||
|
|
||||||
|
</details>
|
||||||
|
|
||||||
|
## Downloads
|
||||||
|
|
||||||
|
<table>
|
||||||
|
<thead>
|
||||||
|
<tr>
|
||||||
|
<th>Click to Download</th>
|
||||||
|
<th>Differences</th>
|
||||||
|
<th>Current Version</th>
|
||||||
|
<th>Date</th>
|
||||||
|
</tr>
|
||||||
|
</thead>
|
||||||
|
<tbody>
|
||||||
|
<tr>
|
||||||
|
<td><a href=https://github.com/YT-Advanced/WSA-Script/releases/tag/WSA-Insider-Version><img src="https://img.shields.io/badge/Pre--Release%20Builds-orange?style=for-the-badge" height="28"></a></td>
|
||||||
|
<td>Follows the "WSA Preview Program Channel" </br> </br> Builds are generally newer than the "WSA Retail" and "Insider Fast Channel"</td>
|
||||||
|
<td>2311.40000.5.0<br></td>
|
||||||
|
<td>Builds Released: 05/01/2024</td>
|
||||||
|
</tr>
|
||||||
|
<tr>
|
||||||
|
<td><a href=https://github.com/YT-Advanced/WSA-Script/releases/latest><img src="https://img.shields.io/badge/Stable%20Builds-blue?style=for-the-badge" alt="Image" height="28"></a></td>
|
||||||
|
<td>Follows the "WSA Retail Channel" <br><br> Builds are generally more stable than the builds in the "WSA Preview Program Channel" </td>
|
||||||
|
<td>2311.40000.5.0<br></td>
|
||||||
|
<td>Builds Released: 05/01/2024</td>
|
||||||
|
</tr>
|
||||||
|
<tr>
|
||||||
|
<td colspan="4"><h4>It is recommend to check this table regularly to see if there is a newer update avaliable for WSA for the Stable Builds and Pre-Release Builds<h4></td>
|
||||||
|
</tr>
|
||||||
|
</tbody>
|
||||||
|
</table>
|
||||||
|
|
||||||
|
## Requirements
|
||||||
|
|
||||||
|
<center><table>
|
||||||
|
<thead>
|
||||||
|
<tr>
|
||||||
|
<th></th>
|
||||||
|
<th><img src="https://upload.wikimedia.org/wikipedia/commons/e/e6/Windows_11_logo.svg" style="width: 200px;"/></th>
|
||||||
|
<th><img src="https://upload.wikimedia.org/wikipedia/commons/0/05/Windows_10_Logo.svg" style="width: 200px;"/></th>
|
||||||
|
</tr>
|
||||||
|
</thead>
|
||||||
|
<tbody>
|
||||||
|
<tr>
|
||||||
|
<td><img style="float: right;" src="https://img.icons8.com/fluency/96/null/windows-update--v1.png" width="60" height="60"/><h4>Windows Build Number<h4></td>
|
||||||
|
<td>Windows™ 11: Build 22000.526 or higher.</td>
|
||||||
|
<td>Windows™ 10: 22H2 10.0.19042.2604 or higher. <br /><br /><b>To use WSA, you must install <a href="https://www.catalog.update.microsoft.com/Search.aspx?q=KB5014032" target="_blank" rel="noopener noreferrer">KB5014032</a> then install <a href="https://www.catalog.update.microsoft.com/Search.aspx?q=KB5022834" target="_blank" rel="noopener noreferrer">KB5022834</a> to use WSA on these Windows 10 builds<b><br /><br /><b></td>
|
||||||
|
</tr>
|
||||||
|
<tr>
|
||||||
|
<td><img style="float: right;" src="https://img.icons8.com/external-smashingstocks-flat-smashing-stocks/66/null/external-RAM-technology-and-devices-smashingstocks-flat-smashing-stocks.png" width="60" height="60"/><h4>RAM<h4></td>
|
||||||
|
<td colspan="2"><ul><li>4 to 6 GB (Not Recommended)</li><li>8 GB (Minimum)</li><li>16 GB (Recommended)</li></ul></td>
|
||||||
|
</tr>
|
||||||
|
<tr>
|
||||||
|
<td><img style="float: right;" src="https://img.icons8.com/3d-fluency/94/null/electronics.png" width="60" height="60"/><h4>Processor<h4></td>
|
||||||
|
<td>Your PC should meet the basic Windows™ 11 requirements i.e Core i3 8th Gen, Ryzen 3000, Snapdragon 8c, or above</td>
|
||||||
|
<td>N/A </br></br> This is a bit of a hit or miss, but it is highly recommended that your processor is listed in the <a href="https://learn.microsoft.com/en-gb/windows-hardware/design/minimum/windows-processor-requirements" target="_blank" rel="noopener noreferrer">supported CPU lists for Windows 11 requirements</a></td>
|
||||||
|
</tr>
|
||||||
|
<tr>
|
||||||
|
<td><img style="float: right;" src="https://img.icons8.com/3d-fluency/94/null/video-card.png" width="60" height="60"/><h4>GPU<h4></td>
|
||||||
|
<td colspan="2">Any compatible Intel, AMD or Nvidia GPU. <br /> GPU Performance may vary depending on its compatibility with Windows Subsystem For Android™ <br /</td>
|
||||||
|
</tr>
|
||||||
|
<tr>
|
||||||
|
<td rowspan="2"><img style="float: right;" src="https://img.icons8.com/3d-fluency/94/null/ssd.png" width="60" height="60"/><h4>Storage<h4></td>
|
||||||
|
<td colspan="2">Solid-state drive (SSD) (RECOMMENDED) <br />OR</br> Hard Disk Drive (HDD) (NOT RECOMMENDED)</td>
|
||||||
|
</tr>
|
||||||
|
<tr>
|
||||||
|
<td colspan="2"><b><i>Minimum Storage Requirements: You must have at least 10GB free on the system drive (C:\)<b><i></td>
|
||||||
|
</tr>
|
||||||
|
<tr>
|
||||||
|
<td><img style="float: right;" src="https://img.icons8.com/stickers/100/null/storage.png" width="60" height="60"/><h4>Partition<h4></td>
|
||||||
|
<td colspan="2"><b><i>NTFS ONLY<b><i> <br /><br /> Windows Subsystem For Android™ can only be installed on a NTFS partition, not on an exFAT partition</td>
|
||||||
|
</tr>
|
||||||
|
<tr>
|
||||||
|
<td rowspan="5"><img style="float: left;" src="https://user-images.githubusercontent.com/68516357/230764789-ad8f7361-4a3b-49a8-a8e9-24fdc87d5781.png" width="66" height="58"/><h4>Windows Features Needed<h4></td>
|
||||||
|
<td colspan="2">Virtual Machine Platform Enabled : <b>Require!!</b></td>
|
||||||
|
</tr>
|
||||||
|
<tr>
|
||||||
|
<td colspan="2">Windows Hypervisor Platform Enabled (Optional)</td>
|
||||||
|
</tr>
|
||||||
|
<tr>
|
||||||
|
<td colspan="2">Windows Subsystem For Linux™ Enabled (Optional)</td>
|
||||||
|
</tr>
|
||||||
|
<tr>
|
||||||
|
<td colspan="2">Hyper-V Enabled (Optional)</td>
|
||||||
|
</tr>
|
||||||
|
<tr>
|
||||||
|
<td colspan="2"><b><i>These optional settings are for virtualization and provide components that are needed to run WSA. You can enable these settings by pressing the Windows Key + R on your keyboard and typing "OptionalFeatures.exe" into the box, pressing enter and selecting the features above followed by pressing apply<b><i></td>
|
||||||
|
</tr>
|
||||||
|
<tr>
|
||||||
|
<td><img style="float: right;" src="https://user-images.githubusercontent.com/68516357/230759907-5d11950e-1b17-4811-8f4e-a0f82e598079.png" width="60" height="60"/><h4>Virtualization<h4></td>
|
||||||
|
<td colspan="2">The Computer must support virtualization and be enabled in BIOS/UEFI and Optional Features. </br> <h3><a href="https://support.microsoft.com/en-us/windows/enable-virtualization-on-windows-11-pcs-c5578302-6e43-4b4b-a449-8ced115f58e1" target="_blank" rel="noopener noreferrer">Guide on how to enable</a><h3></td>
|
||||||
|
</tr>
|
||||||
|
</tbody>
|
||||||
|
</table>
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
<details>
|
||||||
|
<summary><picture><img style="float: right;" src="https://img.icons8.com/color/96/null/software-installer.png" width="60" height="60"/></picture><h1> Installation<h1></summary>
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
> **Note** :
|
||||||
|
> If you have the official Windows Subsystem For Android™ installed, you must [completely uninstall](#uninstallation) it to use MagiskOnWSA.
|
||||||
|
|
||||||
|
> In case you want to preserve your data from the previous installation (official or MagiskOnWSA), you can backup `%LOCALAPPDATA%\Packages\MicrosoftCorporationII.WindowsSubsystemForAndroid_8wekyb3d8bbwe\LocalCache\userdata.vhdx` before uninstallation and restore it after installation. For a more comprehensive and detailed guide, take a look at the **Backup and Restore section** in this README markdown
|
||||||
|
|
||||||
|
1. Go to the [Releases page](https://github.com/YT-Advanced/WSA-Script/releases/latest)
|
||||||
|
2. In the latest release, go to the Assets section and download the Windows Subsystem For Android™ version of your choosing (do not download "Source code")
|
||||||
|
|
||||||
|
> **Note** :
|
||||||
|
> If you want to download WSA with Magisk Delta, please go to [](https://github.com/YT-Advanced/WSA-Script/actions/workflows/custom_build.yml) and download the package from the Action.
|
||||||
|
|
||||||
|
3. Check integrity of downloaded file by [Follow this guide](Guides/Checksum.md)
|
||||||
|
4. Extract the zip file
|
||||||
|
5. Delete the zip file
|
||||||
|
6. Move the newly extracted folder to a suitable location (Documents folder is a good choice), as you will need to keep the folder on your PC to use MagiskOnWSA
|
||||||
|
|
||||||
|
> **Note** :
|
||||||
|
> If you're updating WSA, merge the folders and replace the files for all items when asked
|
||||||
|
|
||||||
|
7. Open the Windows Subsystem For Android™ folder: Search for and double-click `Run.bat`
|
||||||
|
- If you previously have a MagiskOnWSA installation, it will automatically uninstall the previous one while preserving all user data and install the new one, so don't worry about your data.
|
||||||
|
- If the popup windows disappear without asking administrative permission and Windows Subsystem For Android™ is not installed successfully, you should manually run Install.ps1 as administrator:
|
||||||
|
|
||||||
|
- Press `Win+X` and select **Windows™ Terminal (Admin)**
|
||||||
|
|
||||||
|
- Input the command below and press enter, replacing {X:\path\to\your\extracted\folder} including the {} with the path of the extracted folder
|
||||||
|
```Powershell
|
||||||
|
cd "{X:\path\to\your\extracted\folder}"
|
||||||
|
```
|
||||||
|
|
||||||
|
- Input the command below and press enter
|
||||||
|
```Powershell
|
||||||
|
PowerShell.exe -ExecutionPolicy Bypass -File .\Install.ps1
|
||||||
|
```
|
||||||
|
|
||||||
|
- The script will run and Windows Subsystem For Android™ will be installed
|
||||||
|
- If this workaround does not work, your PC is not supported for WSA
|
||||||
|
|
||||||
|
8. Once the installation process completes, Windows Subsystem For Android™ will launch (if this is a first-time install, a window asking for consent to diagnositic information will be shown instead. Sometimes two identical windows will show, this is fine and nothing bad happens if you click OK in both windows)
|
||||||
|
9. Click on the PowerShell window, then press any key on the keyboard, the PowerShell window should close
|
||||||
|
10. Close File Explorer
|
||||||
|
11. **Enjoy**
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
### Notice (Applicable for both Windows 10 and 11):
|
||||||
|
|
||||||
|
1. You can NOT delete the Windows Subsystem For Android™ installation folder.
|
||||||
|
What `Add-AppxPackage -Register .\AppxManifest.xml` does is to register an appx package with some existing unpackaged files,
|
||||||
|
so you need to keep them as long as you want to use Windows Subsystem For Android™.
|
||||||
|
Check https://learn.microsoft.com/en-us/powershell/module/appx/add-appxpackage?view=windowsserver2022-ps for more details.
|
||||||
|
2. You need to register your Windows Subsystem For Android™ appx package before you can run Windows Subsystem For Android™.
|
||||||
|
For [WSA-Script](https://github.com/YT-Advanced/WSA-Script) and [MagiskOnWSALocal](https://github.com/LSPosed/MagiskOnWSALocal) users, you need to run `Run.bat` in the extracted dir.
|
||||||
|
If the script fails, you can take the following steps for diagnosis (admin privilege required):
|
||||||
|
1. Open a PowerShell window and change working directory to your Windows Subsystem For Android™ directory.
|
||||||
|
|
||||||
|
2. Run the command below in PowerShell. This should fail with an ActivityID, which is a UUID required for the next step.
|
||||||
|
```Powershell
|
||||||
|
Add-AppxPackage -ForceApplicationShutdown -ForceUpdateFromAnyVersion -Register .\AppxManifest.xml
|
||||||
|
```
|
||||||
|
|
||||||
|
3. Run the command below in PowerShell. This should print the log of the failed operation.
|
||||||
|
```Powershell
|
||||||
|
Get-AppPackageLog -ActivityID <UUID>
|
||||||
|
```
|
||||||
|
4. Check the log for the reason of failure and fix it.
|
||||||
|
|
||||||
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
<details>
|
||||||
|
<summary><picture><img style="float: right;" src="https://img.icons8.com/external-flaticons-flat-flat-icons/64/null/external-updating-tools-and-material-ecommerce-flaticons-flat-flat-icons.png" width="60" height="60"/></picture><h1> Updating<h1></summary>
|
||||||
|
|
||||||
|
### How do I update without losing any of my apps and data on Windows Subsystem for Android (WSA)
|
||||||
|
|
||||||
|
1. [Download the latest build](https://github.com/YT-Advanced/WSA-Script/releases/latest) (that you want to update to)
|
||||||
|
2. Make sure Windows Subsystem For Android is not running (Click on "Turn off" in the WSA Settings and wait for the spinning loader to disappear)
|
||||||
|
2. Using 7-Zip, WinRAR or any other tool of choice, open the .zip file
|
||||||
|
3. Within the .zip archive open the subfolder (Example: WSA_2xxx.xxxxx.xx.x_x64_Release-Nightly-with-magisk-xxxxxxx-MindTheGapps-13.0-as-Pixel-5-RemovedAmazon)
|
||||||
|
4. Select all the files that are within this subfolder and extract them to the current folder where the file for Windows Subsystem For Android are (the folder you extracted, and installed WSA from)
|
||||||
|
5. When prompted to replace folders, select "Do this for all current items" and click on "Yes"
|
||||||
|
6. When prompted to replace files, click on "Replace the files in the destination"
|
||||||
|
7. Run the ``Run.bat`` file
|
||||||
|
8. Launch Windows Subsystem For Android Settings app and go to the ``About`` tab using the sidebar
|
||||||
|
9. Check if the WSA version matches the latest version/ the version number that you want to update to
|
||||||
|
|
||||||
|
|
||||||
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
<details>
|
||||||
|
<summary><picture><img style="float: right;" src="https://img.icons8.com/color/96/null/uninstall-programs.png" width="60" height="60"/></picture><h1> Uninstallation<h1></summary>
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
> **Note**:
|
||||||
|
>
|
||||||
|
> If you want to preseve your data, make a backup of the `%LOCALAPPDATA%\Packages\MicrosoftCorporationII.WindowsSubsystemForAndroid_8wekyb3d8bbwe\LocalCache\userdata.vhdx` file. After uninstalling, copy the VHDX file back to the `%LOCALAPPDATA%\Package\MicrosoftCorporationII.WindowsSubsystemForAndroid_8wekyb3d8bbwe\LocalCache` folder. For a more comprehensive and detailed guide, take a look at the **Backup and Restore section** in this README markdown
|
||||||
|
|
||||||
|
- To remove WSA installed:
|
||||||
|
|
||||||
|
- **1.)** Make sure that Windows Subsystem For Android™ is not running
|
||||||
|
- **2.)** Search for ``Windows Subsystem For Android™ Settings`` using the built-in Windows Search, or through Add and Remove Programs and press uninstall
|
||||||
|
- **3.)** Delete the WSA folder that extracted you extracted and Run.bat was run from to install WSA (MagiskOnWSA folder)
|
||||||
|
- **4.)** Go to ``%LOCALAPPDATA%/Packages/`` and delete the folder named ``MicrosoftCorporationII.WindowsSubsystemForAndroid_8wekyb3d8bbwe``
|
||||||
|
|
||||||
|
- If you get an error that states that the file(s) could not be deleted, make sure that WSA is turned off
|
||||||
|
|
||||||
|
- To remove WSA installed from the Microsoft Store:
|
||||||
|
|
||||||
|
- **1.)** Search for ``Windows Subsystem For Android™ Settings`` using the built-in Windows Search, or through Add and Remove Programs and press uninstall
|
||||||
|
|
||||||
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
<details>
|
||||||
|
<summary><picture><img style="float: right;" src="https://img.icons8.com/fluency/96/cloud-backup-restore.png" width="60" height="60"/></picture><h1> Backup and Restore Userdata<h1></summary>
|
||||||
|
|
||||||
|
## Backing Up Your Userdata
|
||||||
|
|
||||||
|
In order to make a backup of your WSA data you must copy the Userdata.vhdx (which includes, but is not limited Android Apps and their data, settings etc.), located at `%LOCALAPPDATA%\Packages\MicrosoftCorporationII.WindowsSubsystemForAndroid_8wekyb3d8bbwe\LocalCache\userdata.vhdx`, to a safe location
|
||||||
|
|
||||||
|
## Restoring Your Backup
|
||||||
|
|
||||||
|
Before attempting to restore your backup, you must remove WSA if installed. Then before you run the "Run.bat" script (to reinstall WSA after removing it), you need to remove these lines from Install.ps1:
|
||||||
|
|
||||||
|
Official Magisk:
|
||||||
|
```pwsh
|
||||||
|
Start-Process "wsa://com.topjohnwu.magisk"
|
||||||
|
```
|
||||||
|
Magisk Alpha:
|
||||||
|
```pwsh
|
||||||
|
Start-Process "wsa://io.github.vvb2060.magisk"
|
||||||
|
```
|
||||||
|
Magisk Delta:
|
||||||
|
```pwsh
|
||||||
|
Start-Process "wsa://io.github.huskydg.magisk"
|
||||||
|
```
|
||||||
|
Google Play Store:
|
||||||
|
```pwsh
|
||||||
|
Start-Process "wsa://com.android.vending"
|
||||||
|
```
|
||||||
|
Amazon Appstore:
|
||||||
|
```pwsh
|
||||||
|
Start-Process "wsa://com.amazon.venezia"
|
||||||
|
```
|
||||||
|
After running the script, do not run WSA at all, and go to %localappdata%\Packages and (if the folders do not exist, create them) in MicrosoftCorporationII.WindowsSubsystemForAndroid_8wekyb3d8bbwe\LocalCache\ paste the userdata.vhdx
|
||||||
|
|
||||||
|
Now run WSA and your serdata should hopefully be restored
|
||||||
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
<details>
|
||||||
|
<summary><picture><img style="float: right;" src="https://img.icons8.com/3d-fluency/94/null/help.png" width="60" height="60"/></picture><h1> FAQ<h1></summary>
|
||||||
|
|
||||||
|
|
||||||
|
**Help me, I am having problems with the MagiskOnWSA Builds**
|
||||||
|
|
||||||
|
- Open an [issue in Github](https://github.com/YT-Advanced/WSA-Script/issues) and describe the issue with sufficent detail
|
||||||
|
|
||||||
|
**Help me, I am having problems with installing Windows Subsystem For Android™ on Windows™ 10**
|
||||||
|
|
||||||
|
- I am not working on the patch, and nor claim to. Open an issue in Github, and I will try to assist you with the problem if possible. For full support visit the project homepage and open an issue there: https://github.com/cinit/WSAPatch/issues/
|
||||||
|
|
||||||
|
**How do I get a logcat?**
|
||||||
|
- There are two ways:
|
||||||
|
```
|
||||||
|
adb logcat
|
||||||
|
```
|
||||||
|
or
|
||||||
|
|
||||||
|
- Location in Windows ---> <br/> `%LOCALAPPDATA%\Packages\MicrosoftCorporationII.WindowsSubsystemForAndroid_8wekyb3d8bbwe\LocalState\diagnostics\logcat`
|
||||||
|
|
||||||
|
**Can I delete the installed folder?**
|
||||||
|
|
||||||
|
- No.
|
||||||
|
|
||||||
|
**How can I update Windows Subsystem For Android™ to a new version?**
|
||||||
|
|
||||||
|
- As Explained [Installation instructions](#installation). Download the [latest Windows Subsystem For Android™ Version](#downloads) and replace the content of your previous installation and rerun Install.ps1. Don't worry, your data will be preserved
|
||||||
|
|
||||||
|
**How do I update Magisk?**
|
||||||
|
|
||||||
|
- Do the same as updating Windows Subsystem For Android™. Wait for a new MagiskOnWSA release that includes the newer Magisk version, then follow the [Installation instructions](#installation) to update
|
||||||
|
|
||||||
|
**Can I pass SafetyNet/Play Integrity?**
|
||||||
|
|
||||||
|
- No. Virtual machines like Windows Subsystem For Android™ cannot pass these mechanisms on their own due to the lack of signing by Google. Passing requires more exotic (and untested) solutions like: <https://github.com/kdrag0n/safetynet-fix/discussions/145#discussioncomment-2170917>
|
||||||
|
|
||||||
|
**What is virtualization?**
|
||||||
|
|
||||||
|
- Virtualization is required to run virtual machines like Windows Subsystem For Android™. `Run.bat` helps you enable it. After rebooting, re-run `Run.bat` to install Windows Subsystem For Android™. If it's still not working, you have to enable virtualization in your BIOS/UEFI. Instructions vary by PC vendor, look for help online
|
||||||
|
|
||||||
|
**Can I remount system partition as read-write?**
|
||||||
|
|
||||||
|
- No. Windows Subsystem For Android™ is mounted as read-only by Hyper-V. You can, however, modify the system partition by creating a Magisk module, or by directly modifying the system.img file
|
||||||
|
|
||||||
|
**I cannot adb connect localhost:58526**
|
||||||
|
|
||||||
|
- Make sure developer mode is enabled. If the issue persists, check the IP address of Windows Subsystem For Android™ on the Settings ---> Developer page and try
|
||||||
|
|
||||||
|
```
|
||||||
|
adb connect ip:5555
|
||||||
|
```
|
||||||
|
|
||||||
|
**Magisk online module list is empty?**
|
||||||
|
|
||||||
|
- Magisk actively removes the online module repository. You can install the module locally or by
|
||||||
|
|
||||||
|
**Step 1**
|
||||||
|
|
||||||
|
adb push module.zip /data/local/tmp
|
||||||
|
|
||||||
|
**Step 2**
|
||||||
|
|
||||||
|
adb shell su -c magisk --install-module /data/local/tmp/module.zip
|
||||||
|
|
||||||
|
|
||||||
|
**How do I uninstall Magisk?**
|
||||||
|
|
||||||
|
- Request, using [Issues](https://github.com/YT-Advanced/WSA-Script/issues), a Windows Subsystem For Android™ version that doesn't include Magisk from the [Releases page](https://github.com/YT-Advanced/WSA-Script/releases/latest). Then follow the [Installation instructions](#installation)
|
||||||
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
<details>
|
||||||
|
<summary><picture><img style="float: right;" src="https://img.icons8.com/external-xnimrodx-lineal-color-xnimrodx/96/null/external-guide-education-xnimrodx-lineal-color-xnimrodx.png" width="60" height="60"/></picture><h1> Usage Guides<h1></summary>
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
### Install KernelSU Manager:
|
||||||
|
[<img src="https://img.shields.io/badge/-How%20to%20install%20KernelSU%20Manager-474154?style=for-the-badge&logoColor=white&logo=github" />](Guides/KernelSU.md)
|
||||||
|
|
||||||
|
### Install BusyBox:
|
||||||
|
[<img src="https://img.shields.io/badge/-How%20to%20install%20BusyBox-474154?style=for-the-badge&logoColor=white&logo=github" />](Guides/BusyBox.md)
|
||||||
|
|
||||||
|
### Check Integrity Guide:
|
||||||
|
[<img src="https://img.shields.io/badge/-HOW%20TO%20CHECK%20INTEGRITY%20OF%20DOWNLOAD%20PACKAGES-474154?style=for-the-badge&logoColor=white&logo=github" />](Guides/Checksum.md)
|
||||||
|
|
||||||
|
### GPU Guide:
|
||||||
|
[<img src="https://img.shields.io/badge/-How%20to%20Change%20the%20GPU%20Used-474154?style=for-the-badge&logoColor=white&logo=github" />](Guides/ChangingGPU.md)
|
||||||
|
|
||||||
|
### Sideload Guide:
|
||||||
|
[<img src="https://img.shields.io/badge/-How%20to%20Sideload%20apps-474154?style=for-the-badge&logoColor=white&logo=github" />](Guides/Sideloading.md)
|
||||||
|
|
||||||
|
### Moving WSA to another drive or partition:
|
||||||
|
[<img src="https://img.shields.io/badge/-How%20to%20Move%20WSA%20to%20another%20drive%20or%20partition-474154?style=for-the-badge&logoColor=white&logo=github" />](Guides/MoveToExtDrive.md)
|
||||||
|
|
||||||
|
### LocalHost Loopback Guide:
|
||||||
|
[<img src="https://img.shields.io/badge/-How%20to%20connect%20WSA%20to%20the%20localhost-474154?style=for-the-badge&logoColor=white&logo=github" />](Guides/LocalHostLoopback.md)
|
||||||
|
|
||||||
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
<details>
|
||||||
|
<summary><picture><img style="float: right;" src="https://img.icons8.com/external-soft-fill-juicy-fish/96/null/external-bug-coding-and-development-soft-fill-soft-fill-juicy-fish-2.png" width="60" height="60"/></picture><h1> Having Issues?<h1></summary>
|
||||||
|
|
||||||
|
### Common Issues:
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-Fix%20Install.ps1%20Issue-%23EF2D5E?style=for-the-badge&logoColor=white&logo=Github" />](Fixes/FixInstallps1.md)
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-Fix%20Install.ps1%20Failed%20to%20update-%23EF2D5E?style=for-the-badge&logoColor=white&logo=Github" />](Fixes/nstallPs1FailedToUpdate.md)
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-Fix Virtualization and Virtual Machine Platform Error-%23EF2D5E?style=for-the-badge&logoColor=white&logo=github" />](Fixes/FixVirtError.md)
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-Fix%20Internet%20Issues-%23EF2D5E?style=for-the-badge&logoColor=white&logo=Github" />](Fixes/FixInternet.md)
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-Fix%20Error%200x80073CF0-%23EF2D5E?style=for-the-badge&logoColor=white&logo=Github" />](Fixes/Fix%20Error%200x80073CF0.md)
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-Fix%20Error%200x80073CFD-%23EF2D5E?style=for-the-badge&logoColor=white&logo=Github" />](Fixes/Fix%20Error%200x80073CFD.md)
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-Fix%20Error%200x80073CF6-%23EF2D5E?style=for-the-badge&logoColor=white&logo=Github" />](Fixes/Fix%20Error%200x80073CF6.md)
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-Fix%20Error%200x80073CF9-%23EF2D5E?style=for-the-badge&logoColor=white&logo=Github" />](Fixes/Fix%20Error%200x80073CF9.md)
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-Fix%20Error%200x80073D10-%23EF2D5E?style=for-the-badge&logoColor=white&logo=Github" />](Fixes/Fix%20Error%200x80073D10.md)
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-Fix%20Error%200x80073CFB-%23EF2D5E?style=for-the-badge&logoColor=white&logo=Github" />](Fixes/Fix%20Error%200x80073CFB.md)
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-Fix%20Path%20Too%20Long-%23EF2D5E?style=for-the-badge&logoColor=white&logo=Github" />](Fixes/FixPathTooLong.md)
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-Fix%20Missing%20Icons%20Issue-%23EF2D5E?style=for-the-badge&logoColor=white&logo=Github" />](Fixes/MissingIcons.md)
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-Fix%20Target%20Machine%20Actively%20Refused%20Connection-%23EF2D5E?style=for-the-badge&logoColor=white&logo=Github" />](Fixes/TargetMachineActivelyRefusedConnection.md)
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-Fix%20Target%20Machine%20Actively%20Refused%20Connection-%23EF2D5E?style=for-the-badge&logoColor=white&logo=Github" />](Fixes/TargetMachineActivelyRefusedConnection.md)
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-Fix%20Internet%20security%20settings%20blocked%20from%20opening-%23EF2D5E?style=for-the-badge&logoColor=white&logo=Github" />](Fixes/InternetSecuritySettingsBlock.md)
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-Cannot%20sign%20in%20to%20Google%20Account-%23EF2D5E?style=for-the-badge&logoColor=white&logo=Github" />](Fixes/Google%20Play%20Issues.md)
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-WSA%20Settings%20App%20Crashes%20%2B%20Android%20Apps%20Do%20Not%20Load%20After%20Installation-%23EF2D5E?style=for-the-badge&logoColor=white&logo=Github" />](Fixes/WSA%20Settings%20App%20Crashes%20%2B%20Android%20Apps%20Do%20Not%20Load%20After%20Installation.md
|
||||||
|
)
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-WSA Does Not Load After Install %2B No Splashscreen-%23EF2D5E?style=for-the-badge&logoColor=white&logo=Github" />](Fixes/WSA%20Does%20Not%20Load%20After%20Install%20%2B%20No%20Splashscreen.md)
|
||||||
|
|
||||||
|
[<img src="https://img.shields.io/badge/-Keyboard%20Is%20Not%20Working-%23EF2D5E?style=for-the-badge&logoColor=white&logo=Github" />](Fixes/Keyboard%20Is%20Not%20Working.md)
|
||||||
|
|
||||||
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
<details>
|
||||||
|
<summary><picture><img style="float: right;" src="https://img.icons8.com/external-flaticons-lineal-color-flat-icons/64/null/external-credits-movie-theater-flaticons-lineal-color-flat-icons.png" width="60" height="60"/></picture><h1> Credits<h1></summary>
|
||||||
|
|
||||||
|
- [Microsoft](https://apps.microsoft.com/store/detail/windows-subsystem-for-android%E2%84%A2-with-amazon-appstore/9P3395VX91NR): For providing Windows Subsystem For Android™ and related files. Windows Subsystem For Android™, Windows Subsystem For Android™ Logo, Windows™ 10 and Windows™ 11 Logos are trademarks of Microsoft Corporation. Microsoft Corporation reserves all rights to these trademarks. By downloading and installing Windows Subsystem For Android™, you agree to the [Terms and Conditions](https://support.microsoft.com/en-gb/windows/microsoft-software-license-terms-microsoft-windows-subsystem-for-android-cf8dfb03-ba62-4daa-b7f3-e2cb18f968ad) and [Privacy Policy](https://privacy.microsoft.com/en-gb/privacystatement)
|
||||||
|
- [Cinit and the WSAPatch Guide](https://github.com/cinit/WSAPatch): Many thanks for the comprehensive guide, files and support provided by Cinit and the contributers at the WSAPatch repository. Windows™ 10 Builds in this repo rely on the hard work of this project and hence credit is given where due
|
||||||
|
- [StoreLib](https://github.com/StoreDev/StoreLib): API for downloading WSA
|
||||||
|
- [Magisk](https://github.com/topjohnwu/Magisk): The Magic Mask for Android
|
||||||
|
- [KernelSU](https://github.com/tiann/KernelSU): A Kernel based root solution for Android
|
||||||
|
- [MagiskOnWSALocal](https://github.com/LSPosed/MagiskOnWSALocal): Integrate Magisk root and Google Apps into WSA
|
||||||
|
- [WSAOnWin10](https://github.com/A-JiuA/WSAOnWin10): Integrate Magisk root and Google Apps into WSA (Windows Subsystem for Android) and make it run on **Windows 10** with GitHub Actions
|
||||||
|
|
||||||
|
***The repository is provided as a utility.***
|
||||||
|
|
||||||
|
***Android is a trademark of Google LLC. Windows™ is a trademark of Microsoft LLC.***
|
||||||
|
|
||||||
|
</details>
|
||||||
6
MagiskOnWSA/DLL/docs/index.html
Normal file
6
MagiskOnWSA/DLL/docs/index.html
Normal file
@ -0,0 +1,6 @@
|
|||||||
|
<!DOCTYPE html>
|
||||||
|
<html>
|
||||||
|
<head>
|
||||||
|
<script type="text/javascript">location.replace("./Issues.html")</script>
|
||||||
|
</head>
|
||||||
|
</html>
|
||||||
BIN
MagiskOnWSA/DLL/icu.dll
Normal file
BIN
MagiskOnWSA/DLL/icu.dll
Normal file
Binary file not shown.
211
MagiskOnWSA/DLL/scripts/WSAUpdateChecker.py
Normal file
211
MagiskOnWSA/DLL/scripts/WSAUpdateChecker.py
Normal file
@ -0,0 +1,211 @@
|
|||||||
|
import base64
|
||||||
|
from os import getenv
|
||||||
|
import html
|
||||||
|
import json
|
||||||
|
import re
|
||||||
|
import requests
|
||||||
|
import logging
|
||||||
|
import subprocess
|
||||||
|
|
||||||
|
from typing import Any, OrderedDict
|
||||||
|
from xml.dom import minidom
|
||||||
|
|
||||||
|
from requests import Session
|
||||||
|
from packaging import version
|
||||||
|
|
||||||
|
class Prop(OrderedDict):
|
||||||
|
def __init__(self, props: str = ...) -> None:
|
||||||
|
super().__init__()
|
||||||
|
for i, line in enumerate(props.splitlines(False)):
|
||||||
|
if '=' in line:
|
||||||
|
k, v = line.split('=', 1)
|
||||||
|
self[k] = v
|
||||||
|
else:
|
||||||
|
self[f".{i}"] = line
|
||||||
|
|
||||||
|
def __setattr__(self, __name: str, __value: Any) -> None:
|
||||||
|
self[__name] = __value
|
||||||
|
|
||||||
|
def __repr__(self):
|
||||||
|
return '\n'.join(f'{item}={self[item]}' for item in self)
|
||||||
|
|
||||||
|
logging.captureWarnings(True)
|
||||||
|
env_file = getenv('GITHUB_ENV')
|
||||||
|
token = getenv("API_KEY")
|
||||||
|
authorization = f'Bearer {token}'
|
||||||
|
reqheaders = {
|
||||||
|
"Accept": "application/vnd.github.v3+json",
|
||||||
|
"Authorization" : authorization,
|
||||||
|
}
|
||||||
|
#Catagory ID
|
||||||
|
cat_id = '858014f3-3934-4abe-8078-4aa193e74ca8'
|
||||||
|
|
||||||
|
release_type = "WIF"
|
||||||
|
|
||||||
|
new_version_found = False
|
||||||
|
|
||||||
|
session = Session()
|
||||||
|
session.verify = False
|
||||||
|
|
||||||
|
git = (
|
||||||
|
"git checkout -f update || git switch --discard-changes --orphan update"
|
||||||
|
)
|
||||||
|
|
||||||
|
def MagiskandGappsChecker(type):
|
||||||
|
global new_version_found
|
||||||
|
# Get current version
|
||||||
|
currentver = requests.get(f"https://raw.githubusercontent.com/YT-Advanced/WSA-Script/update/" + type + ".appversion").text.replace('\n', '')
|
||||||
|
# Write for pushing later
|
||||||
|
file = open('../' + type + '.appversion', 'w')
|
||||||
|
file.write(currentver)
|
||||||
|
if new_version_found:
|
||||||
|
return 0;
|
||||||
|
|
||||||
|
# Get latest version
|
||||||
|
latestver = ""
|
||||||
|
msg = ""
|
||||||
|
if (type == "magisk"):
|
||||||
|
latestver = json.loads(requests.get(f"https://github.com/topjohnwu/magisk-files/raw/master/stable.json").content)['magisk']['version'].replace('\n', '')
|
||||||
|
msg="Update Magisk Version from `v" + currentver + "` to `v" + latestver + "`"
|
||||||
|
elif (type == "gapps"):
|
||||||
|
latestver = json.loads(requests.get(f"https://api.github.com/repos/YT-Advanced/MindTheGappsBuilder/releases/latest", headers=reqheaders).content)['name']
|
||||||
|
msg="Update MindTheGapps Version from `v" + currentver + "` to `v" + latestver + "`"
|
||||||
|
|
||||||
|
# Check if version is the same or not
|
||||||
|
if (currentver != latestver):
|
||||||
|
print("New version found: " + latestver)
|
||||||
|
new_version_found = True
|
||||||
|
# Write appversion content
|
||||||
|
subprocess.Popen(git, shell=True, stdout=None, stderr=None, executable='/bin/bash').wait()
|
||||||
|
file.seek(0)
|
||||||
|
file.truncate()
|
||||||
|
file.write(latestver)
|
||||||
|
# Write Github Environment
|
||||||
|
with open(env_file, "a") as wr:
|
||||||
|
wr.write("SHOULD_BUILD=yes\nMSG=" + msg)
|
||||||
|
file.close()
|
||||||
|
|
||||||
|
def WSAChecker(user, release_type):
|
||||||
|
global new_version_found
|
||||||
|
currentver = requests.get(f"https://raw.githubusercontent.com/YT-Advanced/WSA-Script/update/" + release_type + ".appversion").text.replace('\n', '')
|
||||||
|
|
||||||
|
# Write for pushing later
|
||||||
|
file = open('../' + release_type + '.appversion', 'w')
|
||||||
|
file.write(currentver)
|
||||||
|
|
||||||
|
if new_version_found:
|
||||||
|
return 0;
|
||||||
|
# Get information
|
||||||
|
with open("../xml/GetCookie.xml", "r") as f:
|
||||||
|
cookie_content = f.read().format(user)
|
||||||
|
f.close()
|
||||||
|
try:
|
||||||
|
out = session.post(
|
||||||
|
'https://fe3.delivery.mp.microsoft.com/ClientWebService/client.asmx',
|
||||||
|
data=cookie_content,
|
||||||
|
headers={'Content-Type': 'application/soap+xml; charset=utf-8'}
|
||||||
|
)
|
||||||
|
except:
|
||||||
|
print("Network Error!")
|
||||||
|
return 1
|
||||||
|
doc = minidom.parseString(out.text)
|
||||||
|
cookie = doc.getElementsByTagName('EncryptedData')[0].firstChild.nodeValue
|
||||||
|
with open("../xml/WUIDRequest.xml", "r") as f:
|
||||||
|
cat_id_content = f.read().format(user, cookie, cat_id, release_type)
|
||||||
|
f.close()
|
||||||
|
try:
|
||||||
|
out = session.post(
|
||||||
|
'https://fe3.delivery.mp.microsoft.com/ClientWebService/client.asmx',
|
||||||
|
data=cat_id_content,
|
||||||
|
headers={'Content-Type': 'application/soap+xml; charset=utf-8'}
|
||||||
|
)
|
||||||
|
except:
|
||||||
|
print("Network Error!")
|
||||||
|
return 1
|
||||||
|
doc = minidom.parseString(html.unescape(out.text))
|
||||||
|
filenames = {}
|
||||||
|
for node in doc.getElementsByTagName('ExtendedUpdateInfo')[0].getElementsByTagName('Updates')[0].getElementsByTagName('Update'):
|
||||||
|
node_xml = node.getElementsByTagName('Xml')[0]
|
||||||
|
node_files = node_xml.getElementsByTagName('Files')
|
||||||
|
if not node_files:
|
||||||
|
continue
|
||||||
|
else:
|
||||||
|
for node_file in node_files[0].getElementsByTagName('File'):
|
||||||
|
if node_file.hasAttribute('InstallerSpecificIdentifier') and node_file.hasAttribute('FileName'):
|
||||||
|
filenames[node.getElementsByTagName('ID')[0].firstChild.nodeValue] = (f"{node_file.attributes['InstallerSpecificIdentifier'].value}_{node_file.attributes['FileName'].value}",
|
||||||
|
node_xml.getElementsByTagName('ExtendedProperties')[0].attributes['PackageIdentityName'].value)
|
||||||
|
identities = {}
|
||||||
|
for node in doc.getElementsByTagName('NewUpdates')[0].getElementsByTagName('UpdateInfo'):
|
||||||
|
node_xml = node.getElementsByTagName('Xml')[0]
|
||||||
|
if not node_xml.getElementsByTagName('SecuredFragment'):
|
||||||
|
continue
|
||||||
|
else:
|
||||||
|
id = node.getElementsByTagName('ID')[0].firstChild.nodeValue
|
||||||
|
update_identity = node_xml.getElementsByTagName('UpdateIdentity')[0]
|
||||||
|
if id in filenames:
|
||||||
|
fileinfo = filenames[id]
|
||||||
|
if fileinfo[0] not in identities:
|
||||||
|
identities[fileinfo[0]] = ([update_identity.attributes['UpdateID'].value,
|
||||||
|
update_identity.attributes['RevisionNumber'].value], fileinfo[1])
|
||||||
|
wsa_build_ver = 0
|
||||||
|
for filename, value in identities.items():
|
||||||
|
if re.match(f"MicrosoftCorporationII.WindowsSubsystemForAndroid_.*.msixbundle", filename):
|
||||||
|
tmp_wsa_build_ver = re.search(r"\d{4}.\d{5}.\d{1,}.\d{1,}", filename).group()
|
||||||
|
if (wsa_build_ver == 0):
|
||||||
|
wsa_build_ver = tmp_wsa_build_ver
|
||||||
|
elif version.parse(wsa_build_ver) < version.parse(tmp_wsa_build_ver):
|
||||||
|
wsa_build_ver = tmp_wsa_build_ver
|
||||||
|
|
||||||
|
# Check new WSA version
|
||||||
|
if version.parse(currentver) < version.parse(wsa_build_ver):
|
||||||
|
print("New version found: " + wsa_build_ver)
|
||||||
|
new_version_found = True
|
||||||
|
# Write appversion content
|
||||||
|
subprocess.Popen(git, shell=True, stdout=None, stderr=None, executable='/bin/bash').wait()
|
||||||
|
file.seek(0)
|
||||||
|
file.truncate()
|
||||||
|
file.write(wsa_build_ver)
|
||||||
|
# Write Github Environment
|
||||||
|
msg = 'Update WSA Version from `v' + currentver + '` to `v' + wsa_build_ver + '`'
|
||||||
|
with open(env_file, "a") as wr:
|
||||||
|
wr.write("SHOULD_BUILD=yes\nRELEASE_TYPE=" + release_type + "\nMSG=" + msg)
|
||||||
|
file.close()
|
||||||
|
|
||||||
|
# Get user_code (Thanks to @bubbles-wow because of his repository)
|
||||||
|
users = {""}
|
||||||
|
try:
|
||||||
|
response = requests.get("https://api.github.com/repos/bubbles-wow/MS-Account-Token/contents/token.cfg")
|
||||||
|
if response.status_code == 200:
|
||||||
|
content = response.json()["content"]
|
||||||
|
content = content.encode("utf-8")
|
||||||
|
content = base64.b64decode(content)
|
||||||
|
text = content.decode("utf-8")
|
||||||
|
user_code = Prop(text).get("user_code")
|
||||||
|
updatetime = Prop(text).get("update_time")
|
||||||
|
print("Successfully get user token from server!")
|
||||||
|
print(f"Last update time: {updatetime}\n")
|
||||||
|
else:
|
||||||
|
user_code = ""
|
||||||
|
print(f"Failed to get user token from server! Error code: {response.status_code}\n")
|
||||||
|
except:
|
||||||
|
user_code = ""
|
||||||
|
|
||||||
|
if user_code == "":
|
||||||
|
users = {""}
|
||||||
|
else:
|
||||||
|
users = {"", user_code}
|
||||||
|
for user in users:
|
||||||
|
if user == "":
|
||||||
|
print("Checking WSA Stable version...\n")
|
||||||
|
if WSAChecker(user, "retail") == 1:
|
||||||
|
break
|
||||||
|
print("Checking Magisk version...\n")
|
||||||
|
if MagiskandGappsChecker("magisk") == 1:
|
||||||
|
break
|
||||||
|
print("Checking MindTheGapps version...\n")
|
||||||
|
if MagiskandGappsChecker("gapps") == 1:
|
||||||
|
break
|
||||||
|
else:
|
||||||
|
print("Checking WSA Insider version...\n")
|
||||||
|
if WSAChecker(user, "WIF") == 1:
|
||||||
|
break
|
||||||
453
MagiskOnWSA/DLL/scripts/build.sh
Normal file
453
MagiskOnWSA/DLL/scripts/build.sh
Normal file
@ -0,0 +1,453 @@
|
|||||||
|
#!/bin/bash
|
||||||
|
#
|
||||||
|
# This file is part of MagiskOnWSALocal.
|
||||||
|
#
|
||||||
|
# MagiskOnWSALocal is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU Affero General Public License as
|
||||||
|
# published by the Free Software Foundation, either version 3 of the
|
||||||
|
# License, or (at your option) any later version.
|
||||||
|
#
|
||||||
|
# MagiskOnWSALocal is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU Affero General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU Affero General Public License
|
||||||
|
# along with MagiskOnWSALocal. If not, see <https://www.gnu.org/licenses/>.
|
||||||
|
#
|
||||||
|
# Copyright (C) 2024 LSPosed Contributors
|
||||||
|
#
|
||||||
|
|
||||||
|
# shellcheck disable=SC2034
|
||||||
|
cd "$(dirname "$0")" || exit 1
|
||||||
|
# export TMPDIR=$HOME/.cache/wsa
|
||||||
|
if [ "$TMPDIR" ] && [ ! -d "$TMPDIR" ]; then
|
||||||
|
mkdir -p "$TMPDIR"
|
||||||
|
fi
|
||||||
|
WORK_DIR=$(mktemp -d -t wsa-build-XXXXXXXXXX_) || exit 1
|
||||||
|
|
||||||
|
DOWNLOAD_DIR=../download
|
||||||
|
DOWNLOAD_WSA_CONF_NAME=wsa.list
|
||||||
|
DOWNLOAD_CONF_NAME=download.list
|
||||||
|
PYTHON_VENV_DIR="$(dirname "$PWD")/python3-env"
|
||||||
|
OUTPUT_DIR=../output
|
||||||
|
WSA_WORK_ENV="${WORK_DIR:?}/ENV"
|
||||||
|
|
||||||
|
touch "$WSA_WORK_ENV"
|
||||||
|
export WSA_WORK_ENV
|
||||||
|
abort() {
|
||||||
|
[ "$1" ] && echo -e "ERROR: $1"
|
||||||
|
echo "Build: an error has occurred, exit"
|
||||||
|
exit 1
|
||||||
|
}
|
||||||
|
trap abort INT TERM
|
||||||
|
|
||||||
|
default() {
|
||||||
|
ARCH=x64
|
||||||
|
# CUSTOM_MODEL=redfin
|
||||||
|
RELEASE_TYPE=retail
|
||||||
|
MAGISK_BRANCH=topjohnwu
|
||||||
|
MAGISK_VER=stable
|
||||||
|
ROOT_SOL=magisk
|
||||||
|
COMPRESS_FORMAT=none
|
||||||
|
}
|
||||||
|
|
||||||
|
ARCH_MAP=(
|
||||||
|
"x64"
|
||||||
|
"arm64"
|
||||||
|
)
|
||||||
|
|
||||||
|
RELEASE_TYPE_MAP=(
|
||||||
|
"retail"
|
||||||
|
"RP"
|
||||||
|
"WIS"
|
||||||
|
"WIF"
|
||||||
|
"latest"
|
||||||
|
)
|
||||||
|
|
||||||
|
MAGISK_BRANCH_MAP=(
|
||||||
|
"topjohnwu"
|
||||||
|
"HuskyDG"
|
||||||
|
"vvb2060"
|
||||||
|
)
|
||||||
|
|
||||||
|
MAGISK_VER_MAP=(
|
||||||
|
"stable"
|
||||||
|
"beta"
|
||||||
|
"canary"
|
||||||
|
"debug"
|
||||||
|
"release"
|
||||||
|
"delta"
|
||||||
|
"alpha"
|
||||||
|
)
|
||||||
|
|
||||||
|
# CUSTOM_MODEL_MAP=(
|
||||||
|
# "none"
|
||||||
|
# "sunfish"
|
||||||
|
# "bramble"
|
||||||
|
# "redfin"
|
||||||
|
# "barbet"
|
||||||
|
# "raven"
|
||||||
|
# "oriole"
|
||||||
|
# "bluejay"
|
||||||
|
# "panther"
|
||||||
|
# "cheetah"
|
||||||
|
# "lynx"
|
||||||
|
# "tangorpro"
|
||||||
|
# "felix"
|
||||||
|
# )
|
||||||
|
|
||||||
|
ROOT_SOL_MAP=(
|
||||||
|
"magisk"
|
||||||
|
"kernelsu"
|
||||||
|
"none"
|
||||||
|
)
|
||||||
|
|
||||||
|
COMPRESS_FORMAT_MAP=(
|
||||||
|
"7z"
|
||||||
|
"zip"
|
||||||
|
"none"
|
||||||
|
)
|
||||||
|
|
||||||
|
ARGUMENT_LIST=(
|
||||||
|
"compress-format:"
|
||||||
|
"arch:"
|
||||||
|
"release-type:"
|
||||||
|
"root-sol:"
|
||||||
|
"magisk-branch:"
|
||||||
|
"magisk-ver:"
|
||||||
|
"install-gapps"
|
||||||
|
"remove-amazon"
|
||||||
|
)
|
||||||
|
|
||||||
|
default
|
||||||
|
|
||||||
|
opts=$(
|
||||||
|
getopt \
|
||||||
|
--longoptions "$(printf "%s," "${ARGUMENT_LIST[@]}")" \
|
||||||
|
--name "$(basename "$0")" \
|
||||||
|
--options "" \
|
||||||
|
-- "$@"
|
||||||
|
) || abort "Failed to parse options, please check your input"
|
||||||
|
|
||||||
|
eval set --"$opts"
|
||||||
|
while [[ $# -gt 0 ]]; do
|
||||||
|
case "$1" in
|
||||||
|
--compress-format)
|
||||||
|
COMPRESS_FORMAT="$2"
|
||||||
|
shift 2
|
||||||
|
;;
|
||||||
|
--arch)
|
||||||
|
ARCH="$2"
|
||||||
|
shift 2
|
||||||
|
;;
|
||||||
|
--release-type)
|
||||||
|
RELEASE_TYPE="$2"
|
||||||
|
shift 2
|
||||||
|
;;
|
||||||
|
--root-sol)
|
||||||
|
ROOT_SOL="$2"
|
||||||
|
shift 2
|
||||||
|
;;
|
||||||
|
--magisk-branch)
|
||||||
|
MAGISK_BRANCH="$2"
|
||||||
|
shift 2
|
||||||
|
;;
|
||||||
|
--magisk-ver)
|
||||||
|
MAGISK_VER="$2"
|
||||||
|
shift 2
|
||||||
|
;;
|
||||||
|
--install-gapps)
|
||||||
|
HAS_GAPPS=1
|
||||||
|
shift
|
||||||
|
;;
|
||||||
|
--remove-amazon)
|
||||||
|
REMOVE_AMAZON=1
|
||||||
|
shift
|
||||||
|
;;
|
||||||
|
--)
|
||||||
|
shift
|
||||||
|
break
|
||||||
|
;;
|
||||||
|
esac
|
||||||
|
done
|
||||||
|
|
||||||
|
check_list() {
|
||||||
|
local input=$1
|
||||||
|
if [ -n "$input" ]; then
|
||||||
|
local name=$2
|
||||||
|
shift
|
||||||
|
local arr=("$@")
|
||||||
|
local list_count=${#arr[@]}
|
||||||
|
for i in "${arr[@]}"; do
|
||||||
|
if [ "$input" == "$i" ]; then
|
||||||
|
echo "INFO: $name: $input"
|
||||||
|
break
|
||||||
|
fi
|
||||||
|
((list_count--))
|
||||||
|
if (("$list_count" <= 0)); then
|
||||||
|
abort "Invalid $name: $input"
|
||||||
|
fi
|
||||||
|
done
|
||||||
|
fi
|
||||||
|
}
|
||||||
|
|
||||||
|
check_list "$ARCH" "Architecture" "${ARCH_MAP[@]}"
|
||||||
|
check_list "$RELEASE_TYPE" "Release Type" "${RELEASE_TYPE_MAP[@]}"
|
||||||
|
check_list "$MAGISK_BRANCH" "Magisk Branch" "${MAGISK_BRANCH_MAP[@]}"
|
||||||
|
check_list "$MAGISK_VER" "Magisk Version" "${MAGISK_VER_MAP[@]}"
|
||||||
|
check_list "$ROOT_SOL" "Root Solution" "${ROOT_SOL_MAP[@]}"
|
||||||
|
# check_list "$CUSTOM_MODEL" "Custom Model" "${CUSTOM_MODEL_MAP[@]}"
|
||||||
|
check_list "$COMPRESS_FORMAT" "Compress Format" "${COMPRESS_FORMAT_MAP[@]}"
|
||||||
|
|
||||||
|
# shellcheck disable=SC1091
|
||||||
|
[ -f "$PYTHON_VENV_DIR/bin/activate" ] && {
|
||||||
|
source "$PYTHON_VENV_DIR/bin/activate" || abort "Failed to activate virtual environment"
|
||||||
|
}
|
||||||
|
declare -A RELEASE_NAME_MAP=(["retail"]="Retail" ["latest"]="Insider Private" ["RP"]="Release Preview" ["WIS"]="Insider Slow" ["WIF"]="Insider Fast")
|
||||||
|
declare -A ANDROID_API_MAP=(["33"]="13.0" ["34"]="14.0")
|
||||||
|
declare -A ARCH_NAME_MAP=(["x64"]="x86_64" ["arm64"]="arm64")
|
||||||
|
RELEASE_NAME=${RELEASE_NAME_MAP[$RELEASE_TYPE]} || abort
|
||||||
|
echo -e "INFO: Release Name: $RELEASE_NAME\n"
|
||||||
|
WSA_ZIP_PATH=$DOWNLOAD_DIR/wsa-$RELEASE_TYPE.zip
|
||||||
|
vclibs_PATH="$DOWNLOAD_DIR/Microsoft.VCLibs.140.00_$ARCH.appx"
|
||||||
|
UWPVCLibs_PATH="$DOWNLOAD_DIR/Microsoft.VCLibs.140.00.UWPDesktop_$ARCH.appx"
|
||||||
|
xaml_PATH="$DOWNLOAD_DIR/Microsoft.UI.Xaml.2.8_$ARCH.appx"
|
||||||
|
MAGISK_ZIP=magisk-$MAGISK_VER.zip
|
||||||
|
MAGISK_PATH=$DOWNLOAD_DIR/$MAGISK_ZIP
|
||||||
|
CUST_PATH="$DOWNLOAD_DIR/cust.img"
|
||||||
|
ANDROID_API=33
|
||||||
|
update_gapps_files_name() {
|
||||||
|
GAPPS_IMAGE_NAME=gapps-${ANDROID_API_MAP[$ANDROID_API]}-${ARCH_NAME_MAP[$ARCH]}.img
|
||||||
|
GAPPS_RC_NAME=gapps-${ANDROID_API_MAP[$ANDROID_API]}.rc
|
||||||
|
GAPPS_IMAGE_PATH=$DOWNLOAD_DIR/$GAPPS_IMAGE_NAME
|
||||||
|
GAPPS_RC_PATH=$DOWNLOAD_DIR/$GAPPS_RC_NAME
|
||||||
|
}
|
||||||
|
WSA_MAJOR_VER=0
|
||||||
|
getKernelVersion() {
|
||||||
|
local bintype kernel_string kernel_version
|
||||||
|
bintype="$(file -b "$1")"
|
||||||
|
if [[ $bintype == *"version"* ]]; then
|
||||||
|
readarray -td '' kernel_string < <(awk '{ gsub(/, /,"\0"); print; }' <<<"$bintype, ")
|
||||||
|
unset 'kernel_string[-1]'
|
||||||
|
for i in "${kernel_string[@]}"; do
|
||||||
|
if [[ $i == *"version"* ]]; then
|
||||||
|
IFS=" " read -r -a kernel_string <<<"$i"
|
||||||
|
kernel_version="${kernel_string[1]}"
|
||||||
|
fi
|
||||||
|
done
|
||||||
|
else
|
||||||
|
IFS=" " read -r -a kernel_string <<<"$(strings "$1" | grep 'Linux version')"
|
||||||
|
kernel_version="${kernel_string[2]}"
|
||||||
|
fi
|
||||||
|
IFS=" " read -r -a arr <<<"${kernel_version//-/ }"
|
||||||
|
printf '%s' "${arr[0]}"
|
||||||
|
}
|
||||||
|
update_ksu_zip_name() {
|
||||||
|
KERNEL_VER=""
|
||||||
|
if [ -f "$WORK_DIR/wsa/$ARCH/Tools/kernel" ]; then
|
||||||
|
KERNEL_VER=$(getKernelVersion "$WORK_DIR/wsa/$ARCH/Tools/kernel")
|
||||||
|
fi
|
||||||
|
KERNELSU_ZIP_NAME=kernelsu-$ARCH-$KERNEL_VER.zip
|
||||||
|
KERNELSU_PATH=$DOWNLOAD_DIR/$KERNELSU_ZIP_NAME
|
||||||
|
KERNELSU_APK_PATH=$DOWNLOAD_DIR/KernelSU.apk
|
||||||
|
KERNELSU_INFO="$KERNELSU_PATH.info"
|
||||||
|
}
|
||||||
|
|
||||||
|
echo "Generating WSA Download Links"
|
||||||
|
python3 generateWSALinks.py "$ARCH" "$RELEASE_TYPE" "$DOWNLOAD_DIR" "$DOWNLOAD_WSA_CONF_NAME" || abort
|
||||||
|
|
||||||
|
if [ "$RELEASE_TYPE" == "latest" ]; then
|
||||||
|
printf "%s\n" "$(curl -sL https://api.github.com/repos/bubbles-wow/WSA-Archive/releases/latest | jq -r '.assets[] | .browser_download_url')" >> "$DOWNLOAD_DIR/$DOWNLOAD_WSA_CONF_NAME" || abort
|
||||||
|
printf " dir=%s\n" "$DOWNLOAD_DIR" >> "$DOWNLOAD_DIR/$DOWNLOAD_WSA_CONF_NAME" || abort
|
||||||
|
printf " out=wsa-latest.zip\n" >> "$DOWNLOAD_DIR/$DOWNLOAD_WSA_CONF_NAME" || abort
|
||||||
|
WSA_VER=$(curl -sL https://api.github.com/repos/bubbles-wow/WSA-Archive/releases/latest | jq -r '.tag_name')
|
||||||
|
WSA_MAJOR_VER=${WSA_VER:0:4}
|
||||||
|
else
|
||||||
|
# shellcheck disable=SC1090
|
||||||
|
source "$WSA_WORK_ENV" || abort
|
||||||
|
fi
|
||||||
|
|
||||||
|
if ! aria2c --no-conf --log-level=info --log="$DOWNLOAD_DIR/aria2_download.log" -x16 -s16 -j7 -m0 \
|
||||||
|
--async-dns=false --check-integrity=true \
|
||||||
|
-d"$DOWNLOAD_DIR" -i"$DOWNLOAD_DIR/$DOWNLOAD_WSA_CONF_NAME"; then
|
||||||
|
abort "We have encountered an error while downloading files."
|
||||||
|
fi
|
||||||
|
|
||||||
|
echo "Extracting WSA"
|
||||||
|
if [ -f "$WSA_ZIP_PATH" ]; then
|
||||||
|
if ! python3 extractWSA.py "$ARCH" "$WSA_ZIP_PATH" "$WORK_DIR" "$WSA_WORK_ENV"; then
|
||||||
|
abort "Unzip WSA failed"
|
||||||
|
fi
|
||||||
|
echo -e "done\n"
|
||||||
|
# shellcheck disable=SC1090
|
||||||
|
source "$WSA_WORK_ENV" || abort
|
||||||
|
else
|
||||||
|
abort "The WSA zip package does not exist"
|
||||||
|
fi
|
||||||
|
|
||||||
|
echo "Generating Download Links"
|
||||||
|
if [ "$HAS_GAPPS" ] || [ "$ROOT_SOL" = "magisk" ]; then
|
||||||
|
python3 generateMagiskLink.py "$MAGISK_BRANCH" "$MAGISK_VER" "$DOWNLOAD_DIR" "$DOWNLOAD_CONF_NAME" || abort
|
||||||
|
fi
|
||||||
|
|
||||||
|
if [ "$ROOT_SOL" = "kernelsu" ]; then
|
||||||
|
update_ksu_zip_name
|
||||||
|
python3 generateKernelSULink.py "$ARCH" "$DOWNLOAD_DIR" "$DOWNLOAD_CONF_NAME" "$KERNEL_VER" "$KERNELSU_ZIP_NAME" || abort
|
||||||
|
# shellcheck disable=SC1090
|
||||||
|
source "$WSA_WORK_ENV" || abort
|
||||||
|
# shellcheck disable=SC2153
|
||||||
|
echo "KERNELSU_VER=$KERNELSU_VER" >"$KERNELSU_INFO"
|
||||||
|
fi
|
||||||
|
if [ "$HAS_GAPPS" ]; then
|
||||||
|
update_gapps_files_name
|
||||||
|
python3 generateGappsLink.py "$ARCH" "$DOWNLOAD_DIR" "$DOWNLOAD_CONF_NAME" "$ANDROID_API" "$GAPPS_IMAGE_NAME" || abort
|
||||||
|
fi
|
||||||
|
if [ -f "$DOWNLOAD_DIR/$DOWNLOAD_CONF_NAME" ]; then
|
||||||
|
echo "Downloading Artifacts"
|
||||||
|
if ! aria2c --no-conf --log-level=info --log="$DOWNLOAD_DIR/aria2_download.log" -x16 -s16 -j7 -m0 \
|
||||||
|
--async-dns=false --check-integrity=true \
|
||||||
|
-d"$DOWNLOAD_DIR" -i"$DOWNLOAD_DIR/$DOWNLOAD_CONF_NAME"; then
|
||||||
|
abort "We have encountered an error while downloading files."
|
||||||
|
fi
|
||||||
|
fi
|
||||||
|
|
||||||
|
declare -A FILES_CHECK_LIST=([xaml_PATH]="$xaml_PATH" [vclibs_PATH]="$vclibs_PATH" [UWPVCLibs_PATH]="$UWPVCLibs_PATH")
|
||||||
|
if [ "$HAS_GAPPS" ] || [ "$ROOT_SOL" = "magisk" ]; then
|
||||||
|
FILES_CHECK_LIST+=(["MAGISK_PATH"]="$MAGISK_PATH" ["CUST_PATH"]="$CUST_PATH")
|
||||||
|
fi
|
||||||
|
if [ "$ROOT_SOL" = "kernelsu" ]; then
|
||||||
|
update_ksu_zip_name
|
||||||
|
FILES_CHECK_LIST+=(["KERNELSU_PATH"]="$KERNELSU_PATH")
|
||||||
|
fi
|
||||||
|
if [ "$HAS_GAPPS" ]; then
|
||||||
|
update_gapps_files_name
|
||||||
|
FILES_CHECK_LIST+=(["GAPPS_IMAGE_PATH"]="$GAPPS_IMAGE_PATH" ["GAPPS_RC_PATH"]="$GAPPS_RC_PATH")
|
||||||
|
fi
|
||||||
|
for i in "${FILES_CHECK_LIST[@]}"; do
|
||||||
|
if [ ! -f "$i" ]; then
|
||||||
|
echo "Offline mode: missing [$i]"
|
||||||
|
FILE_MISSING="1"
|
||||||
|
fi
|
||||||
|
done
|
||||||
|
if [ "$FILE_MISSING" ]; then
|
||||||
|
abort "Some files are missing"
|
||||||
|
fi
|
||||||
|
if [ "$HAS_GAPPS" ] || [ "$ROOT_SOL" = "magisk" ]; then
|
||||||
|
echo "Extracting Magisk"
|
||||||
|
if [ -f "$MAGISK_PATH" ]; then
|
||||||
|
MAGISK_VERSION_NAME=""
|
||||||
|
MAGISK_VERSION_CODE=0
|
||||||
|
if ! python3 extractMagisk.py "$ARCH" "$MAGISK_PATH" "$WORK_DIR"; then
|
||||||
|
abort "Unzip Magisk failed, is the download incomplete?"
|
||||||
|
fi
|
||||||
|
# shellcheck disable=SC1090
|
||||||
|
source "$WSA_WORK_ENV" || abort
|
||||||
|
chmod +x "$WORK_DIR/magisk/magiskboot" || abort
|
||||||
|
else
|
||||||
|
abort "The Magisk zip package does not exist, rename it to magisk-debug.zip and put it in the download folder."
|
||||||
|
fi
|
||||||
|
echo -e "done\n"
|
||||||
|
fi
|
||||||
|
|
||||||
|
if [ "$HAS_GAPPS" ] || [ "$ROOT_SOL" = "magisk" ]; then
|
||||||
|
echo "Integrating Magisk"
|
||||||
|
"$WORK_DIR/magisk/magiskboot" compress=xz "$WORK_DIR/magisk/magisk64" "$WORK_DIR/magisk/magisk64.xz"
|
||||||
|
"$WORK_DIR/magisk/magiskboot" compress=xz "$WORK_DIR/magisk/magisk32" "$WORK_DIR/magisk/magisk32.xz"
|
||||||
|
"$WORK_DIR/magisk/magiskboot" compress=xz "$MAGISK_PATH" "$WORK_DIR/magisk/stub.xz"
|
||||||
|
"$WORK_DIR/magisk/magiskboot" cpio "$WORK_DIR/wsa/$ARCH/Tools/initrd.img" \
|
||||||
|
"mv /init /wsainit" \
|
||||||
|
"add 0750 /lspinit ../bin/$ARCH/lspinit" \
|
||||||
|
"ln /lspinit /init" \
|
||||||
|
"add 0750 /magiskinit $WORK_DIR/magisk/magiskinit" \
|
||||||
|
"mkdir 0750 overlay.d" \
|
||||||
|
"mkdir 0750 overlay.d/sbin" \
|
||||||
|
"add 0644 overlay.d/sbin/magisk64.xz $WORK_DIR/magisk/magisk64.xz" \
|
||||||
|
"add 0644 overlay.d/sbin/magisk32.xz $WORK_DIR/magisk/magisk32.xz" \
|
||||||
|
"add 0644 overlay.d/sbin/stub.xz $WORK_DIR/magisk/stub.xz" \
|
||||||
|
"mkdir 000 .backup" \
|
||||||
|
"add 000 overlay.d/init.lsp.magisk.rc init.lsp.magisk.rc" \
|
||||||
|
"add 000 overlay.d/sbin/post-fs-data.sh post-fs-data.sh" \
|
||||||
|
"add 000 overlay.d/sbin/lsp_cust.img $CUST_PATH" \
|
||||||
|
|| abort "Unable to patch initrd"
|
||||||
|
elif [ "$ROOT_SOL" = "kernelsu" ]; then
|
||||||
|
echo "Extracting KernelSU"
|
||||||
|
# shellcheck disable=SC1090
|
||||||
|
source "${KERNELSU_INFO:?}" || abort
|
||||||
|
echo "WSA Kernel Version: $KERNEL_VER"
|
||||||
|
echo "KernelSU Version: $KERNELSU_VER"
|
||||||
|
if ! unzip "$KERNELSU_PATH" -d "$WORK_DIR/kernelsu"; then
|
||||||
|
abort "Unzip KernelSU failed, package is corrupted?"
|
||||||
|
fi
|
||||||
|
if [ "$ARCH" = "x64" ]; then
|
||||||
|
mv "$WORK_DIR/kernelsu/bzImage" "$WORK_DIR/kernelsu/kernel"
|
||||||
|
elif [ "$ARCH" = "arm64" ]; then
|
||||||
|
mv "$WORK_DIR/kernelsu/Image" "$WORK_DIR/kernelsu/kernel"
|
||||||
|
fi
|
||||||
|
echo "Integrate KernelSU"
|
||||||
|
mv "$WORK_DIR/wsa/$ARCH/Tools/kernel" "$WORK_DIR/wsa/$ARCH/Tools/kernel_origin"
|
||||||
|
cp "$WORK_DIR/kernelsu/kernel" "$WORK_DIR/wsa/$ARCH/Tools/kernel"
|
||||||
|
fi
|
||||||
|
echo -e "done\n"
|
||||||
|
if [ "$HAS_GAPPS" ]; then
|
||||||
|
update_gapps_files_name
|
||||||
|
if [ -f "$GAPPS_IMAGE_PATH" ] && [ -f "$GAPPS_RC_PATH" ]; then
|
||||||
|
echo "Integrating GApps"
|
||||||
|
"$WORK_DIR/magisk/magiskboot" cpio "$WORK_DIR/wsa/$ARCH/Tools/initrd.img" \
|
||||||
|
"add 000 /lspolicy.rule sepolicy.rule" \
|
||||||
|
"add 000 overlay.d/gapps.rc $GAPPS_RC_PATH" \
|
||||||
|
"add 000 overlay.d/sbin/lsp_gapps.img $GAPPS_IMAGE_PATH" \
|
||||||
|
|| abort "Unable to patch initrd"
|
||||||
|
echo -e "done\n"
|
||||||
|
else
|
||||||
|
abort "The GApps package does not exist."
|
||||||
|
fi
|
||||||
|
fi
|
||||||
|
|
||||||
|
if [ "$REMOVE_AMAZON" ]; then
|
||||||
|
rm -f "$WORK_DIR/wsa/$ARCH/apex/"mado*.apex || abort
|
||||||
|
fi
|
||||||
|
|
||||||
|
echo "Removing signature and add scripts"
|
||||||
|
rm -rf "${WORK_DIR:?}"/wsa/"$ARCH"/\[Content_Types\].xml "$WORK_DIR/wsa/$ARCH/AppxBlockMap.xml" "$WORK_DIR/wsa/$ARCH/AppxSignature.p7x" "$WORK_DIR/wsa/$ARCH/AppxMetadata" || abort
|
||||||
|
cp "$vclibs_PATH" "$xaml_PATH" "$WORK_DIR/wsa/$ARCH" || abort
|
||||||
|
cp "$UWPVCLibs_PATH" "$xaml_PATH" "$WORK_DIR/wsa/$ARCH" || abort
|
||||||
|
cp "../xml/priconfig.xml" "$WORK_DIR/wsa/$ARCH/xml/" || abort
|
||||||
|
cp "../installer/$ARCH/MakePri.ps1" "$WORK_DIR/wsa/$ARCH" || abort
|
||||||
|
cp "../installer/$ARCH/Install.ps1" "$WORK_DIR/wsa/$ARCH" || abort
|
||||||
|
cp "../installer/Run.bat" "$WORK_DIR/wsa/$ARCH" || abort
|
||||||
|
find "$WORK_DIR/wsa/$ARCH" -maxdepth 1 -mindepth 1 -printf "%P\n" >"$WORK_DIR/wsa/$ARCH/filelist.txt" || abort
|
||||||
|
find "$WORK_DIR/wsa/$ARCH/pri" -printf "%P\n" | sed -e 's/^/pri\\/' -e '/^$/d' > "$WORK_DIR/wsa/$ARCH/filelist-pri.txt" || abort
|
||||||
|
find "$WORK_DIR/wsa/$ARCH/xml" -printf "%P\n" | sed -e 's/^/xml\\/' -e '/^$/d' >> "$WORK_DIR/wsa/$ARCH/filelist-pri.txt" || abort
|
||||||
|
echo -e "done\n"
|
||||||
|
|
||||||
|
if [[ "$ROOT_SOL" = "none" ]]; then
|
||||||
|
name1=""
|
||||||
|
elif [ "$ROOT_SOL" = "magisk" ]; then
|
||||||
|
name1="-with-magisk-$MAGISK_VERSION_NAME($MAGISK_VERSION_CODE)-$MAGISK_VER"
|
||||||
|
elif [ "$ROOT_SOL" = "kernelsu" ]; then
|
||||||
|
name1="-with-$ROOT_SOL-$KERNELSU_VER"
|
||||||
|
fi
|
||||||
|
if [ -z "$HAS_GAPPS" ]; then
|
||||||
|
name2="-NoGApps"
|
||||||
|
else
|
||||||
|
name2=-GApps-${ANDROID_API_MAP[$ANDROID_API]}
|
||||||
|
fi
|
||||||
|
#if [[ "$MODEL_NAME" != "default" ]]; then
|
||||||
|
# name3="-as-$MODEL_NAME"
|
||||||
|
#fi
|
||||||
|
artifact_name=WSA_${WSA_VER}_${ARCH}_${WSA_REL}${name1}${name2}
|
||||||
|
#${name3}
|
||||||
|
[ "$REMOVE_AMAZON" ] && artifact_name+=-NoAmazon
|
||||||
|
|
||||||
|
if [ ! -d "$OUTPUT_DIR" ]; then
|
||||||
|
mkdir -p "$OUTPUT_DIR"
|
||||||
|
fi
|
||||||
|
OUTPUT_PATH="${OUTPUT_DIR:?}/$artifact_name"
|
||||||
|
mv "$WORK_DIR/wsa/$ARCH" "$OUTPUT_PATH"
|
||||||
|
{
|
||||||
|
echo "artifact=${artifact_name}"
|
||||||
|
echo "arch=${ARCH}"
|
||||||
|
echo "built=$(date -u +%Y%m%d%H%M%S)"
|
||||||
|
echo "file_ext=${COMPRESS_FORMAT}"
|
||||||
|
} >> "$GITHUB_OUTPUT"
|
||||||
77
MagiskOnWSA/DLL/scripts/extractMagisk.py
Normal file
77
MagiskOnWSA/DLL/scripts/extractMagisk.py
Normal file
@ -0,0 +1,77 @@
|
|||||||
|
#!/usr/bin/python3
|
||||||
|
#
|
||||||
|
# This file is part of MagiskOnWSALocal.
|
||||||
|
#
|
||||||
|
# MagiskOnWSALocal is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU Affero General Public License as
|
||||||
|
# published by the Free Software Foundation, either version 3 of the
|
||||||
|
# License, or (at your option) any later version.
|
||||||
|
#
|
||||||
|
# MagiskOnWSALocal is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU Affero General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU Affero General Public License
|
||||||
|
# along with MagiskOnWSALocal. If not, see <https://www.gnu.org/licenses/>.
|
||||||
|
#
|
||||||
|
# Copyright (C) 2024 LSPosed Contributors
|
||||||
|
#
|
||||||
|
|
||||||
|
import sys
|
||||||
|
import zipfile
|
||||||
|
from pathlib import Path
|
||||||
|
import platform
|
||||||
|
import os
|
||||||
|
from typing import Any, OrderedDict
|
||||||
|
|
||||||
|
|
||||||
|
class Prop(OrderedDict):
|
||||||
|
def __init__(self, props: str = ...) -> None:
|
||||||
|
super().__init__()
|
||||||
|
for i, line in enumerate(props.splitlines(False)):
|
||||||
|
if '=' in line:
|
||||||
|
k, v = line.split('=', 1)
|
||||||
|
self[k] = v
|
||||||
|
else:
|
||||||
|
self[f".{i}"] = line
|
||||||
|
|
||||||
|
def __setattr__(self, __name: str, __value: Any) -> None:
|
||||||
|
self[__name] = __value
|
||||||
|
|
||||||
|
def __repr__(self):
|
||||||
|
return '\n'.join(f'{item}={self[item]}' for item in self)
|
||||||
|
|
||||||
|
|
||||||
|
is_x86_64 = platform.machine() in ("AMD64", "x86_64")
|
||||||
|
host_abi = "x64" if is_x86_64 else "arm64"
|
||||||
|
arch = sys.argv[1]
|
||||||
|
magisk_zip = sys.argv[2]
|
||||||
|
workdir = Path(sys.argv[3])
|
||||||
|
workdir.mkdir(parents=True, exist_ok=True)
|
||||||
|
|
||||||
|
abi_map = {"x64": ["x86_64", "x86"], "arm64": ["arm64-v8a", "armeabi-v7a"]}
|
||||||
|
|
||||||
|
|
||||||
|
def extract_as(zip, name, as_name, dir):
|
||||||
|
info = zip.getinfo(name)
|
||||||
|
info.filename = as_name
|
||||||
|
zip.extract(info, workdir / dir)
|
||||||
|
|
||||||
|
|
||||||
|
with zipfile.ZipFile(magisk_zip) as zip:
|
||||||
|
props = Prop(zip.comment.decode().replace('\000', '\n'))
|
||||||
|
versionName = props.get("version")
|
||||||
|
versionCode = props.get("versionCode")
|
||||||
|
print(f"Magisk version: {versionName} ({versionCode})", flush=True)
|
||||||
|
if 'WSA_WORK_ENV' in os.environ and Path(os.environ['WSA_WORK_ENV']).is_file():
|
||||||
|
with open(os.environ['WSA_WORK_ENV'], 'r') as environ_file:
|
||||||
|
env = Prop(environ_file.read())
|
||||||
|
env.MAGISK_VERSION_NAME = versionName
|
||||||
|
env.MAGISK_VERSION_CODE = versionCode
|
||||||
|
with open(os.environ['WSA_WORK_ENV'], 'w') as environ_file:
|
||||||
|
environ_file.write(str(env))
|
||||||
|
extract_as(zip, f"lib/{ abi_map[arch][0] }/libmagisk64.so", "magisk64", "magisk")
|
||||||
|
extract_as(zip, f"lib/{ abi_map[arch][1] }/libmagisk32.so", "magisk32", "magisk")
|
||||||
|
extract_as(zip, f"lib/{ abi_map[arch][0] }/libmagiskinit.so", "magiskinit", "magisk")
|
||||||
|
extract_as(zip, f"lib/{ abi_map[host_abi][0] }/libmagiskboot.so", "magiskboot", "magisk")
|
||||||
109
MagiskOnWSA/DLL/scripts/extractWSA.py
Normal file
109
MagiskOnWSA/DLL/scripts/extractWSA.py
Normal file
@ -0,0 +1,109 @@
|
|||||||
|
#!/usr/bin/python3
|
||||||
|
#
|
||||||
|
# This file is part of MagiskOnWSALocal.
|
||||||
|
#
|
||||||
|
# MagiskOnWSALocal is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU Affero General Public License as
|
||||||
|
# published by the Free Software Foundation, either version 3 of the
|
||||||
|
# License, or (at your option) any later version.
|
||||||
|
#
|
||||||
|
# MagiskOnWSALocal is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU Affero General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU Affero General Public License
|
||||||
|
# along with MagiskOnWSALocal. If not, see <https://www.gnu.org/licenses/>.
|
||||||
|
#
|
||||||
|
# Copyright (C) 2023 LSPosed Contributors
|
||||||
|
#
|
||||||
|
|
||||||
|
import os
|
||||||
|
import sys
|
||||||
|
from typing import Any, OrderedDict
|
||||||
|
|
||||||
|
import zipfile
|
||||||
|
from pathlib import Path
|
||||||
|
import re
|
||||||
|
import shutil
|
||||||
|
|
||||||
|
|
||||||
|
class Prop(OrderedDict):
|
||||||
|
def __init__(self, props: str = ...) -> None:
|
||||||
|
super().__init__()
|
||||||
|
for i, line in enumerate(props.splitlines(False)):
|
||||||
|
if '=' in line:
|
||||||
|
k, v = line.split('=', 1)
|
||||||
|
self[k] = v
|
||||||
|
else:
|
||||||
|
self[f".{i}"] = line
|
||||||
|
|
||||||
|
def __setattr__(self, __name: str, __value: Any) -> None:
|
||||||
|
self[__name] = __value
|
||||||
|
|
||||||
|
def __repr__(self):
|
||||||
|
return '\n'.join(f'{item}={self[item]}' for item in self)
|
||||||
|
|
||||||
|
|
||||||
|
arch = sys.argv[1]
|
||||||
|
|
||||||
|
zip_name = ""
|
||||||
|
wsa_zip_path = Path(sys.argv[2])
|
||||||
|
rootdir = Path(sys.argv[3])
|
||||||
|
env_file = Path(sys.argv[4])
|
||||||
|
|
||||||
|
workdir = rootdir / "wsa"
|
||||||
|
archdir = Path(workdir / arch)
|
||||||
|
pridir = workdir / archdir / 'pri'
|
||||||
|
xmldir = workdir / archdir / 'xml'
|
||||||
|
if not Path(rootdir).is_dir():
|
||||||
|
rootdir.mkdir()
|
||||||
|
|
||||||
|
if Path(workdir).is_dir():
|
||||||
|
shutil.rmtree(workdir)
|
||||||
|
else:
|
||||||
|
workdir.unlink(missing_ok=True)
|
||||||
|
|
||||||
|
if not Path(workdir).is_dir():
|
||||||
|
workdir.mkdir()
|
||||||
|
|
||||||
|
if not Path(archdir).is_dir():
|
||||||
|
archdir.mkdir()
|
||||||
|
uid = os.getuid()
|
||||||
|
workdir_rw = os.access(workdir, os.W_OK)
|
||||||
|
|
||||||
|
with zipfile.ZipFile(wsa_zip_path) as zip:
|
||||||
|
for f in zip.filelist:
|
||||||
|
filename_lower = f.filename.lower()
|
||||||
|
if arch in filename_lower:
|
||||||
|
zip_name = f.filename
|
||||||
|
if not Path(workdir / zip_name).is_file():
|
||||||
|
print(f"unzipping {zip_name} to {workdir}", flush=True)
|
||||||
|
zip_path = zip.extract(f, workdir)
|
||||||
|
with zipfile.ZipFile(zip_path) as wsa_zip:
|
||||||
|
stat = Path(zip_path).stat()
|
||||||
|
print(f"unzipping from {zip_path}", flush=True)
|
||||||
|
wsa_zip.extractall(archdir)
|
||||||
|
ver_no = zip_name.split("_")
|
||||||
|
long_ver = ver_no[1]
|
||||||
|
rel = ver_no[3].split(".")
|
||||||
|
rel_long = str(rel[0])
|
||||||
|
with open(env_file, 'r') as environ_file:
|
||||||
|
env = Prop(environ_file.read())
|
||||||
|
env.WSA_VER = long_ver
|
||||||
|
env.WSA_REL = rel_long
|
||||||
|
with open(env_file, 'w') as environ_file:
|
||||||
|
environ_file.write(str(env))
|
||||||
|
if 'language' in filename_lower or 'scale' in filename_lower:
|
||||||
|
name = f.filename.split("_")[2].split(".")[0]
|
||||||
|
zip.extract(f, workdir)
|
||||||
|
with zipfile.ZipFile(workdir / f.filename) as l:
|
||||||
|
for g in l.filelist:
|
||||||
|
if g.filename == 'resources.pri':
|
||||||
|
g.filename = f'resources.{name}.pri'
|
||||||
|
l.extract(g, pridir)
|
||||||
|
elif g.filename == 'AppxManifest.xml':
|
||||||
|
g.filename = f'resources.{name}.xml'
|
||||||
|
l.extract(g, xmldir)
|
||||||
|
elif re.search(u'Images/.+.png', g.filename):
|
||||||
|
l.extract(g, archdir)
|
||||||
96
MagiskOnWSA/DLL/scripts/fixGappsProp.py
Normal file
96
MagiskOnWSA/DLL/scripts/fixGappsProp.py
Normal file
@ -0,0 +1,96 @@
|
|||||||
|
#!/usr/bin/python3
|
||||||
|
#
|
||||||
|
# This file is part of MagiskOnWSALocal.
|
||||||
|
#
|
||||||
|
# MagiskOnWSALocal is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU Affero General Public License as
|
||||||
|
# published by the Free Software Foundation, either version 3 of the
|
||||||
|
# License, or (at your option) any later version.
|
||||||
|
#
|
||||||
|
# MagiskOnWSALocal is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU Affero General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU Affero General Public License
|
||||||
|
# along with MagiskOnWSALocal. If not, see <https://www.gnu.org/licenses/>.
|
||||||
|
#
|
||||||
|
# Copyright (C) 2023 LSPosed Contributors
|
||||||
|
#
|
||||||
|
|
||||||
|
from __future__ import annotations
|
||||||
|
from io import TextIOWrapper
|
||||||
|
from typing import OrderedDict
|
||||||
|
from pathlib import Path
|
||||||
|
import sys
|
||||||
|
class Prop(OrderedDict):
|
||||||
|
def __init__(self, file: TextIOWrapper) -> None:
|
||||||
|
super().__init__()
|
||||||
|
for i, line in enumerate(file.read().splitlines(False)):
|
||||||
|
if '=' in line:
|
||||||
|
k, v = line.split('=', 1)
|
||||||
|
self[k] = v
|
||||||
|
else:
|
||||||
|
self[f".{i}"] = line
|
||||||
|
|
||||||
|
def __str__(self) -> str:
|
||||||
|
return '\n'.join([v if k.startswith('.') else f"{k}={v}" for k, v in self.items()])
|
||||||
|
|
||||||
|
def __iadd__(self, other: str) -> Prop:
|
||||||
|
self[f".{len(self)}"] = other
|
||||||
|
return self
|
||||||
|
|
||||||
|
new_props = {
|
||||||
|
("product", "brand"): "google",
|
||||||
|
("system", "brand"): "google",
|
||||||
|
("product", "manufacturer"): "Google",
|
||||||
|
("system", "manufacturer"): "Google",
|
||||||
|
("build", "product"): sys.argv[2],
|
||||||
|
("product", "name"): sys.argv[2],
|
||||||
|
("system", "name"): sys.argv[2],
|
||||||
|
("product", "device"): sys.argv[2],
|
||||||
|
("system", "device"): sys.argv[2],
|
||||||
|
("product", "model"): sys.argv[3],
|
||||||
|
("system", "model"): sys.argv[3],
|
||||||
|
("build", "flavor"): sys.argv[2] + "-user"
|
||||||
|
}
|
||||||
|
|
||||||
|
def description(sec: str, p: Prop) -> str:
|
||||||
|
return f"{p[f'ro.{sec}.build.flavor']} {p[f'ro.{sec}.build.version.release_or_codename']} {p[f'ro.{sec}.build.id']} {p[f'ro.{sec}.build.version.incremental']} {p[f'ro.{sec}.build.tags']}"
|
||||||
|
|
||||||
|
|
||||||
|
def fingerprint(sec: str, p: Prop) -> str:
|
||||||
|
return f"""{p[f"ro.product.{sec}.brand"]}/{p[f"ro.product.{sec}.name"]}/{p[f"ro.product.{sec}.device"]}:{p[f"ro.{sec}.build.version.release"]}/{p[f"ro.{sec}.build.id"]}/{p[f"ro.{sec}.build.version.incremental"]}:{p[f"ro.{sec}.build.type"]}/{p[f"ro.{sec}.build.tags"]}"""
|
||||||
|
|
||||||
|
|
||||||
|
def fix_prop(sec, prop):
|
||||||
|
if not Path(prop).is_file():
|
||||||
|
return
|
||||||
|
|
||||||
|
print(f"fixing {prop}", flush=True)
|
||||||
|
with open(prop, 'r') as f:
|
||||||
|
p = Prop(f)
|
||||||
|
|
||||||
|
p += "# extra props added by MagiskOnWSA and YT-Advanced/WSA-Script"
|
||||||
|
|
||||||
|
for k, v in new_props.items():
|
||||||
|
p[f"ro.{k[0]}.{k[1]}"] = v
|
||||||
|
|
||||||
|
if k[0] == "build":
|
||||||
|
p[f"ro.{sec}.{k[0]}.{k[1]}"] = v
|
||||||
|
elif k[0] == "product":
|
||||||
|
p[f"ro.{k[0]}.{sec}.{k[1]}"] = v
|
||||||
|
|
||||||
|
p["ro.build.description"] = description(sec, p)
|
||||||
|
p[f"ro.build.fingerprint"] = fingerprint(sec, p)
|
||||||
|
p[f"ro.{sec}.build.description"] = description(sec, p)
|
||||||
|
p[f"ro.{sec}.build.fingerprint"] = fingerprint(sec, p)
|
||||||
|
p[f"ro.bootimage.build.fingerprint"] = fingerprint(sec, p)
|
||||||
|
|
||||||
|
with open(prop, 'w') as f:
|
||||||
|
f.write(str(p))
|
||||||
|
|
||||||
|
|
||||||
|
sys_path = sys.argv[1]
|
||||||
|
for sec, prop in {"system": sys_path+"/system/build.prop", "vendor": sys_path+"/vendor/build.prop", "odm": sys_path+"/vendor/odm/etc/build.prop", "vendor_dlkm": sys_path+"/vendor/vendor_dlkm/etc/build.prop"}.items():
|
||||||
|
fix_prop(sec, prop)
|
||||||
79
MagiskOnWSA/DLL/scripts/generateGappsLink.py
Normal file
79
MagiskOnWSA/DLL/scripts/generateGappsLink.py
Normal file
@ -0,0 +1,79 @@
|
|||||||
|
#!/usr/bin/python3
|
||||||
|
#
|
||||||
|
# This file is part of MagiskOnWSALocal.
|
||||||
|
#
|
||||||
|
# MagiskOnWSALocal is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU Affero General Public License as
|
||||||
|
# published by the Free Software Foundation, either version 3 of the
|
||||||
|
# License, or (at your option) any later version.
|
||||||
|
#
|
||||||
|
# MagiskOnWSALocal is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU Affero General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU Affero General Public License
|
||||||
|
# along with MagiskOnWSALocal. If not, see <https://www.gnu.org/licenses/>.
|
||||||
|
#
|
||||||
|
# Copyright (C) 2024 LSPosed Contributors
|
||||||
|
#
|
||||||
|
|
||||||
|
from datetime import datetime
|
||||||
|
import sys
|
||||||
|
|
||||||
|
import requests
|
||||||
|
import json
|
||||||
|
import re
|
||||||
|
from pathlib import Path
|
||||||
|
|
||||||
|
|
||||||
|
class BearerAuth(requests.auth.AuthBase):
|
||||||
|
def __init__(self, token):
|
||||||
|
self.token = token
|
||||||
|
|
||||||
|
def __call__(self, r):
|
||||||
|
r.headers["authorization"] = "Bearer " + self.token
|
||||||
|
return r
|
||||||
|
|
||||||
|
|
||||||
|
github_auth = None
|
||||||
|
if Path.cwd().joinpath('token').exists():
|
||||||
|
with open(Path.cwd().joinpath('token'), 'r') as token_file:
|
||||||
|
github_auth = BearerAuth(token_file.read())
|
||||||
|
print("Using token file for authentication", flush=True)
|
||||||
|
arch = sys.argv[1]
|
||||||
|
arg2 = sys.argv[2]
|
||||||
|
download_dir = Path.cwd().parent / "download" if arg2 == "" else Path(arg2)
|
||||||
|
tempScript = sys.argv[3]
|
||||||
|
android_api = sys.argv[4]
|
||||||
|
file_name = sys.argv[5]
|
||||||
|
print(f"Generating GApps download link: arch={arch}", flush=True)
|
||||||
|
abi_map = {"x64": "x86_64", "arm64": "arm64"}
|
||||||
|
android_api_map = {"33": "13.0", "34": "14.0"}
|
||||||
|
release = android_api_map[android_api]
|
||||||
|
res = requests.get(f"https://api.github.com/repos/LSPosed/WSA-Addon/releases/latest", auth=github_auth)
|
||||||
|
json_data = json.loads(res.content)
|
||||||
|
headers = res.headers
|
||||||
|
x_ratelimit_remaining = headers["x-ratelimit-remaining"]
|
||||||
|
if res.status_code == 200:
|
||||||
|
download_files = {}
|
||||||
|
assets = json_data["assets"]
|
||||||
|
for asset in assets:
|
||||||
|
if re.match(f'gapps.*{release}.*\.rc$', asset["name"]):
|
||||||
|
download_files[asset["name"]] = asset["browser_download_url"]
|
||||||
|
elif re.match(f'gapps.*{release}.*{abi_map[arch]}.*\.img$', asset["name"]):
|
||||||
|
download_files[asset["name"]] = asset["browser_download_url"]
|
||||||
|
with open(download_dir/tempScript, 'a') as f:
|
||||||
|
for key, value in download_files.items():
|
||||||
|
print(f"download link: {value}\npath: {download_dir / key}\n", flush=True)
|
||||||
|
f.writelines(value + '\n')
|
||||||
|
f.writelines(f' dir={download_dir}\n')
|
||||||
|
f.writelines(f' out={key}\n')
|
||||||
|
elif res.status_code == 403 and x_ratelimit_remaining == '0':
|
||||||
|
message = json_data["message"]
|
||||||
|
print(f"Github API Error: {message}", flush=True)
|
||||||
|
ratelimit_reset = headers["x-ratelimit-reset"]
|
||||||
|
ratelimit_reset = datetime.fromtimestamp(int(ratelimit_reset))
|
||||||
|
print(
|
||||||
|
f"The current rate limit window resets in {ratelimit_reset}", flush=True)
|
||||||
|
exit(1)
|
||||||
109
MagiskOnWSA/DLL/scripts/generateKernelSULink.py
Normal file
109
MagiskOnWSA/DLL/scripts/generateKernelSULink.py
Normal file
@ -0,0 +1,109 @@
|
|||||||
|
#!/usr/bin/python3
|
||||||
|
#
|
||||||
|
# This file is part of MagiskOnWSALocal.
|
||||||
|
#
|
||||||
|
# MagiskOnWSALocal is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU Affero General Public License as
|
||||||
|
# published by the Free Software Foundation, either version 3 of the
|
||||||
|
# License, or (at your option) any later version.
|
||||||
|
#
|
||||||
|
# MagiskOnWSALocal is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU Affero General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU Affero General Public License
|
||||||
|
# along with MagiskOnWSALocal. If not, see <https://www.gnu.org/licenses/>.
|
||||||
|
#
|
||||||
|
# Copyright (C) 2024 LSPosed Contributors
|
||||||
|
#
|
||||||
|
|
||||||
|
from datetime import datetime
|
||||||
|
import sys
|
||||||
|
import os
|
||||||
|
from typing import Any, OrderedDict
|
||||||
|
|
||||||
|
import requests
|
||||||
|
import json
|
||||||
|
import re
|
||||||
|
from pathlib import Path
|
||||||
|
from packaging import version
|
||||||
|
|
||||||
|
|
||||||
|
class Prop(OrderedDict):
|
||||||
|
def __init__(self, props: str = ...) -> None:
|
||||||
|
super().__init__()
|
||||||
|
for i, line in enumerate(props.splitlines(False)):
|
||||||
|
if '=' in line:
|
||||||
|
k, v = line.split('=', 1)
|
||||||
|
self[k] = v
|
||||||
|
else:
|
||||||
|
self[f".{i}"] = line
|
||||||
|
|
||||||
|
def __setattr__(self, __name: str, __value: Any) -> None:
|
||||||
|
self[__name] = __value
|
||||||
|
|
||||||
|
def __repr__(self):
|
||||||
|
return '\n'.join(f'{item}={self[item]}' for item in self)
|
||||||
|
|
||||||
|
|
||||||
|
arch = sys.argv[1]
|
||||||
|
arg2 = sys.argv[2]
|
||||||
|
download_dir = Path.cwd().parent / "download" if arg2 == "" else Path(arg2)
|
||||||
|
tempScript = sys.argv[3]
|
||||||
|
kernelVersion = sys.argv[4]
|
||||||
|
file_name = sys.argv[5]
|
||||||
|
abi_map = {"x64": "x86_64", "arm64": "arm64"}
|
||||||
|
print(
|
||||||
|
f"Generating KernelSU download link: arch={abi_map[arch]}, kernel version={kernelVersion}", flush=True)
|
||||||
|
res = requests.get(
|
||||||
|
f"https://api.github.com/repos/tiann/KernelSU/releases/latest")
|
||||||
|
json_data = json.loads(res.content)
|
||||||
|
headers = res.headers
|
||||||
|
x_ratelimit_remaining = headers["x-ratelimit-remaining"]
|
||||||
|
kernel_ver = 0
|
||||||
|
if res.status_code == 200:
|
||||||
|
link = ""
|
||||||
|
assets = json_data["assets"]
|
||||||
|
for asset in assets:
|
||||||
|
asset_name = asset["name"]
|
||||||
|
if re.match(f'kernel-WSA-{abi_map[arch]}-{kernelVersion}.*\.zip$', asset_name) and asset["content_type"] == "application/zip":
|
||||||
|
tmp_kernel_ver = re.search(
|
||||||
|
u'\d{1}.\d{1,}.\d{1,}.\d{1,}', asset_name.split("-")[3]).group()
|
||||||
|
if (kernel_ver == 0):
|
||||||
|
kernel_ver = tmp_kernel_ver
|
||||||
|
elif version.parse(kernel_ver) < version.parse(tmp_kernel_ver):
|
||||||
|
kernel_ver = tmp_kernel_ver
|
||||||
|
print(f"Kernel version: {kernel_ver}", flush=True)
|
||||||
|
for asset in assets:
|
||||||
|
if re.match(f'kernel-WSA-{abi_map[arch]}-{kernel_ver}.*\.zip$', asset["name"]) and asset["content_type"] == "application/zip":
|
||||||
|
link = asset["browser_download_url"]
|
||||||
|
break
|
||||||
|
if link == "":
|
||||||
|
print(
|
||||||
|
f"Error: No KernelSU release found for arch={abi_map[arch]}, kernel version={kernelVersion}", flush=True)
|
||||||
|
exit(1)
|
||||||
|
release_name = json_data["name"]
|
||||||
|
with open(os.environ['WSA_WORK_ENV'], 'r') as environ_file:
|
||||||
|
env = Prop(environ_file.read())
|
||||||
|
env.KERNELSU_VER = release_name
|
||||||
|
with open(os.environ['WSA_WORK_ENV'], 'w') as environ_file:
|
||||||
|
environ_file.write(str(env))
|
||||||
|
elif res.status_code == 403 and x_ratelimit_remaining == '0':
|
||||||
|
message = json_data["message"]
|
||||||
|
print(f"Github API Error: {message}", flush=True)
|
||||||
|
ratelimit_reset = headers["x-ratelimit-reset"]
|
||||||
|
ratelimit_reset = datetime.fromtimestamp(int(ratelimit_reset))
|
||||||
|
print(
|
||||||
|
f"The current rate limit window resets in {ratelimit_reset}", flush=True)
|
||||||
|
exit(1)
|
||||||
|
|
||||||
|
print(f"download link: {link}", flush=True)
|
||||||
|
|
||||||
|
with open(download_dir/tempScript, 'a') as f:
|
||||||
|
f.writelines(f'{link}\n')
|
||||||
|
f.writelines(f' dir={download_dir}\n')
|
||||||
|
f.writelines(f' out={file_name}\n')
|
||||||
|
# f.writelines(f'{apk}\n')
|
||||||
|
# f.writelines(f' dir={download_dir}\n')
|
||||||
|
# f.writelines(f' out=KernelSU.apk\n')
|
||||||
103
MagiskOnWSA/DLL/scripts/generateMagiskLink.py
Normal file
103
MagiskOnWSA/DLL/scripts/generateMagiskLink.py
Normal file
@ -0,0 +1,103 @@
|
|||||||
|
#!/usr/bin/python3
|
||||||
|
#
|
||||||
|
# This file is part of MagiskOnWSALocal.
|
||||||
|
#
|
||||||
|
# MagiskOnWSALocal is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU Affero General Public License as
|
||||||
|
# published by the Free Software Foundation, either version 3 of the
|
||||||
|
# License, or (at your option) any later version.
|
||||||
|
#
|
||||||
|
# MagiskOnWSALocal is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU Affero General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU Affero General Public License
|
||||||
|
# along with MagiskOnWSALocal. If not, see <https://www.gnu.org/licenses/>.
|
||||||
|
#
|
||||||
|
# Copyright (C) 2023 LSPosed Contributors
|
||||||
|
#
|
||||||
|
|
||||||
|
from datetime import datetime
|
||||||
|
import re
|
||||||
|
import sys
|
||||||
|
|
||||||
|
import json
|
||||||
|
import requests
|
||||||
|
from pathlib import Path
|
||||||
|
|
||||||
|
#Android header
|
||||||
|
headers = {
|
||||||
|
'User-Agent': 'Mozilla/5.0 (Linux; Android 13; Pixel 5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.163 Mobile Safari/537.36',
|
||||||
|
}
|
||||||
|
|
||||||
|
class BearerAuth(requests.auth.AuthBase):
|
||||||
|
def __init__(self, token):
|
||||||
|
self.token = token
|
||||||
|
|
||||||
|
def __call__(self, r):
|
||||||
|
r.headers["authorization"] = "Bearer " + self.token
|
||||||
|
return r
|
||||||
|
|
||||||
|
|
||||||
|
github_auth = None
|
||||||
|
if Path.cwd().joinpath('token').exists():
|
||||||
|
with open(Path.cwd().joinpath('token'), 'r') as token_file:
|
||||||
|
github_auth = BearerAuth(token_file.read())
|
||||||
|
print("Using token file for authentication", flush=True)
|
||||||
|
|
||||||
|
magisk_branch = sys.argv[1]
|
||||||
|
magisk_ver = sys.argv[2]
|
||||||
|
download_dir = Path.cwd().parent / \
|
||||||
|
"download" if sys.argv[3] == "" else Path(sys.argv[3])
|
||||||
|
tempScript = sys.argv[4]
|
||||||
|
download_files = {}
|
||||||
|
print(
|
||||||
|
f"Generating Magisk download link: release type={magisk_ver}", flush=True)
|
||||||
|
if not magisk_ver:
|
||||||
|
magisk_ver = "stable"
|
||||||
|
|
||||||
|
if magisk_branch == "vvb2060":
|
||||||
|
try:
|
||||||
|
magisk_link = json.loads(requests.get(
|
||||||
|
f"https://install.appcenter.ms/api/v0.1/apps/vvb2060/magisk/distribution_groups/public/releases/latest?is_install_page=true", headers=headers).content)['download_url']
|
||||||
|
download_files[f"magisk-{magisk_ver}.zip"] = magisk_link
|
||||||
|
except Exception:
|
||||||
|
print("Failed to fetch from AppCenter API...")
|
||||||
|
else:
|
||||||
|
try:
|
||||||
|
magisk_link = json.loads(requests.get(
|
||||||
|
f"https://github.com/{magisk_branch}/magisk-files/raw/master/{magisk_ver}.json").content)['magisk']['link']
|
||||||
|
download_files[f"magisk-{magisk_ver}.zip"] = magisk_link
|
||||||
|
except Exception:
|
||||||
|
print("Failed to fetch from GitHub API, fallbacking to jsdelivr...")
|
||||||
|
magisk_link = json.loads(requests.get(
|
||||||
|
f"https://fastly.jsdelivr.net/gh/topjohnwu/magisk-files@master/{magisk_ver}.json").content)['magisk']['link']
|
||||||
|
download_files[f"magisk-{magisk_ver}.zip"] = magisk_link
|
||||||
|
res = requests.get(
|
||||||
|
f"https://api.github.com/repos/LSPosed/WSA-Addon/releases/latest", auth=github_auth)
|
||||||
|
json_data = json.loads(res.content)
|
||||||
|
headers = res.headers
|
||||||
|
x_ratelimit_remaining = headers["x-ratelimit-remaining"]
|
||||||
|
if res.status_code == 200:
|
||||||
|
assets = json_data["assets"]
|
||||||
|
for asset in assets:
|
||||||
|
if re.match(f'cust.img$', asset["name"]):
|
||||||
|
download_files[asset["name"]] = asset["browser_download_url"]
|
||||||
|
break
|
||||||
|
|
||||||
|
elif res.status_code == 403 and x_ratelimit_remaining == '0':
|
||||||
|
message = json_data["message"]
|
||||||
|
print(f"Github API Error: {message}", flush=True)
|
||||||
|
ratelimit_reset = headers["x-ratelimit-reset"]
|
||||||
|
ratelimit_reset = datetime.fromtimestamp(int(ratelimit_reset))
|
||||||
|
print(
|
||||||
|
f"The current rate limit window resets in {ratelimit_reset}", flush=True)
|
||||||
|
exit(1)
|
||||||
|
with open(download_dir/tempScript, 'a') as f:
|
||||||
|
for key, value in download_files.items():
|
||||||
|
print(
|
||||||
|
f"download link: {value}\npath: {download_dir / key}\n", flush=True)
|
||||||
|
f.writelines(value + '\n')
|
||||||
|
f.writelines(f' dir={download_dir}\n')
|
||||||
|
f.writelines(f' out={key}\n')
|
||||||
191
MagiskOnWSA/DLL/scripts/generateWSALinks.py
Normal file
191
MagiskOnWSA/DLL/scripts/generateWSALinks.py
Normal file
@ -0,0 +1,191 @@
|
|||||||
|
#!/usr/bin/python3
|
||||||
|
#
|
||||||
|
# This file is part of MagiskOnWSALocal.
|
||||||
|
#
|
||||||
|
# MagiskOnWSALocal is free software: you can redistribute it and/or modify
|
||||||
|
# it under the terms of the GNU Affero General Public License as
|
||||||
|
# published by the Free Software Foundation, either version 3 of the
|
||||||
|
# License, or (at your option) any later version.
|
||||||
|
#
|
||||||
|
# MagiskOnWSALocal is distributed in the hope that it will be useful,
|
||||||
|
# but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
# GNU Affero General Public License for more details.
|
||||||
|
#
|
||||||
|
# You should have received a copy of the GNU Affero General Public License
|
||||||
|
# along with MagiskOnWSALocal. If not, see <https://www.gnu.org/licenses/>.
|
||||||
|
#
|
||||||
|
# Copyright (C) 2024 LSPosed Contributors
|
||||||
|
#
|
||||||
|
|
||||||
|
import html
|
||||||
|
import logging
|
||||||
|
import re
|
||||||
|
import sys
|
||||||
|
|
||||||
|
from pathlib import Path
|
||||||
|
from threading import Thread
|
||||||
|
from typing import Any, OrderedDict
|
||||||
|
from xml.dom import minidom
|
||||||
|
|
||||||
|
from requests import Session
|
||||||
|
from packaging import version
|
||||||
|
|
||||||
|
|
||||||
|
class Prop(OrderedDict):
|
||||||
|
def __init__(self, props: str = ...) -> None:
|
||||||
|
super().__init__()
|
||||||
|
for i, line in enumerate(props.splitlines(False)):
|
||||||
|
if '=' in line:
|
||||||
|
k, v = line.split('=', 1)
|
||||||
|
self[k] = v
|
||||||
|
else:
|
||||||
|
self[f".{i}"] = line
|
||||||
|
|
||||||
|
def __setattr__(self, __name: str, __value: Any) -> None:
|
||||||
|
self[__name] = __value
|
||||||
|
|
||||||
|
def __repr__(self):
|
||||||
|
return '\n'.join(f'{item}={self[item]}' for item in self)
|
||||||
|
|
||||||
|
|
||||||
|
logging.captureWarnings(True)
|
||||||
|
arch = sys.argv[1]
|
||||||
|
|
||||||
|
release_name_map = {"retail": "Retail", "RP": "Release Preview",
|
||||||
|
"WIS": "Insider Slow", "WIF": "Insider Fast", "latest": "Insider Private"}
|
||||||
|
release_type = sys.argv[2] if sys.argv[2] != "" else "Retail"
|
||||||
|
release_name = release_name_map[release_type]
|
||||||
|
download_dir = Path.cwd().parent / \
|
||||||
|
"download" if sys.argv[3] == "" else Path(sys.argv[3])
|
||||||
|
ms_account_conf = download_dir/".ms_account"
|
||||||
|
tempScript = sys.argv[4]
|
||||||
|
cat_id = '858014f3-3934-4abe-8078-4aa193e74ca8'
|
||||||
|
user = ''
|
||||||
|
session = Session()
|
||||||
|
session.verify = False
|
||||||
|
if ms_account_conf.is_file():
|
||||||
|
with open(ms_account_conf, "r") as f:
|
||||||
|
conf = Prop(f.read())
|
||||||
|
user = conf.get('user_code')
|
||||||
|
print(
|
||||||
|
f"Generating WSA download link: arch={arch} release_type={release_name}\n", flush=True)
|
||||||
|
with open(Path.cwd().parent / ("xml/GetCookie.xml"), "r") as f:
|
||||||
|
cookie_content = f.read().format(user)
|
||||||
|
|
||||||
|
out = session.post(
|
||||||
|
'https://fe3.delivery.mp.microsoft.com/ClientWebService/client.asmx',
|
||||||
|
data=cookie_content,
|
||||||
|
headers={'Content-Type': 'application/soap+xml; charset=utf-8'}
|
||||||
|
)
|
||||||
|
doc = minidom.parseString(out.text)
|
||||||
|
cookie = doc.getElementsByTagName('EncryptedData')[0].firstChild.nodeValue
|
||||||
|
|
||||||
|
with open(Path.cwd().parent / "xml/WUIDRequest.xml", "r") as f:
|
||||||
|
cat_id_content = f.read().format(user, cookie, cat_id, release_type)
|
||||||
|
|
||||||
|
out = session.post(
|
||||||
|
'https://fe3.delivery.mp.microsoft.com/ClientWebService/client.asmx',
|
||||||
|
data=cat_id_content,
|
||||||
|
headers={'Content-Type': 'application/soap+xml; charset=utf-8'}
|
||||||
|
)
|
||||||
|
|
||||||
|
doc = minidom.parseString(html.unescape(out.text))
|
||||||
|
|
||||||
|
filenames = {}
|
||||||
|
for node in doc.getElementsByTagName('ExtendedUpdateInfo')[0].getElementsByTagName('Updates')[0].getElementsByTagName('Update'):
|
||||||
|
node_xml = node.getElementsByTagName('Xml')[0]
|
||||||
|
node_files = node_xml.getElementsByTagName('Files')
|
||||||
|
if not node_files:
|
||||||
|
continue
|
||||||
|
else:
|
||||||
|
for node_file in node_files[0].getElementsByTagName('File'):
|
||||||
|
if node_file.hasAttribute('InstallerSpecificIdentifier') and node_file.hasAttribute('FileName'):
|
||||||
|
filenames[node.getElementsByTagName('ID')[0].firstChild.nodeValue] = (f"{node_file.attributes['InstallerSpecificIdentifier'].value}_{node_file.attributes['FileName'].value}",
|
||||||
|
node_xml.getElementsByTagName('ExtendedProperties')[0].attributes['PackageIdentityName'].value)
|
||||||
|
|
||||||
|
identities = {}
|
||||||
|
for node in doc.getElementsByTagName('NewUpdates')[0].getElementsByTagName('UpdateInfo'):
|
||||||
|
node_xml = node.getElementsByTagName('Xml')[0]
|
||||||
|
if not node_xml.getElementsByTagName('SecuredFragment'):
|
||||||
|
continue
|
||||||
|
else:
|
||||||
|
id = node.getElementsByTagName('ID')[0].firstChild.nodeValue
|
||||||
|
update_identity = node_xml.getElementsByTagName('UpdateIdentity')[0]
|
||||||
|
if id in filenames:
|
||||||
|
fileinfo = filenames[id]
|
||||||
|
if fileinfo[0] not in identities:
|
||||||
|
identities[fileinfo[0]] = ([update_identity.attributes['UpdateID'].value,
|
||||||
|
update_identity.attributes['RevisionNumber'].value], fileinfo[1])
|
||||||
|
|
||||||
|
with open(Path.cwd().parent / "xml/FE3FileUrl.xml", "r") as f:
|
||||||
|
FE3_file_content = f.read()
|
||||||
|
|
||||||
|
if not download_dir.is_dir():
|
||||||
|
download_dir.mkdir()
|
||||||
|
|
||||||
|
tmpdownlist = open(download_dir/tempScript, 'a')
|
||||||
|
download_files = {}
|
||||||
|
|
||||||
|
|
||||||
|
def send_req(i, v, out_file_name):
|
||||||
|
out = session.post(
|
||||||
|
'https://fe3.delivery.mp.microsoft.com/ClientWebService/client.asmx/secured',
|
||||||
|
data=FE3_file_content.format(user, i, v, release_type),
|
||||||
|
headers={'Content-Type': 'application/soap+xml; charset=utf-8'}
|
||||||
|
)
|
||||||
|
doc = minidom.parseString(out.text)
|
||||||
|
for l in doc.getElementsByTagName("FileLocation"):
|
||||||
|
url = l.getElementsByTagName("Url")[0].firstChild.nodeValue
|
||||||
|
if len(url) != 99:
|
||||||
|
download_files[out_file_name] = url
|
||||||
|
|
||||||
|
|
||||||
|
threads = []
|
||||||
|
wsa_build_ver = 0
|
||||||
|
for filename, values in identities.items():
|
||||||
|
if re.match(f"MicrosoftCorporationII\.WindowsSubsystemForAndroid_.*\.msixbundle", filename):
|
||||||
|
tmp_wsa_build_ver = re.search(
|
||||||
|
u'\d{4}.\d{5}.\d{1,}.\d{1,}', filename).group()
|
||||||
|
if (wsa_build_ver == 0):
|
||||||
|
wsa_build_ver = tmp_wsa_build_ver
|
||||||
|
elif version.parse(wsa_build_ver) < version.parse(tmp_wsa_build_ver):
|
||||||
|
wsa_build_ver = tmp_wsa_build_ver
|
||||||
|
for filename, values in identities.items():
|
||||||
|
if re.match(f"Microsoft\.UI\.Xaml\..*_{arch}_.*\.appx", filename):
|
||||||
|
out_file_name = f"{values[1]}_{arch}.appx"
|
||||||
|
out_file = download_dir / out_file_name
|
||||||
|
elif re.match(f"Microsoft\.VCLibs\..+\.UWPDesktop_.*_{arch}_.*\.appx", filename):
|
||||||
|
out_file_name = f"{values[1]}_{arch}.appx"
|
||||||
|
out_file = download_dir / out_file_name
|
||||||
|
elif re.match(f"Microsoft\.VCLibs\..+_.*_{arch}_.*\.appx", filename):
|
||||||
|
out_file_name = f"{values[1]}_{arch}.appx"
|
||||||
|
out_file = download_dir / out_file_name
|
||||||
|
elif not release_name == 'latest' and re.match(f"MicrosoftCorporationII\.WindowsSubsystemForAndroid_.*\.msixbundle", filename):
|
||||||
|
tmp_wsa_build_ver = re.search(
|
||||||
|
u'\d{4}.\d{5}.\d{1,}.\d{1,}', filename).group()
|
||||||
|
if (wsa_build_ver != tmp_wsa_build_ver):
|
||||||
|
continue
|
||||||
|
version_splitted = wsa_build_ver.split(".")
|
||||||
|
major_ver = version_splitted[0]
|
||||||
|
minor_ver = version_splitted[1]
|
||||||
|
build_ver = version_splitted[2]
|
||||||
|
revision_ver = version_splitted[3]
|
||||||
|
out_file_name = f"wsa-{release_type}.zip"
|
||||||
|
out_file = download_dir / out_file_name
|
||||||
|
else:
|
||||||
|
continue
|
||||||
|
th = Thread(target=send_req, args=(
|
||||||
|
values[0][0], values[0][1], out_file_name))
|
||||||
|
threads.append(th)
|
||||||
|
th.daemon = True
|
||||||
|
th.start()
|
||||||
|
for th in threads:
|
||||||
|
th.join()
|
||||||
|
print(f'WSA Build Version={wsa_build_ver}\n', flush=True)
|
||||||
|
for key, value in download_files.items():
|
||||||
|
print(f"download link: {value}\npath: {download_dir / key}\n", flush=True)
|
||||||
|
tmpdownlist.writelines(value + '\n')
|
||||||
|
tmpdownlist.writelines(f' dir={download_dir}\n')
|
||||||
|
tmpdownlist.writelines(f' out={key}\n')
|
||||||
|
tmpdownlist.close()
|
||||||
2
MagiskOnWSA/DLL/scripts/init.lsp.magisk.rc
Normal file
2
MagiskOnWSA/DLL/scripts/init.lsp.magisk.rc
Normal file
@ -0,0 +1,2 @@
|
|||||||
|
on post-fs-data
|
||||||
|
exec u:r:magisk:s0 0 0 -- /system/bin/sh ${MAGISKTMP}/post-fs-data.sh
|
||||||
44
MagiskOnWSA/DLL/scripts/post-fs-data.sh
Normal file
44
MagiskOnWSA/DLL/scripts/post-fs-data.sh
Normal file
@ -0,0 +1,44 @@
|
|||||||
|
#!/bin/sh
|
||||||
|
MAGISKTMP=/sbin
|
||||||
|
[ -d /sbin ] || MAGISKTMP=/debug_ramdisk
|
||||||
|
MAGISKBIN=/data/adb/magisk
|
||||||
|
if [ ! -d /data/adb ]; then
|
||||||
|
mkdir -m 700 /data/adb
|
||||||
|
chcon u:object_r:adb_data_file:s0 /data/adb
|
||||||
|
fi
|
||||||
|
if [ ! -d $MAGISKBIN ]; then
|
||||||
|
# shellcheck disable=SC2174
|
||||||
|
mkdir -p -m 755 $MAGISKBIN
|
||||||
|
chcon u:object_r:system_file:s0 $MAGISKBIN
|
||||||
|
fi
|
||||||
|
ABI=$(getprop ro.product.cpu.abi)
|
||||||
|
for file in busybox magiskpolicy magiskboot magiskinit; do
|
||||||
|
[ -x "$MAGISKBIN/$file" ] || {
|
||||||
|
unzip -d $MAGISKBIN -oj $MAGISKTMP/stub.apk "lib/$ABI/lib$file.so"
|
||||||
|
mv $MAGISKBIN/lib$file.so $MAGISKBIN/$file
|
||||||
|
chmod 755 "$MAGISKBIN/$file"
|
||||||
|
}
|
||||||
|
done
|
||||||
|
for file in util_functions.sh boot_patch.sh; do
|
||||||
|
[ -x "$MAGISKBIN/$file" ] || {
|
||||||
|
unzip -d $MAGISKBIN -oj $MAGISKTMP/stub.apk "assets/$file"
|
||||||
|
chmod 755 "$MAGISKBIN/$file"
|
||||||
|
}
|
||||||
|
done
|
||||||
|
for file in "$MAGISKTMP"/*; do
|
||||||
|
if echo "$file" | grep -Eq "lsp_.+\.img"; then
|
||||||
|
foldername=$(basename "$file" .img)
|
||||||
|
mkdir -p "$MAGISKTMP/$foldername"
|
||||||
|
mount -t auto -o ro,loop "$file" "$MAGISKTMP/$foldername"
|
||||||
|
"$MAGISKTMP/$foldername/post-fs-data.sh" &
|
||||||
|
fi
|
||||||
|
done
|
||||||
|
wait
|
||||||
|
for file in "$MAGISKTMP"/*; do
|
||||||
|
if echo "$file" | grep -Eq "lsp_.+\.img"; then
|
||||||
|
foldername=$(basename "$file" .img)
|
||||||
|
umount "$MAGISKTMP/$foldername"
|
||||||
|
rm -rf "${MAGISKTMP:?}/${foldername:?}"
|
||||||
|
rm -f "$file"
|
||||||
|
fi
|
||||||
|
done
|
||||||
2
MagiskOnWSA/DLL/scripts/requirements.txt
Normal file
2
MagiskOnWSA/DLL/scripts/requirements.txt
Normal file
@ -0,0 +1,2 @@
|
|||||||
|
requests
|
||||||
|
packaging
|
||||||
5
MagiskOnWSA/DLL/scripts/sepolicy.rule
Normal file
5
MagiskOnWSA/DLL/scripts/sepolicy.rule
Normal file
@ -0,0 +1,5 @@
|
|||||||
|
allow gmscore_app gmscore_app vsock_socket { create connect write read }
|
||||||
|
allow gmscore_app device_config_runtime_native_boot_prop file read
|
||||||
|
allow gmscore_app system_server_tmpfs dir search
|
||||||
|
allow gmscore_app system_server_tmpfs file open
|
||||||
|
allow gmscore_app { system_server_tmpfs media_rw_data_file } filesystem getattr
|
||||||
37
MagiskOnWSA/DLL/xml/FE3FileUrl.xml
Normal file
37
MagiskOnWSA/DLL/xml/FE3FileUrl.xml
Normal file
@ -0,0 +1,37 @@
|
|||||||
|
<s:Envelope xmlns:a="http://www.w3.org/2005/08/addressing"
|
||||||
|
xmlns:s="http://www.w3.org/2003/05/soap-envelope">
|
||||||
|
<s:Header>
|
||||||
|
<a:Action s:mustUnderstand="1">http://www.microsoft.com/SoftwareDistribution/Server/ClientWebService/GetExtendedUpdateInfo2</a:Action>
|
||||||
|
<a:MessageID>urn:uuid:2cc99c2e-3b3e-4fb1-9e31-0cd30e6f43a0</a:MessageID>
|
||||||
|
<a:To s:mustUnderstand="1">https://fe3.delivery.mp.microsoft.com/ClientWebService/client.asmx/secured</a:To>
|
||||||
|
<o:Security s:mustUnderstand="1"
|
||||||
|
xmlns:o="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
|
||||||
|
<Timestamp xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
|
||||||
|
<Created>2017-08-01T00:29:01.868Z</Created>
|
||||||
|
<Expires>2017-08-01T00:34:01.868Z</Expires>
|
||||||
|
</Timestamp>
|
||||||
|
<wuws:WindowsUpdateTicketsToken wsu:id="ClientMSA"
|
||||||
|
xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd"
|
||||||
|
xmlns:wuws="http://schemas.microsoft.com/msus/2014/10/WindowsUpdateAuthorization">
|
||||||
|
<TicketType Name="MSA" Version="1.0" Policy="MBI_SSL">
|
||||||
|
<user>{}</user>
|
||||||
|
</TicketType>
|
||||||
|
</wuws:WindowsUpdateTicketsToken>
|
||||||
|
</o:Security>
|
||||||
|
</s:Header>
|
||||||
|
<s:Body>
|
||||||
|
<GetExtendedUpdateInfo2 xmlns="http://www.microsoft.com/SoftwareDistribution/Server/ClientWebService">
|
||||||
|
<updateIDs>
|
||||||
|
<UpdateIdentity>
|
||||||
|
<UpdateID>{}</UpdateID>
|
||||||
|
<RevisionNumber>{}</RevisionNumber>
|
||||||
|
</UpdateIdentity>
|
||||||
|
</updateIDs>
|
||||||
|
<infoTypes>
|
||||||
|
<XmlUpdateFragmentType>FileUrl</XmlUpdateFragmentType>
|
||||||
|
<XmlUpdateFragmentType>FileDecryption</XmlUpdateFragmentType>
|
||||||
|
</infoTypes>
|
||||||
|
<deviceAttributes>BranchReadinessLevel=CB;CurrentBranch=rs_prerelease;OEMModel=Virtual Machine;FlightRing={};AttrDataVer=21;SystemManufacturer=Microsoft Corporation;InstallLanguage=en-US;OSUILocale=en-US;InstallationType=Client;FlightingBranchName=external;FirmwareVersion=Hyper-V UEFI Release v2.5;SystemProductName=Virtual Machine;OSSkuId=48;FlightContent=Branch;App=WU;OEMName_Uncleaned=Microsoft Corporation;AppVer=10.0.22621.900;OSArchitecture=AMD64;SystemSKU=None;UpdateManagementGroup=2;IsFlightingEnabled=1;IsDeviceRetailDemo=0;TelemetryLevel=3;OSVersion=10.0.22621.900;DeviceFamily=Windows.Desktop;</deviceAttributes>
|
||||||
|
</GetExtendedUpdateInfo2>
|
||||||
|
</s:Body>
|
||||||
|
</s:Envelope>
|
||||||
37
MagiskOnWSA/DLL/xml/GetCookie.xml
Normal file
37
MagiskOnWSA/DLL/xml/GetCookie.xml
Normal file
@ -0,0 +1,37 @@
|
|||||||
|
<Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
|
||||||
|
xmlns:xsd="http://www.w3.org/2001/XMLSchema"
|
||||||
|
xmlns="http://www.w3.org/2003/05/soap-envelope">
|
||||||
|
<Header>
|
||||||
|
<Action d3p1:mustUnderstand="1"
|
||||||
|
xmlns:d3p1="http://www.w3.org/2003/05/soap-envelope"
|
||||||
|
xmlns="http://www.w3.org/2005/08/addressing">http://www.microsoft.com/SoftwareDistribution/Server/ClientWebService/GetCookie</Action>
|
||||||
|
<MessageID xmlns="http://www.w3.org/2005/08/addressing">urn:uuid:b9b43757-2247-4d7b-ae8f-a71ba8a22386</MessageID>
|
||||||
|
<To d3p1:mustUnderstand="1"
|
||||||
|
xmlns:d3p1="http://www.w3.org/2003/05/soap-envelope"
|
||||||
|
xmlns="http://www.w3.org/2005/08/addressing">https://fe3.delivery.mp.microsoft.com/ClientWebService/client.asmx</To>
|
||||||
|
<Security d3p1:mustUnderstand="1"
|
||||||
|
xmlns:d3p1="http://www.w3.org/2003/05/soap-envelope"
|
||||||
|
xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
|
||||||
|
<Timestamp xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
|
||||||
|
<Created>2017-12-02T00:16:15.210Z</Created>
|
||||||
|
<Expires>2017-12-29T06:25:43.943Z</Expires>
|
||||||
|
</Timestamp>
|
||||||
|
<WindowsUpdateTicketsToken d4p1:id="ClientMSA"
|
||||||
|
xmlns:d4p1="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd"
|
||||||
|
xmlns="http://schemas.microsoft.com/msus/2014/10/WindowsUpdateAuthorization">
|
||||||
|
<TicketType Name="MSA" Version="1.0" Policy="MBI_SSL">
|
||||||
|
<user>{}</user>
|
||||||
|
</TicketType>
|
||||||
|
</WindowsUpdateTicketsToken>
|
||||||
|
</Security>
|
||||||
|
</Header>
|
||||||
|
<Body>
|
||||||
|
<GetCookie xmlns="http://www.microsoft.com/SoftwareDistribution/Server/ClientWebService">
|
||||||
|
<oldCookie>
|
||||||
|
</oldCookie>
|
||||||
|
<lastChange>2015-10-21T17:01:07.1472913Z</lastChange>
|
||||||
|
<currentTime>2017-12-02T00:16:15.217Z</currentTime>
|
||||||
|
<protocolVersion>1.40</protocolVersion>
|
||||||
|
</GetCookie>
|
||||||
|
</Body>
|
||||||
|
</Envelope>
|
||||||
677
MagiskOnWSA/DLL/xml/WUIDRequest.xml
Normal file
677
MagiskOnWSA/DLL/xml/WUIDRequest.xml
Normal file
@ -0,0 +1,677 @@
|
|||||||
|
<s:Envelope xmlns:a="http://www.w3.org/2005/08/addressing"
|
||||||
|
xmlns:s="http://www.w3.org/2003/05/soap-envelope">
|
||||||
|
<s:Header>
|
||||||
|
<a:Action s:mustUnderstand="1">http://www.microsoft.com/SoftwareDistribution/Server/ClientWebService/SyncUpdates</a:Action>
|
||||||
|
<a:MessageID>urn:uuid:175df68c-4b91-41ee-b70b-f2208c65438e</a:MessageID>
|
||||||
|
<a:To s:mustUnderstand="1">https://fe3.delivery.mp.microsoft.com/ClientWebService/client.asmx</a:To>
|
||||||
|
<o:Security s:mustUnderstand="1"
|
||||||
|
xmlns:o="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
|
||||||
|
<Timestamp xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
|
||||||
|
<Created>2017-08-05T02:03:05.038Z</Created>
|
||||||
|
<Expires>2017-08-05T02:08:05.038Z</Expires>
|
||||||
|
</Timestamp>
|
||||||
|
<wuws:WindowsUpdateTicketsToken wsu:id="ClientMSA"
|
||||||
|
xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd"
|
||||||
|
xmlns:wuws="http://schemas.microsoft.com/msus/2014/10/WindowsUpdateAuthorization">
|
||||||
|
<TicketType Name="MSA" Version="1.0" Policy="MBI_SSL">
|
||||||
|
<user>{}</user>
|
||||||
|
</TicketType>
|
||||||
|
</wuws:WindowsUpdateTicketsToken>
|
||||||
|
</o:Security>
|
||||||
|
</s:Header>
|
||||||
|
<s:Body>
|
||||||
|
<SyncUpdates xmlns="http://www.microsoft.com/SoftwareDistribution/Server/ClientWebService">
|
||||||
|
<cookie>
|
||||||
|
<Expiration>2045-03-11T02:02:48Z</Expiration>
|
||||||
|
<EncryptedData>{}</EncryptedData>
|
||||||
|
</cookie>
|
||||||
|
<parameters>
|
||||||
|
<ExpressQuery>false</ExpressQuery>
|
||||||
|
<InstalledNonLeafUpdateIDs>
|
||||||
|
<int>1</int>
|
||||||
|
<int>2</int>
|
||||||
|
<int>3</int>
|
||||||
|
<int>11</int>
|
||||||
|
<int>19</int>
|
||||||
|
<int>544</int>
|
||||||
|
<int>549</int>
|
||||||
|
<int>2359974</int>
|
||||||
|
<int>2359977</int>
|
||||||
|
<int>5169044</int>
|
||||||
|
<int>8788830</int>
|
||||||
|
<int>23110993</int>
|
||||||
|
<int>23110994</int>
|
||||||
|
<int>54341900</int>
|
||||||
|
<int>54343656</int>
|
||||||
|
<int>59830006</int>
|
||||||
|
<int>59830007</int>
|
||||||
|
<int>59830008</int>
|
||||||
|
<int>60484010</int>
|
||||||
|
<int>62450018</int>
|
||||||
|
<int>62450019</int>
|
||||||
|
<int>62450020</int>
|
||||||
|
<int>66027979</int>
|
||||||
|
<int>66053150</int>
|
||||||
|
<int>97657898</int>
|
||||||
|
<int>98822896</int>
|
||||||
|
<int>98959022</int>
|
||||||
|
<int>98959023</int>
|
||||||
|
<int>98959024</int>
|
||||||
|
<int>98959025</int>
|
||||||
|
<int>98959026</int>
|
||||||
|
<int>104433538</int>
|
||||||
|
<int>104900364</int>
|
||||||
|
<int>105489019</int>
|
||||||
|
<int>117765322</int>
|
||||||
|
<int>129905029</int>
|
||||||
|
<int>130040031</int>
|
||||||
|
<int>132387090</int>
|
||||||
|
<int>132393049</int>
|
||||||
|
<int>133399034</int>
|
||||||
|
<int>138537048</int>
|
||||||
|
<int>140377312</int>
|
||||||
|
<int>143747671</int>
|
||||||
|
<int>158941041</int>
|
||||||
|
<int>158941042</int>
|
||||||
|
<int>158941043</int>
|
||||||
|
<int>158941044</int>
|
||||||
|
<int>159123858</int>
|
||||||
|
<int>159130928</int>
|
||||||
|
<int>164836897</int>
|
||||||
|
<int>164847386</int>
|
||||||
|
<int>164848327</int>
|
||||||
|
<int>164852241</int>
|
||||||
|
<int>164852246</int>
|
||||||
|
<int>164852252</int>
|
||||||
|
<int>164852253</int>
|
||||||
|
</InstalledNonLeafUpdateIDs>
|
||||||
|
<OtherCachedUpdateIDs>
|
||||||
|
<int>10</int>
|
||||||
|
<int>17</int>
|
||||||
|
<int>2359977</int>
|
||||||
|
<int>5143990</int>
|
||||||
|
<int>5169043</int>
|
||||||
|
<int>5169047</int>
|
||||||
|
<int>8806526</int>
|
||||||
|
<int>9125350</int>
|
||||||
|
<int>9154769</int>
|
||||||
|
<int>10809856</int>
|
||||||
|
<int>23110995</int>
|
||||||
|
<int>23110996</int>
|
||||||
|
<int>23110999</int>
|
||||||
|
<int>23111000</int>
|
||||||
|
<int>23111001</int>
|
||||||
|
<int>23111002</int>
|
||||||
|
<int>23111003</int>
|
||||||
|
<int>23111004</int>
|
||||||
|
<int>24513870</int>
|
||||||
|
<int>28880263</int>
|
||||||
|
<int>30077688</int>
|
||||||
|
<int>30486944</int>
|
||||||
|
<int>30526991</int>
|
||||||
|
<int>30528442</int>
|
||||||
|
<int>30530496</int>
|
||||||
|
<int>30530501</int>
|
||||||
|
<int>30530504</int>
|
||||||
|
<int>30530962</int>
|
||||||
|
<int>30535326</int>
|
||||||
|
<int>30536242</int>
|
||||||
|
<int>30539913</int>
|
||||||
|
<int>30545142</int>
|
||||||
|
<int>30545145</int>
|
||||||
|
<int>30545488</int>
|
||||||
|
<int>30546212</int>
|
||||||
|
<int>30547779</int>
|
||||||
|
<int>30548797</int>
|
||||||
|
<int>30548860</int>
|
||||||
|
<int>30549262</int>
|
||||||
|
<int>30551160</int>
|
||||||
|
<int>30551161</int>
|
||||||
|
<int>30551164</int>
|
||||||
|
<int>30553016</int>
|
||||||
|
<int>30553744</int>
|
||||||
|
<int>30554014</int>
|
||||||
|
<int>30559008</int>
|
||||||
|
<int>30559011</int>
|
||||||
|
<int>30560006</int>
|
||||||
|
<int>30560011</int>
|
||||||
|
<int>30561006</int>
|
||||||
|
<int>30563261</int>
|
||||||
|
<int>30565215</int>
|
||||||
|
<int>30578059</int>
|
||||||
|
<int>30664998</int>
|
||||||
|
<int>30677904</int>
|
||||||
|
<int>30681618</int>
|
||||||
|
<int>30682195</int>
|
||||||
|
<int>30685055</int>
|
||||||
|
<int>30702579</int>
|
||||||
|
<int>30708772</int>
|
||||||
|
<int>30709591</int>
|
||||||
|
<int>30711304</int>
|
||||||
|
<int>30715418</int>
|
||||||
|
<int>30720106</int>
|
||||||
|
<int>30720273</int>
|
||||||
|
<int>30732075</int>
|
||||||
|
<int>30866952</int>
|
||||||
|
<int>30866964</int>
|
||||||
|
<int>30870749</int>
|
||||||
|
<int>30877852</int>
|
||||||
|
<int>30878437</int>
|
||||||
|
<int>30890151</int>
|
||||||
|
<int>30892149</int>
|
||||||
|
<int>30990917</int>
|
||||||
|
<int>31049444</int>
|
||||||
|
<int>31190936</int>
|
||||||
|
<int>31196961</int>
|
||||||
|
<int>31197811</int>
|
||||||
|
<int>31198836</int>
|
||||||
|
<int>31202713</int>
|
||||||
|
<int>31203522</int>
|
||||||
|
<int>31205442</int>
|
||||||
|
<int>31205557</int>
|
||||||
|
<int>31207585</int>
|
||||||
|
<int>31208440</int>
|
||||||
|
<int>31208451</int>
|
||||||
|
<int>31209591</int>
|
||||||
|
<int>31210536</int>
|
||||||
|
<int>31211625</int>
|
||||||
|
<int>31212713</int>
|
||||||
|
<int>31213588</int>
|
||||||
|
<int>31218518</int>
|
||||||
|
<int>31219420</int>
|
||||||
|
<int>31220279</int>
|
||||||
|
<int>31220302</int>
|
||||||
|
<int>31222086</int>
|
||||||
|
<int>31227080</int>
|
||||||
|
<int>31229030</int>
|
||||||
|
<int>31238236</int>
|
||||||
|
<int>31254198</int>
|
||||||
|
<int>31258008</int>
|
||||||
|
<int>36436779</int>
|
||||||
|
<int>36437850</int>
|
||||||
|
<int>36464012</int>
|
||||||
|
<int>41916569</int>
|
||||||
|
<int>47249982</int>
|
||||||
|
<int>47283134</int>
|
||||||
|
<int>58577027</int>
|
||||||
|
<int>58578040</int>
|
||||||
|
<int>58578041</int>
|
||||||
|
<int>58628920</int>
|
||||||
|
<int>59107045</int>
|
||||||
|
<int>59125697</int>
|
||||||
|
<int>59142249</int>
|
||||||
|
<int>60466586</int>
|
||||||
|
<int>60478936</int>
|
||||||
|
<int>66450441</int>
|
||||||
|
<int>66467021</int>
|
||||||
|
<int>66479051</int>
|
||||||
|
<int>75202978</int>
|
||||||
|
<int>77436021</int>
|
||||||
|
<int>77449129</int>
|
||||||
|
<int>85159569</int>
|
||||||
|
<int>90199702</int>
|
||||||
|
<int>90212090</int>
|
||||||
|
<int>96911147</int>
|
||||||
|
<int>97110308</int>
|
||||||
|
<int>98528428</int>
|
||||||
|
<int>98665206</int>
|
||||||
|
<int>98837995</int>
|
||||||
|
<int>98842922</int>
|
||||||
|
<int>98842977</int>
|
||||||
|
<int>98846632</int>
|
||||||
|
<int>98866485</int>
|
||||||
|
<int>98874250</int>
|
||||||
|
<int>98879075</int>
|
||||||
|
<int>98904649</int>
|
||||||
|
<int>98918872</int>
|
||||||
|
<int>98945691</int>
|
||||||
|
<int>98959458</int>
|
||||||
|
<int>98984707</int>
|
||||||
|
<int>100220125</int>
|
||||||
|
<int>100238731</int>
|
||||||
|
<int>100662329</int>
|
||||||
|
<int>100795834</int>
|
||||||
|
<int>100862457</int>
|
||||||
|
<int>103124811</int>
|
||||||
|
<int>103348671</int>
|
||||||
|
<int>104369981</int>
|
||||||
|
<int>104372472</int>
|
||||||
|
<int>104385324</int>
|
||||||
|
<int>104465831</int>
|
||||||
|
<int>104465834</int>
|
||||||
|
<int>104467697</int>
|
||||||
|
<int>104473368</int>
|
||||||
|
<int>104482267</int>
|
||||||
|
<int>104505005</int>
|
||||||
|
<int>104523840</int>
|
||||||
|
<int>104550085</int>
|
||||||
|
<int>104558084</int>
|
||||||
|
<int>104659441</int>
|
||||||
|
<int>104659675</int>
|
||||||
|
<int>104664678</int>
|
||||||
|
<int>104668274</int>
|
||||||
|
<int>104671092</int>
|
||||||
|
<int>104673242</int>
|
||||||
|
<int>104674239</int>
|
||||||
|
<int>104679268</int>
|
||||||
|
<int>104686047</int>
|
||||||
|
<int>104698649</int>
|
||||||
|
<int>104751469</int>
|
||||||
|
<int>104752478</int>
|
||||||
|
<int>104755145</int>
|
||||||
|
<int>104761158</int>
|
||||||
|
<int>104762266</int>
|
||||||
|
<int>104786484</int>
|
||||||
|
<int>104853747</int>
|
||||||
|
<int>104873258</int>
|
||||||
|
<int>104983051</int>
|
||||||
|
<int>105063056</int>
|
||||||
|
<int>105116588</int>
|
||||||
|
<int>105178523</int>
|
||||||
|
<int>105318602</int>
|
||||||
|
<int>105362613</int>
|
||||||
|
<int>105364552</int>
|
||||||
|
<int>105368563</int>
|
||||||
|
<int>105369591</int>
|
||||||
|
<int>105370746</int>
|
||||||
|
<int>105373503</int>
|
||||||
|
<int>105373615</int>
|
||||||
|
<int>105376634</int>
|
||||||
|
<int>105377546</int>
|
||||||
|
<int>105378752</int>
|
||||||
|
<int>105379574</int>
|
||||||
|
<int>105381626</int>
|
||||||
|
<int>105382587</int>
|
||||||
|
<int>105425313</int>
|
||||||
|
<int>105495146</int>
|
||||||
|
<int>105862607</int>
|
||||||
|
<int>105939029</int>
|
||||||
|
<int>105995585</int>
|
||||||
|
<int>106017178</int>
|
||||||
|
<int>106129726</int>
|
||||||
|
<int>106768485</int>
|
||||||
|
<int>107825194</int>
|
||||||
|
<int>111906429</int>
|
||||||
|
<int>115121473</int>
|
||||||
|
<int>115578654</int>
|
||||||
|
<int>116630363</int>
|
||||||
|
<int>117835105</int>
|
||||||
|
<int>117850671</int>
|
||||||
|
<int>118638500</int>
|
||||||
|
<int>118662027</int>
|
||||||
|
<int>118872681</int>
|
||||||
|
<int>118873829</int>
|
||||||
|
<int>118879289</int>
|
||||||
|
<int>118889092</int>
|
||||||
|
<int>119501720</int>
|
||||||
|
<int>119551648</int>
|
||||||
|
<int>119569538</int>
|
||||||
|
<int>119640702</int>
|
||||||
|
<int>119667998</int>
|
||||||
|
<int>119674103</int>
|
||||||
|
<int>119697201</int>
|
||||||
|
<int>119706266</int>
|
||||||
|
<int>119744627</int>
|
||||||
|
<int>119773746</int>
|
||||||
|
<int>120072697</int>
|
||||||
|
<int>120144309</int>
|
||||||
|
<int>120214154</int>
|
||||||
|
<int>120357027</int>
|
||||||
|
<int>120392612</int>
|
||||||
|
<int>120399120</int>
|
||||||
|
<int>120553945</int>
|
||||||
|
<int>120783545</int>
|
||||||
|
<int>120797092</int>
|
||||||
|
<int>120881676</int>
|
||||||
|
<int>120889689</int>
|
||||||
|
<int>120999554</int>
|
||||||
|
<int>121168608</int>
|
||||||
|
<int>121268830</int>
|
||||||
|
<int>121341838</int>
|
||||||
|
<int>121729951</int>
|
||||||
|
<int>121803677</int>
|
||||||
|
<int>122165810</int>
|
||||||
|
<int>125408034</int>
|
||||||
|
<int>127293130</int>
|
||||||
|
<int>127566683</int>
|
||||||
|
<int>127762067</int>
|
||||||
|
<int>127861893</int>
|
||||||
|
<int>128571722</int>
|
||||||
|
<int>128647535</int>
|
||||||
|
<int>128698922</int>
|
||||||
|
<int>128701748</int>
|
||||||
|
<int>128771507</int>
|
||||||
|
<int>129037212</int>
|
||||||
|
<int>129079800</int>
|
||||||
|
<int>129175415</int>
|
||||||
|
<int>129317272</int>
|
||||||
|
<int>129319665</int>
|
||||||
|
<int>129365668</int>
|
||||||
|
<int>129378095</int>
|
||||||
|
<int>129424803</int>
|
||||||
|
<int>129590730</int>
|
||||||
|
<int>129603714</int>
|
||||||
|
<int>129625954</int>
|
||||||
|
<int>129692391</int>
|
||||||
|
<int>129714980</int>
|
||||||
|
<int>129721097</int>
|
||||||
|
<int>129886397</int>
|
||||||
|
<int>129968371</int>
|
||||||
|
<int>129972243</int>
|
||||||
|
<int>130009862</int>
|
||||||
|
<int>130033651</int>
|
||||||
|
<int>130040030</int>
|
||||||
|
<int>130040032</int>
|
||||||
|
<int>130040033</int>
|
||||||
|
<int>130091954</int>
|
||||||
|
<int>130100640</int>
|
||||||
|
<int>130131267</int>
|
||||||
|
<int>130131921</int>
|
||||||
|
<int>130144837</int>
|
||||||
|
<int>130171030</int>
|
||||||
|
<int>130172071</int>
|
||||||
|
<int>130197218</int>
|
||||||
|
<int>130212435</int>
|
||||||
|
<int>130291076</int>
|
||||||
|
<int>130402427</int>
|
||||||
|
<int>130405166</int>
|
||||||
|
<int>130676169</int>
|
||||||
|
<int>130698471</int>
|
||||||
|
<int>130713390</int>
|
||||||
|
<int>130785217</int>
|
||||||
|
<int>131396908</int>
|
||||||
|
<int>131455115</int>
|
||||||
|
<int>131682095</int>
|
||||||
|
<int>131689473</int>
|
||||||
|
<int>131701956</int>
|
||||||
|
<int>132142800</int>
|
||||||
|
<int>132525441</int>
|
||||||
|
<int>132765492</int>
|
||||||
|
<int>132801275</int>
|
||||||
|
<int>133399034</int>
|
||||||
|
<int>134522926</int>
|
||||||
|
<int>134524022</int>
|
||||||
|
<int>134528994</int>
|
||||||
|
<int>134532942</int>
|
||||||
|
<int>134536993</int>
|
||||||
|
<int>134538001</int>
|
||||||
|
<int>134547533</int>
|
||||||
|
<int>134549216</int>
|
||||||
|
<int>134549317</int>
|
||||||
|
<int>134550159</int>
|
||||||
|
<int>134550214</int>
|
||||||
|
<int>134550232</int>
|
||||||
|
<int>134551154</int>
|
||||||
|
<int>134551207</int>
|
||||||
|
<int>134551390</int>
|
||||||
|
<int>134553171</int>
|
||||||
|
<int>134553237</int>
|
||||||
|
<int>134554199</int>
|
||||||
|
<int>134554227</int>
|
||||||
|
<int>134555229</int>
|
||||||
|
<int>134555240</int>
|
||||||
|
<int>134556118</int>
|
||||||
|
<int>134557078</int>
|
||||||
|
<int>134560099</int>
|
||||||
|
<int>134560287</int>
|
||||||
|
<int>134562084</int>
|
||||||
|
<int>134562180</int>
|
||||||
|
<int>134563287</int>
|
||||||
|
<int>134565083</int>
|
||||||
|
<int>134566130</int>
|
||||||
|
<int>134568111</int>
|
||||||
|
<int>134624737</int>
|
||||||
|
<int>134666461</int>
|
||||||
|
<int>134672998</int>
|
||||||
|
<int>134684008</int>
|
||||||
|
<int>134916523</int>
|
||||||
|
<int>135100527</int>
|
||||||
|
<int>135219410</int>
|
||||||
|
<int>135222083</int>
|
||||||
|
<int>135306997</int>
|
||||||
|
<int>135463054</int>
|
||||||
|
<int>135779456</int>
|
||||||
|
<int>135812968</int>
|
||||||
|
<int>136097030</int>
|
||||||
|
<int>136131333</int>
|
||||||
|
<int>136146907</int>
|
||||||
|
<int>136157556</int>
|
||||||
|
<int>136320962</int>
|
||||||
|
<int>136450641</int>
|
||||||
|
<int>136466000</int>
|
||||||
|
<int>136745792</int>
|
||||||
|
<int>136761546</int>
|
||||||
|
<int>136840245</int>
|
||||||
|
<int>138160034</int>
|
||||||
|
<int>138181244</int>
|
||||||
|
<int>138210071</int>
|
||||||
|
<int>138210107</int>
|
||||||
|
<int>138232200</int>
|
||||||
|
<int>138237088</int>
|
||||||
|
<int>138277547</int>
|
||||||
|
<int>138287133</int>
|
||||||
|
<int>138306991</int>
|
||||||
|
<int>138324625</int>
|
||||||
|
<int>138341916</int>
|
||||||
|
<int>138372035</int>
|
||||||
|
<int>138372036</int>
|
||||||
|
<int>138375118</int>
|
||||||
|
<int>138378071</int>
|
||||||
|
<int>138380128</int>
|
||||||
|
<int>138380194</int>
|
||||||
|
<int>138534411</int>
|
||||||
|
<int>138618294</int>
|
||||||
|
<int>138931764</int>
|
||||||
|
<int>139536037</int>
|
||||||
|
<int>139536038</int>
|
||||||
|
<int>139536039</int>
|
||||||
|
<int>139536040</int>
|
||||||
|
<int>140367832</int>
|
||||||
|
<int>140406050</int>
|
||||||
|
<int>140421668</int>
|
||||||
|
<int>140422973</int>
|
||||||
|
<int>140423713</int>
|
||||||
|
<int>140436348</int>
|
||||||
|
<int>140483470</int>
|
||||||
|
<int>140615715</int>
|
||||||
|
<int>140802803</int>
|
||||||
|
<int>140896470</int>
|
||||||
|
<int>141189437</int>
|
||||||
|
<int>141192744</int>
|
||||||
|
<int>141382548</int>
|
||||||
|
<int>141461680</int>
|
||||||
|
<int>141624996</int>
|
||||||
|
<int>141627135</int>
|
||||||
|
<int>141659139</int>
|
||||||
|
<int>141872038</int>
|
||||||
|
<int>141993721</int>
|
||||||
|
<int>142006413</int>
|
||||||
|
<int>142045136</int>
|
||||||
|
<int>142095667</int>
|
||||||
|
<int>142227273</int>
|
||||||
|
<int>142250480</int>
|
||||||
|
<int>142518788</int>
|
||||||
|
<int>142544931</int>
|
||||||
|
<int>142546314</int>
|
||||||
|
<int>142555433</int>
|
||||||
|
<int>142653044</int>
|
||||||
|
<int>143191852</int>
|
||||||
|
<int>143258496</int>
|
||||||
|
<int>143299722</int>
|
||||||
|
<int>143331253</int>
|
||||||
|
<int>143432462</int>
|
||||||
|
<int>143632431</int>
|
||||||
|
<int>143695326</int>
|
||||||
|
<int>144219522</int>
|
||||||
|
<int>144590916</int>
|
||||||
|
<int>145410436</int>
|
||||||
|
<int>146720405</int>
|
||||||
|
<int>150810438</int>
|
||||||
|
<int>151258773</int>
|
||||||
|
<int>151315554</int>
|
||||||
|
<int>151400090</int>
|
||||||
|
<int>151429441</int>
|
||||||
|
<int>151439617</int>
|
||||||
|
<int>151453617</int>
|
||||||
|
<int>151466296</int>
|
||||||
|
<int>151511132</int>
|
||||||
|
<int>151636561</int>
|
||||||
|
<int>151823192</int>
|
||||||
|
<int>151827116</int>
|
||||||
|
<int>151850642</int>
|
||||||
|
<int>152016572</int>
|
||||||
|
<int>153111675</int>
|
||||||
|
<int>153114652</int>
|
||||||
|
<int>153123147</int>
|
||||||
|
<int>153267108</int>
|
||||||
|
<int>153389799</int>
|
||||||
|
<int>153395366</int>
|
||||||
|
<int>153718608</int>
|
||||||
|
<int>154171028</int>
|
||||||
|
<int>154315227</int>
|
||||||
|
<int>154559688</int>
|
||||||
|
<int>154978771</int>
|
||||||
|
<int>154979742</int>
|
||||||
|
<int>154985773</int>
|
||||||
|
<int>154989370</int>
|
||||||
|
<int>155044852</int>
|
||||||
|
<int>155065458</int>
|
||||||
|
<int>155578573</int>
|
||||||
|
<int>156403304</int>
|
||||||
|
<int>159085959</int>
|
||||||
|
<int>159776047</int>
|
||||||
|
<int>159816630</int>
|
||||||
|
<int>160733048</int>
|
||||||
|
<int>160733049</int>
|
||||||
|
<int>160733050</int>
|
||||||
|
<int>160733051</int>
|
||||||
|
<int>160733056</int>
|
||||||
|
<int>164824922</int>
|
||||||
|
<int>164824924</int>
|
||||||
|
<int>164824926</int>
|
||||||
|
<int>164824930</int>
|
||||||
|
<int>164831646</int>
|
||||||
|
<int>164831647</int>
|
||||||
|
<int>164831648</int>
|
||||||
|
<int>164831650</int>
|
||||||
|
<int>164835050</int>
|
||||||
|
<int>164835051</int>
|
||||||
|
<int>164835052</int>
|
||||||
|
<int>164835056</int>
|
||||||
|
<int>164835057</int>
|
||||||
|
<int>164835059</int>
|
||||||
|
<int>164836898</int>
|
||||||
|
<int>164836899</int>
|
||||||
|
<int>164836900</int>
|
||||||
|
<int>164845333</int>
|
||||||
|
<int>164845334</int>
|
||||||
|
<int>164845336</int>
|
||||||
|
<int>164845337</int>
|
||||||
|
<int>164845341</int>
|
||||||
|
<int>164845342</int>
|
||||||
|
<int>164845345</int>
|
||||||
|
<int>164845346</int>
|
||||||
|
<int>164845349</int>
|
||||||
|
<int>164845350</int>
|
||||||
|
<int>164845353</int>
|
||||||
|
<int>164845355</int>
|
||||||
|
<int>164845358</int>
|
||||||
|
<int>164845361</int>
|
||||||
|
<int>164845364</int>
|
||||||
|
<int>164847387</int>
|
||||||
|
<int>164847388</int>
|
||||||
|
<int>164847389</int>
|
||||||
|
<int>164847390</int>
|
||||||
|
<int>164848328</int>
|
||||||
|
<int>164848329</int>
|
||||||
|
<int>164848330</int>
|
||||||
|
<int>164849448</int>
|
||||||
|
<int>164849449</int>
|
||||||
|
<int>164849451</int>
|
||||||
|
<int>164849452</int>
|
||||||
|
<int>164849454</int>
|
||||||
|
<int>164849455</int>
|
||||||
|
<int>164849457</int>
|
||||||
|
<int>164849461</int>
|
||||||
|
<int>164850219</int>
|
||||||
|
<int>164850220</int>
|
||||||
|
<int>164850222</int>
|
||||||
|
<int>164850223</int>
|
||||||
|
<int>164850224</int>
|
||||||
|
<int>164850226</int>
|
||||||
|
<int>164850227</int>
|
||||||
|
<int>164850228</int>
|
||||||
|
<int>164850229</int>
|
||||||
|
<int>164850231</int>
|
||||||
|
<int>164850236</int>
|
||||||
|
<int>164850237</int>
|
||||||
|
<int>164850240</int>
|
||||||
|
<int>164850242</int>
|
||||||
|
<int>164850243</int>
|
||||||
|
<int>164852242</int>
|
||||||
|
<int>164852243</int>
|
||||||
|
<int>164852244</int>
|
||||||
|
<int>164852247</int>
|
||||||
|
<int>164852248</int>
|
||||||
|
<int>164852249</int>
|
||||||
|
<int>164852250</int>
|
||||||
|
<int>164852251</int>
|
||||||
|
<int>164852254</int>
|
||||||
|
<int>164852256</int>
|
||||||
|
<int>164852257</int>
|
||||||
|
<int>164852258</int>
|
||||||
|
<int>164852259</int>
|
||||||
|
<int>164852260</int>
|
||||||
|
<int>164852261</int>
|
||||||
|
<int>164852262</int>
|
||||||
|
<int>164853061</int>
|
||||||
|
<int>164853063</int>
|
||||||
|
<int>164853071</int>
|
||||||
|
<int>164853072</int>
|
||||||
|
<int>164853075</int>
|
||||||
|
<int>168118980</int>
|
||||||
|
<int>168118981</int>
|
||||||
|
<int>168118983</int>
|
||||||
|
<int>168118984</int>
|
||||||
|
<int>168180375</int>
|
||||||
|
<int>168180376</int>
|
||||||
|
<int>168180378</int>
|
||||||
|
<int>168180379</int>
|
||||||
|
<int>168270830</int>
|
||||||
|
<int>168270831</int>
|
||||||
|
<int>168270833</int>
|
||||||
|
<int>168270834</int>
|
||||||
|
<int>168270835</int>
|
||||||
|
</OtherCachedUpdateIDs>
|
||||||
|
<SkipSoftwareSync>false</SkipSoftwareSync>
|
||||||
|
<NeedTwoGroupOutOfScopeUpdates>true</NeedTwoGroupOutOfScopeUpdates>
|
||||||
|
<FilterAppCategoryIds>
|
||||||
|
<CategoryIdentifier>
|
||||||
|
<Id>{}</Id>
|
||||||
|
</CategoryIdentifier>
|
||||||
|
</FilterAppCategoryIds>
|
||||||
|
<TreatAppCategoryIdsAsInstalled>true</TreatAppCategoryIdsAsInstalled>
|
||||||
|
<AlsoPerformRegularSync>false</AlsoPerformRegularSync>
|
||||||
|
<ComputerSpec/>
|
||||||
|
<ExtendedUpdateInfoParameters>
|
||||||
|
<XmlUpdateFragmentTypes>
|
||||||
|
<XmlUpdateFragmentType>Extended</XmlUpdateFragmentType>
|
||||||
|
</XmlUpdateFragmentTypes>
|
||||||
|
<Locales>
|
||||||
|
<string>en-US</string>
|
||||||
|
<string>en</string>
|
||||||
|
</Locales>
|
||||||
|
</ExtendedUpdateInfoParameters>
|
||||||
|
<ClientPreferredLanguages>
|
||||||
|
<string>en-US</string>
|
||||||
|
</ClientPreferredLanguages>
|
||||||
|
<ProductsParameters>
|
||||||
|
<SyncCurrentVersionOnly>false</SyncCurrentVersionOnly>
|
||||||
|
<DeviceAttributes>BranchReadinessLevel=CB;CurrentBranch=rs_prerelease;OEMModel=Virtual Machine;FlightRing={};AttrDataVer=21;SystemManufacturer=Microsoft Corporation;InstallLanguage=en-US;OSUILocale=en-US;InstallationType=Client;FlightingBranchName=external;FirmwareVersion=Hyper-V UEFI Release v2.5;SystemProductName=Virtual Machine;OSSkuId=48;FlightContent=Branch;App=WU;OEMName_Uncleaned=Microsoft Corporation;AppVer=10.0.22621.900;OSArchitecture=AMD64;SystemSKU=None;UpdateManagementGroup=2;IsFlightingEnabled=1;IsDeviceRetailDemo=0;TelemetryLevel=3;OSVersion=10.0.22621.900;DeviceFamily=Windows.Desktop;</DeviceAttributes>
|
||||||
|
<CallerAttributes>Interactive=1;IsSeeker=0;</CallerAttributes>
|
||||||
|
<Products/>
|
||||||
|
</ProductsParameters>
|
||||||
|
</parameters>
|
||||||
|
</SyncUpdates>
|
||||||
|
</s:Body>
|
||||||
|
</s:Envelope>
|
||||||
29
MagiskOnWSA/DLL/xml/priconfig.xml
Normal file
29
MagiskOnWSA/DLL/xml/priconfig.xml
Normal file
@ -0,0 +1,29 @@
|
|||||||
|
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
|
||||||
|
<!-- This file is part of MagiskOnWSALocal.
|
||||||
|
|
||||||
|
MagiskOnWSALocal is free software: you can redistribute it and/or modify
|
||||||
|
it under the terms of the GNU Affero General Public License as
|
||||||
|
published by the Free Software Foundation, either version 3 of the
|
||||||
|
License, or (at your option) any later version.
|
||||||
|
|
||||||
|
MagiskOnWSALocal is distributed in the hope that it will be useful,
|
||||||
|
but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||||
|
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||||
|
GNU Affero General Public License for more details.
|
||||||
|
|
||||||
|
You should have received a copy of the GNU Affero General Public License
|
||||||
|
along with MagiskOnWSALocal. If not, see <https://www.gnu.org/licenses/>.
|
||||||
|
|
||||||
|
Copyright (C) 2023 LSPosed Contributors
|
||||||
|
-->
|
||||||
|
<resources targetOsVersion="10.0.0" majorVersion="1">
|
||||||
|
<index root="\" startIndexAt="\">
|
||||||
|
<default>
|
||||||
|
<qualifier name="Language" value="en-US" />
|
||||||
|
</default>
|
||||||
|
<indexer-config type="folder" foldernameAsQualifier="true" filenameAsQualifier="true"
|
||||||
|
qualifierDelimiter="." />
|
||||||
|
<indexer-config type="PRI" />
|
||||||
|
<indexer-config type="priinfo" />
|
||||||
|
</index>
|
||||||
|
</resources>
|
||||||
81
MagiskOnWSA/cacerts/01ee3bf3.0
Normal file
81
MagiskOnWSA/cacerts/01ee3bf3.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIDzzCCAregAwIBAgIJAPJgZpghday9MA0GCSqGSIb3DQEBCwUAMH4xCzAJBgNV
|
||||||
|
BAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcMCUplcnVzYWxlbTEQMA4G
|
||||||
|
A1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0ZnJlZS5saW5rMSEwHwYDVQQDDBhO
|
||||||
|
ZXRGcmVlIFNpZ24gLCBIYWRyYW5WcG4wHhcNMTcwMzMwMDEwNDAwWhcNMjcwMjA2
|
||||||
|
MDEwNDAwWjB+MQswCQYDVQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIwEAYDVQQH
|
||||||
|
DAlKZXJ1c2FsZW0xEDAOBgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5ldGZyZWUu
|
||||||
|
bGluazEhMB8GA1UEAwwYTmV0RnJlZSBTaWduICwgSGFkcmFuVnBuMIIBIjANBgkq
|
||||||
|
hkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEApRXoigVenMeP9PGM9zt/TDo60AwOrjAS
|
||||||
|
a2zSgR21Hy9IoJGdR57eZKMKvGirzsgTrzjZl/G92FPppx1hKyZjP1IHES0kzG74
|
||||||
|
yK4JtRGC1T4GYutAHM1ZDv7ZoUnGxsEo5or6CFhR+D/zJ5fiiACFypIICb6qUynk
|
||||||
|
aaSamw1JTKLNUCrs6eArJnThBJP+Czi45uM/mdrB5jnajLvRnFgeqcPp6913zKUy
|
||||||
|
4FsHPm5U26kincnRV/04UB4Xx/f3LHv9L9Ao1aViDbZlHverU0ETCEALHWqnfjX/
|
||||||
|
uSk/zRXZRzDRPCGIdVXuxiYINjCzA4+ZRrdc+qhlpuzn9ct7phi3ewIDAQABo1Aw
|
||||||
|
TjAdBgNVHQ4EFgQU3C1v4yi0aNBn4CzFWEnQl2Lcl94wHwYDVR0jBBgwFoAU3C1v
|
||||||
|
4yi0aNBn4CzFWEnQl2Lcl94wDAYDVR0TBAUwAwEB/zANBgkqhkiG9w0BAQsFAAOC
|
||||||
|
AQEAeHISptZ4rtfTGej48OV5o5q/Z5XmU8G4qnkWX4AfqIl3SOfPc6UzHBE+gYyw
|
||||||
|
zhBfvhW+MMHJaBh0LfswRfbuP3nkOQNvzVSIRyvmYqklZTTSQ1J5AsgB39C1LYWB
|
||||||
|
c79cyYZH3EUU+bdXgBlIxTixpOm+eqoxQlIoAMjmOjQMvOKFsZJcj0XUdULfxC2C
|
||||||
|
PbMkCJ6JB5Dr19NZxsQyEE+GhLiPJDtGcjzfHMZwUDMe1qWKAnPR5P9xZegm50HI
|
||||||
|
ogmnZGL6nfpts5yqeHaQunCKQarUbvY7Sp89wI1J+ntVHVnO9VxubHqWj+1nwlna
|
||||||
|
SBAWwK8ruKyu6mDloyilV6c4+g==
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
f2:60:66:98:21:75:ac:bd
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , HadranVpn"
|
||||||
|
Validity
|
||||||
|
Not Before: Mar 30 01:04:00 2017 GMT
|
||||||
|
Not After : Feb 6 01:04:00 2027 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , HadranVpn"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:a5:15:e8:8a:05:5e:9c:c7:8f:f4:f1:8c:f7:3b:
|
||||||
|
7f:4c:3a:3a:d0:0c:0e:ae:30:12:6b:6c:d2:81:1d:
|
||||||
|
b5:1f:2f:48:a0:91:9d:47:9e:de:64:a3:0a:bc:68:
|
||||||
|
ab:ce:c8:13:af:38:d9:97:f1:bd:d8:53:e9:a7:1d:
|
||||||
|
61:2b:26:63:3f:52:07:11:2d:24:cc:6e:f8:c8:ae:
|
||||||
|
09:b5:11:82:d5:3e:06:62:eb:40:1c:cd:59:0e:fe:
|
||||||
|
d9:a1:49:c6:c6:c1:28:e6:8a:fa:08:58:51:f8:3f:
|
||||||
|
f3:27:97:e2:88:00:85:ca:92:08:09:be:aa:53:29:
|
||||||
|
e4:69:a4:9a:9b:0d:49:4c:a2:cd:50:2a:ec:e9:e0:
|
||||||
|
2b:26:74:e1:04:93:fe:0b:38:b8:e6:e3:3f:99:da:
|
||||||
|
c1:e6:39:da:8c:bb:d1:9c:58:1e:a9:c3:e9:eb:dd:
|
||||||
|
77:cc:a5:32:e0:5b:07:3e:6e:54:db:a9:22:9d:c9:
|
||||||
|
d1:57:fd:38:50:1e:17:c7:f7:f7:2c:7b:fd:2f:d0:
|
||||||
|
28:d5:a5:62:0d:b6:65:1e:f7:ab:53:41:13:08:40:
|
||||||
|
0b:1d:6a:a7:7e:35:ff:b9:29:3f:cd:15:d9:47:30:
|
||||||
|
d1:3c:21:88:75:55:ee:c6:26:08:36:30:b3:03:8f:
|
||||||
|
99:46:b7:5c:fa:a8:65:a6:ec:e7:f5:cb:7b:a6:18:
|
||||||
|
b7:7b
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
DC:2D:6F:E3:28:B4:68:D0:67:E0:2C:C5:58:49:D0:97:62:DC:97:DE
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:DC:2D:6F:E3:28:B4:68:D0:67:E0:2C:C5:58:49:D0:97:62:DC:97:DE
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
78:72:12:a6:d6:78:ae:d7:d3:19:e8:f8:f0:e5:79:a3:9a:bf:
|
||||||
|
67:95:e6:53:c1:b8:aa:79:16:5f:80:1f:a8:89:77:48:e7:cf:
|
||||||
|
73:a5:33:1c:11:3e:81:8c:b0:ce:10:5f:be:15:be:30:c1:c9:
|
||||||
|
68:18:74:2d:fb:30:45:f6:ee:3f:79:e4:39:03:6f:cd:54:88:
|
||||||
|
47:2b:e6:62:a9:25:65:34:d2:43:52:79:02:c8:01:df:d0:b5:
|
||||||
|
2d:85:81:73:bf:5c:c9:86:47:dc:45:14:f9:b7:57:80:19:48:
|
||||||
|
c5:38:b1:a4:e9:be:7a:aa:31:42:52:28:00:c8:e6:3a:34:0c:
|
||||||
|
bc:e2:85:b1:92:5c:8f:45:d4:75:42:df:c4:2d:82:3d:b3:24:
|
||||||
|
08:9e:89:07:90:eb:d7:d3:59:c6:c4:32:10:4f:86:84:b8:8f:
|
||||||
|
24:3b:46:72:3c:df:1c:c6:70:50:33:1e:d6:a5:8a:02:73:d1:
|
||||||
|
e4:ff:71:65:e8:26:e7:41:c8:a2:09:a7:64:62:fa:9d:fa:6d:
|
||||||
|
b3:9c:aa:78:76:90:ba:70:8a:41:aa:d4:6e:f6:3b:4a:9f:3d:
|
||||||
|
c0:8d:49:fa:7b:55:1d:59:ce:f5:5c:6e:6c:7a:96:8f:ed:67:
|
||||||
|
c2:59:da:48:10:16:c0:af:2b:b8:ac:ae:ea:60:e5:a3:28:a5:
|
||||||
|
57:a7:38:fa
|
||||||
81
MagiskOnWSA/cacerts/024c10e0.0
Normal file
81
MagiskOnWSA/cacerts/024c10e0.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIID1zCCAr+gAwIBAgIJAIdzf+9gLmi5MA0GCSqGSIb3DQEBCwUAMIGBMQswCQYD
|
||||||
|
VQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIwEAYDVQQHDAlKZXJ1c2FsZW0xEDAO
|
||||||
|
BgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5ldGZyZWUubGluazEkMCIGA1UEAwwb
|
||||||
|
TmV0RnJlZSBTaWduLCBLb3NoZXJTSU0gSVRDMB4XDTE4MDQyMjE2MzMxMloXDTI4
|
||||||
|
MDIyOTE2MzMxMlowgYExCzAJBgNVBAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQ
|
||||||
|
BgNVBAcMCUplcnVzYWxlbTEQMA4GA1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0
|
||||||
|
ZnJlZS5saW5rMSQwIgYDVQQDDBtOZXRGcmVlIFNpZ24sIEtvc2hlclNJTSBJVEMw
|
||||||
|
ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDP4S4XapIOvQv5wWbfBzg2
|
||||||
|
2fY1pWs030zMEOCVvnxMr9Fp1tgs/AVMY+UzkmawwbVDxZQL3goR7RqHPKkvsWXo
|
||||||
|
TEM1DOBajU9l3JRd8djnIMMG0u8wDXzFcVmno/Mh5fCXvhAr9Dd11KokYQKcn5wT
|
||||||
|
uDhJEhyEqB8Ho8BNvTyRts/HrkdJiSFEaSpr2J9BM/v9dIzINfBg/hxy7Em9B0pd
|
||||||
|
wgnKr6Bz0esC10hCYphjzaKpd/23jvfZHZKq4oFSaFzhzC5pbg4cSPCxRUN7kzxs
|
||||||
|
ezRhSoHhzMBXn4ay+VKhBKlKUOxT3STyxPFMYx6s40qlhlmaZ1tN4hLQrwD1jLw7
|
||||||
|
AgMBAAGjUDBOMB0GA1UdDgQWBBSPs38ZeH74K6wWVOIaW6P5ePY71zAfBgNVHSME
|
||||||
|
GDAWgBSPs38ZeH74K6wWVOIaW6P5ePY71zAMBgNVHRMEBTADAQH/MA0GCSqGSIb3
|
||||||
|
DQEBCwUAA4IBAQAcreRYyYYW+7gfAyxfv+AXV2NDlHMuQ6/gS13JgsObnoDcxhT1
|
||||||
|
cSbnAwbhvWXq7uAlD8Kbxp5uNZIt8N5ykqi4qjUXXuBMAZS75Rc9XDmmryBTfC+i
|
||||||
|
fql/2G6Itcj0VaoQK9gbnMumHqdK4wiIJHy4Wx2+b+3CeznwwWz5TWxBJmAqVPCN
|
||||||
|
hiu72Bh+W9wA2xuP65/FcKLpOpROQqUUT0vJd8UT46HMy7X2CXjB/ZWskGYn1V8Z
|
||||||
|
0aEvSW9FQDJllAXnTOLbXqHmY8/bdLraAL7Z7bJYLUxBcVOUe8+B+QN919kJOfk+
|
||||||
|
AYoB1o77qk3kH7jKxxPAH5G7SP2aYtylqb45
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
87:73:7f:ef:60:2e:68:b9
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, KosherSIM ITC"
|
||||||
|
Validity
|
||||||
|
Not Before: Apr 22 16:33:12 2018 GMT
|
||||||
|
Not After : Feb 29 16:33:12 2028 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, KosherSIM ITC"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:cf:e1:2e:17:6a:92:0e:bd:0b:f9:c1:66:df:07:
|
||||||
|
38:36:d9:f6:35:a5:6b:34:df:4c:cc:10:e0:95:be:
|
||||||
|
7c:4c:af:d1:69:d6:d8:2c:fc:05:4c:63:e5:33:92:
|
||||||
|
66:b0:c1:b5:43:c5:94:0b:de:0a:11:ed:1a:87:3c:
|
||||||
|
a9:2f:b1:65:e8:4c:43:35:0c:e0:5a:8d:4f:65:dc:
|
||||||
|
94:5d:f1:d8:e7:20:c3:06:d2:ef:30:0d:7c:c5:71:
|
||||||
|
59:a7:a3:f3:21:e5:f0:97:be:10:2b:f4:37:75:d4:
|
||||||
|
aa:24:61:02:9c:9f:9c:13:b8:38:49:12:1c:84:a8:
|
||||||
|
1f:07:a3:c0:4d:bd:3c:91:b6:cf:c7:ae:47:49:89:
|
||||||
|
21:44:69:2a:6b:d8:9f:41:33:fb:fd:74:8c:c8:35:
|
||||||
|
f0:60:fe:1c:72:ec:49:bd:07:4a:5d:c2:09:ca:af:
|
||||||
|
a0:73:d1:eb:02:d7:48:42:62:98:63:cd:a2:a9:77:
|
||||||
|
fd:b7:8e:f7:d9:1d:92:aa:e2:81:52:68:5c:e1:cc:
|
||||||
|
2e:69:6e:0e:1c:48:f0:b1:45:43:7b:93:3c:6c:7b:
|
||||||
|
34:61:4a:81:e1:cc:c0:57:9f:86:b2:f9:52:a1:04:
|
||||||
|
a9:4a:50:ec:53:dd:24:f2:c4:f1:4c:63:1e:ac:e3:
|
||||||
|
4a:a5:86:59:9a:67:5b:4d:e2:12:d0:af:00:f5:8c:
|
||||||
|
bc:3b
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
8F:B3:7F:19:78:7E:F8:2B:AC:16:54:E2:1A:5B:A3:F9:78:F6:3B:D7
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:8F:B3:7F:19:78:7E:F8:2B:AC:16:54:E2:1A:5B:A3:F9:78:F6:3B:D7
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
1c:ad:e4:58:c9:86:16:fb:b8:1f:03:2c:5f:bf:e0:17:57:63:
|
||||||
|
43:94:73:2e:43:af:e0:4b:5d:c9:82:c3:9b:9e:80:dc:c6:14:
|
||||||
|
f5:71:26:e7:03:06:e1:bd:65:ea:ee:e0:25:0f:c2:9b:c6:9e:
|
||||||
|
6e:35:92:2d:f0:de:72:92:a8:b8:aa:35:17:5e:e0:4c:01:94:
|
||||||
|
bb:e5:17:3d:5c:39:a6:af:20:53:7c:2f:a2:7e:a9:7f:d8:6e:
|
||||||
|
88:b5:c8:f4:55:aa:10:2b:d8:1b:9c:cb:a6:1e:a7:4a:e3:08:
|
||||||
|
88:24:7c:b8:5b:1d:be:6f:ed:c2:7b:39:f0:c1:6c:f9:4d:6c:
|
||||||
|
41:26:60:2a:54:f0:8d:86:2b:bb:d8:18:7e:5b:dc:00:db:1b:
|
||||||
|
8f:eb:9f:c5:70:a2:e9:3a:94:4e:42:a5:14:4f:4b:c9:77:c5:
|
||||||
|
13:e3:a1:cc:cb:b5:f6:09:78:c1:fd:95:ac:90:66:27:d5:5f:
|
||||||
|
19:d1:a1:2f:49:6f:45:40:32:65:94:05:e7:4c:e2:db:5e:a1:
|
||||||
|
e6:63:cf:db:74:ba:da:00:be:d9:ed:b2:58:2d:4c:41:71:53:
|
||||||
|
94:7b:cf:81:f9:03:7d:d7:d9:09:39:f9:3e:01:8a:01:d6:8e:
|
||||||
|
fb:aa:4d:e4:1f:b8:ca:c7:13:c0:1f:91:bb:48:fd:9a:62:dc:
|
||||||
|
a5:a9:be:39
|
||||||
123
MagiskOnWSA/cacerts/0888e817.0
Normal file
123
MagiskOnWSA/cacerts/0888e817.0
Normal file
@ -0,0 +1,123 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIF0zCCA7ugAwIBAgIUC+b3kBsjJ33F8+V3PFpQU+h6H0EwDQYJKoZIhvcNAQEL
|
||||||
|
BQAweTELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAGA1UEBwwJSmVy
|
||||||
|
dXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRmcmVlLmxpbmsx
|
||||||
|
HDAaBgNVBAMME05ldEZyZWUgU2lnbiAsWW9zc2kwHhcNMTkwODEyMTkwNDE5WhcN
|
||||||
|
MjkwNjIwMTkwNDE5WjB5MQswCQYDVQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIw
|
||||||
|
EAYDVQQHDAlKZXJ1c2FsZW0xEDAOBgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5l
|
||||||
|
dGZyZWUubGluazEcMBoGA1UEAwwTTmV0RnJlZSBTaWduICxZb3NzaTCCAiIwDQYJ
|
||||||
|
KoZIhvcNAQEBBQADggIPADCCAgoCggIBAN93Sx7QkE3PZVE1NylelP86p1oA2zv9
|
||||||
|
LQBQUiwKkT4Q4gWX8TkyJL/t9AXMxdyxBF31RdNY8DF32ujfowWQdjARB7UhY8Wq
|
||||||
|
A0YlSbD1RwknRrgt+g5Jq6LpeesKQ2PTp9qGDWVqLIZF8/xBlcJKD/pnNesUdGQ+
|
||||||
|
zLx6sro/Tme6LvaFNw4vHmfLGPnsBveqA27Vkz6j2Aay3STMWS7DMb/+aYBGUKvy
|
||||||
|
rZGd4WOXuCY8GkB1apguEFIBRKwWl40bKXgmKqbQSbrfP1Ze5i8kibPUW6cnGkQZ
|
||||||
|
d5o0GJ+1Vjis6rVULNZTFaoPiWTtZDf3atXtTsVI2MkiUPVJ7yh59OiIFENhPM5Q
|
||||||
|
zSjaix4cScMMhCagKMIcU4XfqcimZY4EnMqTq+FCPvmBPdUwbZnbkJOFe8lcueiP
|
||||||
|
k9Wc3xrvskbDILtfq8e0+AGDPa1ZNv+BkXeQG0bEYsvZTSolBXgXwgXJmtlrM0jR
|
||||||
|
3VzBAJTpzXmYel9o2HWpJcpBwPRjtNPXPrj9bXD6hlFdzMIdt8gx1KRZDXQB0ZJM
|
||||||
|
LHlIEg89BgByriuhLMZ6/nUKcK5Adjo7hyI+WvQrSsD8dM9bt3jqXTjjhNspnB14
|
||||||
|
LvpQeJF9AYhXo1YXYnQ3ipveiUt/ib9Y7BbD2zETOnWZZc7+EhUWBN4Q2Ajv5ddn
|
||||||
|
03zJE08oSiPHAgMBAAGjUzBRMB0GA1UdDgQWBBSZDKHvARiHteEbzaAccd8ZpZUL
|
||||||
|
mDAfBgNVHSMEGDAWgBSZDKHvARiHteEbzaAccd8ZpZULmDAPBgNVHRMBAf8EBTAD
|
||||||
|
AQH/MA0GCSqGSIb3DQEBCwUAA4ICAQBiSiaEOJQRzEm8Sa9ig5k8UEuicZRIt0jR
|
||||||
|
h/rlREa9En559XyxwXGXloFbmiUdlXV26BUtbWYn6J178xZ7B0x9istJq20ZeiZF
|
||||||
|
ABvv9DjuATbOLao65mowPL68C8R6ynRplVV7HE+zB3CUt4fyGEs/ud9n8DaqQysc
|
||||||
|
/im40yPqTobBKWJ1RWOrAddyHpQEqdXVxH2EkHTlyvcr9StTN4/pF5iVYeaniXnZ
|
||||||
|
PXqaEnYoqT9c2q8VAWc2a00dSrmHqw2TGKYJ2cSV8olkcdS6nknBsroQMd6Z8eZs
|
||||||
|
lGnwC1L4Nu1WJg8ZIy+Umcf0xAwSU3Zs7AhWIph+sO1Tc8iNFSLLotOKEO0xjBrZ
|
||||||
|
9ierDYZLAVx6XCIiArzgIM0XOwzPKTkwRZ7ip5n4mWx7GxmFJREAvwjRXuWNLZtj
|
||||||
|
s+IfCshjUfBUymYXn544mhou6uv9TeFQcxJ2RUzNr3xrxCuuriaUOGGBAaqrPpec
|
||||||
|
r2wWl/hlpjcw606NHbDlLzRUDO4Rwy1wZ5F6Pr7VXBqZy43tbB9VNbQErXdth0kH
|
||||||
|
UkjRGtv8zTO3MfG8FO1yv+QsWkHAAx73j8jGeSlLrma/KJAaJPpy0b1ud/12yCY4
|
||||||
|
GkFFhltXuc5f9tx+YvBUprWmZ9pd/tcFC+s/7XtpFU3STdfjlhZ6mzcC0IkxuNO9
|
||||||
|
HamDmBP6+A==
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
0b:e6:f7:90:1b:23:27:7d:c5:f3:e5:77:3c:5a:50:53:e8:7a:1f:41
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign ,Yossi"
|
||||||
|
Validity
|
||||||
|
Not Before: Aug 12 19:04:19 2019 GMT
|
||||||
|
Not After : Jun 20 19:04:19 2029 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign ,Yossi"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:df:77:4b:1e:d0:90:4d:cf:65:51:35:37:29:5e:
|
||||||
|
94:ff:3a:a7:5a:00:db:3b:fd:2d:00:50:52:2c:0a:
|
||||||
|
91:3e:10:e2:05:97:f1:39:32:24:bf:ed:f4:05:cc:
|
||||||
|
c5:dc:b1:04:5d:f5:45:d3:58:f0:31:77:da:e8:df:
|
||||||
|
a3:05:90:76:30:11:07:b5:21:63:c5:aa:03:46:25:
|
||||||
|
49:b0:f5:47:09:27:46:b8:2d:fa:0e:49:ab:a2:e9:
|
||||||
|
79:eb:0a:43:63:d3:a7:da:86:0d:65:6a:2c:86:45:
|
||||||
|
f3:fc:41:95:c2:4a:0f:fa:67:35:eb:14:74:64:3e:
|
||||||
|
cc:bc:7a:b2:ba:3f:4e:67:ba:2e:f6:85:37:0e:2f:
|
||||||
|
1e:67:cb:18:f9:ec:06:f7:aa:03:6e:d5:93:3e:a3:
|
||||||
|
d8:06:b2:dd:24:cc:59:2e:c3:31:bf:fe:69:80:46:
|
||||||
|
50:ab:f2:ad:91:9d:e1:63:97:b8:26:3c:1a:40:75:
|
||||||
|
6a:98:2e:10:52:01:44:ac:16:97:8d:1b:29:78:26:
|
||||||
|
2a:a6:d0:49:ba:df:3f:56:5e:e6:2f:24:89:b3:d4:
|
||||||
|
5b:a7:27:1a:44:19:77:9a:34:18:9f:b5:56:38:ac:
|
||||||
|
ea:b5:54:2c:d6:53:15:aa:0f:89:64:ed:64:37:f7:
|
||||||
|
6a:d5:ed:4e:c5:48:d8:c9:22:50:f5:49:ef:28:79:
|
||||||
|
f4:e8:88:14:43:61:3c:ce:50:cd:28:da:8b:1e:1c:
|
||||||
|
49:c3:0c:84:26:a0:28:c2:1c:53:85:df:a9:c8:a6:
|
||||||
|
65:8e:04:9c:ca:93:ab:e1:42:3e:f9:81:3d:d5:30:
|
||||||
|
6d:99:db:90:93:85:7b:c9:5c:b9:e8:8f:93:d5:9c:
|
||||||
|
df:1a:ef:b2:46:c3:20:bb:5f:ab:c7:b4:f8:01:83:
|
||||||
|
3d:ad:59:36:ff:81:91:77:90:1b:46:c4:62:cb:d9:
|
||||||
|
4d:2a:25:05:78:17:c2:05:c9:9a:d9:6b:33:48:d1:
|
||||||
|
dd:5c:c1:00:94:e9:cd:79:98:7a:5f:68:d8:75:a9:
|
||||||
|
25:ca:41:c0:f4:63:b4:d3:d7:3e:b8:fd:6d:70:fa:
|
||||||
|
86:51:5d:cc:c2:1d:b7:c8:31:d4:a4:59:0d:74:01:
|
||||||
|
d1:92:4c:2c:79:48:12:0f:3d:06:00:72:ae:2b:a1:
|
||||||
|
2c:c6:7a:fe:75:0a:70:ae:40:76:3a:3b:87:22:3e:
|
||||||
|
5a:f4:2b:4a:c0:fc:74:cf:5b:b7:78:ea:5d:38:e3:
|
||||||
|
84:db:29:9c:1d:78:2e:fa:50:78:91:7d:01:88:57:
|
||||||
|
a3:56:17:62:74:37:8a:9b:de:89:4b:7f:89:bf:58:
|
||||||
|
ec:16:c3:db:31:13:3a:75:99:65:ce:fe:12:15:16:
|
||||||
|
04:de:10:d8:08:ef:e5:d7:67:d3:7c:c9:13:4f:28:
|
||||||
|
4a:23:c7
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
99:0C:A1:EF:01:18:87:B5:E1:1B:CD:A0:1C:71:DF:19:A5:95:0B:98
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:99:0C:A1:EF:01:18:87:B5:E1:1B:CD:A0:1C:71:DF:19:A5:95:0B:98
|
||||||
|
|
||||||
|
X509v3 Basic Constraints: critical
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
62:4a:26:84:38:94:11:cc:49:bc:49:af:62:83:99:3c:50:4b:
|
||||||
|
a2:71:94:48:b7:48:d1:87:fa:e5:44:46:bd:12:7e:79:f5:7c:
|
||||||
|
b1:c1:71:97:96:81:5b:9a:25:1d:95:75:76:e8:15:2d:6d:66:
|
||||||
|
27:e8:9d:7b:f3:16:7b:07:4c:7d:8a:cb:49:ab:6d:19:7a:26:
|
||||||
|
45:00:1b:ef:f4:38:ee:01:36:ce:2d:aa:3a:e6:6a:30:3c:be:
|
||||||
|
bc:0b:c4:7a:ca:74:69:95:55:7b:1c:4f:b3:07:70:94:b7:87:
|
||||||
|
f2:18:4b:3f:b9:df:67:f0:36:aa:43:2b:1c:fe:29:b8:d3:23:
|
||||||
|
ea:4e:86:c1:29:62:75:45:63:ab:01:d7:72:1e:94:04:a9:d5:
|
||||||
|
d5:c4:7d:84:90:74:e5:ca:f7:2b:f5:2b:53:37:8f:e9:17:98:
|
||||||
|
95:61:e6:a7:89:79:d9:3d:7a:9a:12:76:28:a9:3f:5c:da:af:
|
||||||
|
15:01:67:36:6b:4d:1d:4a:b9:87:ab:0d:93:18:a6:09:d9:c4:
|
||||||
|
95:f2:89:64:71:d4:ba:9e:49:c1:b2:ba:10:31:de:99:f1:e6:
|
||||||
|
6c:94:69:f0:0b:52:f8:36:ed:56:26:0f:19:23:2f:94:99:c7:
|
||||||
|
f4:c4:0c:12:53:76:6c:ec:08:56:22:98:7e:b0:ed:53:73:c8:
|
||||||
|
8d:15:22:cb:a2:d3:8a:10:ed:31:8c:1a:d9:f6:27:ab:0d:86:
|
||||||
|
4b:01:5c:7a:5c:22:22:02:bc:e0:20:cd:17:3b:0c:cf:29:39:
|
||||||
|
30:45:9e:e2:a7:99:f8:99:6c:7b:1b:19:85:25:11:00:bf:08:
|
||||||
|
d1:5e:e5:8d:2d:9b:63:b3:e2:1f:0a:c8:63:51:f0:54:ca:66:
|
||||||
|
17:9f:9e:38:9a:1a:2e:ea:eb:fd:4d:e1:50:73:12:76:45:4c:
|
||||||
|
cd:af:7c:6b:c4:2b:ae:ae:26:94:38:61:81:01:aa:ab:3e:97:
|
||||||
|
9c:af:6c:16:97:f8:65:a6:37:30:eb:4e:8d:1d:b0:e5:2f:34:
|
||||||
|
54:0c:ee:11:c3:2d:70:67:91:7a:3e:be:d5:5c:1a:99:cb:8d:
|
||||||
|
ed:6c:1f:55:35:b4:04:ad:77:6d:87:49:07:52:48:d1:1a:db:
|
||||||
|
fc:cd:33:b7:31:f1:bc:14:ed:72:bf:e4:2c:5a:41:c0:03:1e:
|
||||||
|
f7:8f:c8:c6:79:29:4b:ae:66:bf:28:90:1a:24:fa:72:d1:bd:
|
||||||
|
6e:77:fd:76:c8:26:38:1a:41:45:86:5b:57:b9:ce:5f:f6:dc:
|
||||||
|
7e:62:f0:54:a6:b5:a6:67:da:5d:fe:d7:05:0b:eb:3f:ed:7b:
|
||||||
|
69:15:4d:d2:4d:d7:e3:96:16:7a:9b:37:02:d0:89:31:b8:d3:
|
||||||
|
bd:1d:a9:83:98:13:fa:f8
|
||||||
81
MagiskOnWSA/cacerts/0b4055f7.0
Normal file
81
MagiskOnWSA/cacerts/0b4055f7.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIID5TCCAs2gAwIBAgIJALnD1+pTBr26MA0GCSqGSIb3DQEBCwUAMIGIMQswCQYD
|
||||||
|
VQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIwEAYDVQQHDAlKZXJ1c2FsZW0xEDAO
|
||||||
|
BgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5ldGZyZWUubGluazErMCkGA1UEAwwi
|
||||||
|
TmV0RnJlZSBTaWduICwgU2ltS2FzaGVyIC0gVHJpcGxlQzAeFw0xNzA2MjYxNzUx
|
||||||
|
MDlaFw0yNzA1MDUxNzUxMDlaMIGIMQswCQYDVQQGEwJJTDEPMA0GA1UECAwGaXNy
|
||||||
|
YWVsMRIwEAYDVQQHDAlKZXJ1c2FsZW0xEDAOBgNVBAoMB05ldEZyZWUxFTATBgNV
|
||||||
|
BAsMDG5ldGZyZWUubGluazErMCkGA1UEAwwiTmV0RnJlZSBTaWduICwgU2ltS2Fz
|
||||||
|
aGVyIC0gVHJpcGxlQzCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAMM5
|
||||||
|
FtnDwNn6ErV5rZhc9VV1ujRRSDfK6n9TjK0zaHKhwrTgzj6YxzopfspqwoZM6QqS
|
||||||
|
ivNtDLKfQyVFUYGAFQiQgShQNYS8GheXqTI/U7SdWgKFUkdcOPmzNusYwa+G0cLz
|
||||||
|
NiRkKS+yRm+sGf+QLu18KACoc5FbL1+rM8OR0aCG2md/K8Z6xnYm371BGEiZjjhX
|
||||||
|
4tGL7SonHPs35Ga4LI6pJfUUItcliWBW6HnwcRk7Ilq/9q5gUjR5sbIvt0+9hdhj
|
||||||
|
1UQjE4gcsPzN5Fc+RvwDXBqozIk8cPVSNycwY2VZ4FofEAjtanS9R5LrshKK6Oi2
|
||||||
|
n61xzE/vHMVUJKYXqcUCAwEAAaNQME4wHQYDVR0OBBYEFFr8sgox5u0dhxiDDE7A
|
||||||
|
n11wTtBNMB8GA1UdIwQYMBaAFFr8sgox5u0dhxiDDE7An11wTtBNMAwGA1UdEwQF
|
||||||
|
MAMBAf8wDQYJKoZIhvcNAQELBQADggEBAJSPrJ3a3M0m+dHuGevOMKOjP5NexEiT
|
||||||
|
hWUX86/b7u0rKfphqGsl4y+wXRCiMydOwZCMg7MQjYvmT8XoN0rlVu73BxpcxYJg
|
||||||
|
I6Il4erTBSitCiXF39RQ3XW/akAqgAsaPSD4TdSImCVHW3UgJxHtRcM4SodIo+Zh
|
||||||
|
7WuNXCC5ET/C4y2EeMOtkWIcuncjPrL7pJwwiHPYjhK+SiievAzDGhrXbJxAmgy2
|
||||||
|
wsV6qU03j0I3fH1jC23SJRA8GudrZqUoTcfQmERPnyTiTp1Hn271crZ8ai9MPZQm
|
||||||
|
c+wKYHlblPbaj0EA06Dh6uCexhyTxa0wRtTODIfCxoHJMWWWPKb9H3k=
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
b9:c3:d7:ea:53:06:bd:ba
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , SimKasher - TripleC"
|
||||||
|
Validity
|
||||||
|
Not Before: Jun 26 17:51:09 2017 GMT
|
||||||
|
Not After : May 5 17:51:09 2027 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , SimKasher - TripleC"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:c3:39:16:d9:c3:c0:d9:fa:12:b5:79:ad:98:5c:
|
||||||
|
f5:55:75:ba:34:51:48:37:ca:ea:7f:53:8c:ad:33:
|
||||||
|
68:72:a1:c2:b4:e0:ce:3e:98:c7:3a:29:7e:ca:6a:
|
||||||
|
c2:86:4c:e9:0a:92:8a:f3:6d:0c:b2:9f:43:25:45:
|
||||||
|
51:81:80:15:08:90:81:28:50:35:84:bc:1a:17:97:
|
||||||
|
a9:32:3f:53:b4:9d:5a:02:85:52:47:5c:38:f9:b3:
|
||||||
|
36:eb:18:c1:af:86:d1:c2:f3:36:24:64:29:2f:b2:
|
||||||
|
46:6f:ac:19:ff:90:2e:ed:7c:28:00:a8:73:91:5b:
|
||||||
|
2f:5f:ab:33:c3:91:d1:a0:86:da:67:7f:2b:c6:7a:
|
||||||
|
c6:76:26:df:bd:41:18:48:99:8e:38:57:e2:d1:8b:
|
||||||
|
ed:2a:27:1c:fb:37:e4:66:b8:2c:8e:a9:25:f5:14:
|
||||||
|
22:d7:25:89:60:56:e8:79:f0:71:19:3b:22:5a:bf:
|
||||||
|
f6:ae:60:52:34:79:b1:b2:2f:b7:4f:bd:85:d8:63:
|
||||||
|
d5:44:23:13:88:1c:b0:fc:cd:e4:57:3e:46:fc:03:
|
||||||
|
5c:1a:a8:cc:89:3c:70:f5:52:37:27:30:63:65:59:
|
||||||
|
e0:5a:1f:10:08:ed:6a:74:bd:47:92:eb:b2:12:8a:
|
||||||
|
e8:e8:b6:9f:ad:71:cc:4f:ef:1c:c5:54:24:a6:17:
|
||||||
|
a9:c5
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
5A:FC:B2:0A:31:E6:ED:1D:87:18:83:0C:4E:C0:9F:5D:70:4E:D0:4D
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:5A:FC:B2:0A:31:E6:ED:1D:87:18:83:0C:4E:C0:9F:5D:70:4E:D0:4D
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
94:8f:ac:9d:da:dc:cd:26:f9:d1:ee:19:eb:ce:30:a3:a3:3f:
|
||||||
|
93:5e:c4:48:93:85:65:17:f3:af:db:ee:ed:2b:29:fa:61:a8:
|
||||||
|
6b:25:e3:2f:b0:5d:10:a2:33:27:4e:c1:90:8c:83:b3:10:8d:
|
||||||
|
8b:e6:4f:c5:e8:37:4a:e5:56:ee:f7:07:1a:5c:c5:82:60:23:
|
||||||
|
a2:25:e1:ea:d3:05:28:ad:0a:25:c5:df:d4:50:dd:75:bf:6a:
|
||||||
|
40:2a:80:0b:1a:3d:20:f8:4d:d4:88:98:25:47:5b:75:20:27:
|
||||||
|
11:ed:45:c3:38:4a:87:48:a3:e6:61:ed:6b:8d:5c:20:b9:11:
|
||||||
|
3f:c2:e3:2d:84:78:c3:ad:91:62:1c:ba:77:23:3e:b2:fb:a4:
|
||||||
|
9c:30:88:73:d8:8e:12:be:4a:28:9e:bc:0c:c3:1a:1a:d7:6c:
|
||||||
|
9c:40:9a:0c:b6:c2:c5:7a:a9:4d:37:8f:42:37:7c:7d:63:0b:
|
||||||
|
6d:d2:25:10:3c:1a:e7:6b:66:a5:28:4d:c7:d0:98:44:4f:9f:
|
||||||
|
24:e2:4e:9d:47:9f:6e:f5:72:b6:7c:6a:2f:4c:3d:94:26:73:
|
||||||
|
ec:0a:60:79:5b:94:f6:da:8f:41:00:d3:a0:e1:ea:e0:9e:c6:
|
||||||
|
1c:93:c5:ad:30:46:d4:ce:0c:87:c2:c6:81:c9:31:65:96:3c:
|
||||||
|
a6:fd:1f:79
|
||||||
123
MagiskOnWSA/cacerts/281f8e47.0
Normal file
123
MagiskOnWSA/cacerts/281f8e47.0
Normal file
@ -0,0 +1,123 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIF1zCCA7+gAwIBAgIUVRcB1uWuaruggL9hYC31+1eO8wEwDQYJKoZIhvcNAQEL
|
||||||
|
BQAwezELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAGA1UEBwwJSmVy
|
||||||
|
dXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRmcmVlLmxpbmsx
|
||||||
|
HjAcBgNVBAMMFU5ldEZyZWUgU2lnbiwgQW1pdE5ldDAeFw0yMDEyMTUxMjQ1MTJa
|
||||||
|
Fw0zMDEyMTMxMjQ1MTJaMHsxCzAJBgNVBAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwx
|
||||||
|
EjAQBgNVBAcMCUplcnVzYWxlbTEQMA4GA1UECgwHTmV0RnJlZTEVMBMGA1UECwwM
|
||||||
|
bmV0ZnJlZS5saW5rMR4wHAYDVQQDDBVOZXRGcmVlIFNpZ24sIEFtaXROZXQwggIi
|
||||||
|
MA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQDNCFBv23NbP80PnYb1j8EQFbUB
|
||||||
|
IUG7ZaR/7acSU5+zFpagTX1HASboUZ6sTVSKYIM/cJ8J6B97PkVb4J1I6+pVa7x3
|
||||||
|
LNJqReP9fCSknshNsc0NlxB4xcCnheov4HYrgW37hznEbiSrR+hDHR0W2A96IEHx
|
||||||
|
x71A3/mQ5Rl2jXv+negYa/xNK8uh+6xGN/zrowPNc8c4EC94hCpuwAzYqoXR+Iph
|
||||||
|
hcdK8WKIge3isEtpYYcswk8U7YIXe6sSAUrVcXaZURTAX00LPptXM92l4C+pBQ4j
|
||||||
|
xgOxXSVJWig7QLJuCPw0BjlLAVwvc4zWib/6tBUcHUZYcZ9+jm7D9sUkD3/Q2WDm
|
||||||
|
BlFMGhGuIGW4FeiX+kSGGYlskds4RYsf6iHVLBAUc3MhtXRPSt3RgTLw823b4dwj
|
||||||
|
OG/0RWjhynRHWmBvW+mWZgGPDZ/VxDR2dltWXGcWyz9hfQNBNhUberBhtLpydHfK
|
||||||
|
4qpYNr7yWBJbXDsXTM6Y5rYVHiWYz/Mf47SEMUhGnqHDlENWNHVAz8LD4xmeywLl
|
||||||
|
1HkcMygyQMKtfTQ8V2Y/7cftfSrTGfG4uTKvewGbsET+ZS0G2aInFijQfnKrhWc+
|
||||||
|
foAVimtJY0KssNDzHpcMMjJAqoIulP4/Mj4ny7XLEIba8o3VI8g20lfZPpo3jl1H
|
||||||
|
KpXNpVOTOR+h/PNUiQIDAQABo1MwUTAdBgNVHQ4EFgQUNtscwInvEKf/FZdrLO1r
|
||||||
|
3yBoFi8wHwYDVR0jBBgwFoAUNtscwInvEKf/FZdrLO1r3yBoFi8wDwYDVR0TAQH/
|
||||||
|
BAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAgEAidKPUdFTIOeiE4CemLVrns6EkNd5
|
||||||
|
zbfi3jeYCvTSzf/ij0Xu7dzZ8valIylgaKQaT3DizHbhtWbmeMbz/0uE08fYIzsY
|
||||||
|
JJBMTf9IoB6bjWcGqWuszM0rVO/wWKhxTG4w+VSScFLT2PHS/8PHpmcQEo8j2QWf
|
||||||
|
+4pAfruFIkoCfApYQE3GaJRZ/vrPGFBfnWEo5K57DivHN/raVu26x83twI6rnYlO
|
||||||
|
htI+p3gV5LZFn66txZAmicA7LFp7wbwTDJwWX+XvOhuHlE11mMkWY3oFei/EZiub
|
||||||
|
n+2Brmt7p9cX2Wkrw5eZdFenGyM8vmzEEExOnuraojfHS/p5G3r4j92Kt/yBZVfK
|
||||||
|
RWqooVQ4J30YL6Z90Rz++wExvsBaYtY+ZjYvso6Mi7N42iemz7fR2h+VBv9BcUKs
|
||||||
|
HET94gNwVsYi7++uqjLyB1NxzpFcPQmfGEJZeQiDeyfY1W2KKiUEsTpi6xu9Bkki
|
||||||
|
dAOiEmiwk2IAv+a0Sd+FalvURx6ldrqCy3ki8offnrPcjedY8kjnyijdOTuj6dTh
|
||||||
|
ybzqxcXItfxrpA+s0bWFh4DK3kP8uUsPBz4q5aHLxtTHMFULXRt4gBifV6InysNx
|
||||||
|
UuqP4yTPCR3QoES4Aba7PR18RnTZXnYWXnsWSspEf1Cf3jTkI9OpB8MHrWh+7v5O
|
||||||
|
AiH5GAGaSCVrseI=
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
55:17:01:d6:e5:ae:6a:bb:a0:80:bf:61:60:2d:f5:fb:57:8e:f3:01
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, AmitNet"
|
||||||
|
Validity
|
||||||
|
Not Before: Dec 15 12:45:12 2020 GMT
|
||||||
|
Not After : Dec 13 12:45:12 2030 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, AmitNet"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:cd:08:50:6f:db:73:5b:3f:cd:0f:9d:86:f5:8f:
|
||||||
|
c1:10:15:b5:01:21:41:bb:65:a4:7f:ed:a7:12:53:
|
||||||
|
9f:b3:16:96:a0:4d:7d:47:01:26:e8:51:9e:ac:4d:
|
||||||
|
54:8a:60:83:3f:70:9f:09:e8:1f:7b:3e:45:5b:e0:
|
||||||
|
9d:48:eb:ea:55:6b:bc:77:2c:d2:6a:45:e3:fd:7c:
|
||||||
|
24:a4:9e:c8:4d:b1:cd:0d:97:10:78:c5:c0:a7:85:
|
||||||
|
ea:2f:e0:76:2b:81:6d:fb:87:39:c4:6e:24:ab:47:
|
||||||
|
e8:43:1d:1d:16:d8:0f:7a:20:41:f1:c7:bd:40:df:
|
||||||
|
f9:90:e5:19:76:8d:7b:fe:9d:e8:18:6b:fc:4d:2b:
|
||||||
|
cb:a1:fb:ac:46:37:fc:eb:a3:03:cd:73:c7:38:10:
|
||||||
|
2f:78:84:2a:6e:c0:0c:d8:aa:85:d1:f8:8a:61:85:
|
||||||
|
c7:4a:f1:62:88:81:ed:e2:b0:4b:69:61:87:2c:c2:
|
||||||
|
4f:14:ed:82:17:7b:ab:12:01:4a:d5:71:76:99:51:
|
||||||
|
14:c0:5f:4d:0b:3e:9b:57:33:dd:a5:e0:2f:a9:05:
|
||||||
|
0e:23:c6:03:b1:5d:25:49:5a:28:3b:40:b2:6e:08:
|
||||||
|
fc:34:06:39:4b:01:5c:2f:73:8c:d6:89:bf:fa:b4:
|
||||||
|
15:1c:1d:46:58:71:9f:7e:8e:6e:c3:f6:c5:24:0f:
|
||||||
|
7f:d0:d9:60:e6:06:51:4c:1a:11:ae:20:65:b8:15:
|
||||||
|
e8:97:fa:44:86:19:89:6c:91:db:38:45:8b:1f:ea:
|
||||||
|
21:d5:2c:10:14:73:73:21:b5:74:4f:4a:dd:d1:81:
|
||||||
|
32:f0:f3:6d:db:e1:dc:23:38:6f:f4:45:68:e1:ca:
|
||||||
|
74:47:5a:60:6f:5b:e9:96:66:01:8f:0d:9f:d5:c4:
|
||||||
|
34:76:76:5b:56:5c:67:16:cb:3f:61:7d:03:41:36:
|
||||||
|
15:1b:7a:b0:61:b4:ba:72:74:77:ca:e2:aa:58:36:
|
||||||
|
be:f2:58:12:5b:5c:3b:17:4c:ce:98:e6:b6:15:1e:
|
||||||
|
25:98:cf:f3:1f:e3:b4:84:31:48:46:9e:a1:c3:94:
|
||||||
|
43:56:34:75:40:cf:c2:c3:e3:19:9e:cb:02:e5:d4:
|
||||||
|
79:1c:33:28:32:40:c2:ad:7d:34:3c:57:66:3f:ed:
|
||||||
|
c7:ed:7d:2a:d3:19:f1:b8:b9:32:af:7b:01:9b:b0:
|
||||||
|
44:fe:65:2d:06:d9:a2:27:16:28:d0:7e:72:ab:85:
|
||||||
|
67:3e:7e:80:15:8a:6b:49:63:42:ac:b0:d0:f3:1e:
|
||||||
|
97:0c:32:32:40:aa:82:2e:94:fe:3f:32:3e:27:cb:
|
||||||
|
b5:cb:10:86:da:f2:8d:d5:23:c8:36:d2:57:d9:3e:
|
||||||
|
9a:37:8e:5d:47:2a:95:cd:a5:53:93:39:1f:a1:fc:
|
||||||
|
f3:54:89
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
36:DB:1C:C0:89:EF:10:A7:FF:15:97:6B:2C:ED:6B:DF:20:68:16:2F
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:36:DB:1C:C0:89:EF:10:A7:FF:15:97:6B:2C:ED:6B:DF:20:68:16:2F
|
||||||
|
|
||||||
|
X509v3 Basic Constraints: critical
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
89:d2:8f:51:d1:53:20:e7:a2:13:80:9e:98:b5:6b:9e:ce:84:
|
||||||
|
90:d7:79:cd:b7:e2:de:37:98:0a:f4:d2:cd:ff:e2:8f:45:ee:
|
||||||
|
ed:dc:d9:f2:f6:a5:23:29:60:68:a4:1a:4f:70:e2:cc:76:e1:
|
||||||
|
b5:66:e6:78:c6:f3:ff:4b:84:d3:c7:d8:23:3b:18:24:90:4c:
|
||||||
|
4d:ff:48:a0:1e:9b:8d:67:06:a9:6b:ac:cc:cd:2b:54:ef:f0:
|
||||||
|
58:a8:71:4c:6e:30:f9:54:92:70:52:d3:d8:f1:d2:ff:c3:c7:
|
||||||
|
a6:67:10:12:8f:23:d9:05:9f:fb:8a:40:7e:bb:85:22:4a:02:
|
||||||
|
7c:0a:58:40:4d:c6:68:94:59:fe:fa:cf:18:50:5f:9d:61:28:
|
||||||
|
e4:ae:7b:0e:2b:c7:37:fa:da:56:ed:ba:c7:cd:ed:c0:8e:ab:
|
||||||
|
9d:89:4e:86:d2:3e:a7:78:15:e4:b6:45:9f:ae:ad:c5:90:26:
|
||||||
|
89:c0:3b:2c:5a:7b:c1:bc:13:0c:9c:16:5f:e5:ef:3a:1b:87:
|
||||||
|
94:4d:75:98:c9:16:63:7a:05:7a:2f:c4:66:2b:9b:9f:ed:81:
|
||||||
|
ae:6b:7b:a7:d7:17:d9:69:2b:c3:97:99:74:57:a7:1b:23:3c:
|
||||||
|
be:6c:c4:10:4c:4e:9e:ea:da:a2:37:c7:4b:fa:79:1b:7a:f8:
|
||||||
|
8f:dd:8a:b7:fc:81:65:57:ca:45:6a:a8:a1:54:38:27:7d:18:
|
||||||
|
2f:a6:7d:d1:1c:fe:fb:01:31:be:c0:5a:62:d6:3e:66:36:2f:
|
||||||
|
b2:8e:8c:8b:b3:78:da:27:a6:cf:b7:d1:da:1f:95:06:ff:41:
|
||||||
|
71:42:ac:1c:44:fd:e2:03:70:56:c6:22:ef:ef:ae:aa:32:f2:
|
||||||
|
07:53:71:ce:91:5c:3d:09:9f:18:42:59:79:08:83:7b:27:d8:
|
||||||
|
d5:6d:8a:2a:25:04:b1:3a:62:eb:1b:bd:06:49:22:74:03:a2:
|
||||||
|
12:68:b0:93:62:00:bf:e6:b4:49:df:85:6a:5b:d4:47:1e:a5:
|
||||||
|
76:ba:82:cb:79:22:f2:87:df:9e:b3:dc:8d:e7:58:f2:48:e7:
|
||||||
|
ca:28:dd:39:3b:a3:e9:d4:e1:c9:bc:ea:c5:c5:c8:b5:fc:6b:
|
||||||
|
a4:0f:ac:d1:b5:85:87:80:ca:de:43:fc:b9:4b:0f:07:3e:2a:
|
||||||
|
e5:a1:cb:c6:d4:c7:30:55:0b:5d:1b:78:80:18:9f:57:a2:27:
|
||||||
|
ca:c3:71:52:ea:8f:e3:24:cf:09:1d:d0:a0:44:b8:01:b6:bb:
|
||||||
|
3d:1d:7c:46:74:d9:5e:76:16:5e:7b:16:4a:ca:44:7f:50:9f:
|
||||||
|
de:34:e4:23:d3:a9:07:c3:07:ad:68:7e:ee:fe:4e:02:21:f9:
|
||||||
|
18:01:9a:48:25:6b:b1:e2
|
||||||
123
MagiskOnWSA/cacerts/2ef957f0.0
Normal file
123
MagiskOnWSA/cacerts/2ef957f0.0
Normal file
@ -0,0 +1,123 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIF4zCCA8ugAwIBAgIUAkc9yNk/4jz9hPra/7vONeYwrtIwDQYJKoZIhvcNAQEL
|
||||||
|
BQAwgYAxCzAJBgNVBAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcMCUpl
|
||||||
|
cnVzYWxlbTEQMA4GA1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0ZnJlZS5saW5r
|
||||||
|
MSMwIQYDVQQDDBpOZXRGcmVlIFNpZ24sIElCIC0gc3BvdG5ldDAeFw0yMDA1MTMw
|
||||||
|
ODIzMjJaFw0zMDA1MTEwODIzMjJaMIGAMQswCQYDVQQGEwJJTDEPMA0GA1UECAwG
|
||||||
|
aXNyYWVsMRIwEAYDVQQHDAlKZXJ1c2FsZW0xEDAOBgNVBAoMB05ldEZyZWUxFTAT
|
||||||
|
BgNVBAsMDG5ldGZyZWUubGluazEjMCEGA1UEAwwaTmV0RnJlZSBTaWduLCBJQiAt
|
||||||
|
IHNwb3RuZXQwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQDNgVcx94Ap
|
||||||
|
985mKOzFx4/lExkRuI8f9hdAUY9XqE94X7fT8hmCP6pxy/7+JzMjfn/YMmECea51
|
||||||
|
cuV4ZH+xUZ5WxoQajx/ICJtfaOSV/YIkB40o6JcN95EhKuickdiWnGFjsOZwc1Wj
|
||||||
|
sqHzjNZJWvV3KnoUGJQfc0F7/Th7HvQoNRqAkUBcXS521m7GqndlmE5zAo7WCD/N
|
||||||
|
7ggWeO2g8xPOW5YldHZ9mMSZXVYLRn95wrEtBX4SVXqSWdlPAE+m1jbHU2Gu2eM5
|
||||||
|
LxichbN1FQRL63aeZJjSgOEDaWnASLlqq+rnIWiecoYOGe7qoNl+jGaNAQmg3bq0
|
||||||
|
nOYouRu7nUGQbOn/eX3BwHEVx9WKiUPHop24NPW70wXXfEU0UNM3FjuU/V/uFA89
|
||||||
|
RQZRcg28O3SrzLybBGwCo+Kp5Sp54a59/Uw5FvX9OSsHX/QqdMxtFWlXvwqeuV8p
|
||||||
|
DOlYrAU8WrttR4ruZ3OJ5Rd5w8eu0U2s+dQLrMVgJo2ji2Ji9tBoHId50KVSBDgq
|
||||||
|
TGs40TB3cnWeO0kf3luz8CgH/+ls08ruDSXpA88FL6adFLfMhfDgBjq9OM0twL31
|
||||||
|
dVeZvxplqSvLQqiO7uc6s2qzGN/KaMP41eZaWuuiwZtwnFbArg8H2zQDpcLM72Ha
|
||||||
|
yeqQUAHHIjDx4pmww9yeSk8a1a0Pt71SLwIDAQABo1MwUTAdBgNVHQ4EFgQUU0dF
|
||||||
|
eW32zoZaL/BW2H++Jj5tyK8wHwYDVR0jBBgwFoAUU0dFeW32zoZaL/BW2H++Jj5t
|
||||||
|
yK8wDwYDVR0TAQH/BAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAgEAlwsfMiO4Bg0E
|
||||||
|
ciN+dAs0+i9grg0CzD2qUpVl6rDN6Vq12DoLgIL/qAH9wiKDPfl9LniwLQfkK/HE
|
||||||
|
U868x90OOaopBhrO+SPfQX0grz2xYDxnMJXuBKDGr8jHy+QeRq2JN4Sq9BW8Ayfo
|
||||||
|
9Z3xFpGAf0pohvT5ipeR45u9BZsGBH49iur+snf+t4PL7we7Q4rZ5Z1ZFO0ctlGh
|
||||||
|
hkS6cGpsmkrH/ysQpD07JmN/Iwklz8xKyiRdRc1qL5BBbLOedawpPNA6PuVBNDg2
|
||||||
|
jLDZyiirC9zBUTIUohruHQ6lWyHxvx5+BcwmU2LEZMfIVFddQ/KOZ5FcsscDUxvg
|
||||||
|
YvFdB7iIZNOMBASowXcp7qq6gySkA0qoD+O55nvDocKkqsImuacmOAHmgXfd6zAV
|
||||||
|
QPo/l/qaMDldpYoKL3WI3GlViTKhBFBKqgb9iR8oKgzMdi+A95XzbHaFFrvG0NaU
|
||||||
|
Qdiuvp7e09Ja44RAbz2Q4JyDhoo1xxgvfCluUMWWT0AdE9UdV88lpaaD3iPHPOao
|
||||||
|
E1QFv5hb04gCSU5V+F8a/SULWUitu7NdiBZQRwYbk8xS7Ta8Qcn1/ICJHsx3FKbJ
|
||||||
|
Z2vhVxCoT22IAdbcd4AL2pJS3EqNZlydfcUg42vCDovKheTWNYQzBW5c0IKPKAq9
|
||||||
|
Z52Mpo8iek5gwCa8k8r1ZTiyODgDO7Y=
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
02:47:3d:c8:d9:3f:e2:3c:fd:84:fa:da:ff:bb:ce:35:e6:30:ae:d2
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, IB - spotnet"
|
||||||
|
Validity
|
||||||
|
Not Before: May 13 08:23:22 2020 GMT
|
||||||
|
Not After : May 11 08:23:22 2030 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, IB - spotnet"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:cd:81:57:31:f7:80:29:f7:ce:66:28:ec:c5:c7:
|
||||||
|
8f:e5:13:19:11:b8:8f:1f:f6:17:40:51:8f:57:a8:
|
||||||
|
4f:78:5f:b7:d3:f2:19:82:3f:aa:71:cb:fe:fe:27:
|
||||||
|
33:23:7e:7f:d8:32:61:02:79:ae:75:72:e5:78:64:
|
||||||
|
7f:b1:51:9e:56:c6:84:1a:8f:1f:c8:08:9b:5f:68:
|
||||||
|
e4:95:fd:82:24:07:8d:28:e8:97:0d:f7:91:21:2a:
|
||||||
|
e8:9c:91:d8:96:9c:61:63:b0:e6:70:73:55:a3:b2:
|
||||||
|
a1:f3:8c:d6:49:5a:f5:77:2a:7a:14:18:94:1f:73:
|
||||||
|
41:7b:fd:38:7b:1e:f4:28:35:1a:80:91:40:5c:5d:
|
||||||
|
2e:76:d6:6e:c6:aa:77:65:98:4e:73:02:8e:d6:08:
|
||||||
|
3f:cd:ee:08:16:78:ed:a0:f3:13:ce:5b:96:25:74:
|
||||||
|
76:7d:98:c4:99:5d:56:0b:46:7f:79:c2:b1:2d:05:
|
||||||
|
7e:12:55:7a:92:59:d9:4f:00:4f:a6:d6:36:c7:53:
|
||||||
|
61:ae:d9:e3:39:2f:18:9c:85:b3:75:15:04:4b:eb:
|
||||||
|
76:9e:64:98:d2:80:e1:03:69:69:c0:48:b9:6a:ab:
|
||||||
|
ea:e7:21:68:9e:72:86:0e:19:ee:ea:a0:d9:7e:8c:
|
||||||
|
66:8d:01:09:a0:dd:ba:b4:9c:e6:28:b9:1b:bb:9d:
|
||||||
|
41:90:6c:e9:ff:79:7d:c1:c0:71:15:c7:d5:8a:89:
|
||||||
|
43:c7:a2:9d:b8:34:f5:bb:d3:05:d7:7c:45:34:50:
|
||||||
|
d3:37:16:3b:94:fd:5f:ee:14:0f:3d:45:06:51:72:
|
||||||
|
0d:bc:3b:74:ab:cc:bc:9b:04:6c:02:a3:e2:a9:e5:
|
||||||
|
2a:79:e1:ae:7d:fd:4c:39:16:f5:fd:39:2b:07:5f:
|
||||||
|
f4:2a:74:cc:6d:15:69:57:bf:0a:9e:b9:5f:29:0c:
|
||||||
|
e9:58:ac:05:3c:5a:bb:6d:47:8a:ee:67:73:89:e5:
|
||||||
|
17:79:c3:c7:ae:d1:4d:ac:f9:d4:0b:ac:c5:60:26:
|
||||||
|
8d:a3:8b:62:62:f6:d0:68:1c:87:79:d0:a5:52:04:
|
||||||
|
38:2a:4c:6b:38:d1:30:77:72:75:9e:3b:49:1f:de:
|
||||||
|
5b:b3:f0:28:07:ff:e9:6c:d3:ca:ee:0d:25:e9:03:
|
||||||
|
cf:05:2f:a6:9d:14:b7:cc:85:f0:e0:06:3a:bd:38:
|
||||||
|
cd:2d:c0:bd:f5:75:57:99:bf:1a:65:a9:2b:cb:42:
|
||||||
|
a8:8e:ee:e7:3a:b3:6a:b3:18:df:ca:68:c3:f8:d5:
|
||||||
|
e6:5a:5a:eb:a2:c1:9b:70:9c:56:c0:ae:0f:07:db:
|
||||||
|
34:03:a5:c2:cc:ef:61:da:c9:ea:90:50:01:c7:22:
|
||||||
|
30:f1:e2:99:b0:c3:dc:9e:4a:4f:1a:d5:ad:0f:b7:
|
||||||
|
bd:52:2f
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
53:47:45:79:6D:F6:CE:86:5A:2F:F0:56:D8:7F:BE:26:3E:6D:C8:AF
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:53:47:45:79:6D:F6:CE:86:5A:2F:F0:56:D8:7F:BE:26:3E:6D:C8:AF
|
||||||
|
|
||||||
|
X509v3 Basic Constraints: critical
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
97:0b:1f:32:23:b8:06:0d:04:72:23:7e:74:0b:34:fa:2f:60:
|
||||||
|
ae:0d:02:cc:3d:aa:52:95:65:ea:b0:cd:e9:5a:b5:d8:3a:0b:
|
||||||
|
80:82:ff:a8:01:fd:c2:22:83:3d:f9:7d:2e:78:b0:2d:07:e4:
|
||||||
|
2b:f1:c4:53:ce:bc:c7:dd:0e:39:aa:29:06:1a:ce:f9:23:df:
|
||||||
|
41:7d:20:af:3d:b1:60:3c:67:30:95:ee:04:a0:c6:af:c8:c7:
|
||||||
|
cb:e4:1e:46:ad:89:37:84:aa:f4:15:bc:03:27:e8:f5:9d:f1:
|
||||||
|
16:91:80:7f:4a:68:86:f4:f9:8a:97:91:e3:9b:bd:05:9b:06:
|
||||||
|
04:7e:3d:8a:ea:fe:b2:77:fe:b7:83:cb:ef:07:bb:43:8a:d9:
|
||||||
|
e5:9d:59:14:ed:1c:b6:51:a1:86:44:ba:70:6a:6c:9a:4a:c7:
|
||||||
|
ff:2b:10:a4:3d:3b:26:63:7f:23:09:25:cf:cc:4a:ca:24:5d:
|
||||||
|
45:cd:6a:2f:90:41:6c:b3:9e:75:ac:29:3c:d0:3a:3e:e5:41:
|
||||||
|
34:38:36:8c:b0:d9:ca:28:ab:0b:dc:c1:51:32:14:a2:1a:ee:
|
||||||
|
1d:0e:a5:5b:21:f1:bf:1e:7e:05:cc:26:53:62:c4:64:c7:c8:
|
||||||
|
54:57:5d:43:f2:8e:67:91:5c:b2:c7:03:53:1b:e0:62:f1:5d:
|
||||||
|
07:b8:88:64:d3:8c:04:04:a8:c1:77:29:ee:aa:ba:83:24:a4:
|
||||||
|
03:4a:a8:0f:e3:b9:e6:7b:c3:a1:c2:a4:aa:c2:26:b9:a7:26:
|
||||||
|
38:01:e6:81:77:dd:eb:30:15:40:fa:3f:97:fa:9a:30:39:5d:
|
||||||
|
a5:8a:0a:2f:75:88:dc:69:55:89:32:a1:04:50:4a:aa:06:fd:
|
||||||
|
89:1f:28:2a:0c:cc:76:2f:80:f7:95:f3:6c:76:85:16:bb:c6:
|
||||||
|
d0:d6:94:41:d8:ae:be:9e:de:d3:d2:5a:e3:84:40:6f:3d:90:
|
||||||
|
e0:9c:83:86:8a:35:c7:18:2f:7c:29:6e:50:c5:96:4f:40:1d:
|
||||||
|
13:d5:1d:57:cf:25:a5:a6:83:de:23:c7:3c:e6:a8:13:54:05:
|
||||||
|
bf:98:5b:d3:88:02:49:4e:55:f8:5f:1a:fd:25:0b:59:48:ad:
|
||||||
|
bb:b3:5d:88:16:50:47:06:1b:93:cc:52:ed:36:bc:41:c9:f5:
|
||||||
|
fc:80:89:1e:cc:77:14:a6:c9:67:6b:e1:57:10:a8:4f:6d:88:
|
||||||
|
01:d6:dc:77:80:0b:da:92:52:dc:4a:8d:66:5c:9d:7d:c5:20:
|
||||||
|
e3:6b:c2:0e:8b:ca:85:e4:d6:35:84:33:05:6e:5c:d0:82:8f:
|
||||||
|
28:0a:bd:67:9d:8c:a6:8f:22:7a:4e:60:c0:26:bc:93:ca:f5:
|
||||||
|
65:38:b2:38:38:03:3b:b6
|
||||||
81
MagiskOnWSA/cacerts/39698488.0
Normal file
81
MagiskOnWSA/cacerts/39698488.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIID2TCCAsGgAwIBAgIJANyOw2Zo67cgMA0GCSqGSIb3DQEBCwUAMIGCMQswCQYD
|
||||||
|
VQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIwEAYDVQQHDAlKZXJ1c2FsZW0xEDAO
|
||||||
|
BgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5ldGZyZWUubGluazElMCMGA1UEAwwc
|
||||||
|
TmV0RnJlZSBTaWduLCBLU0lNIC0gUGFydG5lcjAeFw0xODA0MjYwODIwNTlaFw0y
|
||||||
|
ODAzMDQwODIwNTlaMIGCMQswCQYDVQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIw
|
||||||
|
EAYDVQQHDAlKZXJ1c2FsZW0xEDAOBgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5l
|
||||||
|
dGZyZWUubGluazElMCMGA1UEAwwcTmV0RnJlZSBTaWduLCBLU0lNIC0gUGFydG5l
|
||||||
|
cjCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAPHMntK9YDmWRrtYegwY
|
||||||
|
K4wXPFegP0yyh+ULK2E2aDQkm3Qf8esdYLB032f6BtjSP9OkBALCYa2hgBhxLN/B
|
||||||
|
ozQeSSaZrol8Jw9eB/D8H0j4uGxvqQWCo1jqczIzWcIMOYz7DVbtWcf9Bnh6nAm4
|
||||||
|
fumR6rkR9lgJb6PRcEzgcAp7T/dMm5C70X8jmS42Q1LNBtah2LDx4tPP/PLNDJMA
|
||||||
|
usTJMvub9ttTdSUViHFtryoPpi9Xf8v0UXnHCLN1SouWQfuzwARwcMxMtKlewOiB
|
||||||
|
rHTlFGEDtgMk4iXs3gw47J5HYI0s7GrKA0OQ8i3/kozFdvdl1Fb5pqA+GOGHw0JH
|
||||||
|
x7UCAwEAAaNQME4wHQYDVR0OBBYEFEWCRa1+fLj2mN6Z1YDbIscBUIWrMB8GA1Ud
|
||||||
|
IwQYMBaAFEWCRa1+fLj2mN6Z1YDbIscBUIWrMAwGA1UdEwQFMAMBAf8wDQYJKoZI
|
||||||
|
hvcNAQELBQADggEBALLit1Nn8DsZhzVvp3LaWkM6B/cwj/J4PRieAnlXOieblANa
|
||||||
|
Zk2IHgICyVhau6m9OJVPzja83EthGUkB2Mu0hPYQSbL29n8vMYpz5UmoqYpn78Cb
|
||||||
|
lH0RLGSNTcMiz/5vDyRllbFZQM1FIikO9Pyjp4WjAGeHzgpZqNY1YDjBlQnGcJiC
|
||||||
|
pdMCO/KJCXNHDSpZMI0oFNpanURQdNIB30QmWwOdCodAiXK8NBZ6HXrvxo8VkOKg
|
||||||
|
7P9T6IHq3vpRZ9wpDXYCqDvfdQRurfeTSFl/7U3NB8IxkcTCncQvV+Ry8PY23rZ9
|
||||||
|
wpypjLV/3V23/aanygRRmeyGVHbSh9eSfiMBIHc=
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
dc:8e:c3:66:68:eb:b7:20
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, KSIM - Partner"
|
||||||
|
Validity
|
||||||
|
Not Before: Apr 26 08:20:59 2018 GMT
|
||||||
|
Not After : Mar 4 08:20:59 2028 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, KSIM - Partner"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:f1:cc:9e:d2:bd:60:39:96:46:bb:58:7a:0c:18:
|
||||||
|
2b:8c:17:3c:57:a0:3f:4c:b2:87:e5:0b:2b:61:36:
|
||||||
|
68:34:24:9b:74:1f:f1:eb:1d:60:b0:74:df:67:fa:
|
||||||
|
06:d8:d2:3f:d3:a4:04:02:c2:61:ad:a1:80:18:71:
|
||||||
|
2c:df:c1:a3:34:1e:49:26:99:ae:89:7c:27:0f:5e:
|
||||||
|
07:f0:fc:1f:48:f8:b8:6c:6f:a9:05:82:a3:58:ea:
|
||||||
|
73:32:33:59:c2:0c:39:8c:fb:0d:56:ed:59:c7:fd:
|
||||||
|
06:78:7a:9c:09:b8:7e:e9:91:ea:b9:11:f6:58:09:
|
||||||
|
6f:a3:d1:70:4c:e0:70:0a:7b:4f:f7:4c:9b:90:bb:
|
||||||
|
d1:7f:23:99:2e:36:43:52:cd:06:d6:a1:d8:b0:f1:
|
||||||
|
e2:d3:cf:fc:f2:cd:0c:93:00:ba:c4:c9:32:fb:9b:
|
||||||
|
f6:db:53:75:25:15:88:71:6d:af:2a:0f:a6:2f:57:
|
||||||
|
7f:cb:f4:51:79:c7:08:b3:75:4a:8b:96:41:fb:b3:
|
||||||
|
c0:04:70:70:cc:4c:b4:a9:5e:c0:e8:81:ac:74:e5:
|
||||||
|
14:61:03:b6:03:24:e2:25:ec:de:0c:38:ec:9e:47:
|
||||||
|
60:8d:2c:ec:6a:ca:03:43:90:f2:2d:ff:92:8c:c5:
|
||||||
|
76:f7:65:d4:56:f9:a6:a0:3e:18:e1:87:c3:42:47:
|
||||||
|
c7:b5
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
45:82:45:AD:7E:7C:B8:F6:98:DE:99:D5:80:DB:22:C7:01:50:85:AB
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:45:82:45:AD:7E:7C:B8:F6:98:DE:99:D5:80:DB:22:C7:01:50:85:AB
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
b2:e2:b7:53:67:f0:3b:19:87:35:6f:a7:72:da:5a:43:3a:07:
|
||||||
|
f7:30:8f:f2:78:3d:18:9e:02:79:57:3a:27:9b:94:03:5a:66:
|
||||||
|
4d:88:1e:02:02:c9:58:5a:bb:a9:bd:38:95:4f:ce:36:bc:dc:
|
||||||
|
4b:61:19:49:01:d8:cb:b4:84:f6:10:49:b2:f6:f6:7f:2f:31:
|
||||||
|
8a:73:e5:49:a8:a9:8a:67:ef:c0:9b:94:7d:11:2c:64:8d:4d:
|
||||||
|
c3:22:cf:fe:6f:0f:24:65:95:b1:59:40:cd:45:22:29:0e:f4:
|
||||||
|
fc:a3:a7:85:a3:00:67:87:ce:0a:59:a8:d6:35:60:38:c1:95:
|
||||||
|
09:c6:70:98:82:a5:d3:02:3b:f2:89:09:73:47:0d:2a:59:30:
|
||||||
|
8d:28:14:da:5a:9d:44:50:74:d2:01:df:44:26:5b:03:9d:0a:
|
||||||
|
87:40:89:72:bc:34:16:7a:1d:7a:ef:c6:8f:15:90:e2:a0:ec:
|
||||||
|
ff:53:e8:81:ea:de:fa:51:67:dc:29:0d:76:02:a8:3b:df:75:
|
||||||
|
04:6e:ad:f7:93:48:59:7f:ed:4d:cd:07:c2:31:91:c4:c2:9d:
|
||||||
|
c4:2f:57:e4:72:f0:f6:36:de:b6:7d:c2:9c:a9:8c:b5:7f:dd:
|
||||||
|
5d:b7:fd:a6:a7:ca:04:51:99:ec:86:54:76:d2:87:d7:92:7e:
|
||||||
|
23:01:20:77
|
||||||
123
MagiskOnWSA/cacerts/3f66ddee.0
Normal file
123
MagiskOnWSA/cacerts/3f66ddee.0
Normal file
@ -0,0 +1,123 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIFzzCCA7egAwIBAgIUEwVOrPcQ9DVIGMi4qkZrs70iQnowDQYJKoZIhvcNAQEL
|
||||||
|
BQAwdzELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAGA1UEBwwJSmVy
|
||||||
|
dXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRmcmVlLmxpbmsx
|
||||||
|
GjAYBgNVBAMMEU5ldEZyZWUgU2lnbiwgSVRDMB4XDTIxMDQxNDE3NTE1M1oXDTMx
|
||||||
|
MDQxMjE3NTE1M1owdzELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAG
|
||||||
|
A1UEBwwJSmVydXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRm
|
||||||
|
cmVlLmxpbmsxGjAYBgNVBAMMEU5ldEZyZWUgU2lnbiwgSVRDMIICIjANBgkqhkiG
|
||||||
|
9w0BAQEFAAOCAg8AMIICCgKCAgEAwncsxkaH7L3LnDC3P6gVbqwWc5ieLHnKtgk8
|
||||||
|
AHsHQVuzFbKJikfA5FFdZQoCslPBR83pwzTi2wrnFKzApDdLBrB8NgbAzhimQ0gd
|
||||||
|
miRe4GdC8/W5WDu97+JnI+AGFGrbJxCzBfxc7hYC/0gTp9y8jWO9241OxuhYjlUf
|
||||||
|
7fXHqIlXKlz+h/0PPhop82yv5AeMolyGaQ5LnyuDCGZsS1VG+KiMhxQO9rB5pUAr
|
||||||
|
qHwAJ3UzGqXoMphSyoBYpvNG4R6MGOTvDgSVOZ8CJRbI4Y4/2XRpmXKC4EsKObR5
|
||||||
|
OVqm+iCSxX23DCWg/RBEClB6CAadkEFWXtOATtiCP/pPEGywOxFU82ENV/2MEm/w
|
||||||
|
/HMTLoBiKA8lnq8z1KcPzZ1w8oZk/N+Y/wibuPz+qQJPIW5OiXvNcq2QiVck843v
|
||||||
|
nZjEEd5GEx5FHAiPe71QBKq55Teb4G2/PeO5v26tUc9z1Nl7AQS7equ/XW3Xe5IT
|
||||||
|
+HP+VIq/x0hN9fpAbOwL7vnIZO4oMWR5wVXqo8B2vCd+XtHQXeYldzaggTtc026Q
|
||||||
|
cm/YHaIrexShAWKmfU5MfrGTOrfEgi11aJQTNDZzlR3eodMCkRJmV1wm8LjuJSyz
|
||||||
|
CVas2kLCAQ0LoT4c1Vp8SC2/5FGZNQ9SHhiqzDESNt9efqr4CF7/1MgTGXASunoH
|
||||||
|
UBp3KccCAwEAAaNTMFEwHQYDVR0OBBYEFN7AZUcFTTIew+Sve7rVPacztLA/MB8G
|
||||||
|
A1UdIwQYMBaAFN7AZUcFTTIew+Sve7rVPacztLA/MA8GA1UdEwEB/wQFMAMBAf8w
|
||||||
|
DQYJKoZIhvcNAQELBQADggIBAKf+3/4Adi0mslhs8N/JONbRaord4GBpqRtQ9OXV
|
||||||
|
pgyF7f7S/rBFnTcBbyqCSu0EitrDIAZ81rmJ8Cx0ae827v0fkRKwmtIl/G0QgUzd
|
||||||
|
4uVPe3UuALBjqedhVrfnNGZQvb1jbeTJ9R1u7V95au32fZk+1gHc69eA2NZgQ2kk
|
||||||
|
sazKnC8Urca3CgmVuuE8EeYcChRCWQ8qiCVKicm9g0tfwdLGIJMsQJPi7lXBmdlI
|
||||||
|
Gex5ADiNk3G5dIKVt3BqG9KYXBN9mw6RK7LIMGPJR20ydRy5vxPazKQXHaVWnvfU
|
||||||
|
4Gg7xgjNygMFYuflt6kPfek3HdIo5CASLwzz86dhwqdp0Wun8KMx3wfXu9IArL2p
|
||||||
|
AkT7z1d3zZWiaaXZ+JSUNcmC8560PVUE3Ygdkpi5AKBkLizmKt7ZuSU4LZvlcl7x
|
||||||
|
kvu2ZoAFyXh6LOL+UduLCzXVpCKh9rz1cnRkcqbkfdk3pSs+Z6HXT4aZriRqRNR4
|
||||||
|
0zaIjLLR93s7rlohRmXUu7uxG0wk6K88H4f8n6IHgZHZCeizY2s7rW6ZMsjuHM4T
|
||||||
|
8PrEdYR68VKJ4kSpBRyTxlUT4CZzfRaaViEhN52JSSxXUcfpOphO1tDavyeUAR8r
|
||||||
|
1+Prire6Y6/A0U5mr9gssB2HtBw69FUC6O//foeoc9JLO08dCuDznHs+UtH06hws
|
||||||
|
NA54
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
13:05:4e:ac:f7:10:f4:35:48:18:c8:b8:aa:46:6b:b3:bd:22:42:7a
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, ITC"
|
||||||
|
Validity
|
||||||
|
Not Before: Apr 14 17:51:53 2021 GMT
|
||||||
|
Not After : Apr 12 17:51:53 2031 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, ITC"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:c2:77:2c:c6:46:87:ec:bd:cb:9c:30:b7:3f:a8:
|
||||||
|
15:6e:ac:16:73:98:9e:2c:79:ca:b6:09:3c:00:7b:
|
||||||
|
07:41:5b:b3:15:b2:89:8a:47:c0:e4:51:5d:65:0a:
|
||||||
|
02:b2:53:c1:47:cd:e9:c3:34:e2:db:0a:e7:14:ac:
|
||||||
|
c0:a4:37:4b:06:b0:7c:36:06:c0:ce:18:a6:43:48:
|
||||||
|
1d:9a:24:5e:e0:67:42:f3:f5:b9:58:3b:bd:ef:e2:
|
||||||
|
67:23:e0:06:14:6a:db:27:10:b3:05:fc:5c:ee:16:
|
||||||
|
02:ff:48:13:a7:dc:bc:8d:63:bd:db:8d:4e:c6:e8:
|
||||||
|
58:8e:55:1f:ed:f5:c7:a8:89:57:2a:5c:fe:87:fd:
|
||||||
|
0f:3e:1a:29:f3:6c:af:e4:07:8c:a2:5c:86:69:0e:
|
||||||
|
4b:9f:2b:83:08:66:6c:4b:55:46:f8:a8:8c:87:14:
|
||||||
|
0e:f6:b0:79:a5:40:2b:a8:7c:00:27:75:33:1a:a5:
|
||||||
|
e8:32:98:52:ca:80:58:a6:f3:46:e1:1e:8c:18:e4:
|
||||||
|
ef:0e:04:95:39:9f:02:25:16:c8:e1:8e:3f:d9:74:
|
||||||
|
69:99:72:82:e0:4b:0a:39:b4:79:39:5a:a6:fa:20:
|
||||||
|
92:c5:7d:b7:0c:25:a0:fd:10:44:0a:50:7a:08:06:
|
||||||
|
9d:90:41:56:5e:d3:80:4e:d8:82:3f:fa:4f:10:6c:
|
||||||
|
b0:3b:11:54:f3:61:0d:57:fd:8c:12:6f:f0:fc:73:
|
||||||
|
13:2e:80:62:28:0f:25:9e:af:33:d4:a7:0f:cd:9d:
|
||||||
|
70:f2:86:64:fc:df:98:ff:08:9b:b8:fc:fe:a9:02:
|
||||||
|
4f:21:6e:4e:89:7b:cd:72:ad:90:89:57:24:f3:8d:
|
||||||
|
ef:9d:98:c4:11:de:46:13:1e:45:1c:08:8f:7b:bd:
|
||||||
|
50:04:aa:b9:e5:37:9b:e0:6d:bf:3d:e3:b9:bf:6e:
|
||||||
|
ad:51:cf:73:d4:d9:7b:01:04:bb:7a:ab:bf:5d:6d:
|
||||||
|
d7:7b:92:13:f8:73:fe:54:8a:bf:c7:48:4d:f5:fa:
|
||||||
|
40:6c:ec:0b:ee:f9:c8:64:ee:28:31:64:79:c1:55:
|
||||||
|
ea:a3:c0:76:bc:27:7e:5e:d1:d0:5d:e6:25:77:36:
|
||||||
|
a0:81:3b:5c:d3:6e:90:72:6f:d8:1d:a2:2b:7b:14:
|
||||||
|
a1:01:62:a6:7d:4e:4c:7e:b1:93:3a:b7:c4:82:2d:
|
||||||
|
75:68:94:13:34:36:73:95:1d:de:a1:d3:02:91:12:
|
||||||
|
66:57:5c:26:f0:b8:ee:25:2c:b3:09:56:ac:da:42:
|
||||||
|
c2:01:0d:0b:a1:3e:1c:d5:5a:7c:48:2d:bf:e4:51:
|
||||||
|
99:35:0f:52:1e:18:aa:cc:31:12:36:df:5e:7e:aa:
|
||||||
|
f8:08:5e:ff:d4:c8:13:19:70:12:ba:7a:07:50:1a:
|
||||||
|
77:29:c7
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
DE:C0:65:47:05:4D:32:1E:C3:E4:AF:7B:BA:D5:3D:A7:33:B4:B0:3F
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:DE:C0:65:47:05:4D:32:1E:C3:E4:AF:7B:BA:D5:3D:A7:33:B4:B0:3F
|
||||||
|
|
||||||
|
X509v3 Basic Constraints: critical
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
a7:fe:df:fe:00:76:2d:26:b2:58:6c:f0:df:c9:38:d6:d1:6a:
|
||||||
|
8a:dd:e0:60:69:a9:1b:50:f4:e5:d5:a6:0c:85:ed:fe:d2:fe:
|
||||||
|
b0:45:9d:37:01:6f:2a:82:4a:ed:04:8a:da:c3:20:06:7c:d6:
|
||||||
|
b9:89:f0:2c:74:69:ef:36:ee:fd:1f:91:12:b0:9a:d2:25:fc:
|
||||||
|
6d:10:81:4c:dd:e2:e5:4f:7b:75:2e:00:b0:63:a9:e7:61:56:
|
||||||
|
b7:e7:34:66:50:bd:bd:63:6d:e4:c9:f5:1d:6e:ed:5f:79:6a:
|
||||||
|
ed:f6:7d:99:3e:d6:01:dc:eb:d7:80:d8:d6:60:43:69:24:b1:
|
||||||
|
ac:ca:9c:2f:14:ad:c6:b7:0a:09:95:ba:e1:3c:11:e6:1c:0a:
|
||||||
|
14:42:59:0f:2a:88:25:4a:89:c9:bd:83:4b:5f:c1:d2:c6:20:
|
||||||
|
93:2c:40:93:e2:ee:55:c1:99:d9:48:19:ec:79:00:38:8d:93:
|
||||||
|
71:b9:74:82:95:b7:70:6a:1b:d2:98:5c:13:7d:9b:0e:91:2b:
|
||||||
|
b2:c8:30:63:c9:47:6d:32:75:1c:b9:bf:13:da:cc:a4:17:1d:
|
||||||
|
a5:56:9e:f7:d4:e0:68:3b:c6:08:cd:ca:03:05:62:e7:e5:b7:
|
||||||
|
a9:0f:7d:e9:37:1d:d2:28:e4:20:12:2f:0c:f3:f3:a7:61:c2:
|
||||||
|
a7:69:d1:6b:a7:f0:a3:31:df:07:d7:bb:d2:00:ac:bd:a9:02:
|
||||||
|
44:fb:cf:57:77:cd:95:a2:69:a5:d9:f8:94:94:35:c9:82:f3:
|
||||||
|
9e:b4:3d:55:04:dd:88:1d:92:98:b9:00:a0:64:2e:2c:e6:2a:
|
||||||
|
de:d9:b9:25:38:2d:9b:e5:72:5e:f1:92:fb:b6:66:80:05:c9:
|
||||||
|
78:7a:2c:e2:fe:51:db:8b:0b:35:d5:a4:22:a1:f6:bc:f5:72:
|
||||||
|
74:64:72:a6:e4:7d:d9:37:a5:2b:3e:67:a1:d7:4f:86:99:ae:
|
||||||
|
24:6a:44:d4:78:d3:36:88:8c:b2:d1:f7:7b:3b:ae:5a:21:46:
|
||||||
|
65:d4:bb:bb:b1:1b:4c:24:e8:af:3c:1f:87:fc:9f:a2:07:81:
|
||||||
|
91:d9:09:e8:b3:63:6b:3b:ad:6e:99:32:c8:ee:1c:ce:13:f0:
|
||||||
|
fa:c4:75:84:7a:f1:52:89:e2:44:a9:05:1c:93:c6:55:13:e0:
|
||||||
|
26:73:7d:16:9a:56:21:21:37:9d:89:49:2c:57:51:c7:e9:3a:
|
||||||
|
98:4e:d6:d0:da:bf:27:94:01:1f:2b:d7:e3:eb:8a:b7:ba:63:
|
||||||
|
af:c0:d1:4e:66:af:d8:2c:b0:1d:87:b4:1c:3a:f4:55:02:e8:
|
||||||
|
ef:ff:7e:87:a8:73:d2:4b:3b:4f:1d:0a:e0:f3:9c:7b:3e:52:
|
||||||
|
d1:f4:ea:1c:2c:34:0e:78
|
||||||
122
MagiskOnWSA/cacerts/42afec87.0
Normal file
122
MagiskOnWSA/cacerts/42afec87.0
Normal file
@ -0,0 +1,122 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIFxzCCA6+gAwIBAgIJAMOfeHNsvnuxMA0GCSqGSIb3DQEBCwUAMHoxCzAJBgNV
|
||||||
|
BAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcMCUplcnVzYWxlbTEQMA4G
|
||||||
|
A1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0ZnJlZS5saW5rMR0wGwYDVQQDDBRO
|
||||||
|
ZXRGcmVlIFNpZ24gLElCLUlUQzAeFw0xOTEwMjYxOTEwMjNaFw0yOTA5MDMxOTEw
|
||||||
|
MjNaMHoxCzAJBgNVBAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcMCUpl
|
||||||
|
cnVzYWxlbTEQMA4GA1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0ZnJlZS5saW5r
|
||||||
|
MR0wGwYDVQQDDBROZXRGcmVlIFNpZ24gLElCLUlUQzCCAiIwDQYJKoZIhvcNAQEB
|
||||||
|
BQADggIPADCCAgoCggIBAPistDj0oOuF1Mtu2VyYOK+O/fhMHQIYg3ZG7HMxIPBp
|
||||||
|
dSpCeH+3Z6Qi1YSlDkd0sW7C3KqUt1gsJyf2HZLBrCEBBlFtCN/zCdIjo/pelR7q
|
||||||
|
+qXYr67y980GzZqnlYgGbS3PbthsXfayAQi1LsSR1UXdUg91WgJLFdMgIVsnSq5K
|
||||||
|
w8re1D+V9KfX1SnmH/WDfzb/ickxryyiieMQV+lNegDhsTqSaHuOowsFNgZkwsoo
|
||||||
|
c+DAuHfBFn+jWwZMFPDsiWSROsh4rcft172+I4ReR1Cr2JdHzueJQNx8mTcr5COM
|
||||||
|
e6Hl72K4Kot4G6ohL74GATs6fSP3kcy8UafDSnODAffixZt7S59K9hSqsMVJvTzS
|
||||||
|
T/pmhrQFS7xACj4TJa/f1t+5LYRe6FdwEcXeHNcfSVVRfPgLdiKFAD5ok3TFBXfO
|
||||||
|
fsAkpdhdfSSUOBWLuE/l+Ko56enic59JeewwbC322Ihvn+1PaloVINHQTlXJhCFD
|
||||||
|
CkoizPrm9AFlM2IK+qPN0GSckj2X6Eo/bxFmt6GXsZW8kzoDc4TlclLxoMJB+jJn
|
||||||
|
H1EH9+h1wWNR9kybBnrnKSGdlapD0OK42H/Ul44uLtNLKN3zpMvYWabSdThYTUqZ
|
||||||
|
pCg8tXyQj1z/3l12Ka7QIEqkqTHF35MTe0YrDLbKo4N8s1vlkfevcwHeerSI5ts1
|
||||||
|
AgMBAAGjUDBOMB0GA1UdDgQWBBSnCGbym3/xoGKcYFbwvP2yTjBbADAfBgNVHSME
|
||||||
|
GDAWgBSnCGbym3/xoGKcYFbwvP2yTjBbADAMBgNVHRMEBTADAQH/MA0GCSqGSIb3
|
||||||
|
DQEBCwUAA4ICAQCspY/ayI3Mwvp6nAWpBaLSw/YDWChYAG99prvgCSRYVgwRQGw5
|
||||||
|
oZnhYFSZM+Suh0cHKh3tU1nZDpgn/vvqOmf1IPHCI+ZOEY73YZmPlYD3JE2ZJDzO
|
||||||
|
QdJPwW/07W7XAjCIoLw27C/xJDRpBRCXpqfAfmw8qTrNEsozhX9pzJkCVr6UtYX5
|
||||||
|
X5LWY0oX9Y/OY8dGQeGqQNeAMwVyW0pmUs5lmVTzPP4mhWLmqF8MCPf8ULswBfr+
|
||||||
|
uWHNGG1u7RAwm8MP4hi1IgT8bVLQJjaLFRV/dUVHDs5dnF0ZnpNnvfoJxCbyMjcR
|
||||||
|
JWb4yR+31ZNrC+SZobtTcEOnzuaaL5AHGb6gZt0qGOVoykPM4dtlFH3jVrCdvOAA
|
||||||
|
0QCzjfu6o8Eb2HzdWKKm4Kxl9mlwznQrOCa3jmj6L9g/Y1tetYAnJwrgzZVvrNMV
|
||||||
|
5bLW1beBvb/Y99z3TNhjqgjv5gBeeN0cJ63k8P/ZuikuNuhCub2Lo8diYhaw2C6o
|
||||||
|
5hMg+q5U9FML//mXWsD6bHN68XPQEUf43O8BCOeIOyW1fDIX3y9RcwJf2lP4frkH
|
||||||
|
Eo9RaDUsLWdPVxPvgdVSZUiOxkKJ3CxSJaffrsccNTMcFx/ACzQqn6gxRHPuqK0Y
|
||||||
|
0Ka6pV5b03zWCT+G6qzidxHjKnwOhKV5r+5nYFzcvPpZijK/RmnSDjWuTQ==
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
c3:9f:78:73:6c:be:7b:b1
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign ,IB-ITC"
|
||||||
|
Validity
|
||||||
|
Not Before: Oct 26 19:10:23 2019 GMT
|
||||||
|
Not After : Sep 3 19:10:23 2029 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign ,IB-ITC"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:f8:ac:b4:38:f4:a0:eb:85:d4:cb:6e:d9:5c:98:
|
||||||
|
38:af:8e:fd:f8:4c:1d:02:18:83:76:46:ec:73:31:
|
||||||
|
20:f0:69:75:2a:42:78:7f:b7:67:a4:22:d5:84:a5:
|
||||||
|
0e:47:74:b1:6e:c2:dc:aa:94:b7:58:2c:27:27:f6:
|
||||||
|
1d:92:c1:ac:21:01:06:51:6d:08:df:f3:09:d2:23:
|
||||||
|
a3:fa:5e:95:1e:ea:fa:a5:d8:af:ae:f2:f7:cd:06:
|
||||||
|
cd:9a:a7:95:88:06:6d:2d:cf:6e:d8:6c:5d:f6:b2:
|
||||||
|
01:08:b5:2e:c4:91:d5:45:dd:52:0f:75:5a:02:4b:
|
||||||
|
15:d3:20:21:5b:27:4a:ae:4a:c3:ca:de:d4:3f:95:
|
||||||
|
f4:a7:d7:d5:29:e6:1f:f5:83:7f:36:ff:89:c9:31:
|
||||||
|
af:2c:a2:89:e3:10:57:e9:4d:7a:00:e1:b1:3a:92:
|
||||||
|
68:7b:8e:a3:0b:05:36:06:64:c2:ca:28:73:e0:c0:
|
||||||
|
b8:77:c1:16:7f:a3:5b:06:4c:14:f0:ec:89:64:91:
|
||||||
|
3a:c8:78:ad:c7:ed:d7:bd:be:23:84:5e:47:50:ab:
|
||||||
|
d8:97:47:ce:e7:89:40:dc:7c:99:37:2b:e4:23:8c:
|
||||||
|
7b:a1:e5:ef:62:b8:2a:8b:78:1b:aa:21:2f:be:06:
|
||||||
|
01:3b:3a:7d:23:f7:91:cc:bc:51:a7:c3:4a:73:83:
|
||||||
|
01:f7:e2:c5:9b:7b:4b:9f:4a:f6:14:aa:b0:c5:49:
|
||||||
|
bd:3c:d2:4f:fa:66:86:b4:05:4b:bc:40:0a:3e:13:
|
||||||
|
25:af:df:d6:df:b9:2d:84:5e:e8:57:70:11:c5:de:
|
||||||
|
1c:d7:1f:49:55:51:7c:f8:0b:76:22:85:00:3e:68:
|
||||||
|
93:74:c5:05:77:ce:7e:c0:24:a5:d8:5d:7d:24:94:
|
||||||
|
38:15:8b:b8:4f:e5:f8:aa:39:e9:e9:e2:73:9f:49:
|
||||||
|
79:ec:30:6c:2d:f6:d8:88:6f:9f:ed:4f:6a:5a:15:
|
||||||
|
20:d1:d0:4e:55:c9:84:21:43:0a:4a:22:cc:fa:e6:
|
||||||
|
f4:01:65:33:62:0a:fa:a3:cd:d0:64:9c:92:3d:97:
|
||||||
|
e8:4a:3f:6f:11:66:b7:a1:97:b1:95:bc:93:3a:03:
|
||||||
|
73:84:e5:72:52:f1:a0:c2:41:fa:32:67:1f:51:07:
|
||||||
|
f7:e8:75:c1:63:51:f6:4c:9b:06:7a:e7:29:21:9d:
|
||||||
|
95:aa:43:d0:e2:b8:d8:7f:d4:97:8e:2e:2e:d3:4b:
|
||||||
|
28:dd:f3:a4:cb:d8:59:a6:d2:75:38:58:4d:4a:99:
|
||||||
|
a4:28:3c:b5:7c:90:8f:5c:ff:de:5d:76:29:ae:d0:
|
||||||
|
20:4a:a4:a9:31:c5:df:93:13:7b:46:2b:0c:b6:ca:
|
||||||
|
a3:83:7c:b3:5b:e5:91:f7:af:73:01:de:7a:b4:88:
|
||||||
|
e6:db:35
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
A7:08:66:F2:9B:7F:F1:A0:62:9C:60:56:F0:BC:FD:B2:4E:30:5B:00
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:A7:08:66:F2:9B:7F:F1:A0:62:9C:60:56:F0:BC:FD:B2:4E:30:5B:00
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
ac:a5:8f:da:c8:8d:cc:c2:fa:7a:9c:05:a9:05:a2:d2:c3:f6:
|
||||||
|
03:58:28:58:00:6f:7d:a6:bb:e0:09:24:58:56:0c:11:40:6c:
|
||||||
|
39:a1:99:e1:60:54:99:33:e4:ae:87:47:07:2a:1d:ed:53:59:
|
||||||
|
d9:0e:98:27:fe:fb:ea:3a:67:f5:20:f1:c2:23:e6:4e:11:8e:
|
||||||
|
f7:61:99:8f:95:80:f7:24:4d:99:24:3c:ce:41:d2:4f:c1:6f:
|
||||||
|
f4:ed:6e:d7:02:30:88:a0:bc:36:ec:2f:f1:24:34:69:05:10:
|
||||||
|
97:a6:a7:c0:7e:6c:3c:a9:3a:cd:12:ca:33:85:7f:69:cc:99:
|
||||||
|
02:56:be:94:b5:85:f9:5f:92:d6:63:4a:17:f5:8f:ce:63:c7:
|
||||||
|
46:41:e1:aa:40:d7:80:33:05:72:5b:4a:66:52:ce:65:99:54:
|
||||||
|
f3:3c:fe:26:85:62:e6:a8:5f:0c:08:f7:fc:50:bb:30:05:fa:
|
||||||
|
fe:b9:61:cd:18:6d:6e:ed:10:30:9b:c3:0f:e2:18:b5:22:04:
|
||||||
|
fc:6d:52:d0:26:36:8b:15:15:7f:75:45:47:0e:ce:5d:9c:5d:
|
||||||
|
19:9e:93:67:bd:fa:09:c4:26:f2:32:37:11:25:66:f8:c9:1f:
|
||||||
|
b7:d5:93:6b:0b:e4:99:a1:bb:53:70:43:a7:ce:e6:9a:2f:90:
|
||||||
|
07:19:be:a0:66:dd:2a:18:e5:68:ca:43:cc:e1:db:65:14:7d:
|
||||||
|
e3:56:b0:9d:bc:e0:00:d1:00:b3:8d:fb:ba:a3:c1:1b:d8:7c:
|
||||||
|
dd:58:a2:a6:e0:ac:65:f6:69:70:ce:74:2b:38:26:b7:8e:68:
|
||||||
|
fa:2f:d8:3f:63:5b:5e:b5:80:27:27:0a:e0:cd:95:6f:ac:d3:
|
||||||
|
15:e5:b2:d6:d5:b7:81:bd:bf:d8:f7:dc:f7:4c:d8:63:aa:08:
|
||||||
|
ef:e6:00:5e:78:dd:1c:27:ad:e4:f0:ff:d9:ba:29:2e:36:e8:
|
||||||
|
42:b9:bd:8b:a3:c7:62:62:16:b0:d8:2e:a8:e6:13:20:fa:ae:
|
||||||
|
54:f4:53:0b:ff:f9:97:5a:c0:fa:6c:73:7a:f1:73:d0:11:47:
|
||||||
|
f8:dc:ef:01:08:e7:88:3b:25:b5:7c:32:17:df:2f:51:73:02:
|
||||||
|
5f:da:53:f8:7e:b9:07:12:8f:51:68:35:2c:2d:67:4f:57:13:
|
||||||
|
ef:81:d5:52:65:48:8e:c6:42:89:dc:2c:52:25:a7:df:ae:c7:
|
||||||
|
1c:35:33:1c:17:1f:c0:0b:34:2a:9f:a8:31:44:73:ee:a8:ad:
|
||||||
|
18:d0:a6:ba:a5:5e:5b:d3:7c:d6:09:3f:86:ea:ac:e2:77:11:
|
||||||
|
e3:2a:7c:0e:84:a5:79:af:ee:67:60:5c:dc:bc:fa:59:8a:32:
|
||||||
|
bf:46:69:d2:0e:35:ae:4d
|
||||||
81
MagiskOnWSA/cacerts/482e0622.0
Normal file
81
MagiskOnWSA/cacerts/482e0622.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIDwzCCAqugAwIBAgIJAJvSq+oh8F6+MA0GCSqGSIb3DQEBCwUAMHgxCzAJBgNV
|
||||||
|
BAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcMCUplcnVzYWxlbTEQMA4G
|
||||||
|
A1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0ZnJlZS5saW5rMRswGQYDVQQDDBJO
|
||||||
|
ZXRGcmVlIFNpZ24gLCAwMTkwHhcNMTYwNDIxMTAyNzA1WhcNMjYwMjI4MTAyNzA1
|
||||||
|
WjB4MQswCQYDVQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIwEAYDVQQHDAlKZXJ1
|
||||||
|
c2FsZW0xEDAOBgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5ldGZyZWUubGluazEb
|
||||||
|
MBkGA1UEAwwSTmV0RnJlZSBTaWduICwgMDE5MIIBIjANBgkqhkiG9w0BAQEFAAOC
|
||||||
|
AQ8AMIIBCgKCAQEA5Wq8zAqW7KGANXfbg9Ck8rx4nPjSkerlSPS/yNEVa/L8HulD
|
||||||
|
q/GVMRaPaL+RqI4GQt6LeQAmj1FZS01rQQITNRsg6MhNrPhENhg48rjFNIxuEnMv
|
||||||
|
IfydKGGU2mFXcMtQ9IoRSe4OYE3CKDG0pYzfXhh+TW0H4KKqjO6mjPmMcNjbstpK
|
||||||
|
vOPFg6Xu5em6hvtQCKC0V551WKWmNQiHOpwRdVIdbWBv3S5xiO5tZVigGpEJ1gLe
|
||||||
|
8W+Zn2ozcpvh+m38QSZ0A1DVP5Te/7q9L3+BPub8kz3C6GnNK547ucM5HBmOzNwN
|
||||||
|
luZHVUsehCLc0I965Wd4ZRUXXeeo7BibjRI6mQIDAQABo1AwTjAdBgNVHQ4EFgQU
|
||||||
|
tLpJD3JS6YPg7VQl2gKrPJByEycwHwYDVR0jBBgwFoAUtLpJD3JS6YPg7VQl2gKr
|
||||||
|
PJByEycwDAYDVR0TBAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAQEAThhIvkN/HsFG
|
||||||
|
7jaHl8yyH3IyvHX+LrItJyhRaQ4xALzGllGCLWvN15e2SWITdXncd4nMU7VRVG1k
|
||||||
|
CiX6H55Jh1U/DmZHmUI2HBhf/2liFNKXKDOeHg4u+FIzgzuIc0z+RvwPpw9IVLio
|
||||||
|
Pe6lbaIc5+80kO/mwJwQZoEaqTyL1Ujn69cosiZpiYF3xtxkfBWEWe7XkLunLqqV
|
||||||
|
DoMEGMq+MUxO+Jngv0j/7dSi1/1eovNnrV4YeF2Flvq2xY1aCKO/cocv5v7w5wEm
|
||||||
|
8fMFQwKcT7QcCx+/nkx3r0tDHxO7og7xr8petCK+ULqwL28ha4U0l+kLF0ZRiG5H
|
||||||
|
Ni6Hj6Oi9A==
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
9b:d2:ab:ea:21:f0:5e:be
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , 019"
|
||||||
|
Validity
|
||||||
|
Not Before: Apr 21 10:27:05 2016 GMT
|
||||||
|
Not After : Feb 28 10:27:05 2026 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , 019"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:e5:6a:bc:cc:0a:96:ec:a1:80:35:77:db:83:d0:
|
||||||
|
a4:f2:bc:78:9c:f8:d2:91:ea:e5:48:f4:bf:c8:d1:
|
||||||
|
15:6b:f2:fc:1e:e9:43:ab:f1:95:31:16:8f:68:bf:
|
||||||
|
91:a8:8e:06:42:de:8b:79:00:26:8f:51:59:4b:4d:
|
||||||
|
6b:41:02:13:35:1b:20:e8:c8:4d:ac:f8:44:36:18:
|
||||||
|
38:f2:b8:c5:34:8c:6e:12:73:2f:21:fc:9d:28:61:
|
||||||
|
94:da:61:57:70:cb:50:f4:8a:11:49:ee:0e:60:4d:
|
||||||
|
c2:28:31:b4:a5:8c:df:5e:18:7e:4d:6d:07:e0:a2:
|
||||||
|
aa:8c:ee:a6:8c:f9:8c:70:d8:db:b2:da:4a:bc:e3:
|
||||||
|
c5:83:a5:ee:e5:e9:ba:86:fb:50:08:a0:b4:57:9e:
|
||||||
|
75:58:a5:a6:35:08:87:3a:9c:11:75:52:1d:6d:60:
|
||||||
|
6f:dd:2e:71:88:ee:6d:65:58:a0:1a:91:09:d6:02:
|
||||||
|
de:f1:6f:99:9f:6a:33:72:9b:e1:fa:6d:fc:41:26:
|
||||||
|
74:03:50:d5:3f:94:de:ff:ba:bd:2f:7f:81:3e:e6:
|
||||||
|
fc:93:3d:c2:e8:69:cd:2b:9e:3b:b9:c3:39:1c:19:
|
||||||
|
8e:cc:dc:0d:96:e6:47:55:4b:1e:84:22:dc:d0:8f:
|
||||||
|
7a:e5:67:78:65:15:17:5d:e7:a8:ec:18:9b:8d:12:
|
||||||
|
3a:99
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
B4:BA:49:0F:72:52:E9:83:E0:ED:54:25:DA:02:AB:3C:90:72:13:27
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:B4:BA:49:0F:72:52:E9:83:E0:ED:54:25:DA:02:AB:3C:90:72:13:27
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
4e:18:48:be:43:7f:1e:c1:46:ee:36:87:97:cc:b2:1f:72:32:
|
||||||
|
bc:75:fe:2e:b2:2d:27:28:51:69:0e:31:00:bc:c6:96:51:82:
|
||||||
|
2d:6b:cd:d7:97:b6:49:62:13:75:79:dc:77:89:cc:53:b5:51:
|
||||||
|
54:6d:64:0a:25:fa:1f:9e:49:87:55:3f:0e:66:47:99:42:36:
|
||||||
|
1c:18:5f:ff:69:62:14:d2:97:28:33:9e:1e:0e:2e:f8:52:33:
|
||||||
|
83:3b:88:73:4c:fe:46:fc:0f:a7:0f:48:54:b8:a8:3d:ee:a5:
|
||||||
|
6d:a2:1c:e7:ef:34:90:ef:e6:c0:9c:10:66:81:1a:a9:3c:8b:
|
||||||
|
d5:48:e7:eb:d7:28:b2:26:69:89:81:77:c6:dc:64:7c:15:84:
|
||||||
|
59:ee:d7:90:bb:a7:2e:aa:95:0e:83:04:18:ca:be:31:4c:4e:
|
||||||
|
f8:99:e0:bf:48:ff:ed:d4:a2:d7:fd:5e:a2:f3:67:ad:5e:18:
|
||||||
|
78:5d:85:96:fa:b6:c5:8d:5a:08:a3:bf:72:87:2f:e6:fe:f0:
|
||||||
|
e7:01:26:f1:f3:05:43:02:9c:4f:b4:1c:0b:1f:bf:9e:4c:77:
|
||||||
|
af:4b:43:1f:13:bb:a2:0e:f1:af:ca:5e:b4:22:be:50:ba:b0:
|
||||||
|
2f:6f:21:6b:85:34:97:e9:0b:17:46:51:88:6e:47:36:2e:87:
|
||||||
|
8f:a3:a2:f4
|
||||||
123
MagiskOnWSA/cacerts/4a3b190e.0
Normal file
123
MagiskOnWSA/cacerts/4a3b190e.0
Normal file
@ -0,0 +1,123 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIFzzCCA7egAwIBAgIUWVzvad617aEkkFZ5UDDiq93NTVkwDQYJKoZIhvcNAQEL
|
||||||
|
BQAwdzELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAGA1UEBwwJSmVy
|
||||||
|
dXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRmcmVlLmxpbmsx
|
||||||
|
GjAYBgNVBAMMEU5ldEZyZWUgU2lnbiwgMDk5MB4XDTIxMDQwNzIyMTQ0NFoXDTMx
|
||||||
|
MDQwNTIyMTQ0NFowdzELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAG
|
||||||
|
A1UEBwwJSmVydXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRm
|
||||||
|
cmVlLmxpbmsxGjAYBgNVBAMMEU5ldEZyZWUgU2lnbiwgMDk5MIICIjANBgkqhkiG
|
||||||
|
9w0BAQEFAAOCAg8AMIICCgKCAgEAsnHF+C8rBiEzeZJ88nKVAZEh6SwSrNwoRNLV
|
||||||
|
gr69fj9mU7Tpgu8dRP+1q4MaZDTdXw+pqbvo/R9Jzc/YCN1BvrvL5ULCfNOwoCFa
|
||||||
|
MyLhNQ/zXMwfWiCeWr5qJ0rdpyWrGvXrurYIcbwzgAxpQA5krBUyZI/QJIjWi6PG
|
||||||
|
FZya7YrvzcvEG3Mbzl+E/G12FDuT5NVuNQIBE+mR9ZOFPrZsEDJb7SoZoIic7p1k
|
||||||
|
mrHwPMv3w07QIHOwFq9e8t/c7cFMEqOUC2/+Uw73J2MdYLX5vyTDtChAM0h5M00F
|
||||||
|
14tO7t46ofZ+GHj8w0kNoFk5Z1eNIXMasbs77fCN6LYHN1seuKvDh0p4ZdDLdObo
|
||||||
|
Y2XT8n+I7O2tY5PIaNoWDuQpKwUplY0WQFca7iKyy8ajojJPOMt40SaR7NtBvwl3
|
||||||
|
fYRPHvX57tQB55vpcTq7uVdaeEq3/G19wRVgDLs/MIFaPTV31RyOsrUzIc944aN8
|
||||||
|
YDBG4Mw6uUyVG3wxq9/QgZliW+wNj77gSMFZsj7aA0FqaDpQ4hdoGoehKP+B6y10
|
||||||
|
ZVOqe/sgPnZBW/KW+3uwOP/Bq809Q+G/JUQR23bhqCYht7zbi+f5pOmKXijAjnMh
|
||||||
|
Bs7fnxzc0YMNHYQ3RF9VNiteC8/+8rMgXIjq94cF8vAkm/kHT4qyNIzLVu/oUkrp
|
||||||
|
UYFd0YMCAwEAAaNTMFEwHQYDVR0OBBYEFHpftzbYdX1vM6czqDzA2ABKkMMzMB8G
|
||||||
|
A1UdIwQYMBaAFHpftzbYdX1vM6czqDzA2ABKkMMzMA8GA1UdEwEB/wQFMAMBAf8w
|
||||||
|
DQYJKoZIhvcNAQELBQADggIBACntHyKEjJaGqezp/SYdmvC6Gw0HVEahudZJTlM8
|
||||||
|
uWDCINdJFSSRMnAHC57qeKU+4AuN2ZO0BnRyVSK1XY0rlS0ZeNidRg2g1PgplJ3I
|
||||||
|
4KPKiq0LxllnPtSJiuNp81LazUj5iyqsHCPDE0pZVu1729kTfL2a2Ah3yaB5LxiX
|
||||||
|
6xMuZurI3LscOcfrN3oUH0lvlvt4hjmpi90UJ/Wtd+fllyw1sqInQfv87MOkoFzy
|
||||||
|
u9Rif2ZiBwMw32K9X7q/w7/iw77G1F9u/gbogP7CgDkKCxeyl5rLwkJKgV0g93xg
|
||||||
|
bonHdOmKlHYLMBuEx1CYdvAZcEwPdeiNuKbj1l8iJ4+PeYD2hRo+NmL/8Kjj3XTr
|
||||||
|
Xymah0bNsJFYda7W4plL6DzjvrMjwkLq1IeLDZLvL0iNk0wfe3GY7ojvqcY55XEo
|
||||||
|
TdEHiKqck8uTxzH/U5AGh26nbOxAe6AYNmbgmiJxWZXqYeqEmTx9B6Zk61RdFTem
|
||||||
|
gml5hqvUjM97JmSi/ORF31uP6+Jv35oQEo4YjeDD6ACDiDBjfyjPVMGVAxf6IRSt
|
||||||
|
s9O6OoYKZO09gaRuHXLSY9kfXSGsrV5mqbFr0r2C8n+u8kGjkILaCabil7cMBUfz
|
||||||
|
x95VUUI9AUunwF2ERMuTgfR1CE4gDJcUTU7Wf1o3xEpvCgQ6ffYzBXkHjeOTaZkI
|
||||||
|
zlA/
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
59:5c:ef:69:de:b5:ed:a1:24:90:56:79:50:30:e2:ab:dd:cd:4d:59
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, 099"
|
||||||
|
Validity
|
||||||
|
Not Before: Apr 7 22:14:44 2021 GMT
|
||||||
|
Not After : Apr 5 22:14:44 2031 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, 099"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:b2:71:c5:f8:2f:2b:06:21:33:79:92:7c:f2:72:
|
||||||
|
95:01:91:21:e9:2c:12:ac:dc:28:44:d2:d5:82:be:
|
||||||
|
bd:7e:3f:66:53:b4:e9:82:ef:1d:44:ff:b5:ab:83:
|
||||||
|
1a:64:34:dd:5f:0f:a9:a9:bb:e8:fd:1f:49:cd:cf:
|
||||||
|
d8:08:dd:41:be:bb:cb:e5:42:c2:7c:d3:b0:a0:21:
|
||||||
|
5a:33:22:e1:35:0f:f3:5c:cc:1f:5a:20:9e:5a:be:
|
||||||
|
6a:27:4a:dd:a7:25:ab:1a:f5:eb:ba:b6:08:71:bc:
|
||||||
|
33:80:0c:69:40:0e:64:ac:15:32:64:8f:d0:24:88:
|
||||||
|
d6:8b:a3:c6:15:9c:9a:ed:8a:ef:cd:cb:c4:1b:73:
|
||||||
|
1b:ce:5f:84:fc:6d:76:14:3b:93:e4:d5:6e:35:02:
|
||||||
|
01:13:e9:91:f5:93:85:3e:b6:6c:10:32:5b:ed:2a:
|
||||||
|
19:a0:88:9c:ee:9d:64:9a:b1:f0:3c:cb:f7:c3:4e:
|
||||||
|
d0:20:73:b0:16:af:5e:f2:df:dc:ed:c1:4c:12:a3:
|
||||||
|
94:0b:6f:fe:53:0e:f7:27:63:1d:60:b5:f9:bf:24:
|
||||||
|
c3:b4:28:40:33:48:79:33:4d:05:d7:8b:4e:ee:de:
|
||||||
|
3a:a1:f6:7e:18:78:fc:c3:49:0d:a0:59:39:67:57:
|
||||||
|
8d:21:73:1a:b1:bb:3b:ed:f0:8d:e8:b6:07:37:5b:
|
||||||
|
1e:b8:ab:c3:87:4a:78:65:d0:cb:74:e6:e8:63:65:
|
||||||
|
d3:f2:7f:88:ec:ed:ad:63:93:c8:68:da:16:0e:e4:
|
||||||
|
29:2b:05:29:95:8d:16:40:57:1a:ee:22:b2:cb:c6:
|
||||||
|
a3:a2:32:4f:38:cb:78:d1:26:91:ec:db:41:bf:09:
|
||||||
|
77:7d:84:4f:1e:f5:f9:ee:d4:01:e7:9b:e9:71:3a:
|
||||||
|
bb:b9:57:5a:78:4a:b7:fc:6d:7d:c1:15:60:0c:bb:
|
||||||
|
3f:30:81:5a:3d:35:77:d5:1c:8e:b2:b5:33:21:cf:
|
||||||
|
78:e1:a3:7c:60:30:46:e0:cc:3a:b9:4c:95:1b:7c:
|
||||||
|
31:ab:df:d0:81:99:62:5b:ec:0d:8f:be:e0:48:c1:
|
||||||
|
59:b2:3e:da:03:41:6a:68:3a:50:e2:17:68:1a:87:
|
||||||
|
a1:28:ff:81:eb:2d:74:65:53:aa:7b:fb:20:3e:76:
|
||||||
|
41:5b:f2:96:fb:7b:b0:38:ff:c1:ab:cd:3d:43:e1:
|
||||||
|
bf:25:44:11:db:76:e1:a8:26:21:b7:bc:db:8b:e7:
|
||||||
|
f9:a4:e9:8a:5e:28:c0:8e:73:21:06:ce:df:9f:1c:
|
||||||
|
dc:d1:83:0d:1d:84:37:44:5f:55:36:2b:5e:0b:cf:
|
||||||
|
fe:f2:b3:20:5c:88:ea:f7:87:05:f2:f0:24:9b:f9:
|
||||||
|
07:4f:8a:b2:34:8c:cb:56:ef:e8:52:4a:e9:51:81:
|
||||||
|
5d:d1:83
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
7A:5F:B7:36:D8:75:7D:6F:33:A7:33:A8:3C:C0:D8:00:4A:90:C3:33
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:7A:5F:B7:36:D8:75:7D:6F:33:A7:33:A8:3C:C0:D8:00:4A:90:C3:33
|
||||||
|
|
||||||
|
X509v3 Basic Constraints: critical
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
29:ed:1f:22:84:8c:96:86:a9:ec:e9:fd:26:1d:9a:f0:ba:1b:
|
||||||
|
0d:07:54:46:a1:b9:d6:49:4e:53:3c:b9:60:c2:20:d7:49:15:
|
||||||
|
24:91:32:70:07:0b:9e:ea:78:a5:3e:e0:0b:8d:d9:93:b4:06:
|
||||||
|
74:72:55:22:b5:5d:8d:2b:95:2d:19:78:d8:9d:46:0d:a0:d4:
|
||||||
|
f8:29:94:9d:c8:e0:a3:ca:8a:ad:0b:c6:59:67:3e:d4:89:8a:
|
||||||
|
e3:69:f3:52:da:cd:48:f9:8b:2a:ac:1c:23:c3:13:4a:59:56:
|
||||||
|
ed:7b:db:d9:13:7c:bd:9a:d8:08:77:c9:a0:79:2f:18:97:eb:
|
||||||
|
13:2e:66:ea:c8:dc:bb:1c:39:c7:eb:37:7a:14:1f:49:6f:96:
|
||||||
|
fb:78:86:39:a9:8b:dd:14:27:f5:ad:77:e7:e5:97:2c:35:b2:
|
||||||
|
a2:27:41:fb:fc:ec:c3:a4:a0:5c:f2:bb:d4:62:7f:66:62:07:
|
||||||
|
03:30:df:62:bd:5f:ba:bf:c3:bf:e2:c3:be:c6:d4:5f:6e:fe:
|
||||||
|
06:e8:80:fe:c2:80:39:0a:0b:17:b2:97:9a:cb:c2:42:4a:81:
|
||||||
|
5d:20:f7:7c:60:6e:89:c7:74:e9:8a:94:76:0b:30:1b:84:c7:
|
||||||
|
50:98:76:f0:19:70:4c:0f:75:e8:8d:b8:a6:e3:d6:5f:22:27:
|
||||||
|
8f:8f:79:80:f6:85:1a:3e:36:62:ff:f0:a8:e3:dd:74:eb:5f:
|
||||||
|
29:9a:87:46:cd:b0:91:58:75:ae:d6:e2:99:4b:e8:3c:e3:be:
|
||||||
|
b3:23:c2:42:ea:d4:87:8b:0d:92:ef:2f:48:8d:93:4c:1f:7b:
|
||||||
|
71:98:ee:88:ef:a9:c6:39:e5:71:28:4d:d1:07:88:aa:9c:93:
|
||||||
|
cb:93:c7:31:ff:53:90:06:87:6e:a7:6c:ec:40:7b:a0:18:36:
|
||||||
|
66:e0:9a:22:71:59:95:ea:61:ea:84:99:3c:7d:07:a6:64:eb:
|
||||||
|
54:5d:15:37:a6:82:69:79:86:ab:d4:8c:cf:7b:26:64:a2:fc:
|
||||||
|
e4:45:df:5b:8f:eb:e2:6f:df:9a:10:12:8e:18:8d:e0:c3:e8:
|
||||||
|
00:83:88:30:63:7f:28:cf:54:c1:95:03:17:fa:21:14:ad:b3:
|
||||||
|
d3:ba:3a:86:0a:64:ed:3d:81:a4:6e:1d:72:d2:63:d9:1f:5d:
|
||||||
|
21:ac:ad:5e:66:a9:b1:6b:d2:bd:82:f2:7f:ae:f2:41:a3:90:
|
||||||
|
82:da:09:a6:e2:97:b7:0c:05:47:f3:c7:de:55:51:42:3d:01:
|
||||||
|
4b:a7:c0:5d:84:44:cb:93:81:f4:75:08:4e:20:0c:97:14:4d:
|
||||||
|
4e:d6:7f:5a:37:c4:4a:6f:0a:04:3a:7d:f6:33:05:79:07:8d:
|
||||||
|
e3:93:69:99:08:ce:50:3f
|
||||||
123
MagiskOnWSA/cacerts/4eba579e.0
Normal file
123
MagiskOnWSA/cacerts/4eba579e.0
Normal file
@ -0,0 +1,123 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIFzzCCA7egAwIBAgIUERKcb5NZIK+7kIzZeeqoTynDxo8wDQYJKoZIhvcNAQEL
|
||||||
|
BQAwdzELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAGA1UEBwwJSmVy
|
||||||
|
dXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRmcmVlLmxpbmsx
|
||||||
|
GjAYBgNVBAMMEU5ldEZyZWUgU2lnbiwgSE9UMB4XDTIyMDkxNDE1MjE0MVoXDTMy
|
||||||
|
MDkxMTE1MjE0MVowdzELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAG
|
||||||
|
A1UEBwwJSmVydXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRm
|
||||||
|
cmVlLmxpbmsxGjAYBgNVBAMMEU5ldEZyZWUgU2lnbiwgSE9UMIICIjANBgkqhkiG
|
||||||
|
9w0BAQEFAAOCAg8AMIICCgKCAgEAtAAmmLun08jzoWMLyC/fzCu9aES7fLWCU2Ur
|
||||||
|
u3sntuHLDJabIvU0p16hCMC3MVOTKFAKOJ9A+REyOyewQLJ+0Oi0rOPA6jk/+Srj
|
||||||
|
l69AwzkJYFli7ORClC/N1E2aKWj9evZHHdXeRMs2pklM9eRR+wYQUTQ5bkd0/Lsj
|
||||||
|
81QDUSzmgX/qkq3Dc4AiSt0gR+rd+c70y8IjVnBSwmHspyGv8Ve9DdRR3U01H8pM
|
||||||
|
gYpQVrN8BVfRNVpQgpjlKQZKQM1CcLFqUq++fG/QnhgcVuygGnqWAjNCkfbWi7Hq
|
||||||
|
IMYK5cyA3oLYiBH8gE0Js4ypf/jtFNBTeE7aiNbF6YgD6kPvlBIQ3nWHcvYz83mc
|
||||||
|
/yI8kDPHPBmNnCTxa46AYRBt3ungIKchSoIP2pfUDcwPI8C2o79ninvYxtwg2FH6
|
||||||
|
Mbc/hJqaGrTsFgw9rGitniZ4GHVPftW89O3xBENP9QAHimwbG8BCiwuweDu2xPsR
|
||||||
|
AJJ+a9bFRucDIaacOzrCjuzbXFJIy3KOgghe8V5mYypLHq8/pcDWczL59iWZit+l
|
||||||
|
2gt+wYIU3HxzC2AqzlBFadI10IlLFolaGyH9hJd5U0kYEXVp2IQV/6PGVhvmJI9y
|
||||||
|
9n+MqReibwUQVfuEg+l0gblqC2eTGnab5AVoCK/4cK+zxE0+wBpK70X4NtYLf0BO
|
||||||
|
WItUFK8CAwEAAaNTMFEwHQYDVR0OBBYEFG+/JFFhEinGuN7gWnOZxSMerGmZMB8G
|
||||||
|
A1UdIwQYMBaAFG+/JFFhEinGuN7gWnOZxSMerGmZMA8GA1UdEwEB/wQFMAMBAf8w
|
||||||
|
DQYJKoZIhvcNAQELBQADggIBAEVxrI5JmqQi5DhRAVIet41hFWrEIiJwYMbRYhRK
|
||||||
|
NpW1U4X7OiOm+/8v68oMkh3KHwbpIo48/egUDgv+F7Dzz5NhRgjXQbIW7ixO5+i+
|
||||||
|
7rW+177oJVvKtpD2NAp4o0Nty826AntDzyulSs7KvoE+Ifwq7iUTNwPmeOBpd7N2
|
||||||
|
WCZzpjOhhbuG4yYE+K76nZ34C8+7w3488iL8e5RwJQeuvXnEy4NiFzZmsoYqPUBd
|
||||||
|
HaZIQePxXI3jYi1YdckED3GZwo9VBZkarA5GekBvF9B2z/eKoHfnRrHDuQmBSAY3
|
||||||
|
+GBfqG6WNpDisKSj4YgeNXkTOZjOCyl/a3nwpLUawxAJyPjtgzc2vRDg3eVHUJNN
|
||||||
|
HIp60XVRQwwCTH6dHJiHsDCb2/6DgZzcUW20a4u8+zgDN+M+V8DYGjeTN/2X18br
|
||||||
|
kGN67L+n2krGQmVM4vu+42uOx0SJR/x10D8io7Vl9khWG3pB3GBoQSHivenzNPAW
|
||||||
|
BfJJG4keyG3EAVPHmyHpjP36NXe8rmimOgVVGDujEz+je+w9L4YQgQg5VfVp3+Pu
|
||||||
|
Wd7BbSsig+Vqgw1EDksMScLh34ZwniR1w2QL86XT5ExYNXQdo18fVYV0/OyzXKZx
|
||||||
|
8qnaParnjvguOl0YG4aXh0+72lEeIHXpPMmy6TDDqAOgNlrVbjviBw/J4Nzlty9s
|
||||||
|
bXLk
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
11:12:9c:6f:93:59:20:af:bb:90:8c:d9:79:ea:a8:4f:29:c3:c6:8f
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, HOT"
|
||||||
|
Validity
|
||||||
|
Not Before: Sep 14 15:21:41 2022 GMT
|
||||||
|
Not After : Sep 11 15:21:41 2032 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, HOT"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:b4:00:26:98:bb:a7:d3:c8:f3:a1:63:0b:c8:2f:
|
||||||
|
df:cc:2b:bd:68:44:bb:7c:b5:82:53:65:2b:bb:7b:
|
||||||
|
27:b6:e1:cb:0c:96:9b:22:f5:34:a7:5e:a1:08:c0:
|
||||||
|
b7:31:53:93:28:50:0a:38:9f:40:f9:11:32:3b:27:
|
||||||
|
b0:40:b2:7e:d0:e8:b4:ac:e3:c0:ea:39:3f:f9:2a:
|
||||||
|
e3:97:af:40:c3:39:09:60:59:62:ec:e4:42:94:2f:
|
||||||
|
cd:d4:4d:9a:29:68:fd:7a:f6:47:1d:d5:de:44:cb:
|
||||||
|
36:a6:49:4c:f5:e4:51:fb:06:10:51:34:39:6e:47:
|
||||||
|
74:fc:bb:23:f3:54:03:51:2c:e6:81:7f:ea:92:ad:
|
||||||
|
c3:73:80:22:4a:dd:20:47:ea:dd:f9:ce:f4:cb:c2:
|
||||||
|
23:56:70:52:c2:61:ec:a7:21:af:f1:57:bd:0d:d4:
|
||||||
|
51:dd:4d:35:1f:ca:4c:81:8a:50:56:b3:7c:05:57:
|
||||||
|
d1:35:5a:50:82:98:e5:29:06:4a:40:cd:42:70:b1:
|
||||||
|
6a:52:af:be:7c:6f:d0:9e:18:1c:56:ec:a0:1a:7a:
|
||||||
|
96:02:33:42:91:f6:d6:8b:b1:ea:20:c6:0a:e5:cc:
|
||||||
|
80:de:82:d8:88:11:fc:80:4d:09:b3:8c:a9:7f:f8:
|
||||||
|
ed:14:d0:53:78:4e:da:88:d6:c5:e9:88:03:ea:43:
|
||||||
|
ef:94:12:10:de:75:87:72:f6:33:f3:79:9c:ff:22:
|
||||||
|
3c:90:33:c7:3c:19:8d:9c:24:f1:6b:8e:80:61:10:
|
||||||
|
6d:de:e9:e0:20:a7:21:4a:82:0f:da:97:d4:0d:cc:
|
||||||
|
0f:23:c0:b6:a3:bf:67:8a:7b:d8:c6:dc:20:d8:51:
|
||||||
|
fa:31:b7:3f:84:9a:9a:1a:b4:ec:16:0c:3d:ac:68:
|
||||||
|
ad:9e:26:78:18:75:4f:7e:d5:bc:f4:ed:f1:04:43:
|
||||||
|
4f:f5:00:07:8a:6c:1b:1b:c0:42:8b:0b:b0:78:3b:
|
||||||
|
b6:c4:fb:11:00:92:7e:6b:d6:c5:46:e7:03:21:a6:
|
||||||
|
9c:3b:3a:c2:8e:ec:db:5c:52:48:cb:72:8e:82:08:
|
||||||
|
5e:f1:5e:66:63:2a:4b:1e:af:3f:a5:c0:d6:73:32:
|
||||||
|
f9:f6:25:99:8a:df:a5:da:0b:7e:c1:82:14:dc:7c:
|
||||||
|
73:0b:60:2a:ce:50:45:69:d2:35:d0:89:4b:16:89:
|
||||||
|
5a:1b:21:fd:84:97:79:53:49:18:11:75:69:d8:84:
|
||||||
|
15:ff:a3:c6:56:1b:e6:24:8f:72:f6:7f:8c:a9:17:
|
||||||
|
a2:6f:05:10:55:fb:84:83:e9:74:81:b9:6a:0b:67:
|
||||||
|
93:1a:76:9b:e4:05:68:08:af:f8:70:af:b3:c4:4d:
|
||||||
|
3e:c0:1a:4a:ef:45:f8:36:d6:0b:7f:40:4e:58:8b:
|
||||||
|
54:14:af
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
6F:BF:24:51:61:12:29:C6:B8:DE:E0:5A:73:99:C5:23:1E:AC:69:99
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:6F:BF:24:51:61:12:29:C6:B8:DE:E0:5A:73:99:C5:23:1E:AC:69:99
|
||||||
|
|
||||||
|
X509v3 Basic Constraints: critical
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
45:71:ac:8e:49:9a:a4:22:e4:38:51:01:52:1e:b7:8d:61:15:
|
||||||
|
6a:c4:22:22:70:60:c6:d1:62:14:4a:36:95:b5:53:85:fb:3a:
|
||||||
|
23:a6:fb:ff:2f:eb:ca:0c:92:1d:ca:1f:06:e9:22:8e:3c:fd:
|
||||||
|
e8:14:0e:0b:fe:17:b0:f3:cf:93:61:46:08:d7:41:b2:16:ee:
|
||||||
|
2c:4e:e7:e8:be:ee:b5:be:d7:be:e8:25:5b:ca:b6:90:f6:34:
|
||||||
|
0a:78:a3:43:6d:cb:cd:ba:02:7b:43:cf:2b:a5:4a:ce:ca:be:
|
||||||
|
81:3e:21:fc:2a:ee:25:13:37:03:e6:78:e0:69:77:b3:76:58:
|
||||||
|
26:73:a6:33:a1:85:bb:86:e3:26:04:f8:ae:fa:9d:9d:f8:0b:
|
||||||
|
cf:bb:c3:7e:3c:f2:22:fc:7b:94:70:25:07:ae:bd:79:c4:cb:
|
||||||
|
83:62:17:36:66:b2:86:2a:3d:40:5d:1d:a6:48:41:e3:f1:5c:
|
||||||
|
8d:e3:62:2d:58:75:c9:04:0f:71:99:c2:8f:55:05:99:1a:ac:
|
||||||
|
0e:46:7a:40:6f:17:d0:76:cf:f7:8a:a0:77:e7:46:b1:c3:b9:
|
||||||
|
09:81:48:06:37:f8:60:5f:a8:6e:96:36:90:e2:b0:a4:a3:e1:
|
||||||
|
88:1e:35:79:13:39:98:ce:0b:29:7f:6b:79:f0:a4:b5:1a:c3:
|
||||||
|
10:09:c8:f8:ed:83:37:36:bd:10:e0:dd:e5:47:50:93:4d:1c:
|
||||||
|
8a:7a:d1:75:51:43:0c:02:4c:7e:9d:1c:98:87:b0:30:9b:db:
|
||||||
|
fe:83:81:9c:dc:51:6d:b4:6b:8b:bc:fb:38:03:37:e3:3e:57:
|
||||||
|
c0:d8:1a:37:93:37:fd:97:d7:c6:eb:90:63:7a:ec:bf:a7:da:
|
||||||
|
4a:c6:42:65:4c:e2:fb:be:e3:6b:8e:c7:44:89:47:fc:75:d0:
|
||||||
|
3f:22:a3:b5:65:f6:48:56:1b:7a:41:dc:60:68:41:21:e2:bd:
|
||||||
|
e9:f3:34:f0:16:05:f2:49:1b:89:1e:c8:6d:c4:01:53:c7:9b:
|
||||||
|
21:e9:8c:fd:fa:35:77:bc:ae:68:a6:3a:05:55:18:3b:a3:13:
|
||||||
|
3f:a3:7b:ec:3d:2f:86:10:81:08:39:55:f5:69:df:e3:ee:59:
|
||||||
|
de:c1:6d:2b:22:83:e5:6a:83:0d:44:0e:4b:0c:49:c2:e1:df:
|
||||||
|
86:70:9e:24:75:c3:64:0b:f3:a5:d3:e4:4c:58:35:74:1d:a3:
|
||||||
|
5f:1f:55:85:74:fc:ec:b3:5c:a6:71:f2:a9:da:3d:aa:e7:8e:
|
||||||
|
f8:2e:3a:5d:18:1b:86:97:87:4f:bb:da:51:1e:20:75:e9:3c:
|
||||||
|
c9:b2:e9:30:c3:a8:03:a0:36:5a:d5:6e:3b:e2:07:0f:c9:e0:
|
||||||
|
dc:e5:b7:2f:6c:6d:72:e4
|
||||||
123
MagiskOnWSA/cacerts/6207c6f5.0
Normal file
123
MagiskOnWSA/cacerts/6207c6f5.0
Normal file
@ -0,0 +1,123 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIF0zCCA7ugAwIBAgIUaH5U+ogY8MmdlevWZGKqnge9GKQwDQYJKoZIhvcNAQEL
|
||||||
|
BQAweTELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAGA1UEBwwJSmVy
|
||||||
|
dXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRmcmVlLmxpbmsx
|
||||||
|
HDAaBgNVBAMME05ldEZyZWUgU2lnbiwgQmV6ZXEwHhcNMjIwNjAxMTk1NTIxWhcN
|
||||||
|
MzIwNTI5MTk1NTIxWjB5MQswCQYDVQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIw
|
||||||
|
EAYDVQQHDAlKZXJ1c2FsZW0xEDAOBgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5l
|
||||||
|
dGZyZWUubGluazEcMBoGA1UEAwwTTmV0RnJlZSBTaWduLCBCZXplcTCCAiIwDQYJ
|
||||||
|
KoZIhvcNAQEBBQADggIPADCCAgoCggIBANipYPeTK3GJ9BpwEpEGE/hzB8MlD+Rs
|
||||||
|
hw4tTWWRtZC0ok9kY/jmWJSzRMP4jKbOPtKkiUNNd3l2SvgvrHPuMz/R9B728wK2
|
||||||
|
ZYS295KTRDSgM51e+gCfziUXR36mCCvjuLmRdVbsXrAJjAtlPN1SD9eFDtMx6Pm8
|
||||||
|
LfSK6HyVF4Igafq8el6x9lSdfGqWWxWjuBaO6ooNUoIORYOLOQezMHRG1vfabx58
|
||||||
|
aEKZSN+bvEPmf4m1RXu4ynevE8aEQBHsr/4X7sU7hRXXrxLkS5qJSeqbfS+tp36a
|
||||||
|
HaVA8APRradFLvZa9ejAli8WAwwdw2r6AATQ3mmuIcaZUeC954HPgUwaz97wE2zo
|
||||||
|
GMbsX7bE9oEyLRT8sDV+dvN8MEXvt2XWx4icHLuycqxOGzZKkjmP73qMdeZw+mxW
|
||||||
|
xBk8H7pCWBQsJ5z0xxtir5kBVUqPSdmAOsz3FLhRyW8JB09JurZc3czxaCrVT7oS
|
||||||
|
MGIj+koFIYlbQqudwBTPF3hUBlgvS3PA339YHD6H8Fncj20tb2MxQ6jb5IDnFvY/
|
||||||
|
dc36sSauiUCzwPJM1FHDmaJDQcj7r2EArWDxZrWL1Zt99xf3yQQFUWh8+BMOba9M
|
||||||
|
x1E6XWfhVGlhS9yks0DwOKktO+rZwO3fVTVprWvnzFOWmpHAzvLxfiS5blseebAM
|
||||||
|
3+S4PGQiCHJBAgMBAAGjUzBRMB0GA1UdDgQWBBSFbv9UhQwCMY5hdYElGT2uCS2g
|
||||||
|
PTAfBgNVHSMEGDAWgBSFbv9UhQwCMY5hdYElGT2uCS2gPTAPBgNVHRMBAf8EBTAD
|
||||||
|
AQH/MA0GCSqGSIb3DQEBCwUAA4ICAQB5FmjWgu11dysbxacJO5uLYQ/UVipSFAsl
|
||||||
|
s/x04NRHona1UpOLGt6y70Q4XjkLnabeYc+x5g1UUr6BzDjXb4CG/FLjGhNP4zPE
|
||||||
|
xL9bUXpVThFHyO1LrsnbSLfIJZZ4CRvPmx0vbK0G9p23PTNCv7RFqDfqfA1P0z/g
|
||||||
|
X1n8SatOauOefsM94AihODwoOWLFsl14YnYp99V1f7ChrqZ4GKzgb0M+COJLOAIV
|
||||||
|
Ur6qaa5eqKf8jIw08xbZy19K4jgOEGIDifmoAtYEpCwIzH9VPeDqdcaBGuc+uZUp
|
||||||
|
9mxgIbJk0qgaPmu25TM12x66YeZZvPgeOycl2dzMTIwPvw3TfNzrio7tPRk5GEcT
|
||||||
|
3KzngfFpvQyros/kYQMKMPYL5hssRae4aDGr9sS1D4LR31hhopQ0+w4y/+kQJDbB
|
||||||
|
JCkUP87ae6mtNW4sCXaStWaZZzomonEAxNkh4sfBMT5wVsglU236k/yN5n7Ib/mL
|
||||||
|
yGUBs6lzMdcScG+Ath4cwtxNnC3m2g8w8/MYAf/+wBL/A8r2GAPTqLvfjtEzH621
|
||||||
|
b1Yw4//rSJg5ZpO1IGBFIVBFImBHOpHrjigPEJECiUS3y0jKUNyymo66QqRHwl1Y
|
||||||
|
71gRskGUK6tyfO45ZiLH8r8m7NR1wXBmAAmtOtdzi5H2ahVRNrW/zrfS7ttASJB5
|
||||||
|
20p8M55zUw==
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
68:7e:54:fa:88:18:f0:c9:9d:95:eb:d6:64:62:aa:9e:07:bd:18:a4
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, Bezeq"
|
||||||
|
Validity
|
||||||
|
Not Before: Jun 1 19:55:21 2022 GMT
|
||||||
|
Not After : May 29 19:55:21 2032 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, Bezeq"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:d8:a9:60:f7:93:2b:71:89:f4:1a:70:12:91:06:
|
||||||
|
13:f8:73:07:c3:25:0f:e4:6c:87:0e:2d:4d:65:91:
|
||||||
|
b5:90:b4:a2:4f:64:63:f8:e6:58:94:b3:44:c3:f8:
|
||||||
|
8c:a6:ce:3e:d2:a4:89:43:4d:77:79:76:4a:f8:2f:
|
||||||
|
ac:73:ee:33:3f:d1:f4:1e:f6:f3:02:b6:65:84:b6:
|
||||||
|
f7:92:93:44:34:a0:33:9d:5e:fa:00:9f:ce:25:17:
|
||||||
|
47:7e:a6:08:2b:e3:b8:b9:91:75:56:ec:5e:b0:09:
|
||||||
|
8c:0b:65:3c:dd:52:0f:d7:85:0e:d3:31:e8:f9:bc:
|
||||||
|
2d:f4:8a:e8:7c:95:17:82:20:69:fa:bc:7a:5e:b1:
|
||||||
|
f6:54:9d:7c:6a:96:5b:15:a3:b8:16:8e:ea:8a:0d:
|
||||||
|
52:82:0e:45:83:8b:39:07:b3:30:74:46:d6:f7:da:
|
||||||
|
6f:1e:7c:68:42:99:48:df:9b:bc:43:e6:7f:89:b5:
|
||||||
|
45:7b:b8:ca:77:af:13:c6:84:40:11:ec:af:fe:17:
|
||||||
|
ee:c5:3b:85:15:d7:af:12:e4:4b:9a:89:49:ea:9b:
|
||||||
|
7d:2f:ad:a7:7e:9a:1d:a5:40:f0:03:d1:ad:a7:45:
|
||||||
|
2e:f6:5a:f5:e8:c0:96:2f:16:03:0c:1d:c3:6a:fa:
|
||||||
|
00:04:d0:de:69:ae:21:c6:99:51:e0:bd:e7:81:cf:
|
||||||
|
81:4c:1a:cf:de:f0:13:6c:e8:18:c6:ec:5f:b6:c4:
|
||||||
|
f6:81:32:2d:14:fc:b0:35:7e:76:f3:7c:30:45:ef:
|
||||||
|
b7:65:d6:c7:88:9c:1c:bb:b2:72:ac:4e:1b:36:4a:
|
||||||
|
92:39:8f:ef:7a:8c:75:e6:70:fa:6c:56:c4:19:3c:
|
||||||
|
1f:ba:42:58:14:2c:27:9c:f4:c7:1b:62:af:99:01:
|
||||||
|
55:4a:8f:49:d9:80:3a:cc:f7:14:b8:51:c9:6f:09:
|
||||||
|
07:4f:49:ba:b6:5c:dd:cc:f1:68:2a:d5:4f:ba:12:
|
||||||
|
30:62:23:fa:4a:05:21:89:5b:42:ab:9d:c0:14:cf:
|
||||||
|
17:78:54:06:58:2f:4b:73:c0:df:7f:58:1c:3e:87:
|
||||||
|
f0:59:dc:8f:6d:2d:6f:63:31:43:a8:db:e4:80:e7:
|
||||||
|
16:f6:3f:75:cd:fa:b1:26:ae:89:40:b3:c0:f2:4c:
|
||||||
|
d4:51:c3:99:a2:43:41:c8:fb:af:61:00:ad:60:f1:
|
||||||
|
66:b5:8b:d5:9b:7d:f7:17:f7:c9:04:05:51:68:7c:
|
||||||
|
f8:13:0e:6d:af:4c:c7:51:3a:5d:67:e1:54:69:61:
|
||||||
|
4b:dc:a4:b3:40:f0:38:a9:2d:3b:ea:d9:c0:ed:df:
|
||||||
|
55:35:69:ad:6b:e7:cc:53:96:9a:91:c0:ce:f2:f1:
|
||||||
|
7e:24:b9:6e:5b:1e:79:b0:0c:df:e4:b8:3c:64:22:
|
||||||
|
08:72:41
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
85:6E:FF:54:85:0C:02:31:8E:61:75:81:25:19:3D:AE:09:2D:A0:3D
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:85:6E:FF:54:85:0C:02:31:8E:61:75:81:25:19:3D:AE:09:2D:A0:3D
|
||||||
|
|
||||||
|
X509v3 Basic Constraints: critical
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
79:16:68:d6:82:ed:75:77:2b:1b:c5:a7:09:3b:9b:8b:61:0f:
|
||||||
|
d4:56:2a:52:14:0b:25:b3:fc:74:e0:d4:47:a2:76:b5:52:93:
|
||||||
|
8b:1a:de:b2:ef:44:38:5e:39:0b:9d:a6:de:61:cf:b1:e6:0d:
|
||||||
|
54:52:be:81:cc:38:d7:6f:80:86:fc:52:e3:1a:13:4f:e3:33:
|
||||||
|
c4:c4:bf:5b:51:7a:55:4e:11:47:c8:ed:4b:ae:c9:db:48:b7:
|
||||||
|
c8:25:96:78:09:1b:cf:9b:1d:2f:6c:ad:06:f6:9d:b7:3d:33:
|
||||||
|
42:bf:b4:45:a8:37:ea:7c:0d:4f:d3:3f:e0:5f:59:fc:49:ab:
|
||||||
|
4e:6a:e3:9e:7e:c3:3d:e0:08:a1:38:3c:28:39:62:c5:b2:5d:
|
||||||
|
78:62:76:29:f7:d5:75:7f:b0:a1:ae:a6:78:18:ac:e0:6f:43:
|
||||||
|
3e:08:e2:4b:38:02:15:52:be:aa:69:ae:5e:a8:a7:fc:8c:8c:
|
||||||
|
34:f3:16:d9:cb:5f:4a:e2:38:0e:10:62:03:89:f9:a8:02:d6:
|
||||||
|
04:a4:2c:08:cc:7f:55:3d:e0:ea:75:c6:81:1a:e7:3e:b9:95:
|
||||||
|
29:f6:6c:60:21:b2:64:d2:a8:1a:3e:6b:b6:e5:33:35:db:1e:
|
||||||
|
ba:61:e6:59:bc:f8:1e:3b:27:25:d9:dc:cc:4c:8c:0f:bf:0d:
|
||||||
|
d3:7c:dc:eb:8a:8e:ed:3d:19:39:18:47:13:dc:ac:e7:81:f1:
|
||||||
|
69:bd:0c:ab:a2:cf:e4:61:03:0a:30:f6:0b:e6:1b:2c:45:a7:
|
||||||
|
b8:68:31:ab:f6:c4:b5:0f:82:d1:df:58:61:a2:94:34:fb:0e:
|
||||||
|
32:ff:e9:10:24:36:c1:24:29:14:3f:ce:da:7b:a9:ad:35:6e:
|
||||||
|
2c:09:76:92:b5:66:99:67:3a:26:a2:71:00:c4:d9:21:e2:c7:
|
||||||
|
c1:31:3e:70:56:c8:25:53:6d:fa:93:fc:8d:e6:7e:c8:6f:f9:
|
||||||
|
8b:c8:65:01:b3:a9:73:31:d7:12:70:6f:80:b6:1e:1c:c2:dc:
|
||||||
|
4d:9c:2d:e6:da:0f:30:f3:f3:18:01:ff:fe:c0:12:ff:03:ca:
|
||||||
|
f6:18:03:d3:a8:bb:df:8e:d1:33:1f:ad:b5:6f:56:30:e3:ff:
|
||||||
|
eb:48:98:39:66:93:b5:20:60:45:21:50:45:22:60:47:3a:91:
|
||||||
|
eb:8e:28:0f:10:91:02:89:44:b7:cb:48:ca:50:dc:b2:9a:8e:
|
||||||
|
ba:42:a4:47:c2:5d:58:ef:58:11:b2:41:94:2b:ab:72:7c:ee:
|
||||||
|
39:66:22:c7:f2:bf:26:ec:d4:75:c1:70:66:00:09:ad:3a:d7:
|
||||||
|
73:8b:91:f6:6a:15:51:36:b5:bf:ce:b7:d2:ee:db:40:48:90:
|
||||||
|
79:db:4a:7c:33:9e:73:53
|
||||||
81
MagiskOnWSA/cacerts/66bbb532.0
Normal file
81
MagiskOnWSA/cacerts/66bbb532.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIID4TCCAsmgAwIBAgIJAIsaro78xwDlMA0GCSqGSIb3DQEBCwUAMIGGMQswCQYD
|
||||||
|
VQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIwEAYDVQQHDAlKZXJ1c2FsZW0xEDAO
|
||||||
|
BgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5ldGZyZWUubGluazEpMCcGA1UEAwwg
|
||||||
|
TmV0RnJlZSBTaWduICwgS29zaGVyU2ltIENlbGxjb20wHhcNMTcwMjA5MTYzNzIz
|
||||||
|
WhcNMjYxMjE5MTYzNzIzWjCBhjELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFl
|
||||||
|
bDESMBAGA1UEBwwJSmVydXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQL
|
||||||
|
DAxuZXRmcmVlLmxpbmsxKTAnBgNVBAMMIE5ldEZyZWUgU2lnbiAsIEtvc2hlclNp
|
||||||
|
bSBDZWxsY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAsGzn8/an
|
||||||
|
SokAGXPd8XvBEyNCEby+4MQNa/osraC7ORKNk3C42b0cfPhf8pUpj66L69EcgmhS
|
||||||
|
veZyrZYlDGnUh7/2faF0EwtxffN1UK5qzEFfd2YICHXl81pVvifbmZgB3/c64KFm
|
||||||
|
+2CsyWZ2XTGPzD9zIrJdHFGgHdVu/UDDj0oLU2G0v0npse7au/gKNSxx1StzP3N6
|
||||||
|
uOo6Ih3KB74FCF0hc2aiJpfE9ECinSeHHF39TMzEJNvC4+fuTOb1odYsNP83otp7
|
||||||
|
KbLjCQsCMomxQlQTy3vfTvCA8f2BSILo4U6j/BHyhZriyjvhnPTlonWBrLHU5bd+
|
||||||
|
HNeiIeucPgRz+QIDAQABo1AwTjAdBgNVHQ4EFgQUf3PgrlRBo19oBK4M47swRdXg
|
||||||
|
pAQwHwYDVR0jBBgwFoAUf3PgrlRBo19oBK4M47swRdXgpAQwDAYDVR0TBAUwAwEB
|
||||||
|
/zANBgkqhkiG9w0BAQsFAAOCAQEAUIdlD+x9CFJXvKgmW6FAuAV3w6JG8zz4MwQO
|
||||||
|
5aXbs3g8ioIJ6KUBmtzcQhM/NLVr/oXIXPZxXWI7tP3f5N3iLVwrh6krKOU+jSna
|
||||||
|
HXK0BYXPivp8rRJX56gUQqLUlS94l3iAHX8N+qY2D0hSj4H044R5mWsuYxrtdAr2
|
||||||
|
glaz6luXOo+NMH2uRnWYX/uAAEpbQLPlztVsoV4LsZ2C54dK7neQ+A6qRL/IZwJE
|
||||||
|
bYeRwWYoK7OY/BNLj/Vx25IzZYlU/lP8qa6UcUWmPeyIPJqPvjdO95zEodX2iuWE
|
||||||
|
cuc5pUqSu5/xxosDx3vWpFhPaU5gq9WEN5uPgFd96yHoFKWvtg==
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
8b:1a:ae:8e:fc:c7:00:e5
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , KosherSim Cellcom"
|
||||||
|
Validity
|
||||||
|
Not Before: Feb 9 16:37:23 2017 GMT
|
||||||
|
Not After : Dec 19 16:37:23 2026 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , KosherSim Cellcom"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:b0:6c:e7:f3:f6:a7:4a:89:00:19:73:dd:f1:7b:
|
||||||
|
c1:13:23:42:11:bc:be:e0:c4:0d:6b:fa:2c:ad:a0:
|
||||||
|
bb:39:12:8d:93:70:b8:d9:bd:1c:7c:f8:5f:f2:95:
|
||||||
|
29:8f:ae:8b:eb:d1:1c:82:68:52:bd:e6:72:ad:96:
|
||||||
|
25:0c:69:d4:87:bf:f6:7d:a1:74:13:0b:71:7d:f3:
|
||||||
|
75:50:ae:6a:cc:41:5f:77:66:08:08:75:e5:f3:5a:
|
||||||
|
55:be:27:db:99:98:01:df:f7:3a:e0:a1:66:fb:60:
|
||||||
|
ac:c9:66:76:5d:31:8f:cc:3f:73:22:b2:5d:1c:51:
|
||||||
|
a0:1d:d5:6e:fd:40:c3:8f:4a:0b:53:61:b4:bf:49:
|
||||||
|
e9:b1:ee:da:bb:f8:0a:35:2c:71:d5:2b:73:3f:73:
|
||||||
|
7a:b8:ea:3a:22:1d:ca:07:be:05:08:5d:21:73:66:
|
||||||
|
a2:26:97:c4:f4:40:a2:9d:27:87:1c:5d:fd:4c:cc:
|
||||||
|
c4:24:db:c2:e3:e7:ee:4c:e6:f5:a1:d6:2c:34:ff:
|
||||||
|
37:a2:da:7b:29:b2:e3:09:0b:02:32:89:b1:42:54:
|
||||||
|
13:cb:7b:df:4e:f0:80:f1:fd:81:48:82:e8:e1:4e:
|
||||||
|
a3:fc:11:f2:85:9a:e2:ca:3b:e1:9c:f4:e5:a2:75:
|
||||||
|
81:ac:b1:d4:e5:b7:7e:1c:d7:a2:21:eb:9c:3e:04:
|
||||||
|
73:f9
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
7F:73:E0:AE:54:41:A3:5F:68:04:AE:0C:E3:BB:30:45:D5:E0:A4:04
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:7F:73:E0:AE:54:41:A3:5F:68:04:AE:0C:E3:BB:30:45:D5:E0:A4:04
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
50:87:65:0f:ec:7d:08:52:57:bc:a8:26:5b:a1:40:b8:05:77:
|
||||||
|
c3:a2:46:f3:3c:f8:33:04:0e:e5:a5:db:b3:78:3c:8a:82:09:
|
||||||
|
e8:a5:01:9a:dc:dc:42:13:3f:34:b5:6b:fe:85:c8:5c:f6:71:
|
||||||
|
5d:62:3b:b4:fd:df:e4:dd:e2:2d:5c:2b:87:a9:2b:28:e5:3e:
|
||||||
|
8d:29:da:1d:72:b4:05:85:cf:8a:fa:7c:ad:12:57:e7:a8:14:
|
||||||
|
42:a2:d4:95:2f:78:97:78:80:1d:7f:0d:fa:a6:36:0f:48:52:
|
||||||
|
8f:81:f4:e3:84:79:99:6b:2e:63:1a:ed:74:0a:f6:82:56:b3:
|
||||||
|
ea:5b:97:3a:8f:8d:30:7d:ae:46:75:98:5f:fb:80:00:4a:5b:
|
||||||
|
40:b3:e5:ce:d5:6c:a1:5e:0b:b1:9d:82:e7:87:4a:ee:77:90:
|
||||||
|
f8:0e:aa:44:bf:c8:67:02:44:6d:87:91:c1:66:28:2b:b3:98:
|
||||||
|
fc:13:4b:8f:f5:71:db:92:33:65:89:54:fe:53:fc:a9:ae:94:
|
||||||
|
71:45:a6:3d:ec:88:3c:9a:8f:be:37:4e:f7:9c:c4:a1:d5:f6:
|
||||||
|
8a:e5:84:72:e7:39:a5:4a:92:bb:9f:f1:c6:8b:03:c7:7b:d6:
|
||||||
|
a4:58:4f:69:4e:60:ab:d5:84:37:9b:8f:80:57:7d:eb:21:e8:
|
||||||
|
14:a5:af:b6
|
||||||
81
MagiskOnWSA/cacerts/820d5f23.0
Normal file
81
MagiskOnWSA/cacerts/820d5f23.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIDzTCCArWgAwIBAgIJAM/zhl8GVAzYMA0GCSqGSIb3DQEBCwUAMH0xCzAJBgNV
|
||||||
|
BAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcMCUplcnVzYWxlbTEQMA4G
|
||||||
|
A1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0ZnJlZS5saW5rMSAwHgYDVQQDDBdO
|
||||||
|
ZXRGcmVlIFNpZ24sIEhvdE1vYmlsZTAeFw0xNjA3MTMxMTM5MzZaFw0yNjA1MjIx
|
||||||
|
MTM5MzZaMH0xCzAJBgNVBAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcM
|
||||||
|
CUplcnVzYWxlbTEQMA4GA1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0ZnJlZS5s
|
||||||
|
aW5rMSAwHgYDVQQDDBdOZXRGcmVlIFNpZ24sIEhvdE1vYmlsZTCCASIwDQYJKoZI
|
||||||
|
hvcNAQEBBQADggEPADCCAQoCggEBAK36bGJixwgMX5twmmteI3j+8JfR5XdOSN6N
|
||||||
|
MLLsQuR7/LUXMbCBB5WNDGoF823rDbiIZwuqoH4JVN3I4BNitl0QzB2wlTLzEkMr
|
||||||
|
Db9sA6owahQwhh+m1yNovM3luSlt7eJS8yWUMNgp8gPxWV1j3RBGASHRKuzU2btg
|
||||||
|
I7WZoD5vNX2VrdrN+TxbRsrRHbMZhmv2Q8v4vNf1bwma64VyT+VDALx0V6HSjSnP
|
||||||
|
XMBvY0qtsqQILt53nTrtbTyat1oJaAcaeF/oSi+ibcRqRD0RQjPokD7ZBEIzx7b4
|
||||||
|
5YD4bsdr9WbSMjaa6DMDC0Zr/1MavLJu5DqO9hMljKfxb5HMcB8CAwEAAaNQME4w
|
||||||
|
HQYDVR0OBBYEFLRpqEWnXat8cUzbZ2r+LdeBMj+mMB8GA1UdIwQYMBaAFLRpqEWn
|
||||||
|
Xat8cUzbZ2r+LdeBMj+mMAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQELBQADggEB
|
||||||
|
ADXTOVrk1BbXQiCbPUX0eWOskyu+Nq4uJONFhrhBiKwG/leMd+fKjtbj5avVh81B
|
||||||
|
1NmHojzlls/kWcI4bjfqkKpv1eXKlrRA334BoLxGj7u4dbzgNfCNhE96lA6qIW+6
|
||||||
|
m6BkpYESXc06RX41RVWzYyOJX6foSv8aqdo1aICy+LvBtXewKQixDbGFNqSmSLB5
|
||||||
|
UHcrwjgOK8aWXvaJe2mJAV91HKhfgSFkFsokrVveaP985ej3s59si4htKbI9Qqx0
|
||||||
|
ZBMJdfklpqI1fDdL4cDNssX6kNus+gnJzP0tQW00DMH6V6OIqYrL/CJRJx4634yT
|
||||||
|
ddo6lzNM9hZhrtlM/czjLn8=
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
cf:f3:86:5f:06:54:0c:d8
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, HotMobile"
|
||||||
|
Validity
|
||||||
|
Not Before: Jul 13 11:39:36 2016 GMT
|
||||||
|
Not After : May 22 11:39:36 2026 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, HotMobile"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:ad:fa:6c:62:62:c7:08:0c:5f:9b:70:9a:6b:5e:
|
||||||
|
23:78:fe:f0:97:d1:e5:77:4e:48:de:8d:30:b2:ec:
|
||||||
|
42:e4:7b:fc:b5:17:31:b0:81:07:95:8d:0c:6a:05:
|
||||||
|
f3:6d:eb:0d:b8:88:67:0b:aa:a0:7e:09:54:dd:c8:
|
||||||
|
e0:13:62:b6:5d:10:cc:1d:b0:95:32:f3:12:43:2b:
|
||||||
|
0d:bf:6c:03:aa:30:6a:14:30:86:1f:a6:d7:23:68:
|
||||||
|
bc:cd:e5:b9:29:6d:ed:e2:52:f3:25:94:30:d8:29:
|
||||||
|
f2:03:f1:59:5d:63:dd:10:46:01:21:d1:2a:ec:d4:
|
||||||
|
d9:bb:60:23:b5:99:a0:3e:6f:35:7d:95:ad:da:cd:
|
||||||
|
f9:3c:5b:46:ca:d1:1d:b3:19:86:6b:f6:43:cb:f8:
|
||||||
|
bc:d7:f5:6f:09:9a:eb:85:72:4f:e5:43:00:bc:74:
|
||||||
|
57:a1:d2:8d:29:cf:5c:c0:6f:63:4a:ad:b2:a4:08:
|
||||||
|
2e:de:77:9d:3a:ed:6d:3c:9a:b7:5a:09:68:07:1a:
|
||||||
|
78:5f:e8:4a:2f:a2:6d:c4:6a:44:3d:11:42:33:e8:
|
||||||
|
90:3e:d9:04:42:33:c7:b6:f8:e5:80:f8:6e:c7:6b:
|
||||||
|
f5:66:d2:32:36:9a:e8:33:03:0b:46:6b:ff:53:1a:
|
||||||
|
bc:b2:6e:e4:3a:8e:f6:13:25:8c:a7:f1:6f:91:cc:
|
||||||
|
70:1f
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
B4:69:A8:45:A7:5D:AB:7C:71:4C:DB:67:6A:FE:2D:D7:81:32:3F:A6
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:B4:69:A8:45:A7:5D:AB:7C:71:4C:DB:67:6A:FE:2D:D7:81:32:3F:A6
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
35:d3:39:5a:e4:d4:16:d7:42:20:9b:3d:45:f4:79:63:ac:93:
|
||||||
|
2b:be:36:ae:2e:24:e3:45:86:b8:41:88:ac:06:fe:57:8c:77:
|
||||||
|
e7:ca:8e:d6:e3:e5:ab:d5:87:cd:41:d4:d9:87:a2:3c:e5:96:
|
||||||
|
cf:e4:59:c2:38:6e:37:ea:90:aa:6f:d5:e5:ca:96:b4:40:df:
|
||||||
|
7e:01:a0:bc:46:8f:bb:b8:75:bc:e0:35:f0:8d:84:4f:7a:94:
|
||||||
|
0e:aa:21:6f:ba:9b:a0:64:a5:81:12:5d:cd:3a:45:7e:35:45:
|
||||||
|
55:b3:63:23:89:5f:a7:e8:4a:ff:1a:a9:da:35:68:80:b2:f8:
|
||||||
|
bb:c1:b5:77:b0:29:08:b1:0d:b1:85:36:a4:a6:48:b0:79:50:
|
||||||
|
77:2b:c2:38:0e:2b:c6:96:5e:f6:89:7b:69:89:01:5f:75:1c:
|
||||||
|
a8:5f:81:21:64:16:ca:24:ad:5b:de:68:ff:7c:e5:e8:f7:b3:
|
||||||
|
9f:6c:8b:88:6d:29:b2:3d:42:ac:74:64:13:09:75:f9:25:a6:
|
||||||
|
a2:35:7c:37:4b:e1:c0:cd:b2:c5:fa:90:db:ac:fa:09:c9:cc:
|
||||||
|
fd:2d:41:6d:34:0c:c1:fa:57:a3:88:a9:8a:cb:fc:22:51:27:
|
||||||
|
1e:3a:df:8c:93:75:da:3a:97:33:4c:f6:16:61:ae:d9:4c:fd:
|
||||||
|
cc:e3:2e:7f
|
||||||
123
MagiskOnWSA/cacerts/85c0c4be.0
Normal file
123
MagiskOnWSA/cacerts/85c0c4be.0
Normal file
@ -0,0 +1,123 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIF3TCCA8WgAwIBAgIUGSL6iZ8Kz/CT3Q1kiYoKK75gxfwwDQYJKoZIhvcNAQEL
|
||||||
|
BQAwfjELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAGA1UEBwwJSmVy
|
||||||
|
dXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRmcmVlLmxpbmsx
|
||||||
|
ITAfBgNVBAMMGE5ldEZyZWUgU2lnbiwgSUIgUGFydG5lcjAeFw0yMDA0MjYxNDAz
|
||||||
|
MzlaFw0zMDA0MjQxNDAzMzlaMH4xCzAJBgNVBAYTAklMMQ8wDQYDVQQIDAZpc3Jh
|
||||||
|
ZWwxEjAQBgNVBAcMCUplcnVzYWxlbTEQMA4GA1UECgwHTmV0RnJlZTEVMBMGA1UE
|
||||||
|
CwwMbmV0ZnJlZS5saW5rMSEwHwYDVQQDDBhOZXRGcmVlIFNpZ24sIElCIFBhcnRu
|
||||||
|
ZXIwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCtj4vt55TGvmidDKVj
|
||||||
|
ktTyTHDKIJShq72REaYGfQhweEEBzMRJzprw8spOtL7LsayfyV7On/9NY7X6p79a
|
||||||
|
QFJUM/lGMwj5E5gWWDJt5yEe/LEJTHpeZUXIBu78cJR9pZsUP+iWvqj2TgJ2GwoD
|
||||||
|
WDdSmDWTxY93AP+4BL2421hA/NPjY8xkP+hofupC02WgKIODrC/72FrScQnxnMkD
|
||||||
|
1Hu9Yw4W4kX8FAhWR3YeXRE0gWV93JTWdBOEzM+7DKn9pdpNZdYXBu2UysNTwrsH
|
||||||
|
2c31R86et7o2NRhRup5GDBIgaVAi+RjmnTi7GIj5Js3IhIe9hOW5hoSwhNTZiCT+
|
||||||
|
Ks4zVvdvebA/1XMiQI2HQMQTtLrysYIYjM28YsEWob2JqYQ4eACcmEq2ZZJNMDj4
|
||||||
|
yGSdJVqZBwnwbK6PmmzQc9n7y+hSUHgg/6x7lPGRfG2XsIhrDrK8nuEU4mRSRlGG
|
||||||
|
OEL0dC7GY8ywAI30E5nLPtk6vcToaWAz12rC1waI5xyYKgcP8SdOg70SwQj/2/lO
|
||||||
|
QC5Bzl7581/XKbbLdrsQBXiJ7CN83z046Bs4TqBEqlTzKV257CwLXIW2Kd4nydx+
|
||||||
|
UuGEqeoNDIIxZCapRQ83mKGJmtGraLN73TLAfZJ2xq3xhMlXejR5JB4JGFmAhGBt
|
||||||
|
/Qr3MBAM9Lrn2vD0buihAn5D/QIDAQABo1MwUTAdBgNVHQ4EFgQUxgogJN2fOSCA
|
||||||
|
+Q1tBXEiLQz1clcwHwYDVR0jBBgwFoAUxgogJN2fOSCA+Q1tBXEiLQz1clcwDwYD
|
||||||
|
VR0TAQH/BAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAgEAFslaPHqfvOxKDjLHgbNB
|
||||||
|
Vu+m9/uLfMCMAxo85z8hayEIt7/HEzf03CQji/U3OMJPeah7POKlFkDE9tHxgPmD
|
||||||
|
Xmw7/gKPolJaPHS9hv484Fd7yu47lKuskYxW3FP9b1s7woO5YmCE8hVSWMLHRz1h
|
||||||
|
Sr7Mx8zj9/4nT1TF+ZI85TySCjhq+toQCFVmS/1gv2fqz2UoTJVebdJOwNgyiyjB
|
||||||
|
+y3ekjcXWIVZEsVqNDjM/6C+Uz1LJm+qzAoNOdVc7EIgheUTsNr3te/Zgv0Cg8Eo
|
||||||
|
d4V+EyaQkElbXKqcafZngxjQqyvEVoHocGDTvf+B3DLaqCIldEyWyusGsC1tyoJR
|
||||||
|
vQrkwco1VDWl89o3cPOgalI8M7W1nCougNt7PCNO/RjsdOncJE9UUphLHXO1nIgn
|
||||||
|
mGTVq3ZurDFaIodUNVV4YB+mmJ87ZjIbs8uQUvzEcQnoCmDBg4ABk+e4CJJhzLNP
|
||||||
|
XW+0L8W37ZyHl5Fx2JPWnZuGhZ214ODQJZ1T164G9dfkULHmd3xxc1hGEfvdybHd
|
||||||
|
sDIISA+7z1CJXtZYLJ5noOQG7VbrG0KUvO7U897/miXmF6C1rYwpTVlKhEQ8cChU
|
||||||
|
JnZrCImXL32d8iOzSU4EbLy8Nq89T3fcnWKstGbKpzJdzJ8bJUnveoEEGbo3rP72
|
||||||
|
86H7Aq+q7qWFjZT/vp9J2Is=
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
19:22:fa:89:9f:0a:cf:f0:93:dd:0d:64:89:8a:0a:2b:be:60:c5:fc
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, IB Partner"
|
||||||
|
Validity
|
||||||
|
Not Before: Apr 26 14:03:39 2020 GMT
|
||||||
|
Not After : Apr 24 14:03:39 2030 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, IB Partner"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:ad:8f:8b:ed:e7:94:c6:be:68:9d:0c:a5:63:92:
|
||||||
|
d4:f2:4c:70:ca:20:94:a1:ab:bd:91:11:a6:06:7d:
|
||||||
|
08:70:78:41:01:cc:c4:49:ce:9a:f0:f2:ca:4e:b4:
|
||||||
|
be:cb:b1:ac:9f:c9:5e:ce:9f:ff:4d:63:b5:fa:a7:
|
||||||
|
bf:5a:40:52:54:33:f9:46:33:08:f9:13:98:16:58:
|
||||||
|
32:6d:e7:21:1e:fc:b1:09:4c:7a:5e:65:45:c8:06:
|
||||||
|
ee:fc:70:94:7d:a5:9b:14:3f:e8:96:be:a8:f6:4e:
|
||||||
|
02:76:1b:0a:03:58:37:52:98:35:93:c5:8f:77:00:
|
||||||
|
ff:b8:04:bd:b8:db:58:40:fc:d3:e3:63:cc:64:3f:
|
||||||
|
e8:68:7e:ea:42:d3:65:a0:28:83:83:ac:2f:fb:d8:
|
||||||
|
5a:d2:71:09:f1:9c:c9:03:d4:7b:bd:63:0e:16:e2:
|
||||||
|
45:fc:14:08:56:47:76:1e:5d:11:34:81:65:7d:dc:
|
||||||
|
94:d6:74:13:84:cc:cf:bb:0c:a9:fd:a5:da:4d:65:
|
||||||
|
d6:17:06:ed:94:ca:c3:53:c2:bb:07:d9:cd:f5:47:
|
||||||
|
ce:9e:b7:ba:36:35:18:51:ba:9e:46:0c:12:20:69:
|
||||||
|
50:22:f9:18:e6:9d:38:bb:18:88:f9:26:cd:c8:84:
|
||||||
|
87:bd:84:e5:b9:86:84:b0:84:d4:d9:88:24:fe:2a:
|
||||||
|
ce:33:56:f7:6f:79:b0:3f:d5:73:22:40:8d:87:40:
|
||||||
|
c4:13:b4:ba:f2:b1:82:18:8c:cd:bc:62:c1:16:a1:
|
||||||
|
bd:89:a9:84:38:78:00:9c:98:4a:b6:65:92:4d:30:
|
||||||
|
38:f8:c8:64:9d:25:5a:99:07:09:f0:6c:ae:8f:9a:
|
||||||
|
6c:d0:73:d9:fb:cb:e8:52:50:78:20:ff:ac:7b:94:
|
||||||
|
f1:91:7c:6d:97:b0:88:6b:0e:b2:bc:9e:e1:14:e2:
|
||||||
|
64:52:46:51:86:38:42:f4:74:2e:c6:63:cc:b0:00:
|
||||||
|
8d:f4:13:99:cb:3e:d9:3a:bd:c4:e8:69:60:33:d7:
|
||||||
|
6a:c2:d7:06:88:e7:1c:98:2a:07:0f:f1:27:4e:83:
|
||||||
|
bd:12:c1:08:ff:db:f9:4e:40:2e:41:ce:5e:f9:f3:
|
||||||
|
5f:d7:29:b6:cb:76:bb:10:05:78:89:ec:23:7c:df:
|
||||||
|
3d:38:e8:1b:38:4e:a0:44:aa:54:f3:29:5d:b9:ec:
|
||||||
|
2c:0b:5c:85:b6:29:de:27:c9:dc:7e:52:e1:84:a9:
|
||||||
|
ea:0d:0c:82:31:64:26:a9:45:0f:37:98:a1:89:9a:
|
||||||
|
d1:ab:68:b3:7b:dd:32:c0:7d:92:76:c6:ad:f1:84:
|
||||||
|
c9:57:7a:34:79:24:1e:09:18:59:80:84:60:6d:fd:
|
||||||
|
0a:f7:30:10:0c:f4:ba:e7:da:f0:f4:6e:e8:a1:02:
|
||||||
|
7e:43:fd
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
C6:0A:20:24:DD:9F:39:20:80:F9:0D:6D:05:71:22:2D:0C:F5:72:57
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:C6:0A:20:24:DD:9F:39:20:80:F9:0D:6D:05:71:22:2D:0C:F5:72:57
|
||||||
|
|
||||||
|
X509v3 Basic Constraints: critical
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
16:c9:5a:3c:7a:9f:bc:ec:4a:0e:32:c7:81:b3:41:56:ef:a6:
|
||||||
|
f7:fb:8b:7c:c0:8c:03:1a:3c:e7:3f:21:6b:21:08:b7:bf:c7:
|
||||||
|
13:37:f4:dc:24:23:8b:f5:37:38:c2:4f:79:a8:7b:3c:e2:a5:
|
||||||
|
16:40:c4:f6:d1:f1:80:f9:83:5e:6c:3b:fe:02:8f:a2:52:5a:
|
||||||
|
3c:74:bd:86:fe:3c:e0:57:7b:ca:ee:3b:94:ab:ac:91:8c:56:
|
||||||
|
dc:53:fd:6f:5b:3b:c2:83:b9:62:60:84:f2:15:52:58:c2:c7:
|
||||||
|
47:3d:61:4a:be:cc:c7:cc:e3:f7:fe:27:4f:54:c5:f9:92:3c:
|
||||||
|
e5:3c:92:0a:38:6a:fa:da:10:08:55:66:4b:fd:60:bf:67:ea:
|
||||||
|
cf:65:28:4c:95:5e:6d:d2:4e:c0:d8:32:8b:28:c1:fb:2d:de:
|
||||||
|
92:37:17:58:85:59:12:c5:6a:34:38:cc:ff:a0:be:53:3d:4b:
|
||||||
|
26:6f:aa:cc:0a:0d:39:d5:5c:ec:42:20:85:e5:13:b0:da:f7:
|
||||||
|
b5:ef:d9:82:fd:02:83:c1:28:77:85:7e:13:26:90:90:49:5b:
|
||||||
|
5c:aa:9c:69:f6:67:83:18:d0:ab:2b:c4:56:81:e8:70:60:d3:
|
||||||
|
bd:ff:81:dc:32:da:a8:22:25:74:4c:96:ca:eb:06:b0:2d:6d:
|
||||||
|
ca:82:51:bd:0a:e4:c1:ca:35:54:35:a5:f3:da:37:70:f3:a0:
|
||||||
|
6a:52:3c:33:b5:b5:9c:2a:2e:80:db:7b:3c:23:4e:fd:18:ec:
|
||||||
|
74:e9:dc:24:4f:54:52:98:4b:1d:73:b5:9c:88:27:98:64:d5:
|
||||||
|
ab:76:6e:ac:31:5a:22:87:54:35:55:78:60:1f:a6:98:9f:3b:
|
||||||
|
66:32:1b:b3:cb:90:52:fc:c4:71:09:e8:0a:60:c1:83:80:01:
|
||||||
|
93:e7:b8:08:92:61:cc:b3:4f:5d:6f:b4:2f:c5:b7:ed:9c:87:
|
||||||
|
97:91:71:d8:93:d6:9d:9b:86:85:9d:b5:e0:e0:d0:25:9d:53:
|
||||||
|
d7:ae:06:f5:d7:e4:50:b1:e6:77:7c:71:73:58:46:11:fb:dd:
|
||||||
|
c9:b1:dd:b0:32:08:48:0f:bb:cf:50:89:5e:d6:58:2c:9e:67:
|
||||||
|
a0:e4:06:ed:56:eb:1b:42:94:bc:ee:d4:f3:de:ff:9a:25:e6:
|
||||||
|
17:a0:b5:ad:8c:29:4d:59:4a:84:44:3c:70:28:54:26:76:6b:
|
||||||
|
08:89:97:2f:7d:9d:f2:23:b3:49:4e:04:6c:bc:bc:36:af:3d:
|
||||||
|
4f:77:dc:9d:62:ac:b4:66:ca:a7:32:5d:cc:9f:1b:25:49:ef:
|
||||||
|
7a:81:04:19:ba:37:ac:fe:f6:f3:a1:fb:02:af:aa:ee:a5:85:
|
||||||
|
8d:94:ff:be:9f:49:d8:8b
|
||||||
123
MagiskOnWSA/cacerts/a4f6f3c0.0
Normal file
123
MagiskOnWSA/cacerts/a4f6f3c0.0
Normal file
@ -0,0 +1,123 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIFzzCCA7egAwIBAgIUJd8EwuvF4INK2P9FOVcNOxdqsSgwDQYJKoZIhvcNAQEL
|
||||||
|
BQAwdzELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAGA1UEBwwJSmVy
|
||||||
|
dXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRmcmVlLmxpbmsx
|
||||||
|
GjAYBgNVBAMMEU5ldEZyZWUgU2lnbiwgMDE4MB4XDTIxMDUwNDIwNTMxMFoXDTMx
|
||||||
|
MDUwMjIwNTMxMFowdzELMAkGA1UEBhMCSUwxDzANBgNVBAgMBmlzcmFlbDESMBAG
|
||||||
|
A1UEBwwJSmVydXNhbGVtMRAwDgYDVQQKDAdOZXRGcmVlMRUwEwYDVQQLDAxuZXRm
|
||||||
|
cmVlLmxpbmsxGjAYBgNVBAMMEU5ldEZyZWUgU2lnbiwgMDE4MIICIjANBgkqhkiG
|
||||||
|
9w0BAQEFAAOCAg8AMIICCgKCAgEA1kkqmmuy9XZw0PVC6wwg0BJFs0zWn3IgUYmd
|
||||||
|
8UXeqfT5Uii/PM4as/Wf3EG7ByRE03njCVTFussYEE3lbHEsjzvcCiDxOkG2HoYf
|
||||||
|
G69Bt+jxKPPNFIjom3SB3l6S57UyiSHk5TaS/x7NpjUhVeMde/McBqW7FU/eEYgx
|
||||||
|
PBaqkQNNG0Wqtl6XybwSdsh0vGJ92wzlTwrKhVpAbesu4L9OYVleZtdW7/xtoB1J
|
||||||
|
aMygZmSEV7v6mW7dMzJdRk8zHCssLJJOgGno/5R/i6/ezGeKu31/FtcpGOw6o8Jc
|
||||||
|
yBvAOV4oV/S992Y+Uxll33dYNTg7ABYNtYYd864K51T03HJi/pedNd2ALu0Oqb/I
|
||||||
|
04dYt8ZRVK1I+K1b7LsYzVIM/5YWRS3uCNAfQMsfy/4ECD/IgbXVGI+Z0kHrElgV
|
||||||
|
uYrOglYrAuFrtG1kV4hoPaGsFjzxM/wrdXaJii0EvbLASeX6TDWOP+5xTZhBesTs
|
||||||
|
6/gAR/DzOQpdqEIn5v/+foKgaCtBHdFPbayFoywg/Dq9rjbq+7pOiS9XzywHgOZU
|
||||||
|
Ussq+F0TB0nJ7NkN2Jx5DiAaehOZJpZNWADVheoUehfLGQDA3ffhwi+tdANkgOMc
|
||||||
|
w6igzwbo1PIrZNcoXDpG+3Dpo8J1+X+nXe4HOKh8K5TbdR9xmUAag3sKZZ5wPjyt
|
||||||
|
bAq/II0CAwEAAaNTMFEwHQYDVR0OBBYEFK0REcJzkVprhzsKvxjI9w+vlYTiMB8G
|
||||||
|
A1UdIwQYMBaAFK0REcJzkVprhzsKvxjI9w+vlYTiMA8GA1UdEwEB/wQFMAMBAf8w
|
||||||
|
DQYJKoZIhvcNAQELBQADggIBALe8h93x+yAkpIeVRcOoNpSnpNiDc7/bY2fJxxWy
|
||||||
|
Yo4TaT9J+dhlbdedvzgbm0NUcWCKKA0vmR+/PsKYwdJcko1e3kdKTmWGwEBPDRJC
|
||||||
|
kCGn2ZuXeJokRzyAVKceU7DPHAq7n/C5IJ9ivTMEKYc5SS6WxdxBYePf+tXmPGGi
|
||||||
|
vYrL1hEgZ+oUx1rXRz7Spr8lUFc7PPvjfPLD9uRoO5K6rdkeHiChuY45Sky/A012
|
||||||
|
FRhyKR7liZZPtl6QzuLiIDVNcAoJL3SYeaQMmNt6kupQmMcey1RnOwzq56UGOxMr
|
||||||
|
RSUwgiz56PtQwx6q8R6wqpfJgFipoOzRME6+WgoHPyvIZV9AzNnH4Pv+vfVun8TC
|
||||||
|
AEvbcyjPyJUL89TqJIgpmlyLRmNETurrGWVgOS4/0rJy5q35I4rDMdrbM8S0AJZy
|
||||||
|
rSfwwRZXfmxoxYSkx+W6pyIJoj9dtidp1PsKcDoT7CrapmhOKqJzxKdCX3yNQBd0
|
||||||
|
wWoemiLvBRsCJ1dTZePe470aGmpkL8eLSx68neujrbK9lvDC/GIm97Wx103izZw0
|
||||||
|
TkkSyB/JtXcqERWYVfAnmhaxIPS1Gwvk+ytBs9kYbNx1cHvPR+JUbax8jmmamKHN
|
||||||
|
k20mVi+ExBJcyBCs+1gCkKXSlMUpvOSc+tG+nS390JD5pyui1dPp1dlogIX95ad0
|
||||||
|
H5kG
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
25:df:04:c2:eb:c5:e0:83:4a:d8:ff:45:39:57:0d:3b:17:6a:b1:28
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, 018"
|
||||||
|
Validity
|
||||||
|
Not Before: May 4 20:53:10 2021 GMT
|
||||||
|
Not After : May 2 20:53:10 2031 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign, 018"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (4096 bit)
|
||||||
|
Modulus:
|
||||||
|
00:d6:49:2a:9a:6b:b2:f5:76:70:d0:f5:42:eb:0c:
|
||||||
|
20:d0:12:45:b3:4c:d6:9f:72:20:51:89:9d:f1:45:
|
||||||
|
de:a9:f4:f9:52:28:bf:3c:ce:1a:b3:f5:9f:dc:41:
|
||||||
|
bb:07:24:44:d3:79:e3:09:54:c5:ba:cb:18:10:4d:
|
||||||
|
e5:6c:71:2c:8f:3b:dc:0a:20:f1:3a:41:b6:1e:86:
|
||||||
|
1f:1b:af:41:b7:e8:f1:28:f3:cd:14:88:e8:9b:74:
|
||||||
|
81:de:5e:92:e7:b5:32:89:21:e4:e5:36:92:ff:1e:
|
||||||
|
cd:a6:35:21:55:e3:1d:7b:f3:1c:06:a5:bb:15:4f:
|
||||||
|
de:11:88:31:3c:16:aa:91:03:4d:1b:45:aa:b6:5e:
|
||||||
|
97:c9:bc:12:76:c8:74:bc:62:7d:db:0c:e5:4f:0a:
|
||||||
|
ca:85:5a:40:6d:eb:2e:e0:bf:4e:61:59:5e:66:d7:
|
||||||
|
56:ef:fc:6d:a0:1d:49:68:cc:a0:66:64:84:57:bb:
|
||||||
|
fa:99:6e:dd:33:32:5d:46:4f:33:1c:2b:2c:2c:92:
|
||||||
|
4e:80:69:e8:ff:94:7f:8b:af:de:cc:67:8a:bb:7d:
|
||||||
|
7f:16:d7:29:18:ec:3a:a3:c2:5c:c8:1b:c0:39:5e:
|
||||||
|
28:57:f4:bd:f7:66:3e:53:19:65:df:77:58:35:38:
|
||||||
|
3b:00:16:0d:b5:86:1d:f3:ae:0a:e7:54:f4:dc:72:
|
||||||
|
62:fe:97:9d:35:dd:80:2e:ed:0e:a9:bf:c8:d3:87:
|
||||||
|
58:b7:c6:51:54:ad:48:f8:ad:5b:ec:bb:18:cd:52:
|
||||||
|
0c:ff:96:16:45:2d:ee:08:d0:1f:40:cb:1f:cb:fe:
|
||||||
|
04:08:3f:c8:81:b5:d5:18:8f:99:d2:41:eb:12:58:
|
||||||
|
15:b9:8a:ce:82:56:2b:02:e1:6b:b4:6d:64:57:88:
|
||||||
|
68:3d:a1:ac:16:3c:f1:33:fc:2b:75:76:89:8a:2d:
|
||||||
|
04:bd:b2:c0:49:e5:fa:4c:35:8e:3f:ee:71:4d:98:
|
||||||
|
41:7a:c4:ec:eb:f8:00:47:f0:f3:39:0a:5d:a8:42:
|
||||||
|
27:e6:ff:fe:7e:82:a0:68:2b:41:1d:d1:4f:6d:ac:
|
||||||
|
85:a3:2c:20:fc:3a:bd:ae:36:ea:fb:ba:4e:89:2f:
|
||||||
|
57:cf:2c:07:80:e6:54:52:cb:2a:f8:5d:13:07:49:
|
||||||
|
c9:ec:d9:0d:d8:9c:79:0e:20:1a:7a:13:99:26:96:
|
||||||
|
4d:58:00:d5:85:ea:14:7a:17:cb:19:00:c0:dd:f7:
|
||||||
|
e1:c2:2f:ad:74:03:64:80:e3:1c:c3:a8:a0:cf:06:
|
||||||
|
e8:d4:f2:2b:64:d7:28:5c:3a:46:fb:70:e9:a3:c2:
|
||||||
|
75:f9:7f:a7:5d:ee:07:38:a8:7c:2b:94:db:75:1f:
|
||||||
|
71:99:40:1a:83:7b:0a:65:9e:70:3e:3c:ad:6c:0a:
|
||||||
|
bf:20:8d
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
AD:11:11:C2:73:91:5A:6B:87:3B:0A:BF:18:C8:F7:0F:AF:95:84:E2
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:AD:11:11:C2:73:91:5A:6B:87:3B:0A:BF:18:C8:F7:0F:AF:95:84:E2
|
||||||
|
|
||||||
|
X509v3 Basic Constraints: critical
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
b7:bc:87:dd:f1:fb:20:24:a4:87:95:45:c3:a8:36:94:a7:a4:
|
||||||
|
d8:83:73:bf:db:63:67:c9:c7:15:b2:62:8e:13:69:3f:49:f9:
|
||||||
|
d8:65:6d:d7:9d:bf:38:1b:9b:43:54:71:60:8a:28:0d:2f:99:
|
||||||
|
1f:bf:3e:c2:98:c1:d2:5c:92:8d:5e:de:47:4a:4e:65:86:c0:
|
||||||
|
40:4f:0d:12:42:90:21:a7:d9:9b:97:78:9a:24:47:3c:80:54:
|
||||||
|
a7:1e:53:b0:cf:1c:0a:bb:9f:f0:b9:20:9f:62:bd:33:04:29:
|
||||||
|
87:39:49:2e:96:c5:dc:41:61:e3:df:fa:d5:e6:3c:61:a2:bd:
|
||||||
|
8a:cb:d6:11:20:67:ea:14:c7:5a:d7:47:3e:d2:a6:bf:25:50:
|
||||||
|
57:3b:3c:fb:e3:7c:f2:c3:f6:e4:68:3b:92:ba:ad:d9:1e:1e:
|
||||||
|
20:a1:b9:8e:39:4a:4c:bf:03:4d:76:15:18:72:29:1e:e5:89:
|
||||||
|
96:4f:b6:5e:90:ce:e2:e2:20:35:4d:70:0a:09:2f:74:98:79:
|
||||||
|
a4:0c:98:db:7a:92:ea:50:98:c7:1e:cb:54:67:3b:0c:ea:e7:
|
||||||
|
a5:06:3b:13:2b:45:25:30:82:2c:f9:e8:fb:50:c3:1e:aa:f1:
|
||||||
|
1e:b0:aa:97:c9:80:58:a9:a0:ec:d1:30:4e:be:5a:0a:07:3f:
|
||||||
|
2b:c8:65:5f:40:cc:d9:c7:e0:fb:fe:bd:f5:6e:9f:c4:c2:00:
|
||||||
|
4b:db:73:28:cf:c8:95:0b:f3:d4:ea:24:88:29:9a:5c:8b:46:
|
||||||
|
63:44:4e:ea:eb:19:65:60:39:2e:3f:d2:b2:72:e6:ad:f9:23:
|
||||||
|
8a:c3:31:da:db:33:c4:b4:00:96:72:ad:27:f0:c1:16:57:7e:
|
||||||
|
6c:68:c5:84:a4:c7:e5:ba:a7:22:09:a2:3f:5d:b6:27:69:d4:
|
||||||
|
fb:0a:70:3a:13:ec:2a:da:a6:68:4e:2a:a2:73:c4:a7:42:5f:
|
||||||
|
7c:8d:40:17:74:c1:6a:1e:9a:22:ef:05:1b:02:27:57:53:65:
|
||||||
|
e3:de:e3:bd:1a:1a:6a:64:2f:c7:8b:4b:1e:bc:9d:eb:a3:ad:
|
||||||
|
b2:bd:96:f0:c2:fc:62:26:f7:b5:b1:d7:4d:e2:cd:9c:34:4e:
|
||||||
|
49:12:c8:1f:c9:b5:77:2a:11:15:98:55:f0:27:9a:16:b1:20:
|
||||||
|
f4:b5:1b:0b:e4:fb:2b:41:b3:d9:18:6c:dc:75:70:7b:cf:47:
|
||||||
|
e2:54:6d:ac:7c:8e:69:9a:98:a1:cd:93:6d:26:56:2f:84:c4:
|
||||||
|
12:5c:c8:10:ac:fb:58:02:90:a5:d2:94:c5:29:bc:e4:9c:fa:
|
||||||
|
d1:be:9d:2d:fd:d0:90:f9:a7:2b:a2:d5:d3:e9:d5:d9:68:80:
|
||||||
|
85:fd:e5:a7:74:1f:99:06
|
||||||
BIN
MagiskOnWSA/cacerts/b0396035.0
Normal file
BIN
MagiskOnWSA/cacerts/b0396035.0
Normal file
Binary file not shown.
81
MagiskOnWSA/cacerts/ea335731.0
Normal file
81
MagiskOnWSA/cacerts/ea335731.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIDzzCCAregAwIBAgIJANJjV3HuLlVqMA0GCSqGSIb3DQEBCwUAMH4xCzAJBgNV
|
||||||
|
BAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcMCWplcnVzYWxlbTEQMA4G
|
||||||
|
A1UECgwHTmV0RnJlZTEZMBcGA1UECwwQbmV0ZnJlZS42MTNtLm9yZzEdMBsGA1UE
|
||||||
|
AwwUTmV0RnJlZSBTaWduICxSTCBJU1AwHhcNMTQxMTE1MjMxNjU0WhcNMjQwOTIz
|
||||||
|
MjMxNjU0WjB+MQswCQYDVQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIwEAYDVQQH
|
||||||
|
DAlqZXJ1c2FsZW0xEDAOBgNVBAoMB05ldEZyZWUxGTAXBgNVBAsMEG5ldGZyZWUu
|
||||||
|
NjEzbS5vcmcxHTAbBgNVBAMMFE5ldEZyZWUgU2lnbiAsUkwgSVNQMIIBIjANBgkq
|
||||||
|
hkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA2gEv5S0YJFYrWSNJJNhtBRN9IfyFhh/l
|
||||||
|
NCo2K8DKkq3CFCthHADZu1v9gRAa9NxC7wrsmK/wBTwoVwcHKrxrmxt/vs6bwZZ7
|
||||||
|
9/TwKDA9Ar3SY6bvsDvij0/53frRoAhUJwdFkwlkIN0DNJWv8n3xAoIRBI3pOxcE
|
||||||
|
890Q2RDw+ydc4OIgETIel3vDqe7aTXTjb7BJjqIYTf9Wad3gmTGpRToNhC0kyQuk
|
||||||
|
MN2XxYHhK/+jjoL/O9vcd3ZLaYlYbQbT/Ud63CfIyvB+ASkqnRGFBIQttkzVrPHP
|
||||||
|
fRkhM+C6BlRfv0njt9Hl5jJjreWXSryd5iSwVVU6VtHo6TZFtUwA/wIDAQABo1Aw
|
||||||
|
TjAdBgNVHQ4EFgQUG9R/R+XGIIaXGs74B2+JNqoka7kwHwYDVR0jBBgwFoAUG9R/
|
||||||
|
R+XGIIaXGs74B2+JNqoka7kwDAYDVR0TBAUwAwEB/zANBgkqhkiG9w0BAQsFAAOC
|
||||||
|
AQEAQh9Id5A0LvTu4yCqM8rrP1mpEBKv4XjMWihR9gZ6fBY8NkyWBfyQkylc6Jlm
|
||||||
|
vrtFH4etuQkElN7tL1ZAyXAmOVnXB19asft/swA+UGEpdqmdIJiz+Q9KSP4c64Xw
|
||||||
|
L9svsOqBouiBYPWpURO0AJVk42lmXVGopGcet8hzMmmBejlCbDWi7mu+RJEMIMkp
|
||||||
|
g6cITc6m/Hrawt3oRxfyERKdoXUpTtTV5Cu4oHLwgcdMbp7IvHJO1SS5fP8OhObN
|
||||||
|
9aVsHN+TzDsXZqkvYn/Tn4fO4YtUdokCSzc39caq9ZiwqUpD0dSOYDotlIIXmzxE
|
||||||
|
OmymXu+SCGzKmR72vZouU0NuTw==
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
d2:63:57:71:ee:2e:55:6a
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = jerusalem, O = NetFree, OU = netfree.613m.org, CN = "NetFree Sign ,RL ISP"
|
||||||
|
Validity
|
||||||
|
Not Before: Nov 15 23:16:54 2014 GMT
|
||||||
|
Not After : Sep 23 23:16:54 2024 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = jerusalem, O = NetFree, OU = netfree.613m.org, CN = "NetFree Sign ,RL ISP"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:da:01:2f:e5:2d:18:24:56:2b:59:23:49:24:d8:
|
||||||
|
6d:05:13:7d:21:fc:85:86:1f:e5:34:2a:36:2b:c0:
|
||||||
|
ca:92:ad:c2:14:2b:61:1c:00:d9:bb:5b:fd:81:10:
|
||||||
|
1a:f4:dc:42:ef:0a:ec:98:af:f0:05:3c:28:57:07:
|
||||||
|
07:2a:bc:6b:9b:1b:7f:be:ce:9b:c1:96:7b:f7:f4:
|
||||||
|
f0:28:30:3d:02:bd:d2:63:a6:ef:b0:3b:e2:8f:4f:
|
||||||
|
f9:dd:fa:d1:a0:08:54:27:07:45:93:09:64:20:dd:
|
||||||
|
03:34:95:af:f2:7d:f1:02:82:11:04:8d:e9:3b:17:
|
||||||
|
04:f3:dd:10:d9:10:f0:fb:27:5c:e0:e2:20:11:32:
|
||||||
|
1e:97:7b:c3:a9:ee:da:4d:74:e3:6f:b0:49:8e:a2:
|
||||||
|
18:4d:ff:56:69:dd:e0:99:31:a9:45:3a:0d:84:2d:
|
||||||
|
24:c9:0b:a4:30:dd:97:c5:81:e1:2b:ff:a3:8e:82:
|
||||||
|
ff:3b:db:dc:77:76:4b:69:89:58:6d:06:d3:fd:47:
|
||||||
|
7a:dc:27:c8:ca:f0:7e:01:29:2a:9d:11:85:04:84:
|
||||||
|
2d:b6:4c:d5:ac:f1:cf:7d:19:21:33:e0:ba:06:54:
|
||||||
|
5f:bf:49:e3:b7:d1:e5:e6:32:63:ad:e5:97:4a:bc:
|
||||||
|
9d:e6:24:b0:55:55:3a:56:d1:e8:e9:36:45:b5:4c:
|
||||||
|
00:ff
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
1B:D4:7F:47:E5:C6:20:86:97:1A:CE:F8:07:6F:89:36:AA:24:6B:B9
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:1B:D4:7F:47:E5:C6:20:86:97:1A:CE:F8:07:6F:89:36:AA:24:6B:B9
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
42:1f:48:77:90:34:2e:f4:ee:e3:20:aa:33:ca:eb:3f:59:a9:
|
||||||
|
10:12:af:e1:78:cc:5a:28:51:f6:06:7a:7c:16:3c:36:4c:96:
|
||||||
|
05:fc:90:93:29:5c:e8:99:66:be:bb:45:1f:87:ad:b9:09:04:
|
||||||
|
94:de:ed:2f:56:40:c9:70:26:39:59:d7:07:5f:5a:b1:fb:7f:
|
||||||
|
b3:00:3e:50:61:29:76:a9:9d:20:98:b3:f9:0f:4a:48:fe:1c:
|
||||||
|
eb:85:f0:2f:db:2f:b0:ea:81:a2:e8:81:60:f5:a9:51:13:b4:
|
||||||
|
00:95:64:e3:69:66:5d:51:a8:a4:67:1e:b7:c8:73:32:69:81:
|
||||||
|
7a:39:42:6c:35:a2:ee:6b:be:44:91:0c:20:c9:29:83:a7:08:
|
||||||
|
4d:ce:a6:fc:7a:da:c2:dd:e8:47:17:f2:11:12:9d:a1:75:29:
|
||||||
|
4e:d4:d5:e4:2b:b8:a0:72:f0:81:c7:4c:6e:9e:c8:bc:72:4e:
|
||||||
|
d5:24:b9:7c:ff:0e:84:e6:cd:f5:a5:6c:1c:df:93:cc:3b:17:
|
||||||
|
66:a9:2f:62:7f:d3:9f:87:ce:e1:8b:54:76:89:02:4b:37:37:
|
||||||
|
f5:c6:aa:f5:98:b0:a9:4a:43:d1:d4:8e:60:3a:2d:94:82:17:
|
||||||
|
9b:3c:44:3a:6c:a6:5e:ef:92:08:6c:ca:99:1e:f6:bd:9a:2e:
|
||||||
|
53:43:6e:4f
|
||||||
81
MagiskOnWSA/cacerts/f9b4d31c.0
Normal file
81
MagiskOnWSA/cacerts/f9b4d31c.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIID3TCCAsWgAwIBAgIJALT9ZoUCwnlMMA0GCSqGSIb3DQEBCwUAMIGEMQswCQYD
|
||||||
|
VQQGEwJJTDEPMA0GA1UECAwGaXNyYWVsMRIwEAYDVQQHDAlKZXJ1c2FsZW0xEDAO
|
||||||
|
BgNVBAoMB05ldEZyZWUxFTATBgNVBAsMDG5ldGZyZWUubGluazEnMCUGA1UEAwwe
|
||||||
|
TmV0RnJlZSBTaWduICwgTmV0RnJlZUFueXdoZXJlMB4XDTE2MDQwNTE1MTc0MVoX
|
||||||
|
DTI2MDIxMjE1MTc0MVowgYQxCzAJBgNVBAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwx
|
||||||
|
EjAQBgNVBAcMCUplcnVzYWxlbTEQMA4GA1UECgwHTmV0RnJlZTEVMBMGA1UECwwM
|
||||||
|
bmV0ZnJlZS5saW5rMScwJQYDVQQDDB5OZXRGcmVlIFNpZ24gLCBOZXRGcmVlQW55
|
||||||
|
d2hlcmUwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC19KPegpnTrYAJ
|
||||||
|
m3ZWQ/vEL3rAXBE89jFcDU7xYmRgeEI+CKD+U5exLTmD7w0pQVM45HghlufWL0uy
|
||||||
|
pPYBR0YL6PbvFzskTnlaQuZBbwBsqf7hrAh7gA3nWintID50L8xtHKiRiLfK+NnM
|
||||||
|
//iQ03uwkwLT2xaUMvw7IbZcrHlwTfN6fxvvfhnCIE/Tnjz2p3aQI6ZmrD6rwZLm
|
||||||
|
oX2TGXQGCteOpM0gpn3gi/q30qzMsgCQ6YfeATzjGFe2rMM6Gy66HjNEzO5w6i7W
|
||||||
|
mG57upSNCTIgKjjwtGlZMg53jVqlfuMuZbZO7OwyatpcuV3KgtER5H8HuQboaZ4v
|
||||||
|
IYAA+0IZAgMBAAGjUDBOMB0GA1UdDgQWBBQR8hgc1nsIVVnUyF3uhivwht7AzDAf
|
||||||
|
BgNVHSMEGDAWgBQR8hgc1nsIVVnUyF3uhivwht7AzDAMBgNVHRMEBTADAQH/MA0G
|
||||||
|
CSqGSIb3DQEBCwUAA4IBAQCOBLgAhZGzGCKvXLbITDrZIC4Oh4sBD4geGnlcO8Rt
|
||||||
|
10JLn9lgW0SnYfMoX2ZOayiwlEltF7PB2dYiGk9+7vDjzpChp5HBDLSTJpCdJ5lc
|
||||||
|
AWEyTjGw9z7cfUUnGJtCaNDPvaLjcvi4KELyAyn3HejwPMcG+F1wyCjwWKoo0MX7
|
||||||
|
ac+/qnp50nUcPYGnPS2hKoMp8tVkC56q9h7KU9AfY001b11lnVfeJynDuMKWivgw
|
||||||
|
6KOH0YSvWt8/d6DM6MtxMyAxdS5sP7htj8pdBTMcHHfw44663xdsd+9nvlaSXDNR
|
||||||
|
aq71pK24e7eEg0zZQEJ8L6finDIQAx8jt6kse1uVZW50
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
b4:fd:66:85:02:c2:79:4c
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , NetFreeAnywhere"
|
||||||
|
Validity
|
||||||
|
Not Before: Apr 5 15:17:41 2016 GMT
|
||||||
|
Not After : Feb 12 15:17:41 2026 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , NetFreeAnywhere"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:b5:f4:a3:de:82:99:d3:ad:80:09:9b:76:56:43:
|
||||||
|
fb:c4:2f:7a:c0:5c:11:3c:f6:31:5c:0d:4e:f1:62:
|
||||||
|
64:60:78:42:3e:08:a0:fe:53:97:b1:2d:39:83:ef:
|
||||||
|
0d:29:41:53:38:e4:78:21:96:e7:d6:2f:4b:b2:a4:
|
||||||
|
f6:01:47:46:0b:e8:f6:ef:17:3b:24:4e:79:5a:42:
|
||||||
|
e6:41:6f:00:6c:a9:fe:e1:ac:08:7b:80:0d:e7:5a:
|
||||||
|
29:ed:20:3e:74:2f:cc:6d:1c:a8:91:88:b7:ca:f8:
|
||||||
|
d9:cc:ff:f8:90:d3:7b:b0:93:02:d3:db:16:94:32:
|
||||||
|
fc:3b:21:b6:5c:ac:79:70:4d:f3:7a:7f:1b:ef:7e:
|
||||||
|
19:c2:20:4f:d3:9e:3c:f6:a7:76:90:23:a6:66:ac:
|
||||||
|
3e:ab:c1:92:e6:a1:7d:93:19:74:06:0a:d7:8e:a4:
|
||||||
|
cd:20:a6:7d:e0:8b:fa:b7:d2:ac:cc:b2:00:90:e9:
|
||||||
|
87:de:01:3c:e3:18:57:b6:ac:c3:3a:1b:2e:ba:1e:
|
||||||
|
33:44:cc:ee:70:ea:2e:d6:98:6e:7b:ba:94:8d:09:
|
||||||
|
32:20:2a:38:f0:b4:69:59:32:0e:77:8d:5a:a5:7e:
|
||||||
|
e3:2e:65:b6:4e:ec:ec:32:6a:da:5c:b9:5d:ca:82:
|
||||||
|
d1:11:e4:7f:07:b9:06:e8:69:9e:2f:21:80:00:fb:
|
||||||
|
42:19
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
11:F2:18:1C:D6:7B:08:55:59:D4:C8:5D:EE:86:2B:F0:86:DE:C0:CC
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:11:F2:18:1C:D6:7B:08:55:59:D4:C8:5D:EE:86:2B:F0:86:DE:C0:CC
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
8e:04:b8:00:85:91:b3:18:22:af:5c:b6:c8:4c:3a:d9:20:2e:
|
||||||
|
0e:87:8b:01:0f:88:1e:1a:79:5c:3b:c4:6d:d7:42:4b:9f:d9:
|
||||||
|
60:5b:44:a7:61:f3:28:5f:66:4e:6b:28:b0:94:49:6d:17:b3:
|
||||||
|
c1:d9:d6:22:1a:4f:7e:ee:f0:e3:ce:90:a1:a7:91:c1:0c:b4:
|
||||||
|
93:26:90:9d:27:99:5c:01:61:32:4e:31:b0:f7:3e:dc:7d:45:
|
||||||
|
27:18:9b:42:68:d0:cf:bd:a2:e3:72:f8:b8:28:42:f2:03:29:
|
||||||
|
f7:1d:e8:f0:3c:c7:06:f8:5d:70:c8:28:f0:58:aa:28:d0:c5:
|
||||||
|
fb:69:cf:bf:aa:7a:79:d2:75:1c:3d:81:a7:3d:2d:a1:2a:83:
|
||||||
|
29:f2:d5:64:0b:9e:aa:f6:1e:ca:53:d0:1f:63:4d:35:6f:5d:
|
||||||
|
65:9d:57:de:27:29:c3:b8:c2:96:8a:f8:30:e8:a3:87:d1:84:
|
||||||
|
af:5a:df:3f:77:a0:cc:e8:cb:71:33:20:31:75:2e:6c:3f:b8:
|
||||||
|
6d:8f:ca:5d:05:33:1c:1c:77:f0:e3:8e:ba:df:17:6c:77:ef:
|
||||||
|
67:be:56:92:5c:33:51:6a:ae:f5:a4:ad:b8:7b:b7:84:83:4c:
|
||||||
|
d9:40:42:7c:2f:a7:e2:9c:32:10:03:1f:23:b7:a9:2c:7b:5b:
|
||||||
|
95:65:6e:74
|
||||||
81
MagiskOnWSA/cacerts/fbb5e364.0
Normal file
81
MagiskOnWSA/cacerts/fbb5e364.0
Normal file
@ -0,0 +1,81 @@
|
|||||||
|
-----BEGIN CERTIFICATE-----
|
||||||
|
MIIDxzCCAq+gAwIBAgIJAI2ViHiNxvW8MA0GCSqGSIb3DQEBCwUAMHoxCzAJBgNV
|
||||||
|
BAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcMCUplcnVzYWxlbTEQMA4G
|
||||||
|
A1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0ZnJlZS5saW5rMR0wGwYDVQQDDBRO
|
||||||
|
ZXRGcmVlIFNpZ24gLCB4Mm9uZTAeFw0xNjAzMTMxNjM1MjFaFw0yNjAxMjAxNjM1
|
||||||
|
MjFaMHoxCzAJBgNVBAYTAklMMQ8wDQYDVQQIDAZpc3JhZWwxEjAQBgNVBAcMCUpl
|
||||||
|
cnVzYWxlbTEQMA4GA1UECgwHTmV0RnJlZTEVMBMGA1UECwwMbmV0ZnJlZS5saW5r
|
||||||
|
MR0wGwYDVQQDDBROZXRGcmVlIFNpZ24gLCB4Mm9uZTCCASIwDQYJKoZIhvcNAQEB
|
||||||
|
BQADggEPADCCAQoCggEBALCFuiEa8k1KjSdvAUUXywlvxFUKP4hD2BrY0dvWK0xe
|
||||||
|
WnKO7jHpDK88Dv3+2aa15c09ULKLqw6NDg3zPo1Tzb6hJs2nuI5dXbmoKA8QRQr1
|
||||||
|
ny6JNi4LxAle6LTNqcAw+jsONmyx62vDXpRAHTNsguBdqbKZZp/8jLm9aNg0uvbn
|
||||||
|
g/E6gvUrwCylidcL3fQ3GiZsjj2RgzUITtLG2gCtHdAv87c5OJOw1tONv4Yfayxk
|
||||||
|
uG1n+4Z3eKzsDIbO7wbnWypcI/lod9xGub0st3YWjdxp10N2x5EYLgfwThG03RBk
|
||||||
|
vdWY1kfrzaL1e1jn0x5yqbdOEwzgZeQQZDmNNpybhlECAwEAAaNQME4wHQYDVR0O
|
||||||
|
BBYEFCimmwvFnAJ3VrIam6IzW70HpeNHMB8GA1UdIwQYMBaAFCimmwvFnAJ3VrIa
|
||||||
|
m6IzW70HpeNHMAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQELBQADggEBAKhoWpR6
|
||||||
|
G4atxcAdzQhA3e9LcyRNBdLvtNeZSSPHBPuxRqXDxRT6QhwdYR/mK9WjcOxdA6mj
|
||||||
|
m/wwLvOy3sbDFQySUs0Yu+aWn9GsFBBgdJoTwSgnwjY60wQ+/yyWCXIFabVHz7Nw
|
||||||
|
wepexJVQfz2yfnwfGHo3FCI4526NMwxEzy1Xt17wY4fxFmEusVEKqYKnYsHg2s8K
|
||||||
|
/4GKabaBpcv7iy3vIsks7mGe5NrgNS4MLACC8+5d3XVoqJeXsbX8usaRFDZrseE4
|
||||||
|
O3d27X+0kjPAKx8Ztn70VWDbS7Cuic6kKrBXjjEN5OTD60GJ1CCiZp6miyjkTHBq
|
||||||
|
mRkn51xTIRBX6S0=
|
||||||
|
-----END CERTIFICATE-----
|
||||||
|
Certificate:
|
||||||
|
Data:
|
||||||
|
Version: 3 (0x2)
|
||||||
|
Serial Number:
|
||||||
|
8d:95:88:78:8d:c6:f5:bc
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
Issuer: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , x2one"
|
||||||
|
Validity
|
||||||
|
Not Before: Mar 13 16:35:21 2016 GMT
|
||||||
|
Not After : Jan 20 16:35:21 2026 GMT
|
||||||
|
Subject: C = IL, ST = israel, L = Jerusalem, O = NetFree, OU = netfree.link, CN = "NetFree Sign , x2one"
|
||||||
|
Subject Public Key Info:
|
||||||
|
Public Key Algorithm: rsaEncryption
|
||||||
|
RSA Public-Key: (2048 bit)
|
||||||
|
Modulus:
|
||||||
|
00:b0:85:ba:21:1a:f2:4d:4a:8d:27:6f:01:45:17:
|
||||||
|
cb:09:6f:c4:55:0a:3f:88:43:d8:1a:d8:d1:db:d6:
|
||||||
|
2b:4c:5e:5a:72:8e:ee:31:e9:0c:af:3c:0e:fd:fe:
|
||||||
|
d9:a6:b5:e5:cd:3d:50:b2:8b:ab:0e:8d:0e:0d:f3:
|
||||||
|
3e:8d:53:cd:be:a1:26:cd:a7:b8:8e:5d:5d:b9:a8:
|
||||||
|
28:0f:10:45:0a:f5:9f:2e:89:36:2e:0b:c4:09:5e:
|
||||||
|
e8:b4:cd:a9:c0:30:fa:3b:0e:36:6c:b1:eb:6b:c3:
|
||||||
|
5e:94:40:1d:33:6c:82:e0:5d:a9:b2:99:66:9f:fc:
|
||||||
|
8c:b9:bd:68:d8:34:ba:f6:e7:83:f1:3a:82:f5:2b:
|
||||||
|
c0:2c:a5:89:d7:0b:dd:f4:37:1a:26:6c:8e:3d:91:
|
||||||
|
83:35:08:4e:d2:c6:da:00:ad:1d:d0:2f:f3:b7:39:
|
||||||
|
38:93:b0:d6:d3:8d:bf:86:1f:6b:2c:64:b8:6d:67:
|
||||||
|
fb:86:77:78:ac:ec:0c:86:ce:ef:06:e7:5b:2a:5c:
|
||||||
|
23:f9:68:77:dc:46:b9:bd:2c:b7:76:16:8d:dc:69:
|
||||||
|
d7:43:76:c7:91:18:2e:07:f0:4e:11:b4:dd:10:64:
|
||||||
|
bd:d5:98:d6:47:eb:cd:a2:f5:7b:58:e7:d3:1e:72:
|
||||||
|
a9:b7:4e:13:0c:e0:65:e4:10:64:39:8d:36:9c:9b:
|
||||||
|
86:51
|
||||||
|
Exponent: 65537 (0x10001)
|
||||||
|
X509v3 extensions:
|
||||||
|
X509v3 Subject Key Identifier:
|
||||||
|
28:A6:9B:0B:C5:9C:02:77:56:B2:1A:9B:A2:33:5B:BD:07:A5:E3:47
|
||||||
|
X509v3 Authority Key Identifier:
|
||||||
|
keyid:28:A6:9B:0B:C5:9C:02:77:56:B2:1A:9B:A2:33:5B:BD:07:A5:E3:47
|
||||||
|
|
||||||
|
X509v3 Basic Constraints:
|
||||||
|
CA:TRUE
|
||||||
|
Signature Algorithm: sha256WithRSAEncryption
|
||||||
|
a8:68:5a:94:7a:1b:86:ad:c5:c0:1d:cd:08:40:dd:ef:4b:73:
|
||||||
|
24:4d:05:d2:ef:b4:d7:99:49:23:c7:04:fb:b1:46:a5:c3:c5:
|
||||||
|
14:fa:42:1c:1d:61:1f:e6:2b:d5:a3:70:ec:5d:03:a9:a3:9b:
|
||||||
|
fc:30:2e:f3:b2:de:c6:c3:15:0c:92:52:cd:18:bb:e6:96:9f:
|
||||||
|
d1:ac:14:10:60:74:9a:13:c1:28:27:c2:36:3a:d3:04:3e:ff:
|
||||||
|
2c:96:09:72:05:69:b5:47:cf:b3:70:c1:ea:5e:c4:95:50:7f:
|
||||||
|
3d:b2:7e:7c:1f:18:7a:37:14:22:38:e7:6e:8d:33:0c:44:cf:
|
||||||
|
2d:57:b7:5e:f0:63:87:f1:16:61:2e:b1:51:0a:a9:82:a7:62:
|
||||||
|
c1:e0:da:cf:0a:ff:81:8a:69:b6:81:a5:cb:fb:8b:2d:ef:22:
|
||||||
|
c9:2c:ee:61:9e:e4:da:e0:35:2e:0c:2c:00:82:f3:ee:5d:dd:
|
||||||
|
75:68:a8:97:97:b1:b5:fc:ba:c6:91:14:36:6b:b1:e1:38:3b:
|
||||||
|
77:76:ed:7f:b4:92:33:c0:2b:1f:19:b6:7e:f4:55:60:db:4b:
|
||||||
|
b0:ae:89:ce:a4:2a:b0:57:8e:31:0d:e4:e4:c3:eb:41:89:d4:
|
||||||
|
20:a2:66:9e:a6:8b:28:e4:4c:70:6a:99:19:27:e7:5c:53:21:
|
||||||
|
10:57:e9:2d
|
||||||
38
MagiskOnWSA/docs/Fixes/Fix Error 0x80073CF0.md
Normal file
38
MagiskOnWSA/docs/Fixes/Fix Error 0x80073CF0.md
Normal file
@ -0,0 +1,38 @@
|
|||||||
|
## Issue: </br> Error 0x80073CF0 when "Run.bat" is executed to install Windows Subystem for Android (WSA)
|
||||||
|
### Preface:
|
||||||
|
##### This issue can arise due to many factors such as corruption of files when downloading the .zip/.7z files or extracting from the .zip/.7z files. This can be also caused if the folder name is too long (This is the case as MagiskOnWSA tends to generate a long string for the .zip/.7z file and the folder within the archive.)
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
|
||||||
|
---
|
||||||
|
## Solution
|
||||||
|
|
||||||
|
**1. Ensure the partition/drive you are installing from is NTFS**
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
**2. Redownload WSA Build .zip/.7z file from the [Releases page](https://github.com/MustardChef/WSABuilds/releases) (sometime the files can be corrupted during download and extraction)**
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
**3. Rename the .zip/.7z file to a shorter name, which can be anything to your choosing </br> (For example: WSA_2XXX.XXXXX.X.X_XXXX_Release-Nightly-with-magisk-XXXXXXX-XXXXXX-MindTheGapps-XX.X-RemovedAmazon ----> WSAArchive2XXX)**
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
**4. Extract the .zip or .7z archive (depends on the release) using 7-zip or a proper archive tool and not the built in Windows archive extractor**
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
**5. Rename the extracted folder(s) to a shorter name, which can be anything to your choosing**
|
||||||
|
|
||||||
|
#### For example:
|
||||||
|
- **Before:** WSA_2XXX.XXXXX.X.X_XXXX_Release-Nightly-with-magisk-XXXXXXX-XXXXXX-MindTheGapps-XX.X-RemovedAmazon
|
||||||
|
- **After:** WSAExtracted2XXX
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
**6. Ensure that 'Run.bat' is run as Administrator**
|
||||||
|
|
||||||
|
**Hope this works for you!**
|
||||||
|
|
||||||
108
MagiskOnWSA/docs/Fixes/Fix Error 0x80073CF6.md
Normal file
108
MagiskOnWSA/docs/Fixes/Fix Error 0x80073CF6.md
Normal file
@ -0,0 +1,108 @@
|
|||||||
|
## Issue: </br> Error 0x80073CF6 when "Run.bat" is executed to install Windows Subystem for Android (WSA)
|
||||||
|
### Preface:
|
||||||
|
##### This issue can arise due to many factors that is preventing the app from being registered. Although there is no definite solution, we can try these steps to try to fix the problem
|
||||||
|
##### This installation issue may also arise in systems that are using Modified Windows OSes such as ReviOS, Tiny10/11, etc. This is due to the fact that these OSes have been modified to remove certain features that are deemed unnecessary. This may cause issues with the installation of WSA.
|
||||||
|
</br>
|
||||||
|
|
||||||
|
```Powershell
|
||||||
|
Add-AppxPackage : Deployment failed with HRESULT: 0x80073CF6, Package could not be registered
|
||||||
|
In E:\WSA\Install.ps1:102 Character:1
|
||||||
|
+ Add-AppxPackage -ForceApplicationShutdown -ForceUpdateFromAnyVersion
|
||||||
|
|
||||||
|
+ CategoryInfo : WriteError: (E:\WSA\AppxManifest.xml:String) [Add-AppxPackage], IOException
|
||||||
|
+ FullyQualifiedErrorId : DeploymentError,Microsoft.Windows.Appx.PackageManager.Commands.AddAppxPackageCommand
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
</br>
|
||||||
|
|
||||||
|
---
|
||||||
|
## Prequisite Steps:
|
||||||
|
|
||||||
|
**1. Ensure the partition/drive you are installing from is NTFS**
|
||||||
|
|
||||||
|
**2. Redownload WSA Build .zip (sometime the files can be corrupted during download and extraction)**
|
||||||
|
|
||||||
|
**3. If you have installed WSA prior, make sure that it has been uninstalled and delete all folders containing "WindowsSubsystemForAndroid" from the following directories/paths and the subdirectories within:**
|
||||||
|
|
||||||
|
- *C:\ProgramData\Microsoft\Windows\AppRepository*
|
||||||
|
|
||||||
|
- *C:\ProgramData\Microsoft\Windows\WindowsApps*
|
||||||
|
|
||||||
|
- *%localappdata\ProgramData\Packages*
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
**4. Restart your Computer**
|
||||||
|
|
||||||
|
If the issue has been fixed, then there is no need to follow through the rest of the guide.
|
||||||
|
However, if you have the same issue, it is vital that you obtain the logs and try to decipher what is causing the error
|
||||||
|
|
||||||
|
To obtain the logs (admin privilege required):
|
||||||
|
|
||||||
|
1. Open a PowerShell window and change working directory to your Windows Subsystem For Android™ directory.
|
||||||
|
|
||||||
|
2. Run the command below in PowerShell. This should fail with an ActivityID, which is a UUID required for the next step.
|
||||||
|
```Powershell
|
||||||
|
Add-AppxPackage -ForceApplicationShutdown -ForceUpdateFromAnyVersion -Register .\AppxManifest.xml
|
||||||
|
```
|
||||||
|
3. Run the command below in PowerShell. This should print the log of the failed operation.
|
||||||
|
|
||||||
|
```Powershell
|
||||||
|
Get-AppPackageLog -ActivityID <UUID>
|
||||||
|
```
|
||||||
|
|
||||||
|
</br>
|
||||||
|
|
||||||
|
|
||||||
|
---
|
||||||
|
|
||||||
|
### There are various causes that lead to error 0x80073CF6 </br> Find the fix that matches the error presented in the logs obtained from the instructions above
|
||||||
|
|
||||||
|
---
|
||||||
|
## Issue 1: 0x800706D9 "There are no more endpoints avaliable from endpoint mapper"
|
||||||
|
|
||||||
|
<img src="https://user-images.githubusercontent.com/68516357/227363632-7270ee01-9a98-44c2-9ccc-1fb2ef24897c.jpg" style="width: 900px;"/>
|
||||||
|
|
||||||
|
### **Windows Firewall**
|
||||||
|
|
||||||
|
**1. Ensure that Windows Firewall is on and is working with "Recommended Settings" being enabled**
|
||||||
|
|
||||||
|
**2. Ensure that Windows Firewall service is running. If not, enable it.**
|
||||||
|
|
||||||
|
**3. Restart your PC**
|
||||||
|
|
||||||
|
### Other Firewalls
|
||||||
|
|
||||||
|
**1. Ensure that your Firewall is on and is working with "Recommended Settings" being enabled**
|
||||||
|
|
||||||
|
**2. Ensure that your Firewall is not blocking or preventing new entries**
|
||||||
|
|
||||||
|
**3. Restart your PC**
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
---
|
||||||
|
## Issue 2: 0x80073B06 "Initial screen image for the current application context cannot be recognized"
|
||||||
|
|
||||||
|
```powershell
|
||||||
|
Installing MagiskOnWSA...
|
||||||
|
Add AppxPackage: Deployment failed due to HRESULT: 0x80073CF6, unable to register the package.
|
||||||
|
AppxManifest.xml (24,27): Error 0x80073B06: Unable to install or update package MicrosoftCorporateII.WindowsSubsystemForAndroid_ 8wekyb 3d8bbwe because the initial screen image for the current application context cannot be recognized. The application context may include specific language, DPI, contrast, or other special conditions. If you cannot recognize a context specific splash screen image, add a splash screen image to use as the default setting. Note: For additional information, look for [ActivityId] 94c065bb-5a2a-0004-129b-c1942a5ad901 in the event log, or use the command line Get AppPackageLo g - ActivityID 94c065bb-5a2a-0004-129b-c1942a5ad901 in the location D: WSA WSA Install.ps1:106 Character: 1
|
||||||
|
+ Add-AppxPackage -ForceApplicationShutdown -ForceUpdateFromAnyVersion ...
|
||||||
|
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
|
||||||
|
+ CategoryInfo : WriteError: (D:\WSA\WSA\AppxManifest.xml:String) [Add-AppxPackage], IOException
|
||||||
|
+ FullyQualifiedErrorId : DeploymentError,Microsoft.Windows.Appx.PackageManager.Commands.AddAppxPackageCommand
|
||||||
|
```
|
||||||
|
### Solution:
|
||||||
|
|
||||||
|
**1.** If you encounter this problem when installing from a build built using [MagiskOnWSALocal](https://github.com/LSPosed/MagiskOnWSALocal) or [WSA-Script](https://github.com/YT-Advanced/WSA-Script), try deleting the previously built builds and rebuild. Make sure to delete and reclone the git repo if you are building using MagiskOnWSALocal.
|
||||||
|
|
||||||
|
***Or***
|
||||||
|
|
||||||
|
**2.** If you encounter this problem when installing using prebuilt builds from [Releases](https://github.com/YT-Advanced/WSA-Script/releases/latest) from this repo, try redownloading the latest build. If the issue persists, report to the [Issues](https://github.com/YT-Advanced/WSA-Script/issues) and I will be happy to assist you
|
||||||
|
|
||||||
|
|
||||||
|
---
|
||||||
|
|
||||||
|
**Hope these fixes work for you!**
|
||||||
26
MagiskOnWSA/docs/Fixes/Fix Error 0x80073CF9.md
Normal file
26
MagiskOnWSA/docs/Fixes/Fix Error 0x80073CF9.md
Normal file
@ -0,0 +1,26 @@
|
|||||||
|
## Issue: </br> Error 0x80073CF9 when "Run.bat" is executed to install Windows Subystem for Android (WSA)
|
||||||
|
### Preface:
|
||||||
|
##### This issue can arise due to many factors such as corruption of files when downloading the .zip files or extracting from the .zip files. This can be also caused if the folder name is too long (This is the case as MagiskOnWSA tends to generate a long string for the .zip file and the folder within the archive.)
|
||||||
|
|
||||||
|
<img src="https://user-images.githubusercontent.com/68516357/219852713-fde4520d-9fa8-4c8b-80e6-ac2adecbeae9.png" style="width: 600px;"/>
|
||||||
|
|
||||||
|
---
|
||||||
|
## Solution
|
||||||
|
|
||||||
|
**1. Ensure the partition/drive you are installing from is NTFS**
|
||||||
|
|
||||||
|
**2. Redownload WSA .zip file on [Release page](https://github.com/YT-Advanced/WSA-Script/releases/latest) (sometime the files can be corrupted during download and extraction)**
|
||||||
|
|
||||||
|
**3. Rename the .zip folder to a shorter name, which can be anything to your choosing </br> (WSA_2xxx.xxxxx.xx.x_x64_Release-Nightly-with-magisk-xxxxxxx-MindTheGapps-13.0-as-Pixel-5-RemovedAmazon ----> WSAArchive2XXX)**
|
||||||
|
|
||||||
|
**4. Extract the .zip using WinRAR or a proper archive tool and not the built in Windows .zip extractor**
|
||||||
|
|
||||||
|
**5. Rename the extracted folder(s) to a shorter name, which can be anything to your choosing**
|
||||||
|
|
||||||
|
#### For example:
|
||||||
|
- **Before:** WSA_2XXX.XXXXX.X.X_XXXX_Release-Nightly-with-magisk-XXXXXXX-XXXXXX-MindTheGapps-XX.X-RemovedAmazon
|
||||||
|
- **After:** WSAExtracted2XXX
|
||||||
|
|
||||||
|
**6. Ensure that 'Run.bat' is run as Administrator**
|
||||||
|
|
||||||
|
**Hope this works for you!**
|
||||||
Some files were not shown because too many files have changed in this diff Show More
Loading…
Reference in New Issue
Block a user